Stories from an Examined Professional Life
A Reminiscent on a Life in Computers,along with Humorous and Poignant Stories
By Mark Dawson
General
Acknowledgments
To acknowledge all the people involved in an examined life is an impossible task. There are many hundreds, if not thousands, of people that have positively and negatively impacted my life. I would like to acknowledge both the positive and negative people in my life, as each group has helped me understand my life and hopefully helped me improve my life.
There are, however, a few people that need special acknowledgment as they had a special impact on my life. The first, of course, is my parents, Robert and Elverna Dawson. Parents have the biggest impact on your life and set the tone for the rest of your life. I would also like to acknowledge my two sisters, Patricia and Linda. They, too, have had a large impact (both positive and negative), especially during the formative early years of my life. My wife, Janice, and my daughter Jennifer have also had a major impact on my life and should receive a special acknowledgment. I would also like to acknowledge my in-laws, Robert and Ella Weber, as they too have had a great positive impact on my life, and you could not wish for better in-laws than what I had (may they rest in peace).
I also wish to acknowledge my editor, Grammarly, for the assistance it provided in getting this book polished and ready for publication. Those that know me know that my spelling, grammar, and prose are not of the highest order. I often say that I am a thinker and not a writer. The assistance that Grammarly provided in correcting my spelling, grammar, and prose was considerable, and this product is to be recommended for those that need this type of help. Without this help in improving the composition of this book, it would not have been possible to publish this book.
Of course, any errors or omissions, or flaws in this book are entirely my own. I take full responsibility for everything that I have written, as all authors are fully responsible for what they write.
Forward
An Unexamined Life
Socrates once famously said:
"An Unexamined Life Is Not Worth Living"
Socrates was wrong. An unexamined life can be worth living if it is lived in a moral and ethical way. However, an examined life is a more fulfilling life. If you examine your life, you will learn more about yourself, your strengths, and your weaknesses and have a better understanding of yourself and what is happening around you. These, then, are my stories from my examined life.
You might expect these stories from my examined professional life in computers to be dry and sometimes dull stories about computers and computer technology. This autobiography is not that type of autobiography, except for some parts at the beginning of this book where computers and computer technology are described to set the stage for the stories from my examined life. Instead, this book is a human story, not only about myself but of the people that I worked with and the human events of my professional life. By telling these human stories, I hope to impart some of the wisdom I have gained in my professional life. If not for the impartation of wisdom, there are enough interesting and humorous stories to entertain the reader.
All autobiographies spring forth from the personal memories of the author. As such, human memory is fraught with problems, forgetfulness being the most common problem of human memory. The “Seven normal memory problems” of Persistence, Bias, Suggestibility, Misattribution, Blocking, Absentmindedness, and Transience are all present when writing an autobiography, which can lead to issues of accuracy and objectivity in writing an autobiography. As this autobiography spans fifty years of my memory, this autobiography is susceptible to inaccuracies and subjectivity by myself. I have made a conscientious effort to be as accurate and objective as humanly possible, but I make no claims of perfection or anywhere near perfection of my memory.
For the memory mistakes I may have made in this autobiography, I sincerely apologize. If I should discover any mistakes that I may have made, I will correct this autobiography in the future.
Who, What, When, Where, Why, and How
I am an overweight, out-of-shape, newly-minted senior citizen. I am a heterosexual male, married, and the father of one adult daughter. I am of European descent (mostly Scottish, English, German, and some Eastern European), but most importantly, I am a Human Being (this is what I put on all forms that require I state my race).
As a human being, I have intelligence, and I can think and learn from knowledge, experience, and education. I attempt to keep my mind active and engaged and learn and think about the world around me. I have interests and hobbies (mostly classical, popular, and rock-n-roll music, old movies, historical America, and the history of the physical sciences), as well as a philosophy of life.
I was born (on the Ides of May - 1952) and raised in Philadelphia, PA. I spent my entire adult life in the northern suburbs of Philadelphia, PA. I attended Thomas Holme Elementary School and Abraham Lincoln High School in Philadelphia, PA, and I have some undergraduate credits at the University of Pennsylvania. I was an average to a poor student in elementary and high school, as I was unmotivated, of poor eyesight (which was not discovered until I was in High School), and I believe I am slightly dyslectic. Not until I entered the real world (having a job) did I become interested in learning, which I then took up with great enthusiasm. Consequently, my curriculum vitae is of my life experiences and autodidact education.
I started my adult life being highly introverted and technically oriented. I have since learned to become more extroverted and people-oriented. Most people who know me now would have no idea that I was such in my earlier years and do not suspect that I am still introverted, as I make extensive efforts to be more extroverted when I am with other people. I am considered by my friends, acquaintances, and associates (clients) to be easygoing, humorous, and a nice decent person.
Throughout my life, I have tried to improve myself - intellectually, knowledgeably, technically, and personally. Improvements to my intellect, knowledge, and technical skills have been autodidact through extensive readings and viewings of intelligent person's writings and commentaries. Improvements to my personality have been made with great efforts and significant changes to my approach to life. These changes were a result of self-examination from the stories of my life that were often done with harsh criticisms and critiques of my own faults, words, and deeds in these stories. As a result, I fell prey to the wisdom of the philosopher, author, and journalist Albert Camus:
"Man is always prey to his truths.
Once he has admitted them, he cannot free himself from them."
- Albert Camus
People who knew me in my twenties would not recognize the person I was in my thirties, and people who knew me in my thirties would not recognize the person I was in my forties. My fifties were also a significant change from my thirties and forties, but since then, I have remained basically the same. I am basically the same as I believe that I have obtained a level of intelligence, knowledge, experience, and wisdom that has made me a mature, well-rounded person capable of dealing with any situation that life presents to me. I also believe that this intelligence, knowledge, and experience have provided me with wisdom that I have tried to impart in my Chirps and Articles.
I have traveled somewhat (mostly business) and have spent several months in Sunnyvale, CA, and weeks at a time in Northern Germany, Southern England, and Washington, DC. I have also spent many days at a time in Dallas, TX, and Denver, CO, as well as a few days in numerous other US cities. My vacations have been spent in Bermuda (honeymoon), Cancun, Mexico, central California, and my mother’s homestead in Northern Minnesota. My other vacation places have been at various places in the Northeaster USA, from Maine to Virginia.
I was born with, and still have, a minor heart murmur that is getting progressively worse (now it is Bilateral Bundle Branch Block), and I have absolutely no arches on my feet (every doctor who has examined my feet has commented on this). I have had my tonsils and appendix removed, my nasal passages cleaned out twice, and my deviated septum repaired. I have had very poor eyesight since childhood; I have progressive hearing loss due to my computer occupation and not much of a sense of smell. I had ulcers in my early adulthood (mainly due to work-related stress), and I continue to suffer from hyper-acidity of my stomach) I suffer from sleep apnea, lower back pains from ligament damage, and occasionally upper back pains from a case of whiplash I suffered in an automobile accident. I also suffer from wrist, elbow, and shoulder pains (tendinitis) when I am extensively utilizing a computer. I have high cholesterol and am borderline diabetic. I had my Droopy Eyes (Ptosis) repaired when I was sixty, and I eventually required cataract and lens replacement surgery on my eyes. I regularly have upper respiratory infections, but fortunately, I never had any broken bones or serious injuries in my life. As of this writing, I am scheduled for Osteoarthritic knee replacement on both of my knees. Mostly all of these conditions could be improved if I exercised regularly and had a better diet. But being busy, lazy, and unmotivated, I do none of these things. I have, however, almost died thrice in my life.
People who know me claim that I have a good sense of humor but that I am a very poor joke-teller. I do, however, have the ability to tell stories from my own life, as well as historical and scientific stories, and as such, they regard me as a good storyteller. I have tried to live a moral and ethical life, and honesty and integrity are very important to me in my dealings with myself and others (in other words, I am a straight shooter). I hope that all these characteristics are revealed in this article.
In other words, I am much like most other Americans, and there is nothing special about me other than I think a lot. I have often said that English is my second language, while thinking is my first language. Those that know me, and my writings, know that my second language (English) can be very poor in both spelling and grammar (thank God for computer spell checkers, thesaurus, and grammar checks), and I struggle to write anything. I am a very organized and logical person, and I attempt to keep my writing organized and logical. I attempt to write clearly, concisely, completely, confidently, and understandably. As such, I hope that this book is readable to all with a high school education.
A Professional Life
Upon my retirement from the computer field at the end of 2019, I started to reminisce on my career, and I must say it has been a long and varied career lasting almost a half-century. My career has been centered in the Philadelphia, PA, metropolitan area, where I was born and raised. While I have done most of my work around Philadelphia, I have, in the middle part of my career, taken many national and European business trips, from which I have accumulated many stories and which I will recount in this document. These stories of my professional life and business trips are often humorous, but sometimes pathetic, but always illuminative of the human side of life in the computer field. I hope that these stories will be informative, instructive, and enlightening and I can impart some of the wisdom I have gained throughout my professional life.
Today, many people enter and often remain in a niche field of computer technology. A niche made necessary with the explosion of computer technologies in the last three decades. When I started my career in 1969, such specialization was limited, as most of the computer field was dominated by IBM Mainframe computers. The only specialization was Computer Operations, Computer Programming, Mainframe Operating Systems maintenance, and Mainframe Equipment installation, maintenance, and repair. And, as qualified computer professionals were scarce at the start of my professional career, there was much opportunity for advancement and growth in different fields of computer technology. Because of this scarcity, it was possible to easily move from job to job, which I did quite frequently to advance my career, and always with a pay increase.
There was also no room for any form of racism or religious bigotry in the computer field, although sexism was common at the beginning of my career. I, therefore, got to know and work with a diverse group of Whites, Blacks, Asians, and Latinos, as well as Protestants, Catholics, Jewish, Muslims, and even a few Latter-Day Saints throughout my computer career. I witnessed sexism in the computer field decline and then fall. I have worked with women, been supervised by women, and supervised women. My opinion of all the people I worked with was based on their work—some I liked, some I didn’t like, some I thought were well-qualified, and some I thought were unqualified. I enjoyed working with most of them, and those I didn’t enjoy working with I thought should not be in the computer field or were unsuited to their current positions. Throughout these stories, when I mention the full name of a person, it is because I respected and admired them, and when I mentioned the first name of a person, it was because I liked them and I thought that they were fully qualified in their positions. When I use job titles, it is because I am mostly neutral about them. On some occasions, when I use job titles, it was because I disliked them or thought they were unqualified for their position. Two of the managers that I worked for I do not mention their names, even though I liked and respected them, but they fell short of doing right by me. For one manager in particular, I do not mention his name for the same reason that the Jewish people or Biblical archeology does not know the name of Moses’s Pharaoh, and only God can forgive him for the havoc he wrecked upon the lives of many people who worked for him. I will leave it to the reader to determine who were these three managers.
I began my computer career by attending a three-month Computer Programming trade school after my high school graduation. A trade school in which I learned Mainframe Assembly computer programming language, the Report Program Generator (RPG) programming language, and the COBOL computer programming language. However, upon graduation from this trade school, I discovered very few companies were hiring computer programmers without any experience, but I was able to obtain employment in the Computer Operations field.
I then spent the next several years in Computer Operations in several different companies, which required that I work several different night shifts. My duties were as a punch card and paper printout jockey, a tape jockey, a disk jockey, and a computer console operator, much of which was done by myself or with the assistance of another Computer Operator. Eventually, I worked with a group of Computer Operators as a senior computer operator directing the team of computer operators. I also became an expert in IBM Mainframe Computer Job Control Language and Computer System Utilities. In all these Computer Operator positions, I was able to utilize my job control and utilities expertise to streamline the jobs processes to make the jobs execute more efficiently, thus reducing the job process time by a considerable percentage. I was also the go-to person whenever questions, issues, or concerns arose about job control or utilities.
For reference purposes, I have posted these images of the common IBM Computer and attached peripheral computer equipment that I worked with in my seven-year career as a Computer Operator.

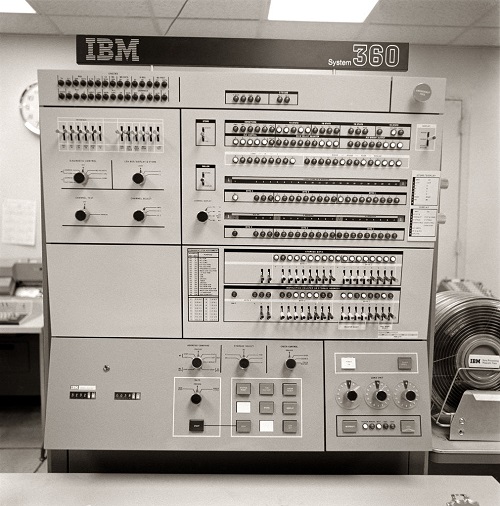
IBM S360 Computer and Front Plate

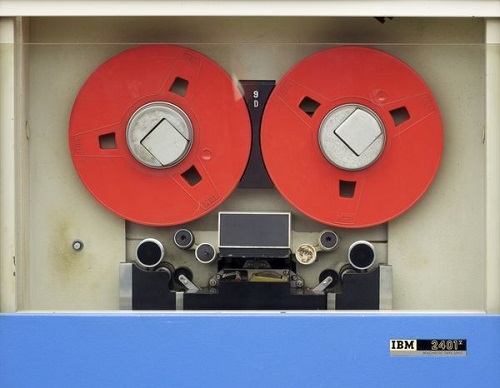
IBM Tape Drives and Tape Mechanism


IBM Removable Disk Drive & IBM Chain Printer


IBM Punched Card Reader & Card Punch
After a short break in my computer operations career, in which I became a Travelling Science Show instructor at the Franklin Institute during the American bi-centennial School year, I resumed my computer career as a Computer Software Configuration Management role for an IBM Mainframe computer programming team for a large banking institution. A Computer Software Configuration Management task before this computer science field was founded. As I was without any methodologies or tools necessary to accomplish this task, I, therefore, needed to create my own methodology and tools to perform this task. After successfully accomplishing this task, I was promoted to an IBM Mainframe Computer Programmer with another team at this bank.
I then became a maintenance programmer with a small group of programmers in a large computer programming department of a large insurance company. Within six weeks of starting this job, I was promoted to the unofficial title of “Super Programmer”, responsible for undertaking the most complex and difficult programming tasks for the entire computer programming department. Within ten months of becoming a super programmer, I was promoted to Senior Designer and Programmer for a project that, as far as we could determine, had never been done in the computer field. A project that was for the Automatic Program Generation for Database Population and Database Reporting. This project consumed the next two years of my professional life, a project that many believed was not possible but a project that succeeded beyond anyone’s expectations.
I then found a new job as a Systems Engineer for classified government programs in a large Aerospace company. A job that I am still not able to discuss in any specific detail due to the classified nature of the work that I performed. A Systems Engineering task that involved the Software, Hardware, Databases, Data Communications, and Computer Operations specifications and design utilizing Structured Analysis (SA) and Structured Design (SD) techniques. A job in which I was a Program Change Control manager, a Computer Systems Lead Engineer for Multi-contractor Coordination, a Computer Systems Chief Engineer, and a Computer Systems Proposal and Program Manager responsible for the Management, Financial, and Technological aspects of classified government programs.
I then left this company after political machinations and back-stabbing exhausted me. After a two-month break, a fellow co-worker from the previous company that I worked with, who had also left this company before I did and for the same reasons, asked me to join him in a new venture he had started. This venture was a Pet Sitting business in a very affluent suburb in which he lived. After seven months of assisting him by being a pet sitter, I started my own venture of pet sitting in the suburb in which I lived. While this venture was successful, it was not profitable enough to support a growing family and consumed so much of my time I had little time left over for my family.
I, therefore, decided to end this pet-sitting venture and strike out on my own as an Independent Computer Consultant for small businesses and the self-employed in my local area, a task that I spent almost three decades performing. As an Independent Computer Consultant, I was responsible for the installation, configuration, and maintenance of Personal Computers (both Windows and Macintosh computers) at my client’s locations. This also involved the installation, configuration, and maintenance of Computer Applications on these computers. Applications such as Microsoft Office (Word, Excel, PowerPoint, and Access), QuickBooks accounting, and Goldmine Customer Relations Management, as well as several other computer applications that my clients needed to run their businesses. I was also responsible for creating the Business Process Automation for my clients, utilizing this computer equipment and applications, as well as training their employees on these computers, applications, and Business Processes. I also learned how to create simple web pages at the start of the Internet revolution, and I created several websites for my business clients. I also assisted my clients in incorporating Internet and Cell Phone technologies in their business operations.
During all these efforts, I had to learn and become proficient in Mainframe, Workstation, and Personal Computers; Computer Database Query and Reporting Languages; Database Analysis and Design utilizing Entity-Relationship Design, Database Normalization techniques; and Database Structure Design for Hierarchical Databases, Inverted Index Databases, and Relational Databases. I also learned and utilized Network Topology, Analysis, and Design on Mainframe computers, as well as Peer-to-Peer and Client-Server Networking on Personal Computers. I also learned and became proficient in Computer Programming with Structured Systems Analysis and Design Methodologies. During my career, I became very proficient and skilled in Computer Systems Training and Computer Systems Testing, as well as documenting computer systems and applications.
In all these efforts, I have learned that it is the people, not computer technology, that are responsible for the success of any computerization. Computer Technology is important to achieve success, but without the people involved, the technology will not be utilized properly and fully to achieve the goals of the business. I, therefore, approach every computer task from a people perspective. A people's perspective of computer technology usage is that without the personal involvement of the persons so affected, there can be no success in instituting computer technology. A perspective that is often lacking with today’s computer specialists. However, the most successful computer technologists are the ones who have this perspective.
I did all this without any formal education, as I have no College Degree. Consequently, I extensively read user manuals, textbooks, and magazine articles on these technologies, thus becoming an autodidact in these technologies. I also, fortunately, had the assistance of several people who were experts and had a College Degree and extensive experience in the computer field that assisted me in my learning. None of this could happen in today’s specialized world of computer technology, and I was fortunate to have lived in an era when specialization had not occurred.
I have written this not with a sense of braggadocio but with a sense of pride in my accomplishments. I have also written this to provide my readers with a sense of how broad and knowledgeable I am in computer technology. I, therefore, believe that I am much more than competent in commenting on the issues of computer technology. I have also learned the importance of people and how to best consider the actions and motivations of people. I have also learned, as in one of my “Truisms”, to:
“Remember to love people and use things, rather than to love things and use people.”
The following are the jobs that I have held, the stories from these jobs, and what I have learned from these stories.
Computer Educational Institute (Jul 1969 - Sep 1969)
Background
Near the end of my senior year of high school, my father and I attended a jobs convention for senior high school students at the Philadelphia Civic Center. At this convention, there were not only potential employers but also some trade schools in attendance. While browsing these different booths, my father and I came across a trade school that taught computer programming – Computer Education Institute (CEI). As Computer Programming was an emerging field in the 1960s, with many opportunities for solid, well-paying employment, my father and I were intrigued about this possibility for my future. The booth representative encouraged me to take a free test that would measure my logic abilities, which were created to determine a person’s aptitude for computer programming. This test was of twenty questions to be answered within thirty minutes. I decided to take the test, which I completed in twenty minutes. After the booth representative graded my test, he informed my father and me that I had answered all the questions correctly, and he also commented that I had completed the test faster than anyone else that he had tested. He informed us that it was not their policy to accept applications for enrollment at the trade booth but only to arrange a follow-up interview with my father and I that would occur at our house. We did arrange and conducted this interview at our home, which lasted about an hour, at which time we agreed that I would attend CEI at the start of the summer session. CEI training consisted of three months of classes on each weekday, with enrollment in either the morning or afternoon class, with each class being a four-hour session. I, therefore, enrolled in afternoon classes from July through September, which I attended.
Classes were intense and much of a grind, but I felt exhilarated as I found that I liked and had an aptitude for computer programming. I spent eight weeks learning how to program in Assembler Language (Machine Language), three weeks learning how to program in COBOL (Common Business Oriented Language), and another week learning RPG (Report Program Generator). At the end of these classes, there was a small graduation ceremony where we all were presented Certificates of Achievement, and I received the award of ‘Dean’s Award for Scholastic Excellence’.
The Teasing
As I was an introverted person and not very social as a result, I was considered a strange bird by my classmates and was the butt of some teasing by them (all but one were recent High School graduates). The one who was not a high school graduate was a family man in his late twenties who tried to defend me, which my shyness did not allow me to do for myself. At one point, he excoriated them in my presence by informing them that while they were teasing me in my absence, I was in the computer room, expediting the running of their assignments on the computer. This drew a silence from them, but no apologies were forthcoming. I learned to accept Que Sera, Sera as a result of my shyness and continued to remain introverted until I proactively tried to overcome my shyness.
The Job Search
Near the end of my graduation, I sought out a Church member, Mr. Smeltzer, who owned a computer operations and programming firm, Trilog Associates, to inquire about employment in his firm. He informed me that medium and small businesses could not afford to hire inexperienced programmers due to the economics of additional training, longer development times, and lower billing rates for inexperienced programmers. He recommended that I try to seek employment with larger companies, and even then, I may not be successful, but I could be offered employment in a lesser role in their computer departments. Advice which I took to heart as I accepted a position in the Computer Operations department of Sun Oil Company upon graduation from CEI.
(p.s. – a few years later, I did eventually go to work at Trilog Associates as a senior computer operator, and my sister married one of Mr. Smelter’s sons).
Delivery Boy (Jun 1969 – Sep 1969)
Background
My paternal Aunt Marge (who was also my Godmother) was an office administrator at a Philadelphia Trade Group organization. One of the members of the trade group who operated a small printing shop mentioned to her that he needed a part-time delivery boy during the summer to pick up and deliver materials to and from his customers, as well as several other odd jobs in his shop. She mentioned that her godson was going to a trade school nearby on a part-time basis and that I would be a good person to hire. After a short interview, he hired me on the spot, and I began working for him immediately while I attended CEI. This job lasted until I graduated from CEI and found a job at Sun Oil Company.
This printing shop had three full-time employees: The Composer, The Printer, and The Collator. While the print shop was owned by an outside person, it was operated and managed by the person who hired me, who also was The Composer of the print jobs. The Composer was the person responsible for making the print plates that the Printer used to produce the paper sheets in the quantity required. The Collator would collate multi-sheet jobs in the proper order and package them for delivery. I would be responsible for picking up the materials from the customers that The Composer needed and delivering the finished product to the customer. I also assisted The Collator with stocking the materials needed for the print shop. I also took it upon myself to sweep and clean the shop on Friday afternoon.
The Composer
The Composer was a very nice and congenial family man in his early forties who was very good at his job responsibilities. The Printer was excellent at his job (which was complicated), and he was a shy and reserved person in his mid-thirties that was a single person that still lived with his mother. The Collator was a divorced woman in her early fifties, and while she was very competent in her job, she tended to be cantankerous. However, we all got along very well, and it was a very smooth functioning operation.
The Printer
One day, in the middle of this job, I arrived at work and noticed that The Printer had a cut and bruises on his forehead, but I made no mention of this to him or the others. Later that day, he abruptly quit and left the premises. In discussing this with The Composer, I mentioned his cut and bruises, to which The Composer commented that he was very busy that day and he had not noticed these cuts and bruises. He telephoned The Printer that evening to discuss the situation to try to lure him back to the job. The next day I learned the truth about what had happened. Unbeknownst to me, the Printer was a homosexual that had visited a nearby gay bar the evening before he sustained his cut and bruises. Upon leaving the gay bar, he was threatened and attacked because of his homosexuality, and he was traumatized to the point that he did not want to be anywhere in the environs of the gay bar, which included the print shop. Despite the support and pleadings of the Composer and the apologies for not noticing the cut and bruises during the workday, The Printer was adamant that he would not come back to work. It, therefore, became necessary to expeditiously hire another printer. The new printer was hired within a few days, but he was not as competent as the other printer and required more supervision to get the job done properly and on schedule.
The lesson that I learned was that it is important to notice any distress from your co-workers and to offer assistance or support to the co-worker or inform the management of any potential problems of a co-worker. It also reinforced my aversion to discrimination and violence against any group of people due to their associations, and most especially against homosexuals. I vowed to myself that I would never use slurs or epithets against any person or group of persons, a vow which I have kept for my entire life.
The Collator
Toward the end of this job, The Collator became more cantankerous and divisive in the workplace. She informed the new Printer that The Composer was not really the boss, as the owner made all the important decisions. As she was friends with the owner, she knew better than The Composer what the owner really wanted. Upon hearing this from The Printer, The Composer promptly fired her after she admitted that she had, indeed, said this to The Printer. She complained to the owner, to which the owner replied it was The Composers' responsibility to decide on hiring and firing decisions, and her employment was terminated. This taught me that the real boss is the person who manages the business and who can hire and fire someone. Something that I carefully kept in mind whenever I dealt with any management of all the companies that I worked for.
Sun Oil Company (Oct 1969 - May 1970)
Background
My first real computer job was as a Debatcher in the Computer Operation department at Sun Oil Company. A Debatcher was responsible for feeding punched card decks into the card reader, then matching the computer printouts to the card deck, and then rubber banding them together and placing them in the mail bin. I was also responsible for learning the other functions of computer operations and assisting the computer operators in their responsibilities as directed and under supervision of the computer operator. This was not a difficult task but an important first step in my computer career. I did, however, establish a work ethic and learned some important lessons.
The Card Shuffle
One of the other Debatchers was not as careful in his efforts as I was. The one task that he undertook was to feed a twenty-tray punched card deck into the card reader in the proper order. This was a grind of a job that took over an hour to accomplish. Near the end of this job, he lost his concentration and feed tray nineteen before tray eighteen. Upon the discovery of his error, he was publicly admonished and required to redo this job. Not wanting to ever be publicly admonished, nor wanting to redo any task I undertook, I was careful to always do a job properly, a caring that I carried with me in all tasks that I undertook in my life.
The First Disk Drives
Hard disk drives were uncommon when I started my computer career, as most data was stored on computer tape files or punched card decks. Hard disk drives were also large, slow, of very limited capacity, and very expensive. Sun Oil had two hard disk drives, one attached to a Univac computer and the other attached to a GE computer. Each one utilized different technologies for their functioning, and I became fascinated with their workings, and I self-taught myself their internal workings. I discovered that if you traced the follow of electricity in a device, you could better understand how the device worked. This fascination carried over to the other computer equipment that I worked with, as well as the computers themselves. I discovered that an understanding of the internal workings of the equipment allowed me to become a more competent and efficient computer operator. I have carried this fascination with the internal workings of all electronic equipment that I utilize so that I may better understand how they work to effectively utilize them and to fix any problems that I may encounter when utilizing them. To me, a black box is only black because of its color and not because it is functioning.
Excessive Swearing
When I was working at Sun Oil, I swore up a storm. One day a mature computer programmer, who I admired, pulled me aside to discuss my swearing. He explained to me that he had noticed that I was extensively swearing and that he believed that this was because of my youth. He also commented that he believed that as this was the first time I was on my own and without parental supervision, I swore much too often so that I would appear to be an adult. However, he explained, swearing did not make you look like an adult, but instead, extensive swearing made you appear childish. He further explained that swearing should only be done in a limited and appropriate manner to draw attention to what you were saying or to emphasize the passion of what you were saying. To do so otherwise was disrespectful and impolite to those around you. He suggested that I limit my swearing to those situations where it was appropriate. I took his words to heart, and I vowed to only swear to myself, and ever since, I only swear on rare occasions where it is appropriate.
Underage Overtime
As this job was the first job where I earned real money, I was interested in earning as much money as possible. I, therefore, volunteered for as much overtime as possible to earn the extra time and a half wage. After several months of doing this, my supervisor informed me that the human resources department had discovered this overtime, and as I was under the age of eighteen, that overtime was not permissible under Pennsylvania’s Child Labor Laws. Even though I was a high school graduate, the law was inflexible on this point, and I would not be allowed to work any overtime until I became eighteen. While I was greatly disappointed in not being allowed to work overtime, I was even more furious at a law that made no sense in my situation and had no flexibility for special circumstances. This was the start of my wariness of governmental laws, rules, and regulations that lacked flexibility based on special circumstances.
The Lack of Promotion
In the spring of 1970, Sun Oil decided to offer a programming course to selected computer operation personnel in the expectation that they would promote someone to a computer programming position. This programming class was to teach the computer language FORTRAN (Formula Translation), a programming language that I was unfamiliar with. I eagerly volunteered for this training in hopes of a promotion to a computer programming position. Four of my co-workers took this course, and while they satisfactorily completed the training, I aced the course and often helped the other co-trainees with their understanding and their assignments. I believed that I had demonstrated I was the best-qualified person for the promotion, which I did not receive. The instructor explained to me that he decided to promote another trainee who was older and had more service time at Sun Oil. He also explained that one of the assignments had a hidden test of ability within the assignment. The assignment was to solve a mathematical problem based on a series of numbers (as it turned out, it was a Fibonacci Sequence, although I did not know this at this time). I had noticed that the series of numbers had a pattern that I could utilize to solve the problem, but if I utilized this pattern, the computer program would only be useful for this pattern. I, therefore, wrote a more generic program that could solve the problem for any series of numbers. Although he commented that this was an efficient solution to the assignment, as he had already made his decision on who to promote, he would not be changing his decision, and he was only authorized to promote one person.
Bell Telephone
I was, of course, greatly disappointed, and I resolved to start an employment search for a company that would hire me as a computer programmer. In my search, I discovered that Bell Telephone was planning to hire inexperienced programmers based on an extensive test of their skills and abilities. I arranged to take this test on a Monday morning, and I telephoned the test manager later in the week to determine my status. He informed me that I had the best test results and that they were preparing a job offer letter that they would mail to me the next week. In my excitement of learning of this, I tender my two weeks’ notice of resignation from Sun Oil which I handed in on Friday afternoon. I eagerly awaited this job offer letter, and when I did not receive this letter by the end of the following week, I telephoned the testing manager to determine its status. He informed me that as the Penn Central Railroad had declared bankruptcy at the beginning of the week that Bell Telephone had put on a hiring freeze until the local economic situation stabilized. Consequently, I will not be receiving a job offer letter in the near future.
Being a very stubborn young person at this time in my life, I did not withdraw my resignation letter but set about to find another job. In this, I was unsuccessful, as most companies had a hiring freeze because of the Penn Central Railroad situation. Therefore, I became unemployed with no unemployment insurance as I had voluntarily terminated my employment. In this, I learned the old adage to ‘never count your chickens until they have hatched’.
Unemployed (Jun 1970 - Jul 1970)
Background
While searching for a new job, I assisted the construction workers that my father had hired to raise the slope of the back roof of our house. My father was doing this to provide more living space for myself and my sister, as well as increase the property value and salability of our home when the time came for my parents to move in their retirement. My assistance reduced the labor cost of this construction and expedited the completion of this project.
Computer Cutter (Aug 1970 - Sep 1970)
Background
I eventually found a job as a night shift specialized computer operator for a small startup company. This company started to utilize new computer technology to create cardboard cutouts for clothing manufacturers. Cutters of the cloth used these cutouts to create the size and shape of the cloth that were needed to sew the clothing. A computer-directed cardboard cutting machine would create the different shapes and sizes that were needed to manufacture clothing. This was an important technology for clothing manufacturers, as it would reduce the waste and cost of clothing manufacturing.
However, there were problems with this new computer technology. The cutting machine would often slightly lose its grip on the cardboard, and the resultant cardboard cutout would be imprecise and not usable. I had to be on the lookout for this problem and discard those cutouts that exhibited this problem. This meant I had to redo the cut, which took more time and material to accomplish. I also discovered that I was not very good at discerning this problem, which I believe was because of my poor eyesight. After two months of continued problems and errors, both my employer and I agreed that I was not suited to this job. We amicably parted ways, as I agreed not to claim unemployment benefits, and they agreed not to claim that I was fired for a cause but that I was laid off.
There was also the problem that Philadelphia-based clothing manufacturers were relocating to South Carolina due to unionization issues and lower labor costs, and as a result, their company sales were plummeting. I also discovered (as a byproduct of my next job) that the new computer operator that they hired was encountering the same problems. Shortly thereafter, this company went out of business because of these problems and issues.
Joseph H. Cohen & Sons (Oct 1970 - Sep 1971)
Background
Within a week, I found a job as the night shift computer operator at a men’s suit clothing manufacturer. The night shift computer operator was responsible for running the daily and weekly business computer jobs, and the shift hours were from 4:00 PM to 12:00 AM. The daily jobs were needed for the next day’s manufacturing and business activities, while the weekly jobs were utilized for materials ordering and financial recap/projections of the business. I was responsible for ensuring these computer jobs were completed before I finished work. Often these daily jobs would take eight to twelve hours to complete, and it was not unusual for me to finish work between 2:00 and 5:00 AM in the morning. I also worked later into Saturday morning to complete the weekly jobs, which were not finished until 7:00 AM to 9:00 AM on Saturday morning. As such, 50-to-60-hour work weeks were common.
After about six weeks of doing this, I realized that the way these jobs were run was inefficient, and I set about making them efficient. Utilizing my knowledge of Job Control Language and Computer System Utilities, I streamlined the processing, which resulted in a reduction of processing time of approximately 15 to 20%. Consequently, my daily work was usually finished by 1:00 AM, and my Saturday work was often completed by 6:00 AM. Thus, my average work week was about 48 to 50 hours. My labor efforts were also reduced by this efficiency, thus making my efforts less physically taxing. However, constant 48 to 50 hours work weeks will drain most people (even a young person such as myself), and I was often exhausted at the end of the work week. I also had no personal life, as my life was mostly working, eating, and sleeping.
This situation remained thusly until the hiring of a new Computer Operations Manager. This new manager wanted to impress the company management by reducing the costs of computer operations. He determined, without discussing it with me, that he could reduce the number of Tape and Disk drives from five to four apiece, which reduced monthly leasing fees. Unbeknownst to him, because he never discussed it with me beforehand, this reduction obliterated my job efficiencies and necessitated a complete redoing of all the Job Control Language and Computer System Utilities. I discovered this reduction as a fait accompli when I showed up for work and noticed the missing tape and disk drives. When I informed the new computer operations manager of the impacts of this reduction, he told me that I would have to work longer hours to correct this problem and run these jobs. At this point, I informed him that I would have to do nothing, as I was resigning on the spot. I, therefore, turned around and left the building, never to return.
My only regret is that I did not provide them with assistance to fix this issue, as I am sure it must have impacted their business and manufacturing operations for the next few days while they fixed the problems of the reduced tape and disk drive. I also suspect that the costs to their business operations and manufacturing for the next few days were more than several years of the leasing costs for the additional tape and disk drive. In my defense, however, I was so exhausted by this point that I could not face the effort to fix this problem, nor the additional future hours it would take to run these jobs on a daily and weekly basis. From this, I learned the lesson of never walking away, except gracefully, from any employer. I also learned that you should discuss any major changes to anything without first discussing the change with all the impacted people – both computer personnel and businesspersons.
But at that point, I felt like the following illustration:

The Magnetic Tape Cartridge Reader
As was usual for this time in computer operations, the major source of input transactions was via punched cards. Punched cards had various problems associated with using them, and with alleviating these problems, it was decided that Joseph H. Cohen & Sons would utilize a new IBM technology developed to replace punch cards - The Magnetic Tape Cartridge. The keypunch operators would record their efforts on a magnetic tape cartridge, which would then be read from the new IBM Magnetic Tape Cartridge reader attached to the computer. This was a novel and innovative approach to solving the problems of punch cards. However, it introduced another problem. The IBM Magnetic Tape Cartridge reader was prone to failure due to an occasional misalignment of the read heads to the magnetic tape. When this happened, it became necessary to have an IBM hardware support technician pay an onsite visit to fix this problem. It also seemed that the more the Magnetic Tape Cartridge reader was used, the more often it failed. At the start of this experiment, the Magnetic Tape Cartridge reader would fail two or three times a month, which gradually became once or twice a week. This onsite visit to fix the Magnetic Tape Cartridge reader delayed the processing of the computer jobs that utilized it by two to three hours, as that is how long it took the hardware support technician to arrive and fix the problem. Many times, the hardware support technician was unfamiliar with the Magnetic Tape Cartridge reader, as it was a new technology that was not in common usage. Eventually, this problem, and the delays it caused in fixing the problem, became unacceptable, and Joseph H. Cohen & Sons discontinued using this equipment. This experience led me to be wary of new, unproven technology being utilized in the normal computer operations required to manage a business.
The Sexploitations
A few weeks after I started working at Joseph H. Cohen & Sons, I gazed out of the large windowpane that separated the Computer Room from the management floor of the company. I quickly noticed that the perimeter of the floor had separate offices for the different managers, who were all white males. The interior of the floor had dozens of desks for the secretaries and clerks who supported the managers, and all these secretaries and clerks were young, attractive, and white or Hispanic females. When the day shift computer operator joined me in my gazing, I mentioned, facetiously, that it was quite a harem out there. He replied that my statement was truer than I expected. He explained that those young ladies were all single and hired from the factory floor as a promotion and at a significant wage increase. As these young women were from the lower class, this promotion gave hope to them that they could become middle class and possibly marry a middle-class manager. He further explained that an unwritten requirement for obtaining the promotion was that they would provide sexual favors to the male management team at the company. All a manager had to do was walk over and invite the woman to ‘lunch’ or ‘dinner’, which was a code term for a visit to the seedy hotel a few blocks away that rented rooms by the hour, and for the purpose of sexual intimacy with the young woman.
I expressed that I had difficulties believing this, but he told me that I qualified for this perk anytime I wished. He volunteered to cover the first hour of my shift anytime that was needed, and he suggested that I give it an immediate try. I declined his offer as I thought that this was unseemly, and I was not sure if he was just joshing with me. I soon discovered from others that he was not joshing, but this was a real perk of my employment. I never partook of this perk because I felt it was wrong, but I did notice others who did partake of this perk.
The Illness
One late evening I started feeling abdominal discomfort and severe nausea, followed by chills and sweats, which I attributed to a high fever. This impacted my ability to continue working, and I telephoned the Computer Department Manager to inform him of my illness, and he agreed to come in and finish my work. When he arrived, I was in worse shape, and he commented on how terrible I looked. As he knew I took public transportation to and from work, he insisted on driving me home and then coming back to finish the work. I felt so miserable that I accepted his offer. The next morning, I went to my doctor, who diagnosed me as having a virus that was going around, and he recommended at least three days of bed rest to recover. I telephoned the Computer Department Manager and informed him that I could not return to work until the following week, and he had the day shift computer cover for me on the second shift. When I returned to work the next week, the day shift computer operator commented that he had no idea of the workload and hours required to finish the workload, as I generally worked nine to eleven hours a day and often six to eight hours of overtime on the weekend. The Computer Operations Manager then informed me that I was to immediately be given a 25% raise to compensate for the long hours that I was working during the week.
The Aggrieved Wife
One of the computer programmers at the company, who was married with children, became very infatuated with one of these women and started a very torrid sexual relationship with her. When his wife found out about the relationship, she charged into the building and confronted the woman, and started a physical confrontation with her. It became necessary for the guards to separate them from each other and forcibly evict the wife from the premises with a warning to never return. Nothing was ever said to the programmer or the female employee involved, as this type of sexual relationship was an acceptable practice at the company, and if they did anything about it, they would have to take action against many other managers who engaged in this practice.
The Black Book
The IBM Field System Engineer who was responsible for maintaining the computers at Joseph H. Cohen & Sons was a late twenties single male who was also eligible for this perk. Upon discussing it with him, he related that he never engaged in this perk. But he did inform me that he had many girlfriends at other companies for which he was the IBM Field System Engineer. He informed me that this was against IBM’s policies, and he needed to be very discreet, or he could lose his job. He kept the girlfriends from knowing about each other by making sure that there was some physical distance from each other and by dating them for romantic purposes as well as sexual purposes.
I asked him how he separated them in his own mind and how he did not slip up and reveal the other girlfriends when he was on a date with one of them. He then took out a little black book that he used to record detailed information about each girlfriend. Before going out on a date or having a sexual liaison with one of them, he would carefully review the information in the Black Book and try to stay within the bounds of what he had recorded about the woman. One night I received a frantic telephone call from him in which he informed me that he was about to go on a date and had misplaced his Black Book. He asked if I would check on the desk which he had utilized that day to see if he had left it on the desk. Upon checking, I discovered the Black Book. He had me read the page on the girl he was about to date so that he could go on a date without incident. I did so, and I found it very interesting reading. He asked me to hold onto the Black Book until he could retrieve it from me the next day. As a reward, he told me that I could read about the other girlfriends if I never revealed what I read. I promised him that his secrets were safe with me, and I spent an interesting night reading his Black Book.
The Sexploitations, The Aggrieved Wife, and The Black Book stories introduced me to the seeder side of business life and the importance of not mixing your business and personal life. I attempted to keep this in mind in my future professional life, and I only failed to do so twice: with my first girlfriend, who I met while employed at Alco Standard Corporation, and when I met my future wife while employed at PSFS.
The Unexpected Gunshot
Every evening one of the jobs I ran took approximately ninety minutes to process and was usually done near the end of the shift. This job did not require any computer operator intervention while it was processing, and if I had no other jobs to process, then I could take a break. During this break, I often went to the building entrance to converse with the armed guard with whom I had become very friendly. These conversations were varied in subject matter, but sometimes he told me stories about what was happening at Joseph H. Cohen & Sons (this is where I learned about some of the sexual exploitations and the aggrieved wife). One evening I went down for a conversation, and I discovered him cleaning his revolver. He explained to me why, what, and how he was cleaning the revolver. After he finished the cleaning, he pointed the revolver above the doorway and pulled the trigger. Much to his and my surprise, the revolver discharged a round. This was a surprise, as he had carefully explained to me that before cleaning a gun, you should make sure that no ammunition was in the gun. He thought that he had done this, but apparently, he was mistaken. I expressed relief that he had not pointed the revolver near me, and he expressed relief that the revolver had not discharged while he was cleaning it. He further explained that he had learned that you should never point a gun except where you intend to shoot and that you should never pull the trigger unless you intend to shoot. The only time that he violated these rules was after cleaning his revolver, and he did this to ensure that the mechanism of the gun was working properly. He humbly apologized that he was not more careful when he unloaded the revolver and that he would make doubly sure the revolver was unloaded before he began any cleaning in the future. As I did not own a firearm, nor intended to own a firearm, the lessons he taught me would not be applicable in my life, but I learned these lessons that in the event that I ever owned a firearm, I would keep these rules in mind.
The Commute
When I started working at Joseph H. Cohen & Sons, I did not own a car, and I took a one-hour fifteen-minute bus, then an elevated train ride, and then another bus ride to and from work. One morning, after working sixteen hours, I was on my way home on the elevated car when I fell asleep in the elevated train car. I was awoken by the train engineer after the elevated train had pulled into the parking shed at the end of the line. Fortunately, another train was pulling out of the shed, and I hopped a ride to the station, where I caught my bus to get home to a long sleep.
The Bus Driver
While working at Joseph H. Cohen & Sons, I did not own a car nor have a driver's license and, therefore, needed to take public transportation to and from work. This posed some difficulties, as it took a bus trip, then an elevated train ride, then another bus trip of about an hour in each direction to get to and from work. The daytime bus route that I took had a bus stop in front of my house, but alas, at this time, bus transportation was infrequent between the hours of midnight to six in the morning in Northeast Philadelphia. On the bus trip home, if I did not catch the last 1:00 AM outbound bus route departing from the Elevated Station to my neighborhood, I would have to take another bus route further from my home, which required that I walk a quarter mile from the bus stop to my home. The first bus route did not operate between the hours of 1:00 AM to 6:00 AM, and the second bus route stopped operations between 1:30 AM to 5:00 AM. A third bus route operated throughout the night, but it required that I walk over a mile and a half from the bus stop to my home.
Many times, because of the efficiencies of the job processes that I instituted, I was able to catch the 1:30 AM outbound bus, and usually, I was the only passenger on the bus. After a few times of this solo passenger travel, the bus driver and I struck up a conversation. The bus driver was always the same person, and he was someone that only had a few years remaining until retirement. He and I both enjoyed these conversations, and it made the trip less boring for both of us. One night the elevated train ride was delayed and did not pull into the station until 1:40 AM. I resigned myself to having to take the other bus route and walk a mile and a half from the bus stop to my house. Much to my surprise, I found the 1:30 AM bus still at the station. Upon boarding the bus, the bus driver remarked that he noticed that the elevated train was delayed, and he decided to wait a few minutes to see if I was aboard the delayed train. He commented that he was glad to do this and that he would continue to do this if he noticed the elevated train was delayed. I thanked him profusely, and we started on the bus route. When we neared the bus stop where I de-boarded the bus, he mentioned that he had observed me walking up the street, and he wondered how far I had to walk to get home. I informed him that I lived about a quarter mile directly on this street. He then informed me that after he reached the end of the bus route, about a quarter mile further on his route, he was finished for the night and that he proceeded directly to the bus terminal without making any stops. As I was always the last and often only passenger on the bus, he volunteered to turn up the street I was walking and deboard me in front of my home, from whence he could proceed directly to the bus terminal. He began to do this, and from then on, when I took his bus, I was dropped off in front of my home. I often think of his kindness and consideration to this day, and I try to reciprocate this type of kindness and consideration to others by offering rides to others when I obtained my driver’s license and purchased a car.
The Public Transportation Incidents
This public transportation also posed a danger to me on two occasions. As Joseph H. Cohen & Sons was located in the heart of North Philadelphia, which was a heavily black neighborhood undergoing the racial tensions of the time, I was often the only white person on the bus. This was no problem for the other non-white persons on the bus or me as we generally were indifferent to each other as typical of bus passengers. I even had a good experience when waiting for a bus at the intersection of two main streets one late Saturday morning. I noticed a young black man walking up the street in an obvious state of fatigue. He approached me and explained that he had been walking for several miles as he did not have the money to take the bus. He asked for a dollar to buy a soda at the nearby Mcdonald's restaurant to refresh himself. He was obviously sincere and very polite, and I reached into my wallet and gave him three dollars so that he could purchase a soda and burger and have enough money left over to take the bus. He profusely thanked me and proceeded to McDonald’s just as my bus arrived.
On another Saturday morning, an older black man approached me in an obvious state of inebriation, put his nose up against my nose, and announced that it was his lucky day as he was going to be able to beat up a whitey. I immediately kneed him in his crouch and ran for the safety of the Joseph H. Cohen & Sons building. I excitedly explained my situation to the guard that I was friendly with, and he immediately ran out of the building with his revolver drawn to confront this person. However, this person had run away after I had kneed him and could not be seen anywhere. The guard noticed that my bus was arriving, and he waited outside until I safely boarded the bus.
Another time as I was riding the bus on a Saturday morning, a young black man boarded the bus and noticed me. He came up to me and began verbally abusing me as the honkey on the bus. The bus went completely silent, and I stoically stared straight ahead and ignored him. After several minutes of his verbal abuse and my stoic countenance, he stated that the honkey was too afraid or cowardly to defend himself. He laughed at me, then found a seat further back on the bus. I immediately de-boarded the bus when it arrived at the elevated train terminal, and he remained on the bus.
The Theft
While working in the early morning one day, I was surprised to see one of the programmers arrive for work at 4:00 AM. He explained that he was finishing up a great effort and needed to do a number of compiles and testing, and he wanted to accomplish this expeditiously before the other programmers started their use of the computer. He started working, and I finished my tasks shortly after he arrived. After I finished, he proffered that I could leave for the day, and he could do his own complies and testing on the computer. Being very tired, I agreed to this as I knew that he had the knowledge and experience necessary to operate the computer as I had seen him do this several times in the past. I, therefore, left work for the day, and when I returned for my next shift, I was informed of a new policy that only computer operators were allowed to operate the computer. No explanation was given for this new policy, and no reprimand for my doing this came forth, as this was a common practice on the first shift.
That night, when I visited the guard, I discovered what had happened to bring about this new policy. After I had turned over the computer to the programmer and left work the previous day, the guard made his rounds of all the floors in the factory, as was his responsibility. He discovered the computer programmer in the finishing department loading finished suits through a window down to a partner who was placing them in a van parked on the street outside the window. He called the police, who caught both of them in the act, and they were promptly arrested for theft. The computer programmer was immediately fired when management arrived for work that morning. As this computer programmer had a wife and children, I can only presume that his foolish actions for a few extra bucks had many negative repercussions on his family. It also had repercussions on the business, as they had to change policies and procedures that impacted all of their employees and install additional security measures to guard against this and other types of employee theft.
I had never even considered stealing from anyone as I regarded it as morally reprehensible, and this incident demonstrated to me that theft from an employer was as morally reprehensible as theft from a person and often had negative repercussions not only on the thief and his family but also upon an employer and their employees.
Jerrold Electronics (Oct 1971 - Sep 1972)
Background
After quitting Joseph H. Cohen & Sons, I very quickly found a Senior Computer Operator job at Jerrold Electronics. Jerrold Electronics was a new and innovative company that supplied miscellaneous parts (mostly cables and connectors) to the fledgling Cable Television industry. Their business operation was located in Center City, Philadelphia, while their manufacturing facilities were located in Nogales, AZ.
I was hired for an unusual day shift from Thursday through Monday, as they needed a computer operator to process and print the weekly business reports and the next week's manufacturing schedule. Another Junior Computer Operator was on staff from a Wednesday through Sunday shift to support the weekend processing. This weekend's processing consisted of running the computer jobs and printing out dozens of reports that were utilized for business operations during the next week. These reports were printed out on multipart computer carbon paper, which required a decollation that was a slow and dirty process. This weekend task also entailed transmitting to Nogales, AZ, via a slow modem, the manufacturing schedule for the next week. This transmission was to occur at noon on Sunday, where they were printed out at the manufacturing plant and utilized during the week.
After a few weeks of doing this, I realized that this process was inefficient, and I therefore, utilized my skills and abilities to make this process efficient. I separated the processing and the print tasks into a Saturday processing and a Sunday printing. I was able to make the Saturday processing task run more efficiently, and it could be completed in seven to eight hours without the need for the assistance of the Junior Computer Operator. The Sunday printing process could be completed in six hours, but it took six hours to decollate the printed reports. For this Sunday's printing process, I needed the assistance of the Junior Computer Operator, especially in the decollation of the reports.
After several weeks of utilizing this efficient process, the Junior Computer Operator and I decided that he did not have to report for work on Saturday but only telephoned in to determine if I needed his assistance. We also decided that I would work on Sunday morning at 8:00 AM to begin the printing process and complete the noon transmission. He would come in at 10:00 AM to do all the decollation. This Sunday schedule would only require about six hours of effort on each of our parts. This went on for several months when we both decided that we were behaving unethically. We, therefore, informed the Computer Operations manager of our efforts to make the wend operation more efficient (however, we told a white lie that it had only been occurring for several weeks rather than several months). It was therefore decided that the Junior Computer Operator shift would be Sunday through Thursday while my shift remained the same. It was also decided that if we completed our task before the end of the shift, we could leave without repercussions.
For my efforts in making the weekend process more efficient, the other computer operators nicknamed me the “super operator”. A nickname that I enjoyed and was also given to me by the other computer operators when I was employed at Reliance Insurance.
In August of 1972, Jerrold Electronics announced that they were moving their headquarters to a suburban Philadelphia location. This was necessitated by Federal governments purchasing the land and building in which they were located for the expansion of the National Independence Hall historic site. As their new location was inaccessible by public transportation, and I did not own a car or have a driver’s license, it became necessary for me to find a new job.
The IMB 1400 Series Computers vs. the IBM 360 Series Computers
The IBM 1400 series were second-generation (transistor) mid-range business decimal computers that IBM marketed in the early 1960s, which were superseded by the IBM System/360 (S/360) family of mainframe computer systems that were available between 1965 and 1978. As the internal architecture was different between these two series, programs written for the IBM 1400 series computers would not function on the IBM System/360 computers. As a transition, IBM produced a special add-in (large) board for the IBM System/360 that could emulate the IBM 1400, allowing them to be run on the IBM System/360. The expectation was that businesses would expeditiously rewrite the IBM 1400 programs to work on the IBM System/360 computers.
As the head of the Jerrold Electronics computer department was an IBM 1400 series computer expert and did not fully understand the IBM System/360 computers, he delayed the rewrites. At the end of 1971, IBM announced that the IBM 1400 emulation board would be discontinued and removed from all IBM System/360 computers by July of 1972. This necessitated a mad rush to rewrite the IBM 1400 programs at Jerrold Electronics, which consumed the programming department resources for several months and delayed new projects or improvements to current programs. They succeeded in this transition but at a higher cost than if they had done this transition in previous years when they had the IBM 1400 emulator. This experience gives truth to the maxim-‘Don’t put off until tomorrow that which should be done today.’
The Incompetent Manager
The Computer Operations manager at Jerrold Electronics obtained her employment at Jerrold Electronics through nepotism as the supervisor of an all-female group of keypunch operators and was promoted to the position of Computer Operations manager when the current manager resigned. While she was very good at supervising the keypunch operators, she was only competent for the ordinary tasks of managing the Computer Operations. She exhibited little capabilities for anything other than the ordinary, and her largest deficit was in the personnel management of the small group of all-male computer operators. She often annoyed the computer operators with the interference of their mundane tasks or in the banter that occurred between a group of guys doing their job. As a result, she had little respect for the computer operators, and we would often do petty non-malicious things to make life annoying for her. In retrospect, we, the computer operators, did not handle this situation properly, and I regret my part in the petty non-malicious things that we did.
The Crying Game
One of the petty non-malicious things that we computer operators did was to stage fake verbal arguments between the computer operators that we all knew were fake. However, the Computer Operations manager did not understand that they were fake and became upset about these fake arguments. One fake argument occurred after the Computer Operations manager decided, for financial reasons, to reduce the number of card readers and printers from two to one each. This required more coordination between the computer operators for the utilization of the sole card reader and printer. This was not difficult to accomplish, but the first time we had a conflict, the two other computer operators and I started a fake argument to rile up the Computer Operations manager. This fake argument became so loud and protracted that the Computer Operations manager burst into tears and ran to the lady’s rest room to calm herself down. We computer operators realized that we had gone too far and apologized to her when she returned. We also reduced the fake arguments to less often fake jibes.
The Nogales, AZ incident
The person who received the Sunday transmission and printed the reports worked on a Sunday in which the manufacturing plant was closed, and all air conditioning and heating were turned off. On a hot summer Sunday, the room in which he worked became very hot, and he decided to remove all his clothing to alleviate the heat. A female guard who was patrolling the plant discovered him in this naked state and reported him to the plant manager. It was decided that they would install a room air conditioner, but it was also decided that they needed to fire him for his indiscretion. If he had informed them about the excessive heat, they would have taken remedial action and solved the problem, and he would have retained his job. A lesson is that one should speak up about problems when they occur rather than wait until the problem becomes intractable.
The Incompetent EAM Operator
In this era of computer processing, most of the input for the processing was done via punched cards, while the output was printed reports that were often on multipart paper with carbon between the parts. This required that the punched cards be sorted in order by the utilization of Electronic Accounting Machines (EAM) and the carbon copies be decollated for distribution to the appropriate departments, which was the responsibility of the EAM Operator. For large card decks, this process was fraught with errors. Cards could jam or be mangled in the EAM sorter machine, and if you did not do this process correctly, they would be sorted out of order. It was also a time-consuming and drudge job. Decollation was a dirty laborious job because of the length of the printouts and the number of carbon copies of the reports. Jerrold Electronics had an EAM Operator who did this job on a full-time basis, and he often made mistakes that required resorting to the card decks. In my reorganization of the weekend processing, I eliminated most of these errors by utilizing a utility program to load the cards into a disk file and running a sort utility program to get this disk file in the proper order. This disk file also speeded up the processing, as the program utilizing the cards did not have to wait to read a card to start the processing. Therefore, the need for an EAM was significantly reduced, and he was assigned other mundane tasks that he did not like. Consequently, he resigned shortly thereafter and was replaced with a clerical person who was trained to operate the EAM machines on a limited basis.
The Beautiful Secretary
The computer department and computer room were located on one half of the floor of the building, with a glass pane separating the computer room from the clerical operations area on the other side of the glass pane. Therefore, both the computer operators and the clerical staff were able to see each other. One day a manager of the clerical staff hired a new personal secretary who was a very lovely and shapely young lady. We computer operators often discretely ogled this young lady as she was very attractive. One of her jobs was to sharpen the lead pencils in a mechanical pencil sharpener located across the room from her desk, which she did early in the morning and after lunch. The sight of her walking to the pencil sharpener and her swaying as she turned the crank to sharpen the pencils was erotic. Upon discovering her routine, we computer operators set up an alert system when this occurred, and we would all gravitate to the glass pane to observe her performing this task. Upon the Computer Operations manager discovering this several weeks after the alert system was in place (the EAM operator let it slip to the Computer Operations manager), she informed the secretary’s manager, who reassigned this task to one of the male clerks in his department. Consequently, a brief but very pleasing interlude in our daily routine was at an end.
The View
The building in which Jerrold Electronics was located was very tall and positioned between Independence Mall and the Delaware River. From the roof of this building, you could see all the historical sites, the riverfront, and the center city of Philadelphia. As the building guard and I were the only people in the building on Sunday morning, and I had become friendly with the building guard as a result, when he was doing his rounds on a lovely Sunday morning, he would stop by and invite me to the roof of the building for about ten minutes to gander at the sights from the roof. This was the best view of Philadelphia I have ever observed, and I still remember it today.
Trilog Associates (Oct 1972 - Mar 1974)
Background
I decided to pay a visit to Trilog Associates, where my now sister's Father-In-Law, Mr. Smeltzer, was a co-owner, to determine if he had an interest in hiring me as I now was an experienced Computer Operator. Trilog Associates was a computer programming, computer operations and processing, and computer facility management firm for a medium-sized business that could not afford its own Computer department. They also had a large and profitable specialty line of business processing retirement plans for small businesses.
They were, indeed, interested in hiring me, as one of their current computer operators had just submitted his resignation. I, therefore, began working as a second-shift computer operator alongside another computer operator. When their business expanded and they needed a third shift, I became the lone third-shift computer operator while the second-shift operator began working by himself. Eventually, as their business continued to expand, a junior computer operator was hired to assist with both the second shift and, eventually, the third shift.
Don Devine - President of Trilog
The second shift operator that I started working with was a tall person (about 6ft, 3in), while I am about 6ft tall. One early evening we were standing together discussing the workload of the night when this shorter man (about 5ft 3in) walked into the computer room and announced, in his best John Wayne voice, that he was Don Devine, the President of Trilog. His John Wayne voice was somewhat amusing to us in that it appeared to be contrived. We had a short, pleasant conversation with him in which, towards the end of the conversation, his voice changed to a more normal tone. I learned from my Father-In-Law that he was a very intelligent person and an excellent businessperson, but somewhat self-conscience about his height. On occasion, I would pass him in the hallway, and we would both stop and have a short conversation which revealed that he was also a very nice person. These encounters reinforced my belief that you should never judge a book by its cover but get to know a person before making a judgment about the person.
Appendicitis
During my time at Trilog, I came down with acute appendicitis, which required an emergency appendectomy to remove my appendix and clean my abdominal cavity. The appendix rupture was so severe that they did not know for thirty-six hours if I would survive the peritonitis poisoning. After three days, I was released from the hospital but required five days of rest to recover. Upon returning to work my third shift, I was left on my own for a few days as the other operator took vacation time to recover from the extra effort of work that he undertook as a result of my absence. This was a strain on my full recovery, as I now had to bear the extra effort of working by myself for a week.
The Sleepy Elevated-Subway Train Ride
When I started working a Trilog, I did not own a car and took a one-hour bus and an Elevated-Subway Train Ride to work. One night I was particularly tired and fell asleep on the elevated Elevated-Subway car. I did not wake up until Elevated-Subway was at the end of the line. I thereupon crossed the platform to ride back to my stop. I again fell asleep and did not wake up until the Elevated Subway was halfway through its route. After crossing over to return to my stop, I again fell asleep and missed my stop. I yet again crossed over to return to my stop and yet again fell asleep until one stop after my stop. At this point, I exited the subway and walked eight city blocks to Trilog in the dead of night. Upon arriving two hours late, the second shift operator was upset I was so late but laughed when I told him the story of my lateness. I then decided it was time to obtain a driver's license and purchase a car which cut my commute to work to one-half hour.
The Printer Chain
The computer printers of the time utilized wide paper on sprockets that moved the paper forward. The printing mechanism was small hammers behind the paper that struck the paper as an inked spinning chain of characters passed by. This was a very noisy process that was muffled by an electro-mechanical hood that would rise to insert the paper and lower it when the printing began. One night the hood rose for me to insert another box of paper, which required that I pivot the automatically stopped printing chain away from the paper to add more paper. Unfortunately, the printer chain did not automatically stop, and when I began the pivot process, the chain broke and slashed my chest. Fortunately, I was far enough away to only receive a small bruise on my chest where it struck me. If I had been any closer, it might have resulted in a more serious injury to my chest. When the IBM Field Engineer arrived to fix the problem, he discovered that the optical sensor that controlled the printer chain had been dirtied by splashed ink and was not functioning properly. He, therefore, recommended that we add the cleaning of this optical sensor to our weekly preventive maintenance procedure to ensure that this would not happen in the future. He also forwarded this suggestion to the IMB Field Engineers' offices so that they would recommend this procedure to all customers that utilized this type of printer. As far as I know, I was the first person attacked by an IBM 1443 printer.
Falling Asleep at the Console
At the end of one busy night, when I was working alone, I started entering a command into the computer console when I fell fast asleep while entering the command. The Computer Operations Manager, Len Oberholtzer, arrived at his normal 7:30 AM to find me fast asleep at the console. After he woke me up, he insisted that I go home immediately while he finished the work. I gratefully accepted his instructions and left work immediately before the first shift operator arrived for work. He was the best Computer Operations Manager that I have ever worked for, and I followed him to his new Computer Operations Manager job at Reliance Insurance after we both left Trilog Associates.
The Marijuana Incident
Trilog managed the Computer Operation department of a small manufacturing business in Northeast Philadelphia, for which Trilog employed a full-time computer operator. This business shut down for one week of the year for vacation for all its employees. When this happened one year, the Trilog computer operator reported for work to assist the second shift computer operator at Trilog’s headquarters in Center City, Philadelphia. This computer operator enjoyed smoking marijuana during his break, which the regular second-shift computer operator tolerated. One late evening the President of Trilog walked into the computer room and smelled something he did not recognize. The computer operator quickly cupped his joint and claimed that he did not smell anything, whereupon the President of Trilog started sniffing the computer equipment to determine if anything was smoldering. Not discovering anything, he requested that the computer operators remain alert for any different odors to ensure that there were no equipment failures and exited the computer room. The joint smoking computer operation then immediately proceeded to the men’s room to flush the joint down the toilet. When he returned, the other computer operator informed him that there would be no more joint smoking in the workplace, including the workplace of the Computer Operations department of a small manufacturing business where he normally worked at. He agreed that this was for the best, and he promised that he would reserve his joint smoking outside the workplace.
The Incompetent Operator
When Trilog decided to add a computer operator to the third shift, they hired a young lady who was just laid off from a company that had gone bankrupt. Although her resume showed that she was fully competent to be a computer operator, she turned out to be unsuitable for the working environment at Trilog Associates. The problems that she encountered were that she had never been assigned to printer duties, as the weight of paper boxes was too heavy for her to handle properly. She also had difficulty handling the large input card trays due to their weight and length. As this was one of her main responsibilities as the junior computer operator, I had to divert my attention from my responsibilities to assist her in the paper and card tray efforts. She also came from a Union shop where her responsibilities were limited, and she had no computer console knowledge or experience. At the time, there were also workplace regulations regarding female employees. A female employee was permitted to take a thirty-minute lunch and a fifteen-minute break between the start of work and lunch, as well as a fifteen-minute break between lunch and the end of the day. She insisted on doing this, and for one hour during the third shift, she was unavailable as she retreated to the lady's lounge that Trilog had set aside for this female lunch and breaks. This impacted the third shift work efforts and shifted more duties and responsibilities upon me when I already had a full load of work. She also was somewhat careless in her duties and made mistakes that had to be corrected. I complained to the Computer Operations Manager about her work, but he informed me it would be difficult to let her go as she could claim sexual discrimination. It would take some action on her part that had a significant negative impact on Trilog to release her from employment. Fortunately, she provided this reason when, a few months into her employment, I assigned her the task of printing out the Certificates of Pension payments that Trilog processed for several of their clients. These were legal certificates due upon January 31st of the year for tax purposes of the recipients. They were also very expensive certificates, as they were custom printed and embossed computer paper. After she had printed out three boxes of these certificates, I discovered that they were misaligned and unsuitable for distribution to the recipients. As we had no extra boxes to reprint these certificates, we had to delay the distribution until we acquired new boxes (a process that took two days because they had to be custom manufactured due to their customized print and embossment). Upon explaining the situation to the Computer Operations Manager when he arrived that morning, he called her into his office and immediately terminated her employment. I was thankful that I no longer had this burden and hopeful that I never had to work with her again. Unfortunately for her, I ran into her again when I started a new job at PSFS (which I shall recount in the PSFS section of this book).
The Slowest Operator
Several weeks after terminating The Incompetent Operator, they hired a new computer operator to assist with third shift operations. Carlos was a good computer operator who I liked very much. His only problem was that he only worked at one speed—slow. This was not a problem once I realized and accommodated his slow speed into the workflow. We had no problems working with each other, which we did until I left Trilog Associates.
The Jewish Operator
A new (Jewish) computer operator, Carl, had been hired to assist with second-shift operations. I only mentioned that he was Jewish, as although he was a non-practicing Jew, he would take off all the High Holy Jewish holidays, and nobody had any problem with him doing so. It was the practice at Trilog Associates that they would close the company on Christmas Eve at 4:00 PM and not reopen until the 26th of December. One year they had an unexpectedly heavy workload for computer operation over the Christmas holiday. The Computer Operations Manager asked for volunteers to work the holiday and noted that he was sure that Carl would volunteer to allow his Christian brothers to be home with their families for the holiday. Carl reacted like a deer in headlights, but he volunteered to work extended time over the holiday to clear up the workload. Carl later related to me that he had party plans with his Jewish friends, but it was the right thing for him to cancel his plans and work over the Christmas holiday. I also volunteered, being single and without any family plans for Christmas (except an early dinner at my sister’s house), to come in Christmas night from 8:00 PM till 8:00 AM the next morning to finish up the extra work.
Howard Bryson
Howard Bryson was a senior programmer that had an interesting backstory which I learned from my sister’s Father-In-Law. Howard came from a lower-class family of five, in which his father suddenly passed away while Howard was a teenager. Howard dropped out of high school to help financially support his mother and siblings and went to work as a mail clerk at the Insurance Company of North America (INA), in which my sister's Father-In-Law, William Smeltzer, was the Vice-President of the Computer Department. Howard would deliver the mail daily to Mr. Smeltzer, at which time he and Mr. Smeltzer would have a conversation. Mr. Smeltzer soon realized that Howard was a very bright person who was capable of more than clerical work. Mr. Smeltzer then encouraged Howard to get his GED (on company time), and afterward, he arranged for Howard to attend programming classes at a local college. Upon the successful completion of these classes, Howard was promoted to a computer programming position, in which he demonstrated high skills and abilities. When Mr. Smeltzer left INA to found Trilog Associates, along with Don Devine, Howard followed him to Trilog, where he became an important factor in the success of Trilog. The most difficult programming assignments were assigned to Howard, for which he was always successful.
Howard was not only a brilliant computer programmer, but he was adept at mathematics and business economics. My Father-In-Law related a story about Howard that illustrated his brilliance. When an offer to purchase Trilog was made by a national company, the owners of Trilog needed to determine the value of the company to determine if they wished to sell Trilog. This was a difficult proposition at the time, as computer programming, computer operations and processing, and computer facility management service companies were uncommon and difficult to valuate. Trilog contracted with a large New York accounting firm to provide guidance to determine the value of Trilog. This accounting firm sent them a long and intricate formula to be used to evaluate the value of Trilog. At an owners-only meeting in the conference room to determine the value of the company, they wrote out this formula on the blackboard to fill in the variables of the formula. It became necessary for Howard to interrupt this meeting to obtain Mr. Smeltzer's signature on a contract extension for a critical change that needed immediate attention to resolve a serious problem. While Mr. Smeltzer was reading the language of the contract extension, Howard studied the formula on the blackboard. After about ten minutes, Mr. Smeltzer signed the contract extension and handed it back to Howard with instructions to immediately begin work on this problem. As Howard was leaving the conference room, he remarked to Mr. Smeltzer that the formula was incorrect, as one of the plus signs needed to be a minus sign for the formula to be correct. The other people in the room chuckled after Howard left the room, but Mr. Smeltzer hushed them and told them if Howard said there was a problem with the formula, that they needed to seriously consider that there was a problem with the formula. They, therefore, contacted the New York accounting firm to ask them to review the problem that Howard pointed out. A few hours later, the New York accounting firm called back and informed them that the formula was incorrect and it needed to be changed, as Howard suggested. Upon doing so, Mr. Smeltzer remarked that whatever Howard had to say was worthy of serious consideration, and Howard was invited to participate in the meetings on the valuation of Trilog Associates.
Bob Arguments
When I became the third shift computer operator, the second shift was manned by Bob, a thirtyish black man who was a very good computer operator. The second and third shift processing was a series of small jobs and a few larger, longer, running jobs. The smaller jobs required much physical effort to process, while the longer jobs generally required less physical effort at the start and the end of the process, with a few hours in-between of visually monitoring the process. After several months Bob started processing the longer jobs on his shift, leaving me the shorter jobs to process during the third shift. After a couple of weeks of this, I bitterly complained to Bob that he was being unfair to me by shifting the physical work to my shift while he had minimal physical work. We had a short argument about this, but Bob conceded that it was unfair for me to do most of the physical work. He, therefore, agreed that he would do two or three hours of the shorter jobs before he began the longer jobs and would leave me one or two of the longer jobs for the third shift. After a few days of this new arrangement, Bob apologized to me for his previous actions and thanked me for not bringing race into the argument (which I would never do). Of course, we would sometimes disagree about which shorter jobs he chose, but Bob conceded when I left Trilog that all of our arguments were never about race and only about choices.
Racist Ernie
The Computer Operations manager who hired me at Trilog Associates was an intelligent and congenial family man who was approaching middle age. He began to be concerned about his family’s future finances, and although Trilog Associates paid him well, he was concerned that he needed higher future income for college expenses and retirement purposes. He, therefore, found another Computer Operations Manager position with a large salary increase and larger retirement benefits at Reliance Insurance Co. After he left Trilog Associates, they appointed the senior first shift computer operator, Ernie, as the new Computer Operations Manager. Ernie was in his early thirties and a single black man. I never had much of a relationship with Ernie, as I was often leaving work when Ernie was arriving for work.
As the new Operations Manager, I needed to interact more often with Ernie, and I noticed that his attitude toward me was somewhat dismissive and impolite. After a month of this interaction, I discussed the situation with the second shift operator, who had worked extensively with Ernie when they both manned the first shift. Bob informed me that Ernie was a racist who hated all whiteys, which was one of the reasons he transferred to the second shift as he did not want to become involved in any possible future problems that this could cause. He also warned me that Ernie was going to make life miserable for me in the hopes that I would resign and that he could replace me with a black man. Ernie’s attitude towards me continued and worsened over the next few weeks, and after one morning of this abuse, I decided to take action. I walked the two blocks that separated Trilog Associates and Reliance Insurance to visit the old Computer Operations Manager at this new job. He greeted me warmly, and when I told him what was happening at Trilog Associates with Ernie, he expressed that he was not surprised as he suspected Ernie of racism. He informed me that he had no current position available but that he would create a position as he needed a person with my skills, talents, and work ethic at Reliance Insurance. The next day he called me and offered me the new position in Computer Operations that he successfully created to hire me. I, therefore, submitted my two-week notice to Trilog Associates and went to work for Reliance Insurance.
About a year and a half after leaving Trilog Associates, I attended the annual dinner with Mr. Smeltzer and his family, along with my family, as a celebration of the marriage of my sister and his son between our families. In a private conversation, I inquired how things were going at Trilog Associates, and more especially about the Computer Operations. He informed me that they had problems with the Computer Operations as Ernie had managed to alienate all the Computer Operations except the black second shift operator, who immunized himself against Ernie. All the other computer operators had resigned at different times, and Ernie had only hired black Computer Operators to replace them. It turned out that they had problems with three of the replacements, as one was incompetent, one was too inexperienced for the job, and the other had a lackadaisical attitude. The other two replacements were well suited for the job, and they had no problems with them. He further informed me that they terminated Ernie’s employment because of these problems, and they had found a new Computer Operations Manager, with which they were very happy.
Reliance Insurance (Apr 1974 - Nov 1975)
Background
One morning, after I had had enough of Racist Ernie, I walked to the office of my former Computer Operations Manager at Reliance Insurance to see if they would be interested in hiring me. While they had no computer operator position available, my former manager was so desirous of hiring me that he swiftly arranged for a new computer operator position, for which I was hired at the top salary for a Senior Computer Operator.
Reliance Insurance was a provider of different lines of insurance that had an extensive Information Technology (IT) Department (a new term coming into vogue for Computer Departments) to support each line of business. They had three IBM Mainframe computers to accomplish this processing, with each computer having six tape and disk drives, along with a punched card reader and computer printer for each computer. They also had about sixty IT personnel to support the IT Department. This was considered a large IT department for the times.
Unbeknownst to the new Computer Operations manager (my former Computer Operations Manager at Trilog Associates), the senior business management at Reliance Insurance was becoming dissatisfied with the senior IT management, as they felt that the IT management was becoming unresponsive to the needs of the business, and rather stodgy in their approach to modern IT. The senior business management undertook a search for a replacement for their senior IT management and discovered that the IT management at the Food Fair Supermarket was considered innovative and forward-looking. As Food Fair Supermarkets had very recently declared bankruptcy and was shutting down operations, the senior business management of Reliance Insurance hired the entire senior IT management of Food Fair Supermarkets as a replacement for their old IT management team. Many of the previous IT senior managers were laid off, but a few remained as ‘consultants’ with no real responsibilities. Unfortunately, the new Computer Operations manager with whom I had worked at Trilog Associates was one of those who were laid off. I was saddened by this as I knew that he was a good man who could have done a good job for the new IT management, but they had their own Computer Operations manager that they brought with them. I do not know what happened to him after he was laid off, but I certainly hoped that things worked out well for him and his family.
The Conversion – Part I
One of the first things that the new computer management team undertook was an evaluation of the current computer operations processing and the large programming projects that were underway. This evaluation discovered three immediate areas of improvement that were implemented as soon as possible.
The Large Programming Project
They discovered a large programming project that was unrealistic in that the computer operations processing would take an exorbitant amount of computer time to accomplish. As a result, this large programming project was halted, and other options were considered. Another option was discovered that would accomplish many of the goals of the original large programming project which was undertaken. This large programming project goal was to compare their insurance salespersons' revenue against their insurance claims to determine the profitability of each salesperson. After this project was completed and processed, they discovered that the salespersons with the most revenue generated had a disproportionally large number of claims against their policies. As a result, the salespersons that they previously thought were the best salesperson turned out to be the worst salesperson when judged by profitability. This led Reliance Insurance to reorganize and lay off many salespersons to focus salespersons on profitability rather than just sales.
The Reorganization of Computer Operations
The evaluation also discovered that Computer Operations were heavily dependent on overtime to meet the needs to process all jobs required during the week. They, therefore, reorganized Computer Operations to operate on six days a week schedule. The new shift arrangement was of four shifts – each shift being twelve and a half hours apiece. There would be a Monday through Wednesday day and night shift and a Thursday through Saturday day and night shift, with Sunday operations, if needed, being covered through volunteer overtime. Each shift would have six computer operators, three of which were senior computer operators responsible for the computer console operations and disk drives, and three junior computer operators responsible for the tape drives and the punched card and computer printer operation. One of the senior computer operators would be designated as the shift leader responsible for all the activities in the computer room. Additionally, they had a printer decollator and odd jobs trainee assigned to each shift. There were a few other support personnel who worked Monday through Friday on traditional nine-to-five shifts. It was also decided that the Monday through Wednesday shift and the Thursday through Saturday shift would be swapped every six weeks to not consign the computer operators to constant weekend work. This meant that every six weeks, the Monday through Wednesday shift would have seven days off at the swap, while the Thursday through Saturday shift would only have one day off at the swap. Everybody liked this arrangement as every twelve weeks you had a week off, balanced by every twelve weeks only having one day off.
The Upgrade of Computer Operations
In this era of IBM Mainframe computing, there were two different Operating Systems (OS) that controlled the processing of the computer—The Disk Operating System (IBM DOS), which allowed for two concurrent processes to run simultaneously, and the Operating System (IBM OS) that allowed for multiple concurrent processes to run simultaneously. Each type had a different Job Control Language (JCL) and Computer Operations Console commands. The IBM DOS was a very good (and less expensive) Operating system for smaller and medium-sized businesses, while the IBM OS Operating system was best for medium-sized and large businesses. Reliance Insurance was utilizing the IBM DOS Operating systems on its two IBM Mainframe computers. The new computer management team decided to lease (IBM Computers were not purchased but leased from IBM) the newest and best IBM Mainframe computer with IBM OS to begin the modernization of computer operations. In addition, programs that were written for the IBM DOS needed to be modified to work with IBM OS to function properly, and the JCL for the modified programs had to be redone. As I was the only computer operator familiar with both IBM DOS and IBM OS, I bore much of the responsibility for the JCL redo, as well as training the other computer operators in IBM OS JCL and the Computer Operations Console commands. As a result of my skills and abilities in IBM OS, I was assigned to the 8:00 PM to 8:30 AM shift, where I would most be needed to fix any problems that arose.
The Mad Rush
The new computer was a dual boot machine as it could be started up with the IBM OS or IBM DOS operating system. During the day, the new computer operated as an IBM OS machine so that the computer programmers could compile and test the programs that were being converted. At night it was booted into IBM DOS so that the daily production jobs that had not been converted could run on the new computer. Sometime in the morning, it would be rebooted into IBM OS for the programmer’s utilization. This resulted in a mad rush by the programmers to have their jobs run on the computer, as illustrated by the following humorous situation drawn by a Computer Operator with an artistic bent:

The Listing Doesn’t Lie
During the conversion process from IBM DOS to IBM OS, the programmers who needed to convert their programs often had difficulties in doing so because of their lack of knowledge or unfamiliarity with the IBM OS. When they encountered difficulties, they would consult with the Operating Systems Programmer who was responsible for maintaining and configuring the IBM DOS and IBM OS of the three computers at Reliance Insurance. This Reliance Insurance Operating Systems Programmer had a hard and fast rule that he would apply before providing any assistance. When the programmer approached him to explain their problem, he would not listen to their problem unless they had the computer listing that showed the problem, exclaiming, ‘The Listing Doesn’t Lie’. This exclamation taught the programmers not to approach him without the listings that showed the problem. When I was assisting him with a thorny problem, he explained that too often in his past, he would provide assistance without the listings, and this often resulted in not solving the problem. He, therefore, concluded that there was nothing like the cold hard facts of the computer listing to solve the problem, and without the cold hard facts, the problem would probably not be resolved, which I adopted whenever I assisted the programmers with their JCL problems. I also generalized this approach to all the problems I encounter in all of life—without cold hard facts; a problem could not be properly resolved.
The Vicki Incident
At the end of the conversion to IBM OS, and after the new management team at Reliance Insurance left for greener pastures, the old management team was reinstated. We also started to encounter minor programming problems with the converted programs during the night shift that were not correctable until the next morning when the programmer started work. This became unacceptable, as these problems were negatively impacting the business operations of Reliance Insurance due to a lack of computer reports that were not available because of these problems.
The computer management team decided the best way to address this situation was to have a computer programmer on-site during the early part of the night shift to make emergency corrections to the programs to get them to work. They, therefore, asked for a computer programmer to volunteer to work a shift of 02:00 PM to 11:30 PM Monday through Thursday, which gave them the benefit of a three-day weekend. Only one programmer volunteered to do this—a single young attractive woman, Vicki, who had an interesting backstory about her employment at Reliance Insurance.
Vicki grew up at her aunt and uncle’s house, who were childless, and after her parents were killed in an automobile accident when she was a young child. The house she grew up in was next to the vice-president of Reliance Insurance's computer department, and both he and his wife were also childless, and they became a surrogate aunt and uncle to Vicki. Vicki became interested in computers as an adolescent because of her association with her surrogate uncle and went to college and obtained a degree in Computer Science, whereupon her surrogate uncle hired her as a computer programmer at Reliance Insurance. This was not nepotism, as Vicki was a very good computer programmer. However, everybody in the Computer Department knew of her relationship with the head of the computer department at Reliance Insurance. They also knew that her surrogate uncle was very protective of Vicki, and everybody else was also protective of Vicki.
After Vicki volunteered, she was met with resistance by her surrogate uncle, as he was concerned that her train ride home would be dangerous, as the center city underground train station was the scene of homeless beggars, several muggings, and even rape and murder after the evening rush hour traffic. Vicki really wanted to undertake this assignment as she (rightfully) believed it would be advantageous to her career. It was decided that she would be assigned to this task with one proviso—a computer operator would escort her to the train station and remain with her until she boarded the train—a task that we computer operators nicknamed the “Vicki Duty’. The Vicki Duty was assigned to a computer Operator who was least busy when it became time to escort Vicki to the train station.
One Thursday night, after several months of Vicki Duty, it was I who was assigned Vicki Duty. This duty was accomplished without any difficulties, and I returned to work knowing that Vicki was safe aboard her train and that she was planning to visit her Aunt and Uncle, who she had not seen in several months, to enjoy her three days off. The next morning, after I had gotten home and started to sleep, I received a telephone call from the Computer Operations Manager, asking if I knew what had happened to Vicki, as she had not made it home and her apartment mate was concerned about her safety. I assured the Computer Operations Manager that Vicki had safely boarded the train, and I informed him of her plans to visit her aunt and uncle.
That evening when I went to work, I asked the day shift computer operations supervisor what happened to Vicki, whereupon he laughed and told me the story of Vicki’s disappearance. After they had talked to me, they called Vicki’s aunt and uncle to determine he she had gone to their place, which she had not. Her roommate then called the police to report a missing person, but the police informed her that as Vicki was an adult, she would have to be missing for over twenty-four hours and be reported so by a relative. At this point, Vicki’s roommate, her aunt and uncle, the Computer Department head, and Vicki’s manager became very concerned about her safety. They all met at Vicki’s apartment to discuss and determine what they could do to locate Vicki, as it was now late morning and Vicki had not shown up. As they were all sitting in the living room of Vicki’s apartment, she stumbled in through the front door, bleary-eyed, obviously hungover, and not cognizant of who was in her apartment. Vicki’s roommate ran up to her and exclaimed, “Vicki, where have you been? I was worried about you.” Vicki then blurted out that she had gone to a local bar after work, met a good-looking guy, and spent the night and morning screwing each other at his apartment. She then exclaimed that she was sore and tired and she needed to go to bed, which she promptly did without realizing who else was in the apartment. Needless to say, all the others were chagrined by what had happened, and they left Vicki’s apartment.
The next Monday, the Computer Department Manager announced that it would no longer be necessary for a computer programmer to be on-site after hours, and any problems that were discovered would have to be resolved early the next morning after the Computer Operations Shift Supervisor telephoned the programmer to alert them that they needed to arrive early to fix the problem. Vicki, meanwhile, barricaded her cubicle with empty computer paper boxes for the next week or two to avoid the awkwardness of the situation. Of course, being a protected person, nobody said anything to her or to each other about this situation, and things returned to normal in short order.
The Mainframe Stoppage
One morning, as I was leaving work, the IBM Field System Engineers showed up to do Preventive Maintenance and a major IBM OS upgrade on the newest Computer. This would require that the computer be unavailable for normal processing for the entire morning, and some of the normal workloads would have to be made up that evening. This happened at least twice a year and sometimes more often, and there was little difficulty in accommodating them as it was a necessity. As I was scheduled to be the shift supervisor that night, as the normal shift supervisor needed the night off for personal reasons, I need to be aware of this and plan for an additional workload that evening. When I arrived that evening, I discovered that the IBM Field Engineers were still at work and the computer doors were open, and various diagnostic equipment was attached to the computer. The day shift supervisor informed me that after they did the IBM OS upgrade and rebooted the computer, it would simply stop in the middle of the reboot. They had been working all day to resolve this problem without being able to correct it.
After three hours without success on my shift trying to correct this problem, I called a halt to their efforts. In my previous employment, I had the opportunity of working with a Senior IBM Field Engineer, Dominick, fixing a problem on another computer. Dominick was so respected for his knowledge and skills that he was somewhat of a tolerated IBM engineer in that he did not have to show up at the client site in the mandatory dark suit and on time as required of all IBM field engineers visiting a client site. I told the two IBM Field Engineers that I wanted Dominick to be called in to fix this problem. They hemmed and hawed at this request and made excuses that he was unreachable at this time of night. Whereupon I informed them that I had Dominick’s home phone number, which he had given to me when we were working together to solve the other computer problem. I then called Dominick at home and explained the problem, and he agreed to come in immediately to assist in solving this problem. About an hour later, Dominick showed up in a Bermuda shirt, shorts, and sneakers without socks to assist in the resolution of this problem.
The IBM Mainframe computers of this time had a series of lights, switches, dials, and buttons on their front plate to assist in determining the status of the computer and to assist in diagnostics of problems. Dominick stood in front of the computer's front plate and had the other IBM Field Engineer depress the reboot button to observe what happened. After a few seconds, when the computer stopped, he reached over and flipped a switch, then he rebooted the computer successfully. Dominick admonished the other IBM Field Engineers that they had turned on the memory address stop switch of the dial settings, which stopped the computer from rebooting then the memory address was accessed. He then turned around and left the building to the chagrined expressions of the two IBM Field Engineers. I then instructed the IBM Field Engineers to remove the diagnostic equipment and restore the computer to me so that we could get our work done. I also informed them I would not sign their work order unless they noted that there would be no charge for the twelve hours they worked to correct a non-existent problem, which they did. A non-existent problem from which I learned to check out the obvious before delving into the obscure, which stead me well in my future professional career and personal life.
The Power Failure
The new computer management team also discovered that the computers were powered by the building's electricity with no backup if the building's electrical system had a problem or failed. This was unacceptable as in the event of a power spike, brownout, or blackout, the computers and the attached computer equipment would instantly power off, which had the potential of damaging the computers or the attached computer equipment. It would also mean that the business reports necessary for the business operation of Reliance Insurance would not be available the next business day.
They, therefore, decided to install an Uninterruptable Power Supply (UPS) for the computer room. Given the electrical demands of mainframe computers, this UPS had to be a gasoline-powered generator with serious battery reserves, the batteries being used to power the computer while the generator powered up (about 20 seconds). This UPS could provide the electricity needed by the computer room in the event of a power blackout or brownout. It was also an expensive proposition to purchase and install a UPS of the size needed for their computer room. They appropriated a rather large closet on the same floor as the computer room and had a UPS knowledgeable and experienced independent contractor install and connect the UPS, which was successfully accomplished. A few weeks after this was done, the building had an electrical failure because of the electricity company having a failure. The UPS successfully did its job, and we continued to operate the computers during the building blackout, which lasted several hours. However, twenty minutes after the building blackout, the UPS stopped working, and the computers and computer equipment powered down, along with all the lighting in the computer room. The UPS independent contractor was alerted but was unable to come in until the early morning to discover the problem with the UPS equipment. The building's electricity was eventually restored, and we were able to determine there was no computer or computer equipment damage. We were able to restart the running computer jobs to the beginning of their processing and deliver the computer reports later in the morning.
When the UPS independent contractor arrived, he was able to immediately pinpoint the problem. The UPS was installed with a one-gallon gasoline tank as it was illegal to have more than one gallon of gasoline in an office building due to the potential fire hazard of large gasoline storage in an office building. It was the responsibility of the company that hired the UPS independent contractor to contact the local fire company to determine how and where to locate a large gasoline tank (most companies install the UPS in a parking lot many yards away from the office building). Reliance Insurance had not carefully read the contract with the UPS independent contractor, which explicitly stated this requirement. A lot of fingers pointing ensued between the computer department, the building engineers, and the company lawyers as too had fallen down on the job, but Reliance Insurance executive management blamed them all for not communicating with each other.
The next problem was where to locate the large gasoline tank, as it had to be at a higher elevation than the UPS equipment, so the gasoline feed was done by gravity when no electricity was available for pumping purposes. Reliance Insurance decided to locate the large gasoline tank on the roof of the building and run a fuel tube from the tank to the large UPS closet. When they approached the fire marshal for approval of this plan, he balked at this idea. He was uncomfortable having a large tank of gasoline on top of a building where if it caught on fire and exploded, it would be like a bomb going off. After much negotiation, he finally agreed to this plan on the condition that the large gasoline tank was elevated by a steel tower twenty feet above the roof, where it would do minimal damage if it exploded. The next problem was how to fuel up this large tank on top of a tall office building and on a steel tower. It was decided that on a Sunday, under the supervision of the fire marshal, the building would be evacuated, and twenty-gallon sealed gasoline barrels would be transported to the freight elevator. These barrels, one by one, would be elevated to the roof, where they would pump up the gasoline into the tank, then the empty twenty-gallon barrels were freight elevated down to the truck when the next full barrel would make the trip. This process took most of the day and was carefully supervised by the Fire Marshall, who also instituted a three-month inspection cycle of this fuel tank to determine if any problems had occurred with the tank, the steel tower, or the fuel line in the preceding three months.
The Tape Drive Dismounts
In modern computing, disk drives are ubiquitous, while tape drives are almost non-existent today. Such was not the case at the early age of Mainframe Computing. Disk drives were of very limited capacity and very expensive, while tape drives were much less expensive, and individual tape reels were relatively inexpensive. In addition, tape reels could store vast amounts of data, and the data could span across multiple tape reels. The operation of the tape drive was that there were two spindles in tape drive. The left spindle was for the feed of the tape reel, while the right spindle was for the take up of the feed tape reel, and between the two spindles was an electromagnetic read-write head. The computer operator would mount the tape on the left spindle and feed the tape through the read-write head to the right spindle, which had an empty tape reel, which the computer operator spun around the hub of the empty reel to grip and tighten the tape. The computer operator would then depress the load button on the tape drive, and a glass window would rise up to seal the tape from dust and dirt contamination. When the tape drive finished reading or writing the tape, it rewound the tape at high speed onto the left spindle, and when finished, it would automatically lower the glass window for the computer operator to remove the tape reel from the tape drive. At any time in this process, the computer operator could depress the stop button to halt the reading or writing of the tape reel and then press the unload button to rewind the tape and lower the glass window. This manual dismount was necessary when there was a failure of a read or a write to the tape reel that caused a loop of the read/write process, which required computer operator intervention to resolve (it also aborted the job, which then needed to be rerun).
When Reliance Insurance leased the new IBM computer, they purchased a bank of tape drives from a third-party manufacturer that was less expensive and faster than IBM Tape Drives. For many months there were no problems with these tape drives, but one day at 7:00 AM, all the tape drives suddenly stopped and automatically dismounted the tapes. This was worrisome, but a diagnostic did not reveal any problems. The next morning the same thing happened at 7:00 AM while I was observing the tape drive from the computer operator console. This caused consternation, but again, a diagnostic did not reveal any problem. The next morning, I decided to stand to the side of the tape drive bank to observe the tape drives if this should happen again. While doing so, I observed a flash of light immediately before it happened again.
Being an amateur astronomer and of a scientific bent mind, I tried to discern how this flash of light occurred and how it could affect the tape drives. I soon realized that the tape librarian arrived at work at exactly 7:00 AM, and the automatic doors with windows opened to admit her to the computer room. I also realized that the sun was rising above the horizon of the buildings to the east, and the sun’s rays through the outside window were being reflected onto the tape drives from the windows of the automatic doors. I then consulted the technical reference manual for the tape drives and discovered that the rising and lowering of the tape drive glass window was controlled by an optical sensor rather than an electromechanical action. The flash of light was activating the optical sensor of the tape drives and forcing a dismount of the tape drive. The immediate resolution to this problem was to close the blinds of the outside windows so that this reflection did not happen. The permanent solution was that the third-party manufacturer mounted a polarizing filter in front of the optical sensor so that no external light source did not activate the dismount on the tape drive.
Air Conditioner Failure
One early morning I was walking behind the tape drives of the secondary computer, which had a three-foot gap between the tape drives and the air conditioner units. As mainframe computers and the equipment attached to the computers generate much heat and noise, Reliance Insurance had a bank of huge air conditioners against the building wall to ventilate the heat and cool the entire computer room, which also contributed to the noise of the computer room. As I was walking, I noticed that my feet were sloshing in a puddle in front of one of the air conditioning units. Upon opening the door to the air conditioning unit, I discovered that a water pipe had sprung a heavy leak at the joint between the water pipe and the air conditioner. Upon raising a tile of the elevated floor (all computer rooms had elevated floors so that you could run the cables connecting the computer and the computer equipment as well as the electrical lines to power the computer and the computer equipment), I noticed that there were about three inches of water between the building floor and the elevated floor (this leak must have been occurring for many hours to build up so much water on the building floor).
We immediately shut off the water line to the air conditioner unit and notified the building engineer, then finished the current jobs running on the computers and power offed all the computers and the computer equipment to prevent an electrical short. The building engineer called a plumber to repair the leak while he arranged for water pumps to be delivered to pump the water outside of the building. This took several hours to accomplish before we could power up the computers and the computer equipment to continue our work.
The next night, when I arrived at work, the day shift computer operation supervisor told us what happened the next morning because of the water leak. Apparently, the water had not only leaked onto the building floor, but it had also leaked through the building floor onto the suspended ceiling of the floor below. At about 10:00 AM, the suspended ceiling came crashing down and drenched the (mostly) female clerks working below, as well as scattering debris of the suspended ceiling onto the desks, filing cabinets, and flooring below the suspended ceiling. He described the results as like a wet tee shirt contest for the clerks and a rubble of debris over the entire floor below. The clerks were allowed to go home for the day while a clean-up crew removed the debris, and a new suspended ceiling was installed.
The Uptight Computer Scheduling Administrator
Reliance Insurance employed a computer operations scheduling administrator, whose job was to ensure that all scheduled jobs were ready to be processed by the computer operators. This meant that all the tapes, punched cards, and special pre-printed forms were organized by the job and ready to be processed by the computer operators. He was also responsible for ensuring that sufficient supplies of blank tapes, blank punched cards, and pre-printed forms were in stock to meet future needs.
While he was very competent in his job, he was an uptight person who insisted that rules and regulations be adhered to by all who worked in computer operations. This did not go over well with the computer operators as they wanted discretion on what, how, and when in the performance of their duties and responsibilities.
On the Saturday night shift, we often finished our work before 8:00 AM, and half the staff would be allowed to leave work early. The other half stayed at work to finish up the odds and ends that remained. During this period of relative inactivity, the remaining staff would down a few cold beers, which we purchased and stored near the air conditioner units to keep them cool, and played cards and drank no more than two cold beers during our card playing. When the uptight computer operations scheduling administrator discovered we were doing this, he went apoplectic and complained bitterly to the Computer Operations Manager.
When the Computer Operations Manager investigated this, he determined that no harm was being done, and it was good for the morale and the comraderies of the computer operators. He only cautioned us to limit our intake of beer and to ensure that all work was completed properly. The uptight computer operations scheduling administrator was not happy with this resolution and continued to complain to the Computer Operations Manager. Finally, the Computer Operations Manager had had enough of these complaints and directed the Saturday night shift supervisor to gather the empty beer cans and put them into the lower left drawer of the uptight computer operations scheduling administrator desk. He would show up at the uptight computer operations scheduling administrator's desk at 8:00 AM the next Monday and ask for a report from the uptight computer operations scheduling administrator, which he knew was in the lower left drawer of his desk. When the uptight computer operations scheduling administrator opened the drawer with the empty beer cans, he was aghast, and the Computer Operations Manager commented that the computer operators were not the only ones drinking beer on the job. He sputtered out a denial, and the Computer Operation Manager cut him off and told him to stop his complaining, or he would take more drastic action to end his complaints. Whereupon the uptight computer operations scheduling administrator never uttered another complaint about this situation.
The Incompetent Computer Operator
Reliance Insurance has a hierarchical structure for computer operators. The Shift Supervisor was responsible for all the activities in the computer room, while the Senior Computer Operator was responsible for the newest computer console operations and providing directions to the computer operators assisting him and assuming the responsibilities of the Computer Shift Supervisor when he was absent. Two Junior Computers were responsible for the two older computer console operations and providing directions to the Computer Operators assisting them. The Computer Operators were responsible for mounting and dismounting the tapes and removable disk drives, as well as the operation of the card readers and printers. A Computer Operator Trainee assisted the Computer Operators in their duties and responsibilities while they learned how to do the job of the Computer Operators. In practice, everybody helped each other in their job as the need arose.
One of the computer operators on staff was competent in operating the card readers and printers and barely competent in mounting and dismounting tapes. This was a drag on the smooth operation of the computer room operations, but we could not lay him off as the Personnel Department would not allow it if he performed within the letter of his job description. We, therefore, had to put up with him and made sure he was not assigned to any tasks that we knew he was not competent to achieve. One Saturday night shift, when all but one job was completed, we allowed the other computer operators to leave early, leaving only myself, the shift supervisor, the EAM operator (who needed to decollate the computer printouts), and the incompetent computer operator present. We sat the incompetent computer operator in front of the computer console and instructed him that if any message appeared on the console, he was to come and get us in the EAM room, where we were playing cards and enjoying a beer.
While the shift supervisor and I were playing cards and drinking beer, I thought I heard a strange sound coming from the computer room. The shift supervisor did not hear it, but we paused to determine if it occurred again. After a minute, the sound occurred again, and we both heard the sound. While we were trying to figure out what the sound was, we heard the sound for a third time. It was then that I realized that the sound was of a removable disk drive crash. A removable disk drive crash occurs when the movable read-write head strikes the magnetic platter causing the destruction of the read-write heads and the platter. We immediately rushed into the computer room to determine what was happening. We discovered that the incompetent computer operator had read a message on the computer console that informed him of a read-write error on one of the removable disk drives and to remove the removable disk and place it into another drive. Rather than coming to inform us of this message, he took it upon himself to move the damaged removable disk to another drive where it damaged the read-write head of that disk drive. He did this a third time and was just completing this action on a fourth removable disk drive, which he also succeeded in damaging.
Removable disk drives and disk packs were expensive pieces of equipment (about twenty thousand dollars per removable disk drive and five thousand dollars for a removable disk pack). The incompetent computer operator had managed to damage twenty-five thousand dollars in computer equipment. We immediately told the incompetent computer operator to leave work and report back on Monday morning when we had to explain what had happened to the Computer Operations Manager. In the meantime, we called the service and repair technician from IBM to fix the damage. When we informed the IBM technician what happened, he informed us that this was not covered under warranty for the equipment, except for the first read-write head replacement, which was covered under warranty. We had him repair the damaged read-write heads and replace the removable disk drive at the cost of about twenty thousand dollars, as the read-write heads were five thousand dollars each to replace and reinstall.
On Monday morning, the Shift supervisor and the incompetent computer operator showed up at the start of the shift to explain what had happened and the costs of repairing the damage. The Computer Operations manager was upset that we allowed the incompetent computer operator to sit in front of the computer, but he was irate that the incompetent computer operator did not follow the instruction to inform us if any message appeared on the computer console. The head of the Computer Department became livid when he was informed about this incident, as he had tried to get this incompetent computer operator fired without success a few weeks before this incident. He, therefore, escorted the incompetent computer operator to the office of the head of Personnel Management and informed the head of Personnel Management that this incompetent computer operator was never to be allowed anywhere near the computer room again. The head of Personnel Management then decided to lay off this incompetent computer operator with two weeks' severance pay and escorted him out of the building. I learned that incompetence could rear its ugly head in unexpected times and places and that you should never tolerate incompetence, as it will always come back to bite you.
Emergency Evacuation Procedure
The new management also instituted an Emergency Evacuation Procedure in the event of a fire or other disaster that could affect the computer room. This was a thirty-step procedure that could take up to thirty minutes to accomplish, with the thirtieth step being to safely evacuate the building through the emergency escape stairwell. The computer operators laughed when they read this Emergency Evacuation Procedure and joked that there should be a zero step that directed you to immediately proceed to step thirty. We were all cognizant of our responsibility to protect the computers and computer equipment, along with the tapes and removable disk packs, but in a disaster, we would be more concerned with our own health and safety and would first do whatever was necessary to preserve our own health and safety. About a year after I resigned from Reliance Insurance, I learned that they did have a fire in the computer room, and the Emergency Evacuation Procedure was helpful in protecting the computers and computer equipment but not very helpful in protecting the tapes and removable disk packs, as they could not be transported to a safe location in the time before the fire reached the tape library.
My Extended Vacation
When it came time for me to take my two-week vacation, I discovered a loophole with the three days a week 12 hours per day schedules. I realized that if you take a one-week vacation before the switch between Monday-Wednesday to Thursday-Saturday, then take a one-week vacation after the switch, you would have three weeks of vacation before returning to work. I further noticed that the Monday Memorial Day holiday occurred on the last week of my Monday-Wednesday shift. As we had off on Memorial Day, and if I took off Tuesday and Wednesday as personal time, I would have four weeks’ vacation before returning to work. Without telling anyone of this discovery, I arranged to take my vacation and personal time around this loophole. On the last day of my work before my four-week vacation, as I was leaving work, I informed my Shift Supervisor that I would see him in a month. He was startled by this comment, and when I explained the loophole that I had found, he laughed and congratulated me on my discovery. When I returned from my four-week vacation, my Shift Supervisor informed me that a new policy regarding vacation time for Computer Operators had been instituted that closed this loophole. I, therefore, would be the only Computer Operator that took advantage of this loophole.
The Employee Association
Reliance Insurance had an Employee Association that arranged a summer Entertainment Park picnic and a winter weekend at a Pocono Mountains Ski Lodge. Because the Computer Operators were somewhat isolated from the rest of the employees, we were often overlooked for the invitations to the picnic and ski trip. Upon the Computer Department Employee Association representative discovering this, she made a concerted effort to invite the Computer Operators to the Ski Lodge trip.
She approached me one morning before the weekend of the Ski Trip to extend a personal invitation to me, which I had little interest in attending as I was not a skier. She persisted and tried to entice me, as many of the employees who went on this trip did not ski but utilized the time as party time. She also informed me that the cost was very modest as they had a special deal with the Ski Lodge. Upon my continued demurral, she also informed me that the rooms were double occupancy, and if I did not have anyone to share the room, she could arrange for an attractive single young lady to share the room with me (she made it apparent that it was common for the single guys and gal employees to do this on the Ski trip). Feeling uncomfortable about this arrangement, I informed her that I was scheduled to work this weekend (true), and furthermore, I was to be the Shift Supervisor this weekend (untrue). She then ended the conversation and continued to extend her personal invitations to the other Computer Operators.
The Head Injury
Early one Sunday morning, when all the work had been completed except for one long print job, I volunteered to stay to complete the print job while everyone else left early. About an hour later (at approximately 3:00 AM), I was straightening out the paper at the rear of the printer (a common task when printing a long report). Unbeknownst to me, because of the noise level in the computer room, the printer hood automatically rose as it had run out of paper, and a new paper box needed to be inserted to continue the printing job. I stood up after straightening out the paper and violently hit the corner of the printer lid in the center of the top of my head. This collusion knocked me dazedly to the floor. When I put my hands on the top of my head, they felt warm and wet, and then when I looked at my hands, they were all bloody. I immediately went to the men’s room and put cold, wet paper towels on my head for a few minutes. When the bleeding did not completely stop, I decided to visit the Emergency Room at Hahnemann Hospital, which was a very short walk away.
Upon arriving at the Emergency Room, they gave me a cold compress to place on my head and instructed me to wait until more serious emergencies were attended to. Little did I know that the Hahnemann Hospital Emergency Room was the designated emergency room for the center city police and fireman to bring in people who require medical treatment. For the next two hours, I watched a parade of injuries troupe through the Emergency Room. After two hours, they treated me, and I needed several stitches to close the wound on my head. They then instructed me to go home and rest and recuperate from my injury.
I telephoned my Shift Supervisor at his home, woke him up, and explained the situation, and he agreed to meet me in the Computer Room to finish the printing job. When he saw the extent of my injury, he immediately insisted that he drive me home and then he would come back to finish the print job. I thanked him and accepted his offer as I was feeling rather woozy, which he did. We also decided that as a safety precaution, no Computer Operator would ever be left alone in the Computer Room in the future.
This incident inspired one of the Computer Operators, who had an artistic bent, to draw the following illustration:

The Conversion – Part II
Near the end of The Conversion – Part I, I asked for a promotion to become a Computer Programmer. The new computer management team was receptive but unsure of my programming skills. They, therefore, agreed to promote me if I successfully converted a small series of six programs from IBM DOS to IBM OS on my days off and without being paid to do so. I agreed to this, as I was anxious to become a Computer Programmer, and I knew that I could do this with little difficulty. I, therefore, began work on this task on the two days I was not working as a Computer Operator.
It was not particularly difficult to convert these six programs, but it was calendar time-consuming, as I was only working part-time to accomplish this task. It eventually took about three months calendar time to complete this conversion. After I finished the conversion task, I began the testing to verify the results. In the testing, I discovered a strange problem. One of the steps in processing these programs was to utilize the IBM OS Sort utility to resort and report on the data in the master tape file. When I examined the report, I discovered that the report data was out of sort order. I checked the IBM Sort utility parameters to ensure that it was sorting the data properly, which it was. I then examined the sort order of the input and output tape files to see what the problem may be. I discovered no apparent problems and then decided to run experiments with dummy data to find the source of the problem. My dummy data testing revealed a possible flaw in the IBM Sort utility. I discussed this possible flaw with the Reliance Insurance Systems Engineer and the IBM Systems Support Engineer for Reliance Insurance. They both agreed that it appeared to be an IBM OS Sort utility problem, except that this sort problem was not present in the IBM DOS Sort utility. I had an idea of what this may be happening in the OS Sort and not the DOS Sort (much too technically complex to explain in this document). The IBM Systems Support Engineer decided to forward my tests and my idea to the IBM Sort Utility Program team located somewhere in New York State for their review. A few days later, I received a telephone call from the IBM Utility Program team member who was analyzing this problem. We discussed the problem and the details of my idea, and he informed me that he would investigate the problem and get back to me. A few days later, he, indeed, got back to me and informed me that my idea was the correct cause of the problem. They were issuing an emergency fix for this problem for all IBM OS computers, which would be done the next week by all the IBM Systems Support Engineers nationwide. In the meantime, he informed me that the IBM Systems Support Engineer for Reliance Insurance would receive the fix the next morning, and he asked me if Reliance Insurance would install the fix immediately and if I would rerun the sort with the real tape data and then verify the sort was working properly. We did so, and we were able to verify that the fix solved the problem. The Reliance Insurance Systems Engineer and the IBM Systems Support Engineer for Reliance Insurance were very impressed that I had found this problem and the cause of this problem, and they noted me to their managers for my skill and ability to discover this problem and explain why the problem was occurring. Two weeks later, I completed my testing, and we implemented the IBM OS converted programs.
I then went to the computer manager's office to discuss my promotion and discovered that near the end of this conversion task, the new computer management team left Reliance Insurance for greener pastures, and the old computer management team was reinstated. When I successfully completed the task, I approached the new old head of the Computer Department to discuss my promotion. He informed me that the promised promotion was from his predecessor, and he did not feel bound by this promise, and he was disinclined to promote me, and he would have to think it over. I was, of course, very upset as I had kept my end of the bargain, and I believed that the promise was between me and the Computer Department management, irrespective of the person in charge. The next day he informed me that they had no Computer Programmer position open, but they would keep me in mind if one opened, but not commit to promoting me if a position opened.
That night I discussed what had happened with my shift supervisor, who had been with Reliance Insurance for ten years and knew the personalities and politics of the Computer Department. He informed me that as I was part of the new computer management team that had just departed, I could expect that I would not get the promotion out of enmity for anyone who was part of the new computer management team. I informed him that I was not part of the new computer management team and I had been hired by the Computer Operations Manager that preceded the new computer management team. He expressed surprise about this, as he too believed I was part of the new computer management team. Apparently, everyone had assumed I was part of the new computer management team as I came on board at the same time as the new computer management team and with the knowledge and skill of IBM OS computer operations. He also offered the opinion that this misunderstanding was uncorrectable, as everyone had labored with this misconception for a year and a half. He, therefore, believed that I would never receive the promotion and that my career path at Reliance Insurance would be limited.
Shaken by this knowledge, I was irate that I had not been paid for my efforts and would not receive my deserved promotion. I, therefore, telephoned the National Labor Relations Bureau in Philadelphia and explained the situation to a supervisor in the bureau. He informed me that it was illegal for them to have not paid me for my efforts and that they could correct this illegality. He also informed me that there was nothing they could do about the lack of a promotion as there was nothing illegal about not promoting me. We agreed that his boss would telephone the head of the IT Department to demand that he pay me for my efforts in converting these programs. This would be done in an unofficial capacity, and if they did not pay me, I would have to lodge an official complaint with the bureau. The next night my shift supervisor informed me that they had agreed to pay me, and I needed to total up the hours that I spent converting these programs. I did so that night and presented the list of my hours to my shift supervisor the next morning. That night, as I arrived for work, my shift supervisor presented me with a check for payment for the time I spent converting the programs. He also informed me that my career was at an end, but they couldn’t fire me as they had been in the wrong. I informed him that it would not be necessary to fire me as I was resigning on the spot. He agreed with me that this was the best course of action for me, and he wished me luck in my future career. I went home and took the next week off to calm myself down, and then contacted a computer personnel recruiter, who obtained employment for me as a Computer Operator within a week.
Alco Standard Corp. (Nov 1975 - Aug 1976)
Background
Alco Standard Corporation was a holding company that owned about a dozen companies in the metropolitan region. Some of these companies had minicomputers to help run their business, while others had no computerization of their business. The management of Alco Standard Corporation wished to computerize all these businesses and centralize the finances of these businesses at the corporate location in Valley Forge, Pa. The small computer department at Alco Standard Corporation proposed that each company have a minicomputer to run their business, which would daily transmit their financials to a minicomputer located at corporate headquarters, which would then consolidate these financials into a comprehensive corporate financial statement.
The business management of Alco Standard Corporation was concerned about this proposal as it would require the purchase of multiple minicomputers for all the companies. It would also require development and support staff at each company who would be responsible for the programming and operations of these minicomputers. The business management of Alco Standard Corporation, therefore, hired the services of a prestigious account firm in Philadelphia to examine the computerization of all the companies and the corporation. This accounting firm concluded that the cost of the proposed minicomputer solution would be high and unwarranted and that the best solution would be an IBM Mainframe computer at corporate headquarters and computer terminals at the company locations, which would transmit the data to the IBM Mainframe computer at corporate headquarters. A printer would also be installed at each company for the production of daily reports at the company locations.
The corporate computer department reluctantly agreed to this proposal, and they purchased an IBM Mainframe computer and hired a staff of about twenty computer program developers and eventually six computer operators of three shifts of two computer operators per shift. Shift operations did not begin until a few months later, after the completion of the first computer system development. I was one of the first computer operators hired, and I assisted in the first shift computer operations support for the development of the new computer job processing. It soon became apparent the Computer Department management had very little knowledge or experience with IBM Mainframe computers, and they were learning on the job. It also became apparent that they were not learning well and that they made many rookie mistakes. They were also not very receptive to my critiques and suggestions, and I believe that this lack of receptiveness was because of my lack of personal diplomatic skills due to my technical orientation and my bad attitude left over from my previous employment.
The Christmas Party
The entire computer department was in place by mid-December, and the computer management decided to hold a Christmas party for all the team members to become more sociable with each other. They provided beer, wine, champagne, and hors d'oeuvres the afternoon of Christmas Eve when all work was suspended at noon when the party began at the office. Being introverted and reserved, I mostly indulged in the refreshments and only minimally interacted with the staff. Midway through the party, I was approached by a young lady who was very assertive and persistent in interacting with me. As I was reluctant to engage in any personal relations with a co-worker due to my sexploitation observations from previous employment, it took quite an effort on her part and quite a few drinks on my part for her to get me to let down my guard. But my guard did break down, and we retreated to a secluded office where we became quite amorous and were, of course, observed by several of the staff. We parted ways at the end of the party and did not see each other until we both arrived for work the day after Christmas. I apologized to my manager for my actions, and he observed that I was not the first person at an office party to become inebriated and intimate with a co-worker. He also informed me that management had no problem with personal employee involvement as long as both people were single persons.
Later in the day, the young lady approached me privately and expressed her desire to have a personal relationship with me. We, therefore, began to torridly date each other and became very intimate. This relationship lasted about six months, at which time I realized that I was not interested in a long-term relationship with her, and I broke off our relationship. Thankfully, my employment ended at Alco Standard Corporation a few weeks later, and this break-up had no repercussions in the workplace.
The Tape Drive Debacle
An example of their rookie mistakes, and their unwillingness to need my advice, occurred in the very first computer job that they ran. This computer job was a series of transaction creation jobs for each company they owned, followed by a series of two-file merges to update the corporate financial record file. A two-file merge was one of the most common computer processing jobs at the time, in which a transaction file was compared to a master file, and a new master file was created from the additions, changes, and deletions from the transaction file. Normally the master files were tape files, and the transactions were punched card decks or tape files. They decided that for those companies that were not computerized, they would create a disk-based transaction file for each company by loading the card decks that they keypunched and from and a tape transaction file from those companies they owned that had computerized financial files. These transaction files were loaded onto temporary disk files, which were automatically deleted when the job process was complete. This computer process was a series of jobs, as each company they owned had its own individual job for the two-file merge process.
The first run of this process was expected to take many hours of processing, as it was the initial build of the master file from the combined transaction file, and the effort required to create the large transaction files for this master file creation was time-consuming. Upon learning about this job process, I informed them, in no uncertain (and undiplomatic) terms, that the utilization of temporary disk transaction files was a very bad idea. My reasoning was that if anything went wrong during this process, the temporary disk files would be deleted, and they would have to start the job process from the beginning to recover from any problem that they may encounter. I suggested that they create permanent disk transaction files, which could be deleted by a separate job run by the computer operator after the successful completion of the job process. If they had permanent disk files, it would be possible to restart the job process from the point of failure after the problem was corrected. They responded that what could go wrong as they had new computer equipment and new tapes that they were utilizing for this job process, and they ignored my advice.
By the time they first ran this job process, I was assigned to the second shift (probably to shunt me and my attitude aside). One day I arrived for the start of the second shift and discovered all the managers gathered in front of the computer. I was informed that they had been running this initial job process since 9:00 AM, and they were in the final two-file merge process of creating the first master file based on all the previous transaction processing jobs. I took over the computer console operator's chair and watched the creation of the new master tape file. Approximately twenty minutes later, the tape drive hesitated and performed a rewrite sequence, which is usually indicative of an impending tape or tape drive failure. Sure enough, a few moments later, the computer console reported a tape failure and aborted the job, whereupon it deleted the temporary disk files. I swiveled my chair around and asked the manager if they wished for me to restart and run this process during the second shift. They nodded their assent and immediately left the computer room. I did successfully rerun this process, and the new master file was successfully created around midnight. The next day when I arrived at work, the Computer Operations Manager informed me that they had changed the job process to utilize permanent disk files, which would be deleted by a separate job that the computer operator would run after the successful two-file merge was completed, as I had originally suggested.
The Ill-Suited Computer Operations Manager
This problem highlighted another problem that they had. The Computer Operations Manager was ill-suited for this job, as he was a former corporate minicomputer operator that had no knowledge or experience in IBM Mainframe computers. He was promoted to this position because of his years of service at Alco Standard Corporation. I also believe that he was ill-suited because he did not have a manager’s mindset, as he was subservient to the directions of upper computer management. He was also not very analytical in his approach but was very task focused in all that he did. An experienced IBM Mainframe Computer Operations manager with independent decision responsibilities and analytical abilities would never have allowed this tape drive failure debacle to have occurred. An experienced IBM Mainframe Computer Operations manager would also have been supportive of my critiques and suggestions, as they were IBM Mainframe technology based.
When I went to work with Alco Standard Corporation, I signed a one-year employment contract, as they wanted all new hires to be in place for one year to ensure a smooth implementation of this new corporate computer information technology. Shortly after this tape drive failure debacle, I mentioned to the ill-suited Computer Operations Manager that I would be leaving at the end of my employment contract. A half-hour later, he approached me and informed me that they were willing to terminate my employment contract immediately if I did not make any unemployment claim against them. I assured him that I would not do so, at which point they gave me a two-week severance paycheck, and I immediately left the premises.
My regret about my Alco Standard Corporation experience was that I allowed my anger about my previous employment to interfere with my current job performance. I also learned the importance of carefully listening to other people’s comments and critiques, even those that I did not care for, and considering them before reaching a decision. I learned as well that I should never allow my egotism, based upon my superior technological knowledge and experience, to control my words or deeds but to try to work harmoniously with others less knowledgeable and experienced.
Franklin Institute (Sep 1976 - Jun 1977)
Background
While working at Jerrold Electronics, I visited the Franklin Institute Museum and its Observatory, as I was an Amateur Astronomer and a science aficionado. While at the Observatory, I entered into a discussion this the person manning the observatory, who was also an Amateur Astronomer. He informed me that he was a volunteer and suggested that I become a volunteer at the Observatory on my days off. I accepted this invitation and began to man the Observatory on my Tuesday and Wednesday days off. After about six months of this, it was suggested that I become a volunteer Science Instructor throughout the museum, which I gladly accepted. As I changed employers, I continued volunteering on my days off. After my abrupt exit from Alco Standard, I went to the Franklin Institute the next day while I considered my options for future employment. I mentioned my situation to the supervisor of The Travelling Science Shows that the Franklin Institute performed at the local metropolitan schools. He informed me that they had just obtained a Federal Grant to expand these Travelling Science Shows as part of America’s Bi-Centennial celebrations. He suggested that I take a break from my computer career and work for him as a Travelling Science Show instructor. I thought it over and concluded that I needed a break and that the break would not interfere with my computer career. Although the pay was low, I accepted his offer, and for the next nine months, I was a full-time Travelling Science Show Instructor.
Traveling Science Shows
These Travelling Science Shows were dynamic and fun, involved audience participation, and all the students loved them, and all the teachers thought were great teaching aids (which they were). The shows that I gave were Hot & Cold (thermodynamics), Forces & Motions (Newtonian Motion), Electricity and Magnetism (Electromagnetism), and Light & Sight (Visual Perception and Optical Illusions), while the Chemistry show was given by a Travelling Science Show instructor who had a chemical degree. These shows were adaptable to the age of the audience, except for the Light & Sight and Chemistry shows that were developed and presented to only Junior High School students. None of the shows were developed and presented to High School students, as these shows were too elementary for students of that age.
The excitement and expressions on the students’ faces were emotionally satisfying for me, and I thoroughly enjoyed my time as a Travelling Science Show Instructor. When it came to an end, I resumed my computer career. However, there are some stories from this time as a Travelling Science Show Instructor that have stayed with me throughout my life.
The Troublesome Student Story
While setting up my show on the stage of an auditorium at a rural elementary school, there was a lone male student of about ten years of age sitting in the front row of the auditorium. The Vice- Principal stopped by to ask if I needed anything and then asked if the student was causing any trouble. I responded that he was no trouble, and the Vice- Principal remarked that if he started causing trouble, I should bring the student to his office where he could stay. After the Vice- Principal left, I invited the boy onstage to help me set up the show. He eagerly accepted and followed my directions, and he asked intelligent questions about the equipment that we were setting up. As I had arrived at the school earlier than I expected, when we had finished setting up the equipment, we had twenty or so minutes before the show was scheduled to start.
The young boy and I sat down next to each other in the front row of the auditorium, and I asked him why the Vice- Principal thought he was a troublemaker. He responded that it was because he was a troublemaker, and I then asked him why he was a troublemaker. After his hemming and hawing and further interrogatories by myself, I discovered that this student was bored by schooling as he was very intelligent and a rapid learner, and the other students did not like him. His boredom led him to make trouble to enliven his day at school. I suggested that there were other better ways to relieve his boredom, such as reading ahead, asking intelligent and probing questions of the teacher, participating in classroom discussions, and assisting the students who were having difficulty learning the subject. I commented that not only would he display his intelligence and gain the admiration of the other students, but that he may become good friends with the students he helped and be invited to join in during their playtime. When the show started, I invited this boy to be my onstage assistant, Igor, whereupon he helped the other students who I called upon onstage to assist me and me. After the show was finished, this boy stayed behind to help me disassemble the equipment while the other students went outside to play. I left the school hoping that I was able to help this boy not be a troublemaker in the future.
About a month and a half afterward, the Travelling Science Show supervisor showed me a letter from the Vice-Principal of this school, in which he commended me on what I had done for this student. The boy had a rapid transformation in his attitude and grades, and he was considered one of the brightest students in the school, that he was cooperative and helpful in the classroom, and the other students now included him in their social activities. Consequently, he was no longer considered a troublemaker. After reading this letter, I felt immense satisfaction that I had helped turn the life around of a troubled student.
The Junior High Silence Story
I was scheduled to give the Light and Sight show at a newly constructed Junior High School in central NJ, which had an auditorium in which the windows could be electrically shut so that no outside light would enter the auditorium. This was important to the Light & Sight show, as this show started in darkness to illustrate that without light, there could be no sight. At the beginning of the show, I addressed the students as ladies and gentlemen and then asked for the lights to be turned off. As the lights went out, the students started a cacophony of noise and comments that disrupted the show. I remained silent in the dark while the cacophony settled down. During my silence, the principal asked if I wanted the lights turned on, which I declined to do so. After a few minutes, the students settled down, and I addressed them by saying that at the beginning of the show, I addressed them as ladies and gentlemen, but if they wished, I could restart the show by addressing them as boys and girls. They remained silent, and for the rest of the show, they became one of the most behaved Junior High School students that I had ever given this show to.
The Newark NJ Story
Newark, NJ, was a city in northern New Jersey that was recovering from the devastation of the violent race riots that had occurred in the early seventies. I was scheduled to give the Hot & Cold show to a local all-black public elementary school in the center of Newark, NJ. When I pulled up to the front of the school and got out of my station wagon, I noticed a small group of young black teens eyeing me up from the nearby street corner. Not wishing to have any trouble, I lit upon the idea of pulling out the tank of liquid nitrogen that I utilized in the show. I pulled off the cap of this tank of liquid nitrogen and breathed very heavily into the tank, which caused me to be enveloped in a large cloud of steam. When the cloud dissipated, this group of teens was nowhere to be seen. The principal rushed out of the building and instructed me to pull my station wagon into the locked fenced yard to the side of the school, where I and my station wagon would have no difficulties. I could load my show equipment directly into the auditorium where the show was to be given. I did so and gave the show to a most enthusiastic and behaved student body.
The Deaf School Story
I was scheduled to give a Travelling Science Show at the State School for the Deaf outside of Trenton, NJ. I was assured that it would be no problem as a teacher signer would be by my side to communicate with the deaf students. All went well, except that at the beginning of the show, I noticed that I was raising my voice to be louder than the din of the student’s noisemaking. This was an automatic response I had acquired in giving many Travelling Science Shows. I stopped talking to the students to turn to the teacher signer to ask why I was shouting. She responded that there was no reason to shout as the students could not hear me and that they were unaware that they were making noises. She signed to them that they should try to remain silent, but she informed me that this was a difficult task for them. I continued with the show, but I consciously kept my voice down.
PSFS Savings Bank (Jul 1977 - Jun 1980)
Background
After my Franklin Institute interlude, I decided it was time to get back into the computer field. I then sent my resume out to prospective employers, and I received a response back from the Philadelphia Saving Fund Society (PSFS) bank. They wished to arrange an interview with me about a new position for which they were looking to hire someone.
I was to be interviewed by the manager of the online programming team, Mary Ann Haggerty, who I knew, as she had worked at Trilog Associates, where I was a computer operator. She knew of my reputation for quality work, and she was desirous of hiring me. She explained to me that they had an unusual and unique situation. She informed me that they have been looking into creating a new position which they named the Development Support Library (DSL), which she wanted me to fill.
The DSL position was, in essence, what is now called a software configuration manager. The problem that they faced was that they had about a dozen main programs that ran their online banking systems, which their tellers used for customer transaction processing. These dozen programs had dozens of subprograms that they utilized to do their processing. In all, there were over several dozen of subprograms that were utilized by the dozen main programs. The problem they had was that they were unsure of where all these subprograms were located within the main programs. They needed someone who could chart and organize these subprograms so that when a subprogram was changed, they could determine which programs needed to be tested. They were also concerned that some of the subprograms were duplicating the functions of another subprogram, and they wished to eliminate such duplication. They also needed a way of versioning the main programs and the subprograms and managing the versioning. Today there are many software programs that manage this type of environment, but at this time, this was a totally new endeavor, and there were no computer programs that could do this for them. Additionally, as this was before there were microcomputers, there were not any spreadsheets or database programs that could be utilized to perform these duties. The person they were looking to fulfill the DSL position would be responsible for implementing and managing a DSL system to accomplish these goals.
My First-Day Experience
Upon starting work at PSFS, my manager took me around to introduce me to all the people in the programming department. At one cubicle, I was introduced to a female computer programmer, who was the female computer operator that I had arranged to be terminated from employment at Trilog Associates. Upon returning to my manager's office, I informed my manager that I knew this female computer programmer and that I was responsible for her employment being terminated at Trilog Associates. I expressed my concern about a possible conflict with her due to our previous joint employment. My new manager expressed surprise that she was a computer operator at Trilog, as her resume stated that she was a computer programmer at Trilog. I assured my manager that she was not a computer programmer at Trilog, as she only worked with me in computer operations. My new manager seemed relieved, then explained to me that her manager was dissatisfied with this female computer programmer's performance and was looking for a good reason to terminate her employment. Upon telephoning Trilog Associates to confirm that she was a computer operator and not a computer programmer, they immediately terminated her employment for falsifying her employment application. Although I felt somewhat indirectly responsible for her termination, I kept in mind that she was directly responsible for her termination as she falsified her resume, and her performance as a Computer Programmer was deficient.
The DSL Effort
The IBM Information Management System (IMS) was a hierarchical chained database system from IBM, and for IBM Mainframe computers, that was utilized by the Online Programming team to provide teller and customer services at the branch offices. PSFS was the first bank in the Philadelphia Metropolitan Region that had online real-time teller customer transactions. All the other banks had paper transactions that were sent to the home office at the end of banking hours, which were converted into punch cards that were processed overnight by their computers.
The DSL effort was more difficult than expected, as my preliminary analysis had determined that the number of sub-programs was over three times greater than expected, and they were utilized more often than they realized. I needed to design and develop an IMS database to store, retrieve, and report on this database, which required that I learn IMS technology. In addition, the IMS technology was not very good at this type of processing (a problem that would be resolved in the future by Relational Data Base technology). This effort required that I utilize the IMS Query function to add, delete, and change the information in the DSL database, as well as learn the IMS reporting language to generate the reports I would need to manage the DSL procedures. My manager and the other online programming team members examined my analysis and agreed with my assessment, and it was agreed that I should do so. It also meant that I had to become very familiar with the Roscoe program editing system that PSFS had just installed before my employment at PSFS, and with which no programmer at PSFS was thoroughly familiar.
During one of my somewhat heated discussions with an online programmer about the DSL’s responsibilities, he blurted out, “Listen, you DSL (pronounced DISSIL), you need to do it differently.” which relieved the tension, and we soon resolved the issue to his satisfaction. But from that point on, I was known as the DISSIL.
The Roscoe Revolution
The Roscoe computer system was a non-IBM product for IBM mainframe computers that changed the way computer programmers performed their tasks. Prior to the Roscoe revolution, computer programmers maintained their programs on punched card decks, in which they added or removed punched cards to make changes to the program. This card deck (known as the Source Deck) was then taken to the computer room where the computer operators fed them into the card reader to be assembled or complied by the computer, which produced a punched card deck of the machine instructions to run the program (known as the Object Deck). As the online programming team had many programs and subprograms, each Source Deck had to be assembled separately, and then the Object Decks were combined to create an executable program. This required that these Object Deck punched cards be maintained along with the Source Deck punched cards. This was a cumbersome procedure, and often problems were encountered, such as improperly positioned changes in the source deck, as well as dropped card decks or card reader jams. The Roscoe Revolution changed all this.
The Roscoe system was a multi-terminal system where the terminals were connected and controlled by the IBM Mainframe computer. The computer programs were stored on a hard disk drive in a Roscoe database, which the Roscoe system could then display the program on the Roscoe terminal. The computer programmer could then text edit the program on the terminal and submit the program to be assembled or compiled by the computer. This was a much more efficient process for the computer programmer, which saved a considerable amount of time for the computer programmer, as they non longer needed to work with card decks and eliminated the problems of utilizing card decks. Roscoe also had a macro language that executed Roscoe commands that the programmer could utilize in their efforts. I realized that Roscoe and its macro language, along with the IMS Data Base that I was to create to catalog the programs and subprograms, could be utilized to assist in the DSL functions. I also created a Roscoe macro in which the Object Decks were also saved to the Roscoe database. These Object Decks could then be automatically combined in Roscoe to create an executable program, which could be used for testing the program. I also created a Roscoe macro that copied the tested program executable into the production program library after the program was successfully tested. I also configured the Roscoe system in such a manner that we could institute a computer program versioning system, which had never been done before at PSFS.
The development and testing of the IMS DSL Data Base and the development and testing of the Roscoe system and its macro language would extend the time required to establish the DSL system. However, it would semi-automate the DSL system and save considerable overhead time and increase accuracy in managing the DSL system. Both the manager of the Computer Programming Department and my manager agreed it was time well spent, and they approved the additional time to create the DSL system. After nine months of intensive effort by myself, along with the assistance of the Online Programming team, we had a working DSL system that was fully functional.
The Testing Automation.
The IMS Data Base system had a Batch Testing System (BTS) that allowed the computer programmer to simulate online transactions via punched cards. The BTS would query a small testing database, and it would print out the results of any additions, changes, or deletions to the database as a result of the computer program testing. This BTS testing was done haphazardly by the Online Programming Team, as each programmer would create the card transactions needed to test their changes. It was decided to standardize the BTS testing for an individual program by creating BTS card transactions for each program and to semi-automate the BTS testing process. I was assigned to do this standardization as part of the DSL administration. For the next three months, I created the BTS testing card transactions for each program as a Roscoe file. The computer programmer that made any changes to a program or subprogram was responsible for creating BTS transactions, which I incorporated into the appropriate BTS testing file. I then created a BTS testing Roscoe macro that would submit the changed program for execution utilizing the Roscoe file of BTS transactions for the program. This automated process saved the programmers considerable effort in doing their BTS testing, as well as making the BTS tests more thorough and accurate.
For any significant programming changes, we had what we called a full-up test. In a full-up test, the real database was substituted with the small testing database, and several branch offices had their tellers report early to process transactions against the small testing database. We also had the problem of assuring that the tellers entered the proper transactions to accomplish the full-up testing. The Banking Systems Department was the headquarters department that represented the branch office, the branch managers, and the tellers and branch personnel in designing the branch office processes and in all issues regarding the Online Banking system. The Banking Systems Department also assisted us in creating the proper transactions for a full-up test, then verifying and approving the full-up test results. When the full-up testing was completed, the small testing database was substituted with the real database for the start of the business day. The effort to substitute the real and small testing databases took some time to accomplish, and we sometimes encountered difficulties that negated the full-up testing. I was given the task to determine if we could automate and speed up this task, as well as eliminate the difficulties that we sometimes encountered. I was successfully able to automate this task and eliminate the difficulties that we sometimes encounter. I was also able to utilize the Roscoe BTS file transactions that were developed to test the significant programming changes to provide full-up testing transaction information for the tellers to enter.
Reorganization of the Programming Department Procedures
The Computer Programming Department head was so impressed by what I did he asked me to assist in the development of DSL procedures for the other three programming teams in his department. I spent the next four months doing so, along with the time I spent managing the DSL processes for the Online Programming team. One of the big changes that were made in the programs of the other programming teams was in the data and transaction file definitions, which were hardcoded into the program. This hardcoding resulted in the programs having different file and field names for the same data files. It was decided that a master set of data and transaction file and field definitions would be created in Roscoe, with a Roscoe command that would automatically incorporate the Roscoe master set of file and field names into the program. When a programmer made a change to a program, they were responsible for removing the hardcoded file and field names and incorporating the Roscoe command to retrieve the master file and field names. This necessitated that the processing sections of the program change any file and field names to the master file and field names. While this could be difficult and time-consuming for the programmers, the long-term benefits to the Computer Programming Department were intangible but substantial. To assist in this conversion process, I created a Roscoe macro that could compare the hardcoded file and field names to the master file and field names and generate a list of the differences, which made it easier for the programmers to accomplish this conversion.
After a year and a half at PSFS, I finally completed all my development and testing work, and I settled into the daily tasks of managing the DSL processes for the Online Programming team.
The Relational Database and the Structure System Analysis and Design Revolution
The daily tasks of managing the DSL processes for the Online Programming team required only about thirty hours a week of my time, as I had successfully automated many tasks that they originally thought would be manual tasks. My manager encouraged me to expand the scope of my computer technology knowledge during the time I was not doing my DSL tasks. I, therefore, decided to learn about Relational Data Base Systems and Yourdon Structured System Analysis and Design.
Relational Data Base Systems were based on the relational model of data, as proposed by E. F. Codd in 1970. A system used to maintain relational databases is a Relational Database Management System (RDBMS). Many relational database systems are equipped with the option of using SQL (Structured Query Language) for querying and updating the database. A relational model organizes data into one or more tables (or "relations") of columns and rows, with a unique key identifying each row. Rows are also called records or tuples. Columns are also called attributes. Generally, each table/relation represents one "entity type" (such as customer or product). The rows represent instances of that type of entity (such as "Lee" or "chair"), and the columns represent values attributed to that instance (such as address or price).
I soon realized the potential of RDBMS to solve computer information search and retrieval processes and came to believe that RDBMS was the future of database systems, which computer history has proven me correct. While not having an RDBMS to work with at PSFS, I book-learned as much as book learning could accomplish about RDBMS.
Yourdon Structured System Analysis and Design are methods for analyzing business requirements and developing specifications for converting these practices into computer programs, hardware configurations, and related manual procedures. Structured analysis and design techniques are fundamental tools of systems analysis. They developed from classical systems analysis of the 1960s and 1970s. Structured analysis is part of a series of structured methods that represent a collection of analysis, design, and programming techniques that were developed in response to the problems facing the software world from the 1960s to the 1980s. In this timeframe, most commercial programming was done in Cobol and Fortran, then C and BASIC. As computer systems were getting larger and more complex, computer system development became harder and harder to do so and more fraught with errors. There was little guidance on "good" design and programming techniques, and there were no standard techniques for documenting requirements and designs, which the Yourdon methods significantly helped alleviate.
The most common form of computer coding prior to Yourdon was known as spaghetti coding. Each programmer had their own methodology of designing and developing a computer program in which the computer logic was often convoluted and undecipherable except for the computer programmer who wrote the code. If a change was required to the program, and the original computer programmer was unavailable to make the change, the assigned programmer often had to analyze the program to understand how and where to make the change, which increased the time required to make the change and introduced the possibility of the assigned programmer misunderstanding the spaghetti code and not making the correct change. With Yourdon Structured System Analysis and Design, this problem was very much reduced.
In the era when computer tapes were utilized for data storage, the most common way of updating the master tape file was known as a two-file merge. The master data tape file was compared to a transactions file (which may be punched cards, a tape file, or a disk file) to create a new master data tape file with the additional, changed, or deleted transactions. The logic to determine whether to add, change, or delete a master tape data file was designed and coded by the original programmer and was often convoluted, difficult to change, and sometimes incorrect. After reading the textbook on Yourdon Structured System Analysis and Design, I realized that there was only one proper way to accomplish a two-file merge. I also realized, with my knowledge of Roscoe, that I could use Roscoe macros to generate an outline of a two-file merge program utilizing the Roscoe master set of file and field names definitions that avoided all these problems, which I did. Upon showing this outline program to several programmers at PSFS, they were amazed that this was possible and agreed that the outline program should be utilized for all future two-file merge program development. When the Computer Department Management was informed of this Roscoe macro, they decided that when a significant two-file merge program was upgraded, they would consider converting the two-file merge program to this Yourdon automatically generated two-file merge outline program.
The knowledge that I gained from my study of Relational Data Base Systems and Yourdon Structured System Analysis and Design turned out to be very helpful in my future computer career, especially in my next employment after I resigned from PSFS.
Computer Programmer Promotion
After many months of administrating the DSL system and learning about Relational Data Base Systems and Yourdon Structured System Analysis and Design, I became bored with the DSL administrative tasks. I discussed this with my manager, and she agreed that I deserved promotion and that someone else could take over the DSL administrative tasks. The Computer Programming Department head was also agreeable that I should receive a promotion. However, the Personnel Department at PSFS was reluctant to hire or promote anyone to a computer programmer position that did not have a college computer degree. My Computer Programming Department head and the Personnel Department head reached a compromise about my promotion, in consideration of all the excellent work that I had done for the Computer Programming Department. The Personnel Department agreed to my promotion if I attended a college computer programming course and achieved an excellent grade in this course.
In discussing this with my manager, she suggested that I enroll in the Pierce Junior College computer programming night school course, as she had heard good things about this course. As Pierce Junior College was a few blocks from PSFS, I walked to their admissions office and signed up for this course. I also stopped by the bookstore to purchase the textbook that was utilized for the course. Upon returning to PSFS, I reviewed this textbook and realized I already had the skills and abilities of the first twenty out of twenty-four chapters of the textbook. At the end of each chapter, there was a programming assignment, and as I had six weeks before the first class, I set about doing each chapter's programming assignment. On the first night of class, I had the first twenty chapters programming assignment completed, which I brought with me to class.
On the first night of class, the professor introduced himself as a manager of a programming team in a big local business. The students then introduced themselves to the professor and the other classmates and provided a brief background of their computer experience and expectations for the course. I was the only student who had a computer background, while the other students were hoping to enter the computer field by taking this course. The professor then tried to engage the students in a discussion about computers, but this discussion turned into a dialog between myself and him, as we were the only ones that had knowledge about computers. After the class was over, the professor asked me to stay so we could talk about the class and why I was taking this course. I explained to him I was taking this course to get a promotion, and in preparation for this class, I had completed the first twenty chapters of programming assignments, which I showed him. He responded that he was hoping that the class would be able to cover the first ten chapters, and it was obvious that I had demonstrated all the skills that he hoped to achieve with the class. He also expressed concern that my presence may dampen the spirits of the other students, and he suggested that I not return to class and that he would give me a completion and a 4.0 grade for the class. I agreed that this would be the best course of action, and I never returned to class.
The next morning when I went to work, my manager asked how the course went. I responded that I had passed the course with a 4.0 grade. I explained to her how this had happened, and she laughed, saying that she should have expected no less from me. She then informed the Computer Programming Department head what happened, and he agreed that I met the Personnel Department requirements for the hiring or promotion to Computer Programmer. The promotion had to be slightly delayed, as they needed to find a replacement for me as the new DSL administrator, whom I would have to train. Fortunately, a night Computer Operator who had recently married and his wife was pregnant with their first child had been asking for a promotion to the day shift for obvious reasons. I was familiar with this Computer Operator through my interactions with him in my DSL Administrator capacity, and he had always expressed interest in what I was doing, and I knew that he was a good and capable computer operator that had skills that could be applied as the DSL Administrator. He was promoted to the new DSL Administrator and started the next Monday, and I spent the next two weeks training him. As there was no Computer Programmer position available at this time, they created a new computer programmer position in another programming team that I was assigned to.
The Spaghetti Program Code and Boolean Logic Problem
Upon being promoted to Computer Programmer, my new manager decided to assign me to a difficult programming problem that had bedeviled them in the last year. He had a two-file merge program that, without rhyme nor reason, would occasionally not process a transaction or retain an unchanged master data record. This was a rare occurrence that they manually corrected when it was discovered, and he had two other programmers examine this program to try to discover the problem with the program. The other two programmers were unable to discover any problem with the program, and my manager was despairing that this problem would ever be resolved.
As he had no programming assignment for me, he asked me to examine this program to see if I could uncover the problem. When I reviewed this problem in Roscoe, I realized that it was one of the worse examples of spaghetti programming I have ever seen and that I would have to print out the entire program to chart the computer processing logic to determine where the problem may lay. This program took over a dozen pages to print out (indeed, a very large program for the time), and for the next three days, I charted the program logic on this printout. In doing so, I discovered that the Boolean comparison logic between the master and transaction files was duplicated in three different parts of the program and in three different ways. This combination of three and three was the cause of this problem, and each Boolean comparison logic had a Boolean logic error. I was amazed that this problem did not generate more errors than it did, but the combination of the three Boolean comparison logic sometimes canceled out the problem (which may have been why the original programmer had three different comparison logic parts in the program).
I took the computer listing into my manager's office to inform him and show him where the problem was. He was amazed that I had found the problem in short order and asked me how long it would take to fix the problem. After a few caustic remarks about the original programmer, I informed him that the problem could not be fixed and that I would have to rewrite the program to eliminate this problem. He cautioned me that I should not repeat the caustic remarks about the original programmer to the other programmers, as the other programmers may be reluctant to allow me to examine their programs for fear of me making caustic remarks about their programming. He then asked how long it would take to rewrite the program, and I responded it would take a week or two to rewrite the program. He was astonished that it would take so little time, as his guesstimate was that it would take five or six weeks to rewrite the program. I reminded him of the ROSCOE macro I had written for a two-file merge and that I could utilize this Roscoe macro to generate the outline of the program, then copy and paste the processing logic of the old program into the new program, then make any processing changes necessary for the new program to operate correctly. He gave me permission to proceed and cautioned me to take as much time as necessary to ensure the new program worked properly. By the end of the next week, I had accomplished this task, and my new program replaced the old program, and they had no more problems with this program.
After I completed this task, my manager assigned me to review the other programs that the original programmer had written to determine if they also had severe problems. After I reviewed these programs, I informed him that there were no severe problems in these programs but that the spaghetti code in these programs needed to be cleaned up to ensure that future problems were not encountered. I was then given the task of cleaning up the spaghetti code in these programs, which took me several months to accomplish.
The Upgrade to the Certificate of Deposit System
My next task was to assist in the upgrade to the Certificate of Deposit (COD) system. PSFS had decided to offer a Special COD that had a higher interest rate but would only be issued in denominations of $100,000. This Special COD had to be segregated into separate processing from the Regular CODs, as they were forming a separate Special COD clerical group to administer the Special COD to cater to wealthy customers who purchased these Special CODs. When a customer inquired about purchasing these Special CODs, they would be directed to the Special COD clerical group, which would assign a member of this Special COD clerical group who would be responsible for catering to the needs of these persons. Customers could buy, redeem, or inquire about their Special CODs by telephoning the Special COD clerical group member who was assigned to the customer. This computer programming effort required that I work with the Online Programming team to accomplish this segregation and to develop the new computer programs that the Special COD clerical group required to administer these Special CODs. This also required that I work closely with this Special COD clerical group to ensure that the Special COD clerical group had all the computer tools and reports that they needed to perform their jobs. In undertaking this effort, I became much more familiar with the business processes of utilizing a computer system to achieve a business goal. It took a few months to accomplish and implement this new system for Special CODs, and at the end of this effort, I left PSFS for greener pastures for the reasons I shall explain in The Collapse of PSFS section of this document.
* * * * *
During my career at PSFS, several incidents occurred that helped shape my approach to my computer career and, in some cases, my life. They are:
The Human Beans Programming Team Manager
One of the senior computer programmers was promoted to a new manager position for his quality work as a senior programmer at PSFS. Unfortunately, his interpersonal management skills were lacking, as typical of many programmers that were promoted into management positions. He was also somewhat authoritative, issuing instructions rather than eliciting cooperation. He also had difficulty in dealing with the non-computer PSFS personnel that utilized the computer system for which he was responsible (again, as typical of many programmers when dealing with non-programmers).
The Computer Programming Department Manager worked with him to improve his deficiencies, and he often overreacted in trying to improve his management skills. This was not much of an issue with the programmers on his team, but it was sometimes annoying. The computer system that he managed was scheduled to be upgraded and expanded, which required him to work closely with the PSFS departments that utilized this computer system. He managed to annoy the PSFS department personnel and antagonize the PSFS department managers while working with these people to accomplish this computer system upgrade and expansion.
One of his most annoying habits was his using the term ‘human beings’ rather than persons or people. It was also unfortunate that he also mispronounced ‘human beings’ as ‘human beans’. In doing so, he became known as the ‘Human Bean Manager’. After the computer system upgrades and expansions were successfully completed, the PSFS department managers let it be known to the Computer Programming Department Manager that they no longer wished to work with the Human Bean Manager. With sorrow, the Computer Programming Department Manager realized that this situation was untenable, and he asked the Human Bean Manager to find employment outside of PSFS but allowed him to take as much time as he needed to find other employment. About six weeks later, he resigned from PSFS and was replaced by the lead programmer of the computer system upgrades and expansions. This new manager was liked by all, had very good management skills, and worked well with all the people in PSFS. He would also be my future manager when I was promoted to Computer Programmer.
The General
One of the programming teams was managed by a person who was affectionately known as The General, as he had been with the PSFS computing department since its modern inception with IBM Mainframe computers. He was the original Online Program Team Manager who designed, developed, and implemented the Online Baking System until he turned over those duties and responsibilities to my current manager, and then he became the programming team manager for the Certificates of Deposit computer processing system. He was well respected and liked by all in the Computer Programming Department, and he was an easygoing and affable person. The PSFS Computer Programming Department had a policy that the Online Programming team was assumed to be in error when the Offline Programming teams detected a mismatch of the numbers and amounts between the two systems. This was done to ensure the integrity of the Online Teams computer processing system, as it was extremely important that the online programs be correct. One day it was found that the Offline Certificate of Deposit computer system did not agree with the Online Certificate of Deposit numbers and amounts. Invoking this policy, The General refused to investigate this problem until the Online Programming Team had thoroughly examined their programs.
After three long days of three programmers thoroughly examining our Certificate of Deposit programs, we could not discover any problems. I went back to The General and earnestly requested that his programmers examine their programs to determine if they had any problems. He agreed to do so, and within the hour, his programmers found an error in their program that explained this problem. Being exhausted by our three previous days' examination, I made some unkind comments about The General for not doing this examination earlier, which found their way back to him. He became very upset with me and complained to my manager. After he discussed this with my manager, and my manager discussed this with me, I realized how wrong I was to make those comments. I, therefore, went to The General's office to offer my humble apologies and ask for his forgiveness. We had a polite and respectful conversation about my comments, and he forgave me, as he attributed my comments to my youth and inexperience in working in programming departments. I thanked him for his forgiveness, and he never showed any animosity toward me in the future. With this incident, I learned a very important lesson in holding my tongue and humbly apologizing when I was in the wrong.
The Imperious Vice-President of the Computer Department
The Vice-President of the Computer Department at PSFS was a narcissistic egotist whose main skill was office politics. He was very good at avoiding responsibility and shifting blame to others when problems arose. Many of his directions were more in the form of orders, and very few of his directions were written directions, as formalizing his directions would make it difficult for him to avoid responsibility and shift blame. Only the Computer Programming Department and Computer Operations Managers were allowed to enter his office uninvited, but they had to be announced by his secretary before they were allowed to enter his office. All others had to await a summons from him to enter his office, and most of these summonses came about when problems occurred, as he wished to chastise someone. He had no personal interactions with anyone employed in the Computer Department; he never attended any meetings or gatherings of the department's staff, and he was rarely seen by anyone at any time in the Computer Department. At the annual PSFS Christmas Party, attended by almost all employees of PSFS, it was mandatory for him to show up, but he only mingled with the Executive Management of PSFS. Morale was surprisingly good in the PSFS computer department as he did not directly intervene in the normal work in the computer department. He also left the personnel management to the Computer Programming Department and Computer Operations Managers, who had very good interpersonal skills.
His office was reflective of his personality, as this large office had only a single spotlight light that was centered and directed above his rather large desk and magnificent chair that was on an elevated dais. There were no other chairs in his office, and when you entered his office, you had to stand in front of his elevated dais and look up at him to speak to him. This was not much of a problem, as very few people entered his office. There was also a men’s restroom next to his office, which, unbeknownst to me, was reserved for him and his guests. One day while walking by this restroom, I decided to utilize this restroom, which by happenstance, he was utilizing at the same time. He gave me a dirty look but did not deign to speak with me. By the time I got back to my cubicle, my manager was waiting for me to inform me about this reserved restroom, as he had telephoned her to complain about my transgression into his private restroom.
The Reserve Limit Catastrophe
The Reserve Limit was a mandatory requirement from the Federal Reserve Bank that required all banks to keep a minimum amount of cash reserves to process cash transactions at their bank and as a protection in the unlikely event of a cash run on the bank. This Reserve Limit was computed every night by a formula from the Federal Reserve Bank to determine the minimal cash reserves that had to be available for the next business day transactions at the bank. Any violation of this Reserve Limit was considered a criminal violation of Federal Law, and the executive management was liable for prosecution, and if found guilty, they could be severely fined and/or imprisoned for lengthy sentences if it was determined that they were negligent or committing fraud.
The Online Programming team was responsible for computing this cash reserve at the end of banking hours, and in part, it was done by having the bank tellers log in and record the amount of monies in their cash drawer, and when they logged out, they had to record the amount of monies in their cash drawer, which was reconciled with the transaction amounts that they had processed between logging in and out. This also prevented theft by the tellers, as when they logged in to the Online Banking System, a random teller bucket was assigned to their computer terminal as a security measure. The tellers were not permitted to leave their computer terminals until the reconciliation was properly completed, and in the event of a reconciliation problem, the Branch Manager had to become involved in resolving the reconciliation problem. After the tellers logged in and off from the Online Banking System, this random teller bucket was cleared out as a security measure before they re-logged in and entered any customer's transactions.
One day, after the Online Programming team implemented a change to one of its programs, Banking System received a telephone call from a Branch Manager informing them that they could not reconcile a teller that had fallen ill and wished to leave work early. This caused all work of the Online Programming team to stop as we investigated this problem. We quickly tracked down the problem and determined that it was a very serious problem.
One of the Online Programming Team members needed to make a change to a subprogram of the main program that we had just implemented. The normal procedure to accomplish this was for the programmer to inform the DSL Administrator (myself) that he needed to have a new version of the subprogram to make the change. I would then copy this subprogram to a new version so that he could make the change to the new version, and I would schedule a BTS test for the subprogram. As I was out sick for a few days when he needed to make this change, he created a new version of the subprogram to make the change (Roscoe's security was minimal, and it was possible for him to do so). When I returned to work, he forgot to inform me that he had changed a subprogram, and therefore I did not schedule a BTS test for this subprogram. It turned out that the change to this subprogram was one computer instruction that cleared out the random teller bucket when they logged in, then cleared out the random teller bucket after they had successfully reconciled and logged out. As a result, when all the tellers logged in the morning that the change was implemented, they not only started out with their own cash drawer money, but their cash monies were added to the previous cash drawer bucket monies. This was a disaster, as since these buckets were randomly assigned, it was impossible to trace the teller who previously used this bucket to correct this problem. Therefore, no reconciliation was possible for any teller who logged onto their computer terminal that morning. The Online Banking system was shut down, and the tellers had to revert to the paper transaction system that was in place before PSFS had an online banking system.
This was an extremely difficult problem to resolve, and all the members of the Online Programming team worked many hours of overtime to resolve this problem. A resolution was proposed by an Online Programming Team member, and after much discussion and planning, that took two days to resolve the issues associated with the proposed resolution; it would then take another two days to create and test the computer program to fix this problem. In all, it took five days before the tellers were able to utilize the Online Banking system, and during this time, it was impossible to calculate the Reserve Limit. After this problem was resolved, it was discovered that PSFS had fallen below the Reserve Limit for the entire time it took to resolve this problem. It, therefore, became necessary for the President of PSFS to walk a short distance to the Federal Reserve Bank of Philadelphia to inform the head of the Federal Reserve Bank that PSFS had fallen below the Reserve Limit for five days. After the head of the Federal Reserve Bank listened to the reasons for falling below the Reserve Limit, he agreed that this was an accidental mistake that had no negative impacts. He informed the President of PSFS that no criminal prosecution was warranted but that no further falling below the Reserve Limit would be tolerated. PSFS then instituted a new policy that in the event of their being unable to calculate the Reserve Limit that they would automatically increase their cash reserves by up to 50% from the previous Reserve Limit amount to ensure that they never fell below the Reserve Limit in the future.
Another consequence of this problem was as the computer programmers at PSFS were salaried persons but were paid overtime, as it was expected that they would work overtime to complete their assignments by the due date. However, the other non-computer department people who assisted us in resolving this problem were also salaried persons that were not eligible for overtime pay. Therefore, there was some enmity between the two groups, as the persons who caused the problem received overtime, while the persons who had not caused the problem were not paid any overtime to help fix the problem. This enmity soon dissipated as everybody realized the unfairness of this, and everybody recognized that there was nothing they could do about this.
After this problem was resolved, my manager and I were summoned to The Imperious Vice-President of the Computer Department office for a severe chastising, which was the only interaction I had with him during my entire career at PSFS, except for the restroom incident.
The PIN Problems
PSFS was not a leader in the utilization of ATM machines, and when PSFS decided to embrace this technology, it needed a way to distinguish itself. The Marketing Department decided that a distinguishing ploy would be to utilize four-letter words instead of the traditional four numbers for the Personal Identification Numbers (PIN) needed to access the ATM. Nobody in management ever considered that using a four-letter word instead of four numbers could lead to problems.
The first problem was who would decide which four-letter words would be utilized for the PIN word list. The Marketing Department, as well as other departments involved in the ATM project, managed to dodge this responsibility, and it fell to my manager to create a list of a few thousand four-letter words. She was not the best person to create this list, as she was somewhat innocent of the derogatory meanings of many common words in the English language. She undertook this responsibility, and every evening, as she was too busy during the day, she selected a few dozen four-letter words from her dictionary, which were reviewed for approval at the weekly meeting of the ATM project members.
The next problem was that it was decided that the testing needed a separate list of a few dozen four-letter PIN words for the testing, which for security reasons, could not duplicate any of the four-letter words in the real list of PIN words. This responsibility fell to the lead Computer Programmer for the ATM project. He decided that for the testing, the four-letter PIN words would be slightly off-colored words that would not be approved for the real list of four-letter PIN words.
Another problem was that it was also decided that this list of PIN words should be encrypted and scrambled in such a manner that it could not be utilized in a security breach. A convoluted computer algorithm was created to achieve this goal, and this computer algorithm was applied to the testing four-letter PIN word list. The testing four-letter PIN word list was properly encrypted, and it was successfully utilized throughout the testing. The plan was to replace this testing four-letter PIN word list with the real four-letter PIN word list on the day that the ATM system was implemented.
The final problem was that to ensure that the ATM system was operating properly, the first day of the issuing of the production ATM cards was limited to a few dozen PSFS employees and a select list of a few thousand PSFS customers who were early applicants for an ATM card. The Banking Systems Representative for the ATM Project was a married woman who had a flirtatious (if not more) reputation, and she was one of the first persons to receive a production ATM card with her PIN word. When she opened the welcome brochure with her ATM Card and PIN word, it was discovered that her PIN word was ‘SLUT’. She was astonished when she read her PIN word and remarked to everyone that she thought that no off-colored words were in the real PIN word list. As the other PSFS employees looked at their PIN words and complained, it soon became obvious to the ATM Online Computer Team that they had a problem. Apparently, the test PIN word list had been accidentally incorporated into the real ATM system rather than the real PIN word list.
A mad scramble ensued as the next batch of several thousand customer ATM cards had been created and were scheduled to be mailed out that day. This mailing was halted, and the ATM cards were destroyed. The online programming team had to update the ATM computer system with the real PIN word list, compile a list of who had been issued an ATM card, and delete these records from the IMS database so that they could reissue these cards after they fixed the problem. The Marketing Department had to compose a letter of apology to the ATM customers that had received the testing PIN word with their ATM cards.
My manager and the lead Online Computer Team programmer for the ATM project were summoned to The Imperious Vice-President of the Computer Department office for a severe chastising, which was the only interaction that he had with the ATM Online Computer Team during the entire project.
The Halon Incident
Halon (Halomethane) is a gas that is used in fire extinguishing systems. Holon reduced the oxygen level in the room in which it was released, which put out the fire. Halon was supposedly safe to breathe as there was sufficient oxygen to support life. Therefore, PSFS decided to install a Halon fire extinguishing system in the computer room, which would put out a fire and allow the computer operators to breathe while they shut down the computers. Halon was a very expensive gas, so PSFS decided to put the automatic Halon release on the detection of a fire on a thirty-second delay in the event there was a false fire alarm. During this delay, an audible alarm would be sounded so that a computer operator could disable the automatic release in the event of a false alarm (they could also trigger an immediate release in the event of an actual fire).
Unfortunately, they scheduled a meeting of the computer operators to explain this Halon system for a few days after the Halon system was activated. In the meantime, the installation of the Halon system disrupted the normal airflow of the air conditioning of the computer room, which caused hot and cold spots in the computer room. They, therefore, called in the air conditioner maintenance person to readjust the airflow in the computer room to even out the temperature. The method he utilized to determine the airflow was to light up a cigar and watch the drifting smoke to determine which air vents needed to be adjusted. Of course, this set off the fire alarm, and the Halon system started the countdown to release the Halon. As nobody knew about this audible alarm, no action was taken by any computer operator. Thirty seconds later, the Halon was released, and they discovered another problem with the Halon system. The nozzles for the Halon release were installed just above the suspended ceiling below the solid ceiling, and they were not anchored properly. When the Halon was released, these Halon nozzles acted as jets, hit the solid ceiling above, and bounced down to strike the suspended ceiling, which caused the suspended ceiling to collapse on top of the computers and computer equipment, as well as the computer elevated floor. Chaos reigned, as nobody knew what happened, and everybody fled the computer room.
The first person out of the computer room was the air conditioner maintenance person, who promptly left the building and changed his telephone number so that he could not be reached by PSFS. The Computer Operations Manager had to visit his office to explain that it was not his fault and PSFS would take no legal action against him. They also asked him to come back and readjust the airflow on the newly reinstalled suspended ceiling, which now had solidly anchored Halon nozzles on the solid ceiling. He agreed to do so after PSFS signed a legal waiver absolving him of all responsibility for what had previously occurred. When he returned to readjust the airflow, the Halon system was turned off to prevent a reoccurrence of an accidental release of the Halon.
The Fire and Police Alarm Incidents
About a year after the Halon Incident, PSFS decided to install a police and a fire alarm switch under the two computer console desks that would notify the police or fire department in the event they needed immediate assistance from these departments. Once again, they activated the system before informing the nighttime computer operators of its existence. The night after it was activated, the computer operator discovered the fire alarm switch under one of the computer console desks and tripped it. About ten minutes later, the tape librarian was looking out the outside window and noticed several fire trucks at the front entrance to the building. She commented that there must be a fire inside the building, and she alerted the shift supervisor to be cognizant of this situation. A minute later, the firemen burst into the PSFS computer room, looking for a fire. As there was no fire, everyone was confused as to why the firemen thought there was a fire in the computer room. The Chief of the Firemen explained that they had received an alert that there was a fire in the computer room, at which point the shift supervisor realized that the switch they had tripped must have been the fire alarm that the Computer Department Management had informed them was going to be installed. The Fire Department was not amused by this situation, and they fined PSFS a hefty amount for sending a false fire alarm.
Two days later, another computer operator discovered a switch underneath the other computer console desk, and he asked the shift supervisor what that switch was for. Not knowing what it was for, he examined the switch and accidentally tripped the switch. He stood there gloomily, wondering what was to happen as a result of his accidentally tripping the switch. A few minutes later, the police burst into the PSFS computer room, dressed in bulletproof vests and decked out with shotguns and semi-automatic rifles and guns. The shift supervisor explained to the police lieutenant that it was a false alarm due to his accidentally tripping the switch. The Police Department was not amused by this situation, and they fined PSFS a hefty amount for sending a false police alarm.
Needless to say, the switches were replaced with switches that were harder to trip accidentally, and all computer room personnel were called into an all-hands meeting where they were informed of these switches and their proper utilization.
The Special COD Clerical Group Supervisor
After we had finished the Upgrade to the Certificate of Deposit System, it became necessary for the manager of the COD processing unit to appoint a supervisor for the small Special COD clerical group. This Special COD clerical group was composed of six young ladies who all felt that they deserved promotion to the supervisor of this group. One of the attractive single young ladies in this group asked me for advice on what she could do to receive this promotion to the supervisor of the group. Everyone who worked in the COD processing group, except for this young lady, was aware that the COD Manager had a sexual interest in this young lady. Being much less diplomatic at this time in my life, I informed her of the sexual interest of the married COD Manager. She demurred that this was not true, and he only treated her like he would treat a niece of his. I assured her that this was not true and that the only surefire way to receive this promotion was for her to satisfy his sexual interest. She thought it over and thanked me for my advice, then departed. Two weeks later, the COD Manager announced that this young lady was promoted to the supervisory position of the Special COD clerical group. When I privately congratulated her on the promotion, then inquired about the advice that I had given her, she responded, “I got the promotion, didn’t I” then smiled at me and departed.
The Future Wife
Personal affairs between the men and women at PSFS were very common, and several marriages were the result of these affairs. It was also an unfortunate fact that some divorces and remarriages were a result of these affairs. I myself started a relationship with a woman from Banking Systems with whom I had been working closely. We both agreed that this relationship was to remain a secret while it was occurring. It was only after we became engaged to be married that we revealed this relationship to our co-workers. All our co-workers expressed surprise at this relationship, as they had no inkling that anything was occurring between the two of us. They all were also in agreement that we were a good match, were happy for us, and wished us well in our future marriage.
The Collapse of PSFS
At the end of my career at PSFS, there were rumblings that PSFS was having financial difficulties. As my soon-to-be wife and I were both employed by PSFS, we became concerned that if this happened, we would personally be impacted by the loss of both of our employment. We, therefore, decided that it would be best for both of us for me to find employment with another company. I, therefore, began a search for other employment, and I very quickly found a job in which I was very much interested and which also came with a significant salary increase from my current salary.
A few years after I left PSFS, my now wife was assigned to a large and important project to convert PSFS from a Savings Bank to a Commercial Bank. During this assignment, she discovered that PSFS was indeed having financial problems, and if this conversion was not completed properly and successfully, there was a danger that PSFS may go bankrupt. PSFS did eventually collapse while my wife was on an unpaid leave of absence, and most of the headquarters employees were laid off and received unemployment, except for my wife, who was ineligible for unemployment due to her being on an unpaid leave of absence.
* * * * *
I sincerely believe that it was not until my employment at PSFS that I started to become a mature adult. I still had much to learn before I was satisfied with my maturity, but in my professional computer career, starting with my employment at PSFS, I was on the road to becoming a fully mature adult.
INA / CIGNA (Jul 1980 - Sep 1984)
Background
Insurance Company of North America (INA) was in the process of developing a computer application system utilizing Yourdon Structured System Analysis and Designed that would report the company finances in a Generally Accepted Accounting Procedures (GAAP) manner. GAAP reporting was not done for Banks, Financial, and Insurance companies due to the unique circumstance of their finances, and instead, they utilized Statutory Reporting of their company finances. Statutory Reporting gave a more accurate picture of their finances, but it was difficult to understand unless you knew the intricacies of Statutory Reporting. The Insurance Commissioner of Pennsylvania wanted to see if GAAP reporting was feasible, as this reporting was more understandable by many more people. The CEO of INA agreed to try to accomplish this, but with no guarantees that it would work or be usable.
When my resume, which mentioned my knowledge of Yourdon techniques, was reviewed by the Programming Manger for this GAAP computer system, he contacted me to arrange for an interview. The supervisor of the programming team responsible for developing this GAAP computer system conducted my interview and, immediately after the interview, decided to hire me as a maintenance programmer for the GAAP computer system. This was an open position, as two of the development programmers on the GAAP computer system were being reassigned to another development project when the GAAP system was completed.
The First Week Experience
After arriving for my first day of employment at INA and signing all the paperwork required of a new employee, I was escorted to the supervisor of the GAAP programming team's cubicle. He informed me that they had discovered a major problem that needed correcting before I could start working as a maintenance programmer for the GAAP computer system. He also informed me that another programming team needed assistance in developing a simple program to update the Expenses System to recalculate the Reserve Limit amounts for the expenses system.
The Reserve Limit was much the same concept of Banking Reserve Limits that I had worked on at PSFS, except it was calculated differently for each State rather than a Federal calculation. INA had just gotten approval from several dozen State Insurance Commissions to recalculate the Reserve Limit to a lower amount. This recalculation was to be done by a standard subroutine that did the recalculation for all the computer systems that had a reserve limit. This required that a programmer for each computer system write a program to read the master tape file, then pass information from the master tape file to the subroutine, which would then do the recalculation, then pass the updated reserve limit information, which would be written to a new master tape file. In programming practice, this is a very simple program that is not difficult to accomplish.
The supervisor of the Expenses System (as well as two other computer systems) needed someone to do this for the expenses system, as the other programmers were working on the other computer systems. After being introduced to the supervisor of the Expense System, he explained that he would have to teach me how the new programming environment worked, which had just been installed a few months before I was employed, but that this assignment was a good introduction to this new programming environment. He led me to a terminal and informed me that they had installed Roscoe as their new programming environment, and I informed him that I was a Roscoe expert from my previous employment. I also mentioned that I knew Roscoe macros as well, and he expressed surprise, as no one at INA understood Roscoe macros and how they could be utilized in the programming environment. Within twenty minutes of his showing me how they utilized Roscoe, I was ready to start programming the Expenses Reserve Limit update.
By Wednesday afternoon, I had completed the program and submitted it for overnight testing. On Thursday morning, I reviewed the test results and deemed the program to be working properly and that it could be run that weekend. The supervisor of the Expenses System stopped by my cubicle early Thursday morning to get a status report, and I informed him the program was complete, tested, and ready to be run on the weekend. He expressed surprise that I had completed the program so quickly, but upon reviewing the program and the test results, he agreed that the program was finished. I then asked him if there was any other assistance that I could provide for him. He responded that he had no other work for me, but he suggested that I review the recalculation subroutine, as that would help me understand how reserve limits were calculated, which would be important in my future career at INA.
After printing out the subroutine and examining it line by line, I discovered about one-third of the way through my examination what I believed was a Boolean Logic error that would produce incorrect results from the calculation. While staring at the Boolean Logic error and wondering how I could bring up this possible error to my supervisor, he passed by my cubical, stopped, commented that I looked like a deer in headlights, and asked me what was wrong. After informing him that I believed that I had discovered a Boolean Logic error in the subroutine, he laughed. He assured me that the subroutine was developed by one of their most senior Computer Designers and Programmers and that I was probably mistaken or did not understand the Boolean Logic. He suggested that I telephone the senior Computer Designer and Programmer and ask about the Boolean Logic so that he could explain how I was mistaken and help me understand the Boolean logic. He also assured me that this person would not take offense to my questioning and would be happy to help me understand.
Upon telephoning this person, I explained that I was a new hire that was doing the Expenses System Reserve Limit update. I further explained that in reviewing his subroutine, I believed that I had discovered a Boolean Logic error in the subroutine. I further explained that this was a simple error that could easily be corrected. He asked me to hold on for a few moments while he displayed this subroutine on his Roscoe terminal. He then asked what line number I thought had the Boolean Logic error and what the error was. After he paused speaking to me for several seconds, which I thought was an eternity, the next thing I heard was, “Oh Shit!” He then told me he would get back to me, and our telephone conversation ended. About an hour later, someone rounded the corner of the aisle where my cubical was located and shouted, “Where is this Mark Dawson!” Everybody, including my supervisor, poked their heads out of their cubicle and pointed at me. He then walked up to me and introduced himself as the senior Computer Designer and Programmer who wrote the subroutine. He then informed me, the other programmers, and my supervisor that I had, indeed, discovered a Boolean Logic error in the subroutine. He explained to me that if I had not discovered this error, then INA would have been in violation of the State laws, and they could have been severely fined and faced the possibility of criminal prosecutions, and he guesstimated that I had saved INA millions of dollars in fines. He also slapped a dollar bill on my desk and told me that coffee at the cafeteria was on him for the next week (a cup of coffee was only twenty cents at that time). Everybody was impressed and congratulated me on my discovery of the Boolean Logic error.
The next day, Friday, as I had nothing to do, I decided to recreate my Roscoe macros to generate an outline of a two-file merge program, which paid dividends the very next week of my employment at INA.
The Second Week Experience
When I went to work the next Monday morning, I reported to my GAAP supervisor, who informed me that the problem they had discovered was more complex than they originally thought and that it would take a few more weeks to correct the problem, and that my services would not be required until they solved the problem. However, he also informed me that his manager had a thorny program problem that they wished me to investigate.
I went to see his (and my) manager to discover what he wanted me to investigate. He explained to me that they had a two-file merged program that was not processing the transactions properly, much like The Spaghetti Program Code and Boolean Logic Problem I had at PSFS. He asked me to review the problem and determine how it could be fixed and how long it would take to fix it.
By the end of the day, I determined what the problem was and how to fix it. It was again the problem of spaghetti code and Boolean Logic errors. I waited until the next morning to show my manager what I had discovered. He was amazed that I found the problem so quickly, as another programmer had examined this program for a few days and had not uncovered the problem. He then asked how it could be fixed and how long it would take. I informed him that it would take the rest of the week and be ready by next Monday morning. He was amazed that I thought this could be done so quickly. I then informed him of my Roscoe macro that could generate an outline of a Yourdon two-file merge program and that I would only have to copy and paste the processing code of the old program and fix the Boolean Logic error. He gave me permission to proceed, but he told me he thought that I was too optimistic about how long it would take. By Friday afternoon, I had completed and tested the new program and informed my manager that the new program was ready to be implemented. He was again amazed, but after reviewing the new program and my testing, he agreed it was ready to be implemented.
He then informed me that he had another program that had much more difficult problems to be investigated and that I would start my investigations of this program on Monday morning.
The Thirds and Fourth Week Experience
The program that had the much more difficult problems to be investigated was written in the PL/1 programming language. As I had little knowledge nor any experience in PL/1 programming, I was concerned if I could properly investigate this program. My manager turned to his bookcase and pulled out a small-volume book that explained the basics of PL/1 programming. He told me to take the next several days to review this book and then look at the PL/1 program to determine if I felt that I could properly investigate this program. After doing so, I informed him at the end of the week that it would be possible for me to review this program in general, but any specific investigation would require a PL/1 programmer to investigate this program. He informed me that he had a PL/1 programmer, who also had a mathematics degree, that would be available at the end of the week to further investigate this program's problems.
I spent the next week investigating this PL/1 program processing and Boolean logic. I determined that this PL/1 program was so convoluted that it would take the PL/1 programmer weeks to analyze this program to discover all the problems with this PL/1 program. My manager instructed me to discuss all that I had discovered with the PL/1 programmer who would take over for me and that he would henceforth be responsible for the further investigation of this PL/1 program. My manager also informed me that the GAAP computer system problems had been resolved and that I would start working on the GAAP system starting the next Monday morning.
The Fifth and Sixth Week Experience
The first few days of working with the GAAP system were spent learning the structure of the GAAP programs and the programming environment utilized to maintain the GAAP system. As this was a Yourdon design system, the structure and programming environment was more complex than other computer systems. After learning the structure and environment, I mentioned to my supervisor that the programming environment was convoluted and time-consuming, and with my knowledge of Roscoe macros and Software Configuration Management that I had gained while at PSFS, I could make the programming environment much easier and less time-consuming. He asked how long this would take, and I informed him that it would take me approximately four days to develop the Roscoe macros and another day to train the GAAP programmers on how to use these Roscoe macros. He told me to proceed, and by the end of the next week, the Roscoe macros were in place, and all the GAAP programmers were trained in this new programming environment.
The Super Programmer Designation
The following Monday morning, my GAAP supervisor requested I attend a meeting with our manager. My manager informed me that because of the new programming environment for the GAAP system that I had developed, the GAAP supervisor informed him that he needed one less programmer to maintain the GAAP system and that I was the one less programmer. My manager also informed me that in the INA Computer Programmer Maintenance Department (which I was a member of), they had unofficially designated five programmers as “super programmers” who were assigned the thorniest and most difficult programming assignments. He congratulated me on being named the sixth super programmer in the department and said that henceforth I would be assigned as needed to the most difficult programming problems. He also informed me that nobody had ever been unofficially named a super programmer that did not have at least sixteen months of employment at INA, and I had achieved this distinction in just six weeks. For the next nine months, I was given super programmer assignments, which were interesting programming assignments.
The Delphi Revolution
As I was walking down the hall from the computer programming department to the computer operations department, I chanced to pass by someone with who I had worked closely at PSFS. Bob Cimprich had left PSFS a few months before I did, but he could not tell us what company he was going to or what he would be doing for the company, as he signed a non-disclosure agreement as part of his employment with his new employer. As I was now an employee at INA, he was permitted to talk to me about what he was doing at INA, and we went to the cafeteria, where he informed me of all that he was doing.
INA had a difficult business problem in that all the computer information that they gathered was very difficult to report upon in a timely fashion for the businesspeople to make business decisions. This was because the reporting of the tape file data was a laborious programming effort, as a programmer had to write a program for every report that was requested. Given the volume of reports the businesspeople were requesting, and the limited number of programmers to fulfill these report requests, the process of prioritizing the report requests and assigning a programmer to create the report could take several months, if at all, for the reports to be produced. This was hampering the INA businesspeople in making business decisions in a timely manner with up-to-date computer information.
The Delphi system project had two teams, the Delphi System Development team and the Delphi System Business Analysts team. The small Delphi System Development team, in which Bob was the senior computer designer, was investigating how to technically resolve this problem, while the small Delphi System Business Analysts team was responsible for determining the business requirements for the database information that needed to be stored in the database, as well as the reporting requirement for the database data. They concluded that they needed a computer system that would be able to load the tape file information into a disk-based database system with no programming effort to accomplish this disk database loading. They also concluded that they needed a computer system that could generate a report of this database information by the Delphi System Business Analysts team specifying what information was required from the database, the order of the information, and the subtotaling and totaling of the numerical data (amounts and counts) of the requested information. As far as they knew and researched, they determined that there was no computer system ever developed that could accomplish these goals. They, therefore, were about to start developing a computer system to accomplish these goals. The CEO of INA was so concerned about this business problem that he took a personal interest in this project, regularly monitored the status of this project, and directed that any and all resources needed to accomplish these goals be allocated to achieve the success of this project. Many in the Computer Systems Department thought that this computer system was technologically infeasible and that if it succeeded, it would consume so many computer resources that it would be impractical to utilize. Nevertheless, the INA CEO insisted that the Computer Systems Department attempt to develop this computer system and that he would brook no interference in the development of this computer system. He accomplished this by having the Manager of the Delphi System Project report to him monthly as to the status of the project and any issues or concerns that the Manager of the Delphi System Project may have.
As Bob explained the general design of how they hoped to accomplish these goals, I had many questions and offered many comments and concerns about the general design. At the end of our discussion in the cafeteria, Bob remarked that they had been given permission to start the development of the system, and he was searching for a lead programmer to design and code the programs required to accomplish the automated database population task. He also remarked that as soon as he saw me walking down the hallway, he knew that he wanted me to undertake this task, as he had been impressed by my Roscoe macros to generate an outline of a two-file merge program, and he thought I had the skills and abilities necessary to succeed in this task. He inquired as to the status of my current effort, and I informed him that my current effort would be completed by the end of the week. He then informed me that he had the authority to hire anybody he thought could succeed in this task, and he and I should inform my manager that I would start working for Bob on Monday morning. We went to my manager's office to inform him of my transfer, and he objected, as he had two other assignments that he wanted me to complete before he would consider allowing me to transfer to Bob’s team. Bob then took my manager and me to the Vice-President of the Computer Programming Maintenance office to inform him of his need to transfer me starting next week. My manager started to object, but the Vice-President cut him off and informed him that I would start working for Bob on Monday morning, as Bob had the authority to do so.
The next nine months of the design and development of the automated database computer system were some of the most exciting and challenging efforts I undertook as a computer programmer. The Data Base Management System chosen for this effort was ADABAS (a contraction of "adaptable database system,") which had a fourth-generation programming language, NATURAL, as part of ADABAS DBMS. My first task was to learn the ADABAS DBMS and NATURAL programming language, which took me approximately two weeks to accomplish. I then began to design the Natural programs that were necessary to accomplish the goal of automatically populating the ADABAS DBMS. This computer system was eventually named ‘Delphi’, and I shall henceforth refer to this computer system as the Delphi system.
The Delphi system would allow a Delphi system business analyst to define the format of the tape input on a Delphi terminal. This format was often very complex due to the nature of how the data was stored on the tape, and the Delphi system had to accommodate this complexity. The Delphi system business analyst would define the format of the ADABAS database that would store this data, then define the rules needed to transfer the tape data to the database. The rules were about a dozen commands to manipulate the tape data to be transferred to the ADABAS database that they had defined. One of the rules was a Boolean Logic conditional (If/Then/Else), which was difficult and tricky to accomplish in the completed Delphi system. After the Delphi system business analyst was finished doing so in the Delphi system, they would submit the results for the Delphi system to generate a COBOL program that would automatically populate the database with the tape data.
Once the database was populated, the other part of the Delphi system would allow the Delphi system business analyst to define the reports they wanted to create from the populated database. The Delphi system business analyst specified what information was required from the database, the order of the information, and the subtotaling and totaling of the numerical data (amounts and counts) of the requested information. When they were finished, they would submit the report request through the Delphi system, which would generate a Natural program to create the report.
After the Delphi system was completed and thoroughly tested, it was decided that the automated database population task would be reserved for the Delphi system business analyst, but the automated reporting task would be open to selected businesspersons at the discretion of the Delphi System Business Analysts team. The Delphi system business analyst would be responsible for training and providing support for these businesspersons who were approved to do so.
After nine months of intensive design and coding by myself, we had a working prototype of the Delphi system. The Delphi System Business Analysts team was tasked to thoroughly test the Delphi system, and a database administrator, Jerry, was hired to manage the ADABAS DBMS. We also hired another computer programmer, fresh out of college, to assist me in any corrections or refinements that the Delphi system business analyst discovered or requested. After one year of development, we had a fully functional Delphi system that met all the initial requirements of the computer system, and the computer resources that the Delphi system utilized were not impractical and, indeed, were not significant.
Near the end of the first year of the development of the Delphi system, the manager of the Delphi System Development team was released from his employment at INA because of some unethical conduct he was engaged in. He had hired a new Senior Designer, who was not qualified for this position, to serve alongside Bob. He and this new Senior Designer had formed an independent computer consulting firm staffed with three new or little experienced programmers. They then contracted with this independent computer consulting firm to provide their programmers to work under the new Senior Designer. Thus, they were double dipping as employees of INA and as the owners of the independent computer consulting firm. It also did not help that the manager of the Delphi System Development team had personality conflicts (he was egotistical, arrogant, and arbitrary in his decisions), and INA management was looking for a legal way to release this manager. When they discovered this double dipping (which did not take very long as one of the three new programmers revealed the truth), they had security escort the Delphi System Development team manager and the new Senior designer out the front door and informed them that they would not be allowed to enter the premises henceforth. Bob was immediately promoted as the new manager of the Delphi System Development team, and I was designated as the Senior Designer responsible for all the technical aspects of the Delphi system. We also hired three other programmers to assist in the Delphi system development, for which I was responsible for supervising their efforts.
The next two years were spent refining and expanding the capabilities of the Delphi system, as the Delphi system was considered a huge success. I, therefore, became the lead designer and programmer of a computer system that, as far as anybody knew, had never been attempted in the computer field. Even the ADABAS DBMS vendor did not know if this was possible, and INA requested that the ADABAS DBMS vendor review my design notes to give their opinion, which was neutral, but that they thought it was a worthwhile effort. We were so successful that the ADABAS DBMS vendor asked us to give a presentation at the annual International ADABAS Users Group Conference, which I did. The ADABAS DBMS vendor, after we were successful, decided to create their own report generation system based on my efforts, which they named Super Natural, and they included Super Natural within the ADABAS DBMS. We were so successful that INA realized that they were saving millions if not tens of millions of dollars a year, and they were making better and more timely business decisions.
The International ADABAS Users Group Conference
The ADABAS vendor, Software AG (based in West Germany), held an annual conference in various cities in the United States. At this week-long conference Software AG presented its near future plans for the development of ADABAS and NATURAL, and various third-party vendors of ADABAS add-ons displayed their products, and they invited ADABAS users to give papers on their utilization of ADABAS and NATURAL. The Vice-President of Computer Programming Maintenance had never sent any of his staff to a conference and, indeed, to any computer training classes or conferences, except for an ADABAS/Natural weeklong course that Bob, Jerry, and I attended to learn more about ADABAS and NATURAL. The Manager of the Delphi System Project convinced the reluctant Vice-President of Computer Programming Maintenance that it was important for the Delphi System Development team leaders (Bob, Jerry, and me) to attend these annual conferences.
The first conference we attended was held in New Orleans, LA, and the Manager of the Delphi System Project persuaded Software AG to invite the Vice-President of Computer Programming Maintenance as a guest to this conference so that he may observe what occurred during these conferences. The Vice-President of Computer Programming Maintenance, along with the manager of the Delphi System Project, arrived late Tuesday morning and stayed until Thursday morning. On Tuesday evening Software AG wined and dined the Vice-President of Computer Programming Maintenance and the Manager of the Delphi System Project, and after his visit, the Vice-President of Computer Programming Maintenance decided that this was a worthwhile conference that the Delphi System Development team would attend every year.
On Wednesday evening, the Vice-President of Computer Programming Maintenance decided to take us all out to dinner at a fine Italian restaurant that his wife learned about from the PBS series ‘Great Chefs of New Orleans’ (he had made reservations at this restaurant as soon as he accepted the invitation from Software AG to visit the conference). When we arrived at this restaurant, were seated, and began to review the menu, I was taken aback. The entrees on this menu were more costly than our daily meal allowance for an INA business trip. The Vice-President of Computer Programming Maintenance noticed my discomfort and remarked to me that I looked distressed, and it was probably due to the prices on the menu. He told everyone to disregard the prices on the menu and order whatever they desired, as, after all, he was the person that approved all expense reports. We followed his instructions, and we all agreed that the meals we ordered were some of the best meals that we had ever had.
The next year's conference was held in Las Vegas, NV, and all three of us once again went to this conference. I will leave whatever happened in Las Vegas in Las Vegas, except to say that there was nothing to note of a professional matter about this conference that needs to be related herein. However, I will say that we all very much enjoyed this conference (and Las Vegas).
The next and last conference that I attended was in Anaheim, CA, and only Jerry and I attended, as Bob had left CIGNA. This was also the conference where I was to give my presentation on the Delphi system. This was the first time that I had given a presentation to more than six people and my first time giving a presentation to strangers. I had a fear of public speaking, and I was filled with anxiety about this presentation. I prepared this presentation and reviewed it with the new manager of the Delphi System Development team and the Manager of the Delphi System Project, who made some suggestions but generally approved what I had prepared. I then privately practiced this presentation several times, then gave it to the Delphi system team (whose attendance was mandatory). The presentation at the conference went well, with over one hundred attendees, as Software AG encouraged conference participants to attend this presentation. The only difficulty was that one of the attendees was skeptical and questioned the Delphi system's accuracy in generating a program and the practicality of allowing users to define and run their own reports. As his questions were intelligent and reasonable, I was able to answer his questions and skepticism intelligently and reasonably. Initially, I was somewhat uneasy about his questions and skepticism, but after I was able to deal with his questions and skepticism, I became at ease. After my presentation was finished, we both attended the next presentation, and I sat down next to him. We continued conversing about the Delphi system until the next speaker began his presentation, and I became friendly with him for the rest of the conference. This experience alleviated my public speaking anxiety, and I have since given many presentations, both professionally and publicly, to many different-sized and diverse audiences. I have even written a web page, “Public Speaking”, about how to prepare and present a presentation or speech.
The West Coast Conference
INA was holding a business conference for its west coast executives one summer in San Francisco, California. The west coast operations of INA were located in Los Angles, but they held the conference in San Francisco so that the executives would not be distracted by daily work issues. The Vice-President of Computer Programming Maintenance, the Manager of the Delphi System Project, the Delphi System Business Analyst Manager, and Bob and I were to attend this conference to demonstrate the capabilities of the Delphi system and determine the interest of the west coast INA business executives in utilizing the Delphi System. Our presentation was warmly received, and many of the business executives were very interested in obtaining access to the Delphi system.
As the Manager of the Delphi System Project had in the past spent three months in San Francisco, he decided to give us a car tour of the city one evening. San Francisco had a number of steep streets that the Manager of the Delphi System Project drove us on. At one street, as we crested the hill and started on a long steep incline, the Vice-President of Computer Programming Maintenance yelled at the Manager of the Delphi System Project that if he took his foot off the brake, he was fired. He also drove us on Lombard Street, which is an east–west street in San Francisco, California, that is famous for a steep, one-block section with eight hairpin turns. Stretching from The Presidio East to The Embarcadero (with a gap on Telegraph Hill), most of the street's western segment is a major thoroughfare designated as part of U.S. Route 101. The famous one-block section claimed to be "the most crooked street in the world", is located along the eastern segment of the Russian Hill neighborhood. It is a major tourist attraction, receiving around two million visitors per year and up to 17,000 per day on busy summer weekends as of 2015. We ended our car tour at the San Francisco wharf, where the Manager of the Delphi System Project knew of a very good restaurant where we had dinner.
The Line of Business Sales and Purchases
INA, like other insurance companies, would purchase and sell lines of business to other insurance companies. When they purchased a line of business, they would have a programmer incorporate the seller's computer tape file data as transactions into the two-file merge program that was for the line of business. When they sold a line of business, they had to extract the records for this line of business from the master tape file. This process took a considerable amount of programming effort, often taking months to accomplish. In one case, INA had purchased a large and complex line of business that had to be incorporated into three two-file merge programs. When my manager attended the managers meeting to discuss this effort, he realized with some effort on my part that the Delphi system could be utilized to accomplish this effort. The super programmer that was assigned this task had some knowledge of the Delphi system from his assistance to a Delphi system business analyst in the automated loading of a tape file he was very familiar with. He thought that a Delphi system solution to this incorporations could be possible with some alterations to the Delphi system. Instead of saving the output of the Delphi system in a database, he needed the Delphi system to save the data on up to three tape files. He also needed two additional rules and an expansion of the conditional rule to allow for nested conditions.
Bob returned from this meeting and asked me to meet with the super programmer to discuss the changes he required. I did so, and the super programmer offered a concept of how a nested conditional rule could be incorporated into the Delphi system. I realized that what he required was possible and that his concept of a nested conditional rule was the best way to accomplish this in the Delphi system. I informed Bob that what the super programmer required could be done with about two weeks of effort on my part. Bob told me to immediately proceed to make these changes, and I informed the super programmer that the changes to the Delphi system would be available to him in two weeks. He had no problem with this, as he expected it would take him about two weeks to define the input and output tape files in the Delphi system. We both proceeded in our efforts and two weeks later, both he and I were ready to start defining the rules to create the transaction output tape files. After spending the day with the super programmer to demonstrate the Delphi system rules, he proceeded to create all the rules to perform the creation of the three transaction tapes. This took him about two weeks to accomplish, and in the end, he generated a Delphi system fully functional COBOL program that accomplished what was necessary to incorporate the purchased line of business computer data into the INA computer systems. In all, it took him a month’s worth of effort to achieve what he had guesstimated would have taken him four months utilizing the previous means of incorporating a purchased line of business.
A few weeks later, this same super programmer was given the task of extracting the INA computer tape file data to a tape file for a line of business that INA had just sold to another insurance company. He again utilized the Delphi system to accomplish this, and he completed the task in two weeks, which would have taken him four to six weeks utilizing the previous means of performing this task. At this point, the Vice-President of Computer Programming Maintenance decided that all line of business sales or purchases computer processing would be done in the Delphi system.
The INA/CG Merger
Several months later, INA and Connecticut General (CG) announced that they would merge into one company—CIGNA. INA was a large insurer of property and casualty insurance with a small life and health insurance business, while CG was a large insurer of life and health with a small property and casualty insurance business. It was decided that INA would incorporate CG’s small property and casualty computer data into our computer systems, while CG would incorporate INA’s small life and health computer data into their computer systems. The only unresolved question was which computer management team would be the top dog after the merger. The INA and CG senior business executives decided that whoever completed the computer data conversion process first would be the top dog. They did this with the caveat that if INA or CG computer management was not cooperative with each other, the uncooperative computer management team would not become the top dog. The race was on, and a week-long meeting was held at CG’s computer systems headquarters, with both company teams responsible for this incorporation in attendance. Much computer data information was swapped between these two teams, and they parted with an agreement that the next month’s meeting would be held at INA’s computer systems headquarters, at which they would discuss their plans and schedule for this incorporation.
The super programmer that had used the Delphi system for the other line of business incorporation that utilized the Delphi system was the lead INA programmer for the INA/CG incorporations. He immediately started utilizing the Delphi system to define the CG input tape data files, but he did not need to define the output tape transaction files as they were already defined in the Delphi system from previous incorporations. He also had the other INA programmer start defining the INA life and health computer data extractions in the Delphi system. By the time the next meeting between INA and CG was held at INA’s computer systems headquarters, he had completed the Delphi system work and generated the programs that he needed to do the incorporation of CG's computer data and was about to begin the testing.
When the INA/CG meeting started, the CG programming team was invited to give their presentation first, as they were the guests of INA. After an hour of presenting what and how they intended to do the INA computer data incorporation into the CG computer data system, they proudly announced that they expected this effort to take nine months if no major problems were encountered and perhaps up to eleven months if they encountered some problems. When the INA super programmer stood up to announce INA plans, he simply stated the incorporations programming was completed, and he was about to start the testing and expected to be able to incorporate the CG computer data next week. He then sat down, and the CG people expressed astonishment and disbelief that he had already completed the programming effort. At that point, the Manager of the Delphi System Project stood up and gave his presentation on the capabilities and usage of the Delphi system to the CG people. The INA super programmer then explained how he utilized the Delphi system to create the programs so quickly with the Delphi system and then showed the CG programmers the computer programs that the Delphi system had generated.
The CG people realized that the race was over and that INA had won the race by well over a mile. It was decided that INA would install remote Delphi system terminals at CG’s computer systems headquarters (which INA had the capability to do so in a few days) and that a Delphi system business analyst and I would travel to CG to provide training and assistance to the CG programming team in how to utilize the Delphi system. Two weeks later, in the dead of winter, we both were at CG’s computer systems headquarters in Hartford, CT, for four days to provide this training and assistance. The CG programming team had few problems in utilizing the Delphi system to generate their own programs to incorporate the INA computer data into their computer systems, which they accomplished in six weeks. This was the swiftest, easiest, and most accurate incorporation of another company’s computer data that the CG programmers had ever accomplished. Needless to say, INA computer systems management became the top dog for CIGNA computer systems management.
North American General
When INA and CG merged, they were unsure of what to name the new company. They, therefore, hired a prestigious marketing consulting firm to assist them in determining the name of the new company. After a few months, and after great expense, they had reached a decision, and they made a public announcement that they would reveal the new name at a Friday afternoon press conference. They also decided to announce the new name on Thursday morning to their senior vice presidents to prepare them for any questions that their staff may have. Several hundred senior vice presidents gathered in the auditoriums in both companies’ headquarters, which was simulcast to the other auditorium.
While I did not witness the following story, the Manager of the Delphi System Project was in attendance and a witness to this story, and he related this story to the Delphi system team when he returned from this meeting. The senior executives were on stage, and the CEOs of both companies made some opening remarks and then turned over the stage to their marketing executives and the prestigious marketing consulting firm representative. These marketing people then explained the process for determining the name of the joint company and dropped the veil covering the new name. As all the onstage executives were beaming and congratulating themselves, they revealed the new company name—North American General. After a few moments, someone in the audience of the INA auditorium shouted out, “NAG—now that’s a good acronym for an insurance company.” All onstage froze in their spots, turned pale, and started to stammer as they realized their faux pau. Then they hastily announced to the people in the auditorium that they should forget what they had just announced, and they would get back to them on the next day with the new name for the company. The next day at the press conference, they announced the new name of the company would be CIGNA, a combination of two great companies’ acronyms into one new acronym.
The Vice-President of Computer Programming Maintenance
The Vice-President of Computer Programming Maintenance had a difficult job of coordinating the efforts of six programming managers and sixty programmers, along with coordinating their efforts with the Computer Operations department and with the management of the various business departments that utilized the products of the computer systems he managed. He was very good at his job, well respected by everybody, and liked by his staff. He was somewhat of a stickler for rules and procedures, as that was the only means that he could properly do his job. The Delphi system development team was somewhat of an outlier of the rules and procedures, as this development was not a normal programming effort. As we reached the end of the first year of the Delphi system development, we were encountering problems with obtaining quick turnaround from Computer Operations for the jobs we submitted to them. After discussing this with Computer Operations, we reached a compromise in which Computer Operations agreed to provide a quick turnaround for us between 4:00 AM and 8:00 AM. The Delphi system development team had no problem coming in early for the month or so it would take to complete the development. This required that Bob and I get permission from the Vice-President of Computer Programming Maintenance to change our work hours to 4:00 AM to 12:45 PM.
One of the things that the Vice-President of Computer Programming Maintenance was a stickler about was that all his staff had to arrive before 9:00 AM and not leave before 05:00 PM. To ensure this, he positioned his office between the two entrances that led into the computer programming work area and had a large window installed in his office that he could utilize to observe the comings and goings of his staff. As he arrived for work at 8:00 AM and usually did not leave until 6:00 PM, he was able to keep track of when everybody arrived or departed from work. Everybody on his staff knew this, and nobody on his staff would arrive late or depart early without permission from their managers.
When Bob and I went into his office to discuss the new work hours for the Delphi system development team as a result of our compromise with Computer Operations, he expressed concern that he would not be able to monitor the working hours of the Delphi system development team. I responded that it would be my responsibility to monitor their working hours, as Bob would continue to work normal hours, and I would be working the same hours as the Delphi system development team. He glumly accepted these new work hours for the Delphi system development team, as he knew of the importance of our completing our efforts in a timely fashion.
Handle the Truth
At the end of the year, after the Delphi system was implemented, we scheduled an upgrade to the ADABAS DBMS and the Delphi system over the holidays, for which I was responsible. Bob and the Manager of the Delphi System Project were taking a vacation during the Christmas week, as well as many other persons at INA, including the Computer Operations IBM OS System Engineer who was responsible for all upgrades and upgrades to any system software. As the ADABAS DBMS was considered systems software, he also bore some responsibility for this upgrade.
The Vice-President of Computer Programming Maintenance held a Christmas Party for his staff in the cafeteria on the afternoon of Christmas Eve. During this party, he and Bob discussed the upgrade, and he decided to postpone the upgrade until after the new year. Unfortunately, Bob forgot to relay this decision of the postponement to me. I, therefore, proceeded with the upgrade as originally scheduled. After the upgrade was completed, the Delphi system started to exhibit some anomalous behavior. An investigation did not reveal the cause of this behavior, and the Vice-President of Computer Programming Maintenance was becoming concerned. He called me into his office to discuss this situation and casually remarked that it was a good thing that we had postponed the upgrade. I was taken aback by this remark, as I had not known of the postponement and had done the upgrade. I remained silent and left his office to continue my investigations of this anomalous behavior. After an hour or two, I discovered the cause of the anomalous behavior as being that an IBM OS setting needed to be changed for the upgraded ADABAS DBMS to work properly. A change to an IBM OS setting for which we required the Computer Operations IBM OS System Engineer, who was on vacation, to make.
I, therefore, had to go back to the Vice-President of the Computer Programming Maintenance office to explain the problem and admit that I had made the ADABAS DBMS upgrade that he thought had been postponed. He was visibly upset with me that I had not informed him that I had done the upgrade. He irately told me that he would not tolerate being misinformed as he could handle the truth but that it was not possible to properly handle falsehoods. After we discussed how to correct this problem, he had calmed down sufficiently that he told me that I had made a big mistake in not truthfully informing him of the upgrade, but he would forgive me this one time as he understood my dilemma of protecting Bob about Bob’s mistake of not informing me of the postponement. To his credit, he never showed any animosity toward me in the future. But I always remembered and kept in mind a truth that he revealed to me—you should be willing and able to properly handle the truth, but it was not possible to properly handle falsehoods.
My Responsibility—My Authority
A short time after Bob was promoted to the Delphi System Development team and I became the Senior Designer, I was working with a junior Delphi system business analyst in the development of a new Delphi system rule. She was unsatisfied with how I was developing this rule, and I explained to her that the rule had to be implemented in this manner to work properly in the Delphi system. She exclaimed that I had to find another way that satisfied her, and she remarked that I was not really in charge and she was going to complain to Bob, who was really in charge. I informed her that Bob’s office door was always open, and she was free to discuss anything with Bob. She immediately marched into Bob’s office to register her complaint. Two minutes later, she slouched out of Bob’s office with her tail between her legs and plopped herself into her chair without speaking a word. A few minutes later, I went into Bob’s office to discuss the new rule and her complaint.
Bob informed me that he told her that I was the senior designer, that I had the responsibility and authority to make technical decisions, and that he would support me in any technical decision that I made. Bob did inquire about the technical reasons for my decision, and he agreed that I had made the correct decision. From this incident, I developed an aphorism that I applied in my future computer career:
"Do not accept responsibility
without the authority to do what you believe is correct. For to do
so will ultimately result in failure, a failure for which you
shall receive the blame."
- Mark Dawson
University of PA
Near the end of my career at CIGNA, the CIGNA Executive management reached an agreement with the University of Pennsylvania that twenty employees of CIGNA’s designation would be enrolled at the university’s night school for adults at CIGNA’s expense. These employees would still have to undergo a screening by the university’s enrollment department to determine if they were suitable for enrollment. When the Manager of the Delphi System Project heard of this program, he arranged for me to become one of these twenty CIGNA employees. I had no problem passing the screening, and I was enrolled in classes two nights a week. The first class I took, an uncredited class, was a refresher course on Algebra and Trigonometry, which was being taught by Dr. John Allen Paulos of Temple College. Dr. Paulos later achieved some fame as an author of books about mathematics for the lay public. He and I got along famously, as we both had Kaypro CPM microcomputers which we talked about. Taking this course paid dividends in my future career, as I utilized this knowledge on several projects that I worked on at GE Aerospace. He remarked to me, at the end of the course, that I had some mathematical talent that I should develop. The next course that I took was Informal and Formal Logic. I was very knowledgeable about Formal Logic, as Boolean Logic is Formal Logic, but I have little knowledge of Informal Logic. During the instruction about Formal Logic, I was a wiz at the instructional materials for Formal Logic, and I often assisted the other students in understanding Formal Logic. The Professor was appreciative of my efforts and remarked that my assistance made the instruction of Formal Logic much easier for him.
After this course, I took several other courses, but my employment at GE Aerospace intervened, as I was working overtime or on business trips, which made it impossible to attend courses. It also didn’t help that CIGNA discovered I was no longer an employee and stopped their payment of my tuition. Although GE Aerospace had a tuition reimbursement benefit, my duties did not allow me to continue taking courses at the University of Pennsylvania, and I stopped taking courses.
Reorganization and Promotions of the Delphi System Staff
After the INA/CG merger was complete, my manager, Bob, received an offer from a large company to become their head of the Computer Programming Department, which he accepted. After Bob left CIGNA, they decided to appoint the manager of the Delphi System Business Analysts team as the interim manager of the Delphi System Development team. I had no problem working for him, as we had a very good working relationship as the manager of the Delphi System Business Analysts team. I was, however, dissatisfied with my salary (as explained below), and I put my resume out to determine my value in the marketplace. I received an offer for an interesting position at a very good salary increase over my present salary. In discussing this offer with my interim manager, he informed me that there would shortly be a reorganization of the Delphi systems teams and that I could expect that I would be the new manager of the Delphi system development team if I stayed at CIGNA. I, therefore, turned the offer down and stayed at CIGNA with the expectation of a promotion and a corresponding salary increase. Two months later, they reorganized the Delphi management, and the Manager of the Delphi System Project decided that the new manager of the Delphi System Development team should be a person who could play the office politics game. This was not a strength of mine (an understatement), and he promoted the Delphi Database Administrator to be the new manager of the Delphi System Development team, who had office politics skills. I received no promotions nor salary increase in this reorganization, as I was on an accelerated salary increase schedule. This infuriated me, as I had stayed at CIGNA with the expectation of receiving this promotion. I was also angered as my skills and abilities were a primary factor in the success of the Delphi system, and I had done so much for INA/CIGNA during my career at INA/CIGNA, which saved them much time and monies because of my efforts, yet I remained the lowest paid person on the Delphi system team.
During my career at INA/CIGNA, I was the lowest-paid super programmer, and for my efforts on the Delphi system development. Indeed, by the time I left CIGNA, the entire Delphi system team coworkers were being paid more than I was being paid, even the people that I supervised (I had seen the salary schedule of the Delphi personnel which Bob had left on his desk before he left CIGNA). This included a new Senior Designer on the Delphi System Development team that was hired at a 33% increase above my salary.
This occurred because I had been hired as a computer maintenance programmer at a good salary, and the personnel policies of INA did not allow for salary increases beyond a maximum percentage for a minimum time interval between salary increases. Because of my efforts at INA/CIGNA, I was much more than a maintenance programmer, and I thought I was grossly underpaid. My manager and his manager agreed that I was being woefully underpaid, and they attempted to correct this situation by placing me on an accelerated pay raise schedule within INA’s personnel policies. I calculated that with the accelerated pay raise schedule, it would take approximately four to five years to bring my salary up to what my market value was, in addition to all the salary monies that I was not being paid during the accelerated schedule. Being a young man with a young family, I was not interested in waiting for five years to get paid what I was worth. I, therefore, put my resume out on the market to see if some other companies wish to hire me at a greater salary. Within a few days of putting my resume out, I received a telephone call from GE Aerospace, who were very interested in hiring me at a greater salary. After an employment offer from GE Aerospace, I tendered my resignation from CIGNA within a week after the reorganization of the Delphi management was in place.
The Demise of the VP
Several years after leaving CIGNA, I ran across a CIGNA coworker at a local shopping mall. We decided to have lunch together and catch up on what we were doing. He related the following story to me, and while I cannot vouch for the facts of this story, I can vouch for his honesty and integrity.
The Vice-President of Computer Programming Maintenance had been forced into retirement, as the President of Information Technology at CIGNA had become dissatisfied with him. This dissatisfaction stemmed from the change in computer technology from mainframe computers and tape systems to workstations and microcomputers and the replacement of tape systems with disk database systems. He was having difficulty keeping up with this modern computer technology, and his management style did not fit the new breed of computer programmers of this new technology, which was causing dissatisfaction within the ranks of his staff.
Despite his decades of employment at CIGNA, the President of Information Technology at CIGNA decided it was time for a new Vice-President of Computer Programming Maintenance. However, they needed a legal reason for replacing him for fear of an age discrimination lawsuit by him, and he provided the legal reason. While attending a party of the managers of CIGNA Information Technology, he drank too much wine, and while he was driving home slightly drunk, he was pulled over by the local police and charged with driving under the influence of alcoholic beverages. Upon his guilty plea, the President of Information Technology at CIGNA arranged for a good severance package and full pension benefits for him, released him from employment at CIGNA, and it was rumored that he went into full retirement.
As I approached the end of my computer career, I remembered this story. And as I came to believe that computer technology was passing me by, this story was an important factor in my decision to retire.
GE Aerospace (Oct 1984 - Dec 1991)
Background
The next Monday evening, after my employment agent sent out my resume during the previous week, I received a telephone call from a manager at the GE Aerospace Military Data Systems Operations (M&DSO) Military Command, Control, and Communications (MC3I) division. He explained that he was very intrigued by my resume and interested in determining if I would be an appropriate hire. He further explained that the normal hiring process within his division was an introductory phone call of about thirty minutes to determine if an in-person interview of two to three hours was warranted. After the in-person interview determined if a person was a good hire, the hiring manager would recommend, at the Friday staff meeting with the Systems Engineering Manager, that an offer of employment be tendered. This offer would contain the position for which they were being hired, as well as the starting salary and the terms of the hiring process, which would be mailed to the prospective employee the next Monday by the Human Resources department.
This phone call was my initial 30-minute telephone interview, which turned into a three-hour discussion with him. He explained as this was a classified government contract, he could not give me any details of what I would be doing. He just assured me that they would be utilizing all my skills and talents, and I would be the leader of this effort. During this interview, we discussed in detail my efforts at PSFS and INA/CIGNA. At the end of this three-hour telephone interview, he informed me that he was very desirous of hiring me and that the normal hiring process would not be employed. He intended to directly recommend to the Systems Engineering Manager the next morning that an offer letter of employment be sent by mail immediately. He also asked me what salary I desired that would entice me to accept his offer. Several days later, I did receive this offer letter at my salary requirement, which was a 25% increase over my current salary. As the terms of the offer were that if I accepted the offer, I would be committed to coming to work at GE Aerospace or paying a substantial fine for breaking the terms of the offer. This fine was necessary because as soon as I accepted the offer, they would begin the process of obtaining the initial security clearances I needed to start working on this classified government contract, and this fine was the cost of the initial clearances. I decided to accept his offer, and I showed up for work two weeks later. The first day I showed up for work was also the first day that I met my new manager. He again informed me that as it was a classified government contract, I would have to attain security clearances before he could provide me with any additional information. Thus began my career at GE Aerospace by waiting for my security clearances to be approved by the U.S. Government.
Awaiting Clearance
The proper security clearances I needed to start working on this classified government contract required some time for the Government to process. It also took me several days to gather and write down the information that was required to obtain the proper security clearance for my work at GE M&DSO MC3I. As the contract that I was to work on required an Extensive Background Investigation, which often took a week or two of government efforts, but often took several months for the government to begin this investigation due to a backlog of security clearances requests, it took approximately seven months before I finally received my security clearances. During this time, it was expected that you would enhance your technical skills and learn the policies and procedures of M&DSO. The manager of Awaiting Clearance also tried to find short-term unclassified assignments that you could be assigned, but my Systems Engineering Manager was not too keen on this because as soon as someone received their clearances, they had to immediately start work on the classified government contract.
All classified work at GE M&DSO was done in a Sensitive Compartmented Information Facility (pronounced “skiff”), a U.S. Department of Defense term for a secure room. It can be a data center or a secure room or building that guards against electronic surveillance and suppresses data leakage of sensitive military and security information. SCIFs are used to deny unauthorized personnel, such as foreign intelligence services or corporate spies, the opportunity for undetected entry into facilities for the exploitation of sensitive activities. These SCIF rooms or buildings were windowless and required secure access by approved personnel only. Many times, the rooms in a building SCIF had their own secure access to restrict access to personnel cleared to see the classified information that was in the room.
When my security clearances were approved, I was escorted by a security officer to the security department SCIF to receive a two-hour security briefing and clearances, but only after I signed a legal contract not to reveal anything that was said or shown during the security briefing to anyone not approved to know such information. When my security briefing was complete, I was escorted by a security officer to the SCIF building where I would be working and formally introduced to my manager. A formal introduction was required when two or more cleared persons worked together to ensure that they all knew that they could share classified information with each other.
FERB
Upon being formally introduced to my manager, he was then able to give me classified details on their classified government contract. He informed me that the government contract was subdivided into six segments, with a different contractor responsible for each segment. They had obtained the segment four contract, and he informed me the first thing he wanted me to do was read all the different segment specifications that described what their segments were responsible for accomplishing. As the segment specifications were rather large and boring, it was going to take me several days to accomplish this. We agreed to meet on Friday afternoon to discuss my duties and responsibilities after I read the segment specifications. Upon reading the segment specifications, I discovered that in segment four, which was our segment, there was no mention of my specific skills and abilities. However, in segment five, there was quite a bit of mention of my specific skills and abilities. When meeting with my manager on Friday afternoon, I discussed this discovery with him. At that point, he informed me that when they were hiring me, they were very certain that they were going to win the segment five contract, but as it turns out, they did not win segment five; they won segment four which they had also submitted a proposal. This meant that they had no job for me relating to my specific skills and abilities. I then asked him what my duties and responsibilities in segment four would be. He informed me that they had a pressing need for someone to take charge of the Factory Engineering Review Board (FERB) and to get it organized and operating smoothly.
MC3I was structured into two sections (Systems Engineering and Software Engineering) led by General Manager John Carrow. Systems Engineering had several teams (Data Base, Hardware, Networking, Operational Processes and Training, and Testing), each with a manager reporting to the Systems Engineering Manager. The other section, Software Engineering, had six different software teams responsible for the design and development of the components of the computer software system that was to be developed, each team led by a manager reporting to a Software Engineering Manager. Each contract within MC3I was led by a Program Manager and a Chief Engineer reporting to the Program Manager, with the Program Manager reporting to the General Manager. The Program Manager was responsible for the Legal, Financial, and Contractual Requirements of the contract, while the Chief Engineer was responsible for all the technical aspects of the contract. In the time that I was FERB leader MC3I had only one contract and, hence, only one Program Manager and one Chief Engineer, but they were trying to obtain other contracts. The hierarchy of the MC3I organizational structure was:
- General Manager
- Contractual
- Program Manager A
- Chief Engineer
- Program Manager B
- Chief Engineer
- Program Manager C
- Chief Engineer
- Engineering
- Systems Engineering
- Data Base team
- Hardware team
- Networking team
- Operational Processes and Training team
- Testing team
- Software Engineering
- Software Team 1
- Software Team 2
- Software Team 3
- Software Team 4
- Software Team 5
- Software Team 6
- Legal & Financial
- Legal Representative
- Financial Officer
- Systems Engineering
- Program Manager A
- Contractual
The FERB leader was responsible for handling Requests For Changes (RFC) to the contract from both the government and MC3I. My duties and responsibilities were to be the FERB leader to get FERB working properly and efficiently (as it was not currently so doing) and the management of two other FERB members, an MC3I engineer responsible for processing MC3I initiated RFCs, and a clerical assistant. I was also to be responsible for the processing of RFCs from the government, which were the majority of RFCs that FERB processed. This involved receiving government RFCs, evaluating them for distribution to the responsible manager(s) for the change, and distributing the changes to the appropriate managers for them to determine the technical, cost, and schedule impacts of the RFC. A meeting would then be held with all the responsible managers to determine the total impacts for the RFC; the results of such meetings would be presented by the FERB leader at the weekly Friday morning Contract Management Board meeting. The Contract Management Board was composed of the General Manager, Program Manager, Chief Engineer, Systems Engineering Manager, Software Engineering Manager, and the Financial Manager of MC3I. The Contract Management Board would approve, modify, or reject the managers’ recommendations. If approved or modified by the Contract Management Board, a statement of the technical, cost, and schedule impacts would be prepared by the FERB leader and forwarded to the government for review and approval or rejection. If the government accepted the change, then FERB was to inform the Contract Management Board and the managers of the acceptance, who would then incorporate the change into the contract. If the Contract Management Board rejected the managers’ recommendations, then the FERB leader would restart the process to incorporate the reasons for the rejection and to represent it to the Contract Management Board for their approval, modification, or rejection.
This job was essentially a paperwork job being given to me, a highly technically skilled and abilities person. But I applied my rule of if it's worth doing, it was worth doing well, and I did it well. Within several weeks I had the FERB organized and operating efficiently, and then I spent several more months being the FERB leader. After about four months of being the FERB leader, my manager called me into his office and informed me that the Contract Management Board and all the technical managers thought that my efforts were outstanding, and they wanted me to become the permanent FERB leader. But I hated this job; I hated getting up every morning and going to this job, I hated every minute I was doing this job, and I couldn't wait to leave it at the end of the day to forget about this job. But I always did it very well. I informed my manager that if he could not find a job that utilizes my technical skills and abilities within GE, I would start looking for a job that utilizes my technical skills and abilities outside of GE. He laughed! He informed me that he had told everybody that he did not expect me to accept this job, and he thought I would outright reject the job (he knew and understood my frustration with this job). He then proposed another job for me that had just become available—CALMA.
At the beginning of my FERB leadership, I was introduced to the Software Engineering Manager, Tony Meluskey, with whom I became very friendly. There was no mistaking Tony for a person of Polish heritage, as his name implied, and his appearance was of a traditional Polish shipyard worker. In one of our chats, he related the story of his parent’s recent visit to their homeland, and I inquired seriously but facetiously about what part of Italy they were from. His stunned look was priceless, and after a few moments, I began to laugh. He shook his head and remarked that I had really gotten him on my facetiousness and began to laugh with me about his incredulousness.
Working at MC3I could be very stressful due to security rules and regulations and the demands, size, and importance of the MC3I contract. During the time I was the FERB leader, I encountered the Financial Officer in the men’s room and remarked to him that he looked terrible and should see a doctor. He informed me that he was just very tired because of the intense financial renegotiations with the government that was necessary as the contract was being enlarged and restructured. I found out that a few minutes after I had left the men’s room, the Financial Officer collapsed and died in the men’s room. I vowed that I would not collapse and die from work-related issues. MC3I named a conference room after him, which was little comfort to all of us who knew and liked him.
In retrospect, being the FERB Leader allowed me to showcase my abilities to all the managers and upper management at MC3I, with which they were well pleased and which stood me well in my future career in MC3I. I also developed a personal relationship with all of them, which made my future working relationship with them much more harmonious, and I was often considered for important assignments as the MC3I management was well aware of my skills and abilities.
CALMA
GE had just purchased another company, CALMA, that developed and manufactured Computer-Aided Design and Manufacturing (CAD/CAM) equipment and software that was highly technical and engineering-oriented. However, this new company lacked the skills of a database designer and developer that they needed to create the software to manage the CAD/CAM drawings, and they needed assistance in this area of the CAD/CAM system they were manufacturing. They had hired an outside contractor to develop the software and database that would be needed for this product. However, they were concerned about the skills, abilities, and capabilities of this outside vendor. They wish to have somebody evaluate what this contractor was doing to determine any issues, concerns, and problems and propose solutions for anything that was discovered with the software contractor’s efforts. So, off I went to CALMA’s headquarters on the other side of the country, in Sunnyvale, California, to perform this evaluation.
Originally, I was scheduled to be there for three weeks, but after one week of the initial evaluation, I determined that it was a much larger job than the original three weeks, as I had already discovered several major problems. After presenting my initial results to the management of CALMA, they agreed it was a larger job, and they were willing to hire me for the larger job, which would take three months to accomplish. The hotel I was staying at in Sunnyvale was a Residence Inn, which was constructed much like a two-story apartment complex, with each room being laid out and furnished like an open one-bedroom apartment. This made my extensive stay much more comfortable and homier.
As I had an infant daughter a little over a year old, this put added effort on my wife to take care of her while I was away for three months. However, GE M&DSO had a policy that if you were on a business trip for over three weeks, you could return home for a weekend at their expense, or your spouse could travel to your work location at their expense (but not your children’s expense) for a visit.
The first two times I utilized this policy, I flew home to be with my wife and child; however, the third time I utilized this policy, I had my wife come to Sunnyvale, California, on a two-week vacation from her job, accompanied by our daughter. This was because CALMA and GE agreed to let me take a one-week vacation in the middle of my efforts for CALMA. We started our vacation by traveling to San Simeon, California, and the estate of William Randolph Hearst. After two days of visiting the estate, we traveled across California to Yosemite National Park for a three-day visit to the park. We then traveled back to Sunnyvale, CA, through the California Wine Country and spent the final Saturday and Sunday touring San Francisco, California. We also were able to squeeze in a visit to the Winchester Mystery House in San Jose, California.
On the first morning after my wife and daughter arrived, my daughter was standing up in the crib at the end of our bed, which the hotel so generously supplied, and when we awoke, she yelled out, “Happy Days!” These were happy days, and we all enjoyed this vacation.
After I went back to work from my vacation, my wife and daughter went to San Diego to visit a college chum of hers, from which she planned to drive to La Cañada, California in the county of Los Angeles, where she was to meet her parents who were visiting her godparents. In the middle of this week, my CALMA manager asked if I could go to San Diego, California, to brief their local office on the computer system that was being developed (they were computer systems experts that wanted to know what I was doing). I readily agreed and flew to San Diego on Thursday morning and briefed them in the afternoon. I then joined my wife and daughter at her friend’s house on Friday and then drove us to La Cañada very early Saturday morning, where we stayed in her godparent’s house. Her godfather gave my wife, daughter, and me a car tour of Los Angles on Sunday. I then flew back to Sunnyvale very early Monday morning to continue my CALMA efforts, and my wife and daughter spent the next few days with her parents and godparents in La Cañada, and they all visited Disneyland on one of those days.
Ilie Năstase was a World No. 1 Romanian tennis player. He was ranked world No. 1 in singles from 23 August 1973 to 2 June 1974 and was the first man to hold the top position on the computerized Association of Tennis Professionals (ATP) rankings. Ilie Năstase is one of the ten players in history who have won over 100 total ATP titles, with 64 in singles and 45 in doubles. He was also a guest at the hotel I was staying at, staying directly over my room, where he was competing at a regional tennis tournament. I met him in the parking lot on three occasions, where we had a brief, pleasant chat. I should also mention that all three times I met him in the parking lot, he had a different beautiful woman draped around him.
One Sunday afternoon, after I had returned from my excursions of the weekend days in which I explored San Francisco and its environs, I noted a small group of people in the lounge in the hotel foyer, where they served complimentary beer and wine between 4:00 PM and 6:00 PM. This group was speaking in an accent that sounded Australian to my ears, and after we introduced ourselves, I discovered that they were indeed Australian. They had checked into the hotel for a week’s stay, as they were attending a training course from a Silicon Valley vendor of a complex piece of software that they were going to utilize in their company’s business operations. We sat together, drank beers, and swapped stories. One of the group members was late to this gathering, and he and his wife showed up around an hour later. It turned out he was not Australian but had been born and raised in Philadelphia, PA (my hometown), and had immigrated to Australia ten years previously. He and his wife, and I spent the next two hours talking about Philadelphia and what had happened in Philadelphia since he had left. As the Australians got up to leave for dinner, his wife personally and privately thanked me for spending so much time discussing Philadelphia with her husband, as her husband had expressed some homesickness on the flight to Sunnyvale, and our discussion was like a tonic for him.
A few days later, I again hooked up with the Australians in the lounge, except this time they had bought a half dozen cases of Foster’s Australian beer that they were consuming. These beer cans were 32 oz. apiece, and they were drinking them like they were iced tea. They invited me to join them, and they plied me with about six cans of beer in the next three hours. Needless to say, by the time they decided to go to dinner, I was pretty much plastered by imbibing six 32 oz cans of beer, and when they invited me to dinner, I politely declined to go to bed and sleep off the beer. The next day at work was not very productive, as I was still feeling the effects of the beer, but I did learn one important lesson—never get into a beer-drinking fest with Australians, as you will come out second best in this fest.
One weekend I decided to visit San Jose on Saturday and drive down the Pacific Coast highway on Sunday. San Jose was an interesting place, and I revisited San Jose on another weekend. I arose and started my trip down the Pacific Coast highway at sunrise on Sunday, as I wanted to get an early start so that I could see as much of the Pacific Coast and Big Sur as possible. Big Sur has been called the "longest and most scenic stretch of undeveloped coastline in the contiguous United States", and after my drive along the Big Sur, I can attest to the truthfulness of this. My plan was to drive down the Pacific Coast highway until midafternoon, then cut over to the West Side Freeway to return to Sunnyvale. During this drive, I made short stops at Santa Cruz, Salinas, and Monterey, then proceeded down the Big Sur. I pulled over into a lookout rest stop to enjoy the view and noticed that another person traveling north had pulled over at another lookout spot about 100 yards away from my lookout spot. This person then proceeded to take a bagpipe out of his car and then started to play bagpipe music for the next half hour. I sat, watched, and listened to his playing and the scenery for the full half hour. When he finished and proceeded north, I then proceeded south. When we passed each other on the Pacific Coast Highway, I noticed on the side of his car an emblem for a Scottish Bagpipe Marching Band, which gave reason to my opinion that he was a very good bagpipe player.
Being an amateur astronomer, I also visited Lick Observatory one Saturday. The Lick Observatory is an astronomical observatory owned and operated by the University of California. It is on the summit of Mount Hamilton at an elevation of 1,283 meters (4,209 ft) above sea level, in the Diablo Mountain Range just east of San Jose, California, United States. It houses the historic James Lick Telescope, which is a refracting telescope built in 1888. It has a lens 91 centimeters (36 in) in diameter—a major achievement in its day. The instrument remains in operation, and public viewing is allowed on a limited basis. Also called the "Great Lick Refractor" or simply "Lick Refractor", it was the largest refracting telescope in the world until 1897 and now ranks third.
The drive to the observatory was via a narrow, steep two-lane asphalt paved road that had many curves and a speed limit of fifteen miles per hour. It took over a half hour to reach the observatory, and to my surprise, I was the only visitor to Lick Observatory this Saturday morning. I engaged in a personal discussion with the volunteer tour guide, who I discovered was a fellow amateur astronomer. When I told him that I was an amateur astronomer and that I was a volunteer that operated the Franklin Institute Observatory, he gave me a closer and more detailed look at the James Lick Telescope, which was generally unavailable for public tours. He then informed me he was planning an observation session at his Amateur Astronomy Club private telescope that evening. This Amateur Astronomy club had a 16” reflecting telescope located on a mountain top in the Diablo Range just west of Sunnyvale. He invited me to join him in this observing session that evening. We agreed to meet at the base of the mountain top, where he would drive me to the observatory, as it was too dangerous for anyone to drive on the road in the dark to and from the observatory without knowing the way. Upon arrival at the observatory, and just as the sun was setting, a thick cloud bank rolled in from the Pacific Ocean. This cloud bank was lower than the mountaintop and effectively blocked the light pollution from Silicon Valley. This cloud bank made for extremely dark, clear, and steady skies above the observatory, ideal conditions for observing the heavens. We spent the next four hours observing in one of the best observing sessions that I have ever had as an amateur astronomer. For his kindness, I mailed him a diskette of a CP/M microcomputer dBase database with over three hundred deep sky objects and their positions and descriptions that I had been compiling on my CP/M microcomputer for the last few years. He assured me that he and his club could utilize this database when they planned their observation sessions.
For the three months of my effort at CALMA, I applied my rule of if it's worth doing, it’s worth doing well, and I did it well, and I was able to resolve all the issues, concerns, and problems with this computer software and DBMS. CALMA had assigned two of their junior programmers to this computer system who would be responsible for maintaining this computer software and DBMS after the contractor finished their efforts. These junior programmers were unfamiliar with DBMS technology and how to program DBMS queries, additions, deletions, and updates. I took it upon myself to instruct them in DBMS technology and how to program commands for the DBMs to query and update the database. I also introduced them to Yourdon Structured System Analysis and Design, as I discovered that the computer software that was being developed by the subcontractor had many elements of Yourdon programming techniques that they needed to know to maintain this computer software. On my last day at CALMA, they expressed their gratitude to me for doing this, and they commented that they now thought that they could properly maintain this computer system, which they initially had many doubts about being able to do so.
During my evaluation efforts, I sometimes requested that the subcontractor make changes to their computer software, which they recognized as worthwhile changes that they implemented. I also made changes in the DBMS structure that allowed the DBMS to operate more efficiently and consume fewer computer resources. I also created a query and editing (add, delete, or change data in the DBMS) capability written in the fourth-generation programming language of the DMBS that I needed to do the evaluation, and the two junior programmers would need to maintain the computer system. I also created the backup/recovery and maintenance procedures for the DBMS, which I also needed for my evaluation, and the junior programmers would also require to do their jobs.
On my last day at CALMA, I reported on the results of my evaluation and the remaining efforts the subcontractor needed to undertake to correct their computer software problems. As a result of my efforts, CALMA was able to successfully manufacture its product with this subcontractor’s capability. CALMA’s President was so satisfied with my efforts that he wrote a glowing letter of commendation to the President and CEO of GE (Jack Welch). Jack Welch personally read this letter and passed this letter down the chain of command with a note that I should be considered a very valuable employee of M&DSO. The management at MC3I was so impressed that Jack Welch had personally done so that they approved his recommendation that I would be considered a valuable employee, and I began to receive important assignments.
Wrangler and JMIE
Upon returning from CALMA, I was informed that they had a technical problem with another contract, Wrangler, that required my skills and abilities to help resolve. Wrangler and JMIE were significant computer software upgrades to preexisting DBMS computer systems. The Wrangler DBMS programming team needed a query and editing (add, delete, or change data in the DBMS) capability written in the fourth-generation programming language of the DMBS for the purpose of program development and testing. They allocated nine weeks of my time to create this capability, but because of my skills and abilities, and my previous experience with this type of capability, I was able to accomplish this effort in three weeks. They then asked that I do the same thing for another contract, JMIE, which had a different DBMS and fourth-generation programming language, which took me another three weeks to accomplish.
Promotion
After my efforts in FERB, CALMA, and Wrangler / JMIE, I was called into my manager’s office for a performance appraisal. I was concerned about this performance appraisal, as my manager and I often disagreed with each other. My manager noted these disagreements and thanked me for disagreeing with him. He explained that my disagreements with him were so intelligent and reasonable that he always considered them in making his decisions, and he appreciated them as they often led to better decisions by himself. He also noted and appreciated that after he had made a decision that I disagreed with, I carried out his instructions to the best of my ability without complaints or grumbling. He asked me to continue disagreeing with him when appropriate, as it made for better decisions by him and helped him to become a better manager.
He then informed me that my efforts were so outstanding that upper management decided that I was hired at the wrong pay grade and that I was to be promoted two pay levels and receive an additional 25% salary increase. It was also very fortunate that I finished the Wrangle / JMIE task in so short a period of time because when I finished these tasks, it coincidentally happened that they had received a new 18-month contract for which they were staffing up. It was decided that I would be the technical lead on one portion of this contract, the LTMS portion of this contract.
LTMS
LTMS was a project that involved two other government contractors working on a classified government contract for a classified agency. This agency was tasked with analyzing intelligence information and providing other classified agencies and departments with the results of their analysis. The Director of this agency was very concerned that with the increasing requests and workload of his agency, they would not be able to meet the future demands on his agency’s services. He, himself, lit upon the idea that if was possible to connect an electromechanical device that the analyst used in their efforts with the new workstation automation of the analyst tasks and transmit the data from the electromechanical device to the workstation computer, which performed calculations on the data, the analyst’s efforts would be more efficient, and the turnaround time would be significantly reduced.
The managers at the classified agency were very concerned about whether it was technically feasible to interface the electromechanical device and the workstation computer. This was at a time when the main attachments to a workstation were a monitor, printer, keyboard, and mouse, and other equipment attachments were few and far between that took extensive engineering effort to accomplish. As the electromechanical device was not designed nor manufactured to support this capability of transmitting information, it was necessary to redesign and retool the electromechanical device to accommodate this capability. They were also concerned that the calculations of the workstation computer would not be sufficiently accurate to be useful due to the precision of the data being sent from the electromechanical device to the workstation computer. Nevertheless, the Director of the agency instructed them to try and determine the feasibility of his idea by attempting to do this with one electromechanical device and one workstation computer. If they succeeded, it would then lead to a follow-on contract with the two contractors to do this for all electromechanical devices that could be attached to the workstation computers. He created an agency team to manage this effort, consisting of a middle manager of the agency, who was a former analyst who was appointed as the Contracting Officer Technical Representative (COTR) that was responsible for all technical decisions of the LTMS system. The Director also assigned two other senior analysts on a part-time basis (they only attended the meetings) to the LTMS project agency team.
Although this follow-on contract would be profitable for both contractors, the two contractors were feuding with each other. The electromechanical device contractor, who had a long-standing relationship with the agency, had just lost the contract for the new workstation automation of the analyst tasks to the other contractor. The electromechanical device contractor was concerned that they would lose influence at the agency to the contractor for the new workstation automation. The contractor for the new workstation automation was indeed trying to increase their influence at the agency, and both contractors were being non-cooperative with each other. The GE M&DSO Systems Integration department, which provided legal and bureaucratic support for large government computing projects, and which had a contract to provide this support for the agency in the new workstation automation project, suggested that the agency hire a GE M&DSO MC3I engineering department who would be responsible for the technical integration of the one electromechanical device to the one workstation computer. As GE M&DSO MC3I had a small contract with the agency to provide a Management Information System to keep track of the informational request of the agency, and also keep track of the progress of these requests and assist in the scheduling of the analysts to these requests, this was easily doable as an add-on to our contract with the agency. The agency did so with the implied threat that if the two contractors did not start cooperating with each other and making a good-faith effort to successfully achieve the goals of the LTMS system, then the entire LTMS effort would be turned over to the GE M&DSO MC3I engineering department.
GE M&DSO MC3I had no interest in taking over the LTMS project, as it did not fit into their business goals. However, they were very interested in establishing a good relationship with the agency, as that could be a pathway to other classified contracts with other classified government agencies. They, therefore, undertook this LTMS integration task, and I was assigned to become the lead and initially the only engineer for this integration task.
My first task was to find a means to end the feuding between the two contractors and get them working together to solve the technical issues and produce something that would be useful. I did this by only providing technical opinions to the COTR, and the COTR would assign tasks to one of the two contractors based on my opinion, and I would only be responsible for documenting the decisions and monitoring the progress of the other contractors’ efforts. I, in effect, became the enemy of my enemy of the two other contractors, who soon realized that the agency's management was always following my opinions and that they needed to pay attention too and consider my opinions. I also always presented a non-threatening attitude and, as a technically intelligent person to the two contractors, I also balanced the two contractors’ issues and concerns to reach a reasonable opinion. They gradually accepted me as an important part of the LTMS effort, and I maintained a friendly relationship with both contractors throughout the contract.
The design stage, which took about five months, consisted of determining how the workstation computer and the electromechanical device needed to be modified to connect to each other. After the connection details were established, we then determined the design changes to the electromechanical device and the new control box that would be added to the electromechanical device to send the data, the functionality required for the interface device driver of the workstation computer, and the control mechanization that managed the communication between the workstation computer and the electromechanical device. We then determined what data and the format of the data that was to be sent from the electromechanical device to the workstation computer. The data and the format were determined based on the many algorithms the analyst wanted to invoke to perform the necessary calculations. We also designed the Graphical User Interface (GUI) for the workstation computer. As there were over thirty algorithms that could be invoked, this was a time-consuming design process. It was my responsibility to balance the wants and needs of the two contractors, recommend a course of action to the agency’s management, and document all that was decided in the design phase in an Interface Control document. The design phase required extensive travel for the two contractors and myself to the agency’s headquarters in Washington D.C. and occasional travel to one or the other contractor’s locations, which were nearby Denver, CO, and Dallas, TX. It also involved one trip to Los Angeles, CA, at the end of the design stage to brief the agency's satellite office management on the design of LTMS.
I booked a very early morning flight to Los Angeles for this briefing and an early evening flight back to Philadelphia. This briefing only took two hours in the morning, and I had the rest of the day to explore Los Angeles in my rented car, which turned out to be a convertible car, as the rental agency had no other car available that day, and they charged me the rental fee for the intermediate car that I had booked. I decided to change my flight back to Philadelphia from early evening until late evening to take full advantage of the time I had to explore Los Angeles. I visited many tourist attractions in Los Angeles and arrived at the airport for my 11:30 PM flight. When I checked in for my flight, the check-in receptionist informed me that there would be a forty-five-minute delay in the flight. She also informed me that since this flight was to occur after midnight, I could upgrade my seat to first class for an additional twenty dollars. I informed her that I was not permitted to fly first class on a business trip, and she informed me that if I gave her cash, my company would never know I had flown first class. I immediately gave her a twenty-dollar bill and was seated in first class. This was a luxurious seat in that all drinks and food were free. After we took off and I put my seat back into its fully prone position, and I immediately fell fast asleep. The next thing I knew was the flight attendant waking me up and requesting that I put my seat in the full upright position as we were about to land in Philadelphia. Thus, I got to fly first class but did not get to enjoy any of the amenities of first-class seating, except the very comfortable seating of first class.
Every time I visited Denver, my breakfast was complimentary at the hotel I stayed at, and my lunch was complimentary at the Denver contractor’s cafeteria. This left my full daily meal allowance expense for the day to dine at some nice restaurants in the Denver area. On my trips to Denver, I discovered that Denver was the main shipping point for fresh seafood from the Gulf of Mexico and the eastern United States to the west coast of the United States, and therefore had plentiful, varied, and inexpensive seafood served at many restaurants. One of these restaurants, The Board Room, located in the center city of Denver, was famous for its seafood sampler platter and large shrimp tray entrée, and I dined at this restaurant a few times when I visited Denver. I also discovered a small steakhouse and tavern, The Aurora Sunset, located In Aurora, CO, just outside of Denver, where I stayed on my trips to Denver, that served some of the best steaks that I had ever eaten. Every time I visited Denver, I always had a different steak meal at this restaurant, which never disappointed me. Alas, I did not have the same meal experience in Dallas, as although my breakfast was complimentary at the hotel I stayed at, the Dallas contractor had no cafeteria, and I had to buy my lunch outside the Dallas contractors’ location. I was also staying far enough outside of Dallas that I only once visited Dallas to view the sights, and the restaurants around where I was staying were good but nothing special. As for my visits to Washington D.C., my breakfast was complimentary at the hotel I stayed at, the government agency where I was working had a cafeteria that all were required to use for security reasons, but all were required to pay for their cafeteria food. As I was staying at an Alexandria, Virginia hotel, there were many fine restaurants around the hotel, and the hotel restaurant also had very good meals; it was not necessary for me to go to Washington, D.C., to dine. However, and one meeting that I and another MC3I attended, he mentioned to me he knew of a restaurant on the northern border of Washington D.C. that had excellent food but was a bit of a dump, and he commented to me that the presence of a horse could improve its décor. We went to this restaurant, and I agreed that the food was excellent, and the décor was a dump. The meal was so good that I occasionally went to this restaurant by myself on my other trips to Washington, D.C.
Near the end of the design phase, the COTR began discussions of how to test the LTMS system and how to train the analysts in the usage of the LTMS system. He asked each contractor to submit a proposal for the testing and training of the LTMS system. A few weeks later, they submitted their proposals, and the COTR and the two other agency analysts reviewed these proposals. Legally I was not permitted to review these proposals, as they contained confidential company information, but the COTR was able to extract the technical portions of the proposal that did not contain any confidential company information. He then asked me to review and comment on this technical extraction that would illuminate any issues or concerns that I had about the testing and training for the LTMS system. We all found these proposals to be lacking, as the workstation computer contractor proposed a Computer-Based Training (CBT) system, and the electromechanical device contractor proposed individual training for the several hundred analysts that would utilize the LTMS system. Also, both contractors did not pay sufficient attention to the other contractors' portion of the LTMS system. The testing procedures were insufficient for a systems test, as they concentrated on testing the components of the LTMS system, while the training proposal required efforts by the other contractor to supply training materials. These proposals were unmanageable in their execution and untenable to the agency’s management, thus leading to the agency’s conclusion that these proposals were deficient in their testing and training. The COTR also informed me that the costs associated with each contractor’s proposal were excessive and could not be funded. The COTR then asked me to submit an unsolicited proposal from MC3I for the testing and training of the LTMS system.
After discussing this with the Systems Testing Manager, and the Systems Operations Manager (who was responsible for training and operational procedures) of MC3I, we decided on a simplified testing and training proposal. With my knowledge of LTMS, and my assistance in the development of the testing and training materials, the Systems Testing Manager planned to develop a testing approach from the perspective of the LTMS analyst’s workflow. The Systems Operations Manager proposed that we train a small cadre of the agency's analysts on how to utilize the LTMS system and algorithms, again from the perspective of the LTMS analyst’s workflow. This cadre would then be responsible for the training of the other analysts, using the materials we supplied to train them when an LTMS system was installed in their work area. We were able to produce a testing and training proposal in three weeks, which we then submitted to the agency. A few days after our submittal, the COTR informed me that our proposals were what the agency needed and required and were within the budget for testing and training of the LTMS system. They were in the process of preparing a contract for MC3I to provide the testing and training for the LTMS system, which was signed by both parties a week later.
After the contract was signed, I went to the Systems Testing Manager to begin his efforts, and he assigned a part-time testing supervisor to start the detailed testing efforts, with a plan to assign a full-time testing engineer after the testing supervisor and I had concluded our preliminary work. When I went to the Systems Operations Manager to begin his efforts, he had some bad news for me. The person who he had planned to assign to the LTMS training effort was Awaiting Clearance but had been expected to be cleared by the time of the start of the LTMS training effort. Unfortunately, this person was denied clearance, and he had no person available to assign to the LTMS training effort.
We glumly looked at each other, as we both knew that the contract was signed and that we had to come up with a solution to this problem. After talking it over, he asked me if my workload was full-time during the LTMS development efforts of the two contractors. I had to admit that I did not expect a full-time effort in my efforts as the lead engineer, as I only expected that I would have to attend the monthly one-day meeting at Washington D.C. and a two-day meeting in Denver or Dallas on alternative months, and a weekly one-day review of the contractor’s status reports at MC3I. Therefore, I had a window of three weeks in a month that I had planned to support the MC3I testing and training efforts. The Systems Operations Manager suggested that I utilize this window to write the User Manual we planned to create and that he would supply a full-time training person near the end of the training development to create the Tabletop Reference Guide and Training Presentation materials that we were also contracted to create based on the User Manual. At the end of the LTMS system testing, this full-time training person and I would provide three weeks of training for the small cadre of agency analysts on how to utilize the LTMS system and algorithms that we were also contracted to provide.
When I protested that I had no training experience and may not be capable of writing a user manual, he offered to assign his most experienced trainer, on a part-time basis of six hours a week, to supervise and assist me in the creation of this user manual. As we had no other option, we decided on this course of action. This would, however, require that we modify the LTMS Integration and Testing and Training contracts to reflect this change. When I informed the COTR of this change, he understood the need for the change and that he thought this was a good idea as it would save them money, as my hours were reduced in the LTMS Integration contract and shifted to the LTMS Testing and Training contract with no additional costs to the Testing and Training contract. He also remarked that he thought that I was the best person to write the user manual and conduct the training based on my knowledge and experience with the LTMS integration, and I would not have to be brought up to speed as another training person would have to be.
At the next monthly meeting, it was announced that MC3I would provide the LTMS Testing and Training for the LTMS system, and the other two contractors seemed passive in their acceptance of this arrangement. I later learned that both contractors were not enthusiastic about providing testing and training because of the interruption to their development efforts that this testing and training development would entail, and they were relieved when this task was assigned to MC3I. I also introduced the MC3I Systems Testing supervisor and the Systems Training supervisor, who presented our plans for testing and training. They all agreed that this was a good testing and training plan, but they also all agreed that the Systems Testing supervisor was somewhat confrontational and abrasive to the two contractors, and they privately asked if he could be replaced. The COTR also thought it would be a good idea if he was replaced, and I agreed with him that it would be best for the LTMS project to replace him. When I returned to MC3I after this meeting, I discussed this situation with the Systems Testing Manager, and he also agreed that he should be replaced, and he assigned another testing supervisor, who later became my Program Manager in the TADMS effort, who was much more diplomatic but less experienced in testing. This did not turn out to be a problem, and when I introduced the new Systems Testing supervisor to the COTR, he very quickly realized that the new supervisor of testing was the best person for the job.
When the Systems Operations Manager formally introduced me to the Systems Training supervisor, Phil Talkin, we only knew each other to nod a hello as we passed each other in the hallways. It wasn’t until he started working on LTMS that I became friends with Phil, and we became best friends both professionally and personally. After we were formally introduced, we began an hours-long discussion about LTMS. Phil inquired if the User Manual had to be developed under Military Specifications (MILSPEC), and I replied in the negative and that we were free to develop the user manual any way that we saw fit to meet the requirements of the analysts who would be using this manual. Phil’s eyes lit up as he always wanted to create a user manual that was not MILSPEC, and he had often thought about how he would do so. In addition, since all the analysts that would be utilizing the LTMS were college graduates, highly intelligent, and independent thinkers with varied backgrounds, this user manual would have to be written with this in mind. He told me about his thoughts on how we should write this user manual, and I agreed that this was the best approach for the LTMS User Manual. He also decided that it would be best for the LTMS training that he relocate his cubicle across from my cubicle, as this would allow me to simply turn around and ask a question of him or to receive direction from him when I encountered issues or concerns. This was possible as I was the only person working in the corner of this room, as I needed to be isolated as only a few persons at MC3I had the proper security clearances to see the intelligence information that I utilized in my LTMS efforts (Phil also had the proper clearances, as well as the other personnel who were assigned to the LTMS contract).
As I was the engineering leader of the team, and I was also an individual contributor as the developer of the user manual under Phil’s direction, it was required that I write a weekly status report to Phil, which he would then pass on this status report to me as the engineering leader, so that I as the engineering leader could then pass it on to the agency’s COTR. At the end of the first week, I wrote my first status report to Phil and left it on his desk, as he was not present when I finished this status report. I left my cubicle for a time to work with the Systems Testing supervisor. When I returned to my cubicle and found Phil present, I sat at my desk and discovered my status report on my desk full of red ink. There was not one single sentence in this status report that Phil did not correct for spelling or grammatical errors. I turned around to Phil in a state of shock, and Phil took one look at me and started laughing, then began to console me. He commented to me that in the week he had been working with me, he had formed the opinion that I was one of the most intelligent and flexible technical people he had ever worked with. He also informed me that, like most technical persons, I had difficulty with spelling or grammar and communicating technical information to non-technical persons. He volunteered to mentor me to overcome these deficiencies if I was agreeable. I looked at my status report, then back to Phil and said, “Apparently, I need the mentoring.” Phil chuckled and remarked that it was important that we do so, as the LTMS User Manual was to be written for non-technical persons. We spent the next hour talking about my shortcomings as a writer and communicator (which I now freely admit), and Phil mentored me to improve these skills, as well as imparting to me his training knowledge and skills. This he cheerfully did, and I am eternally grateful for his generosity in sharing his knowledge and counsel and improving my communication skills when dealing with non-technical people.
Phil was a very intelligent, very knowledgeable, very congenial, and conversant person not only in his training capabilities but in many areas of arts and literature, the sciences, and history, and it could truly be said of Phil that he was a Renaissance Man. Many of his interests were also interests of mine, which solidified our friendship. His last name was also apt, as Phil loved to talk, and he had difficulty knowing when to stop talking. This became a problem at one of our monthly development meetings, where Phil was scheduled to give an outline and progress report presentation on the MC3I training efforts to the COTR and the other contractors. Phil had prepared an excellent presentation that we both agreed provided an accurate state of our efforts in the training development. When he gave this presentation, he had everybody eating out of his hand. But then he started talking beyond the presentation materials about issues and concerns of the training that had not been resolved, I could see that the COTR and the other contractors were becoming alarmed, and I almost literally had to drag Phil off stage. I then informed the COTR and the other contractors that these issues and concerns were not significant, that we were working on resolving them, and that we would provide them with status updates of these issues and concerns at a future monthly development meeting, which seemed to mollify them. When Phil and I were driving back to our hotel rooms, I had to mildly dress him down for going off script, and I reminded him that I was also playing a political game of goodwill that required some delicacy as to what MC3I presented to the agency and the other contractors. Two months later, Phil provided another presentation at the monthly development meeting, which addressed the resolution of these issues and concerns, and he did not go off script. The other problem Phil had was that he was constantly late for appointments. I informed him that this would not be acceptable and that I would gladly mentor him on how to not be late for meetings if he allowed me to do so (he laughed). His main lateness problem was that he would start conversing with someone before a meeting and lose track of time. I, therefore, undertook the effort to find Phil well before the meeting started and direct his efforts to get ready for the meeting, cutting off any conversation that he and others wished to engage in before the meeting.
The LTMS testing and training development required that I work closely with a small, specialized agency team that did the computational algorithms on their large and very expensive electromechanical device, which provided support to the analysts in their efforts. This required that they and I select sample intelligence information that could be utilized for the testing and training. I also had to learn how the computational algorithms functioned to properly document the algorithms in the LTMS User Manual. This small, specialized agency team had never documented these algorithms nor how to utilize the algorithms with the intelligence information on their electromechanical device. Each of the team members had personal notes and comments about the algorithms and how to utilize the algorithms—but no formal documentation. They, therefore, needed to make a copy of their personal notes and comments on the algorithms, apply these algorithms against the selected sample intelligence information, and provide me with the results of their computations. After I created the LTMS manual, this specialized agency team realized that if they replaced the LTMS electromechanical device operation with the operation of their electromechanical device, they would have an excellent user manual for their department's use, which they all had wanted but were too busy to develop. They, therefore, decided to do this, and they finally had a user manual for their department.
The members of this small, specialized agency team were scientists that were considered to be the best in their field by the agency but had no recognition outside of the agency due to the highly classified nature of their work. I, therefore, decided to add a paragraph to the Acknowledgement section of the LTMS User Manual that named each member of the team, along with the acknowledgment of the names of agency personnel who were involved in the LTMS system project. This was the first time in the agency's history that a user manual ever acknowledged the contributions of the agency personnel to the development of any system contracted by the agency (and they all appreciated that I did this)
After I received a copy of their notes and comments, the selected sample intelligence information, and the results of their computations, I needed the two MC3I graphic artists to create scientific diagrams of the algorithms and drawings of the selected Intelligence information, which were to be included in the LTMS testing and training documentation. This was no easy task (as such drawings at that time were all hand drawn), and there were over one hundred drawings that they had to create. All of these drawings required detailed accuracy to be reviewed and approved by the small, specialized agency team at the agency. As these two graphic artists were busy on the main contract of MC3I, the lead graphic designer decided to take on additional work to free up the other graphic artist to create the LTMS drawings. They also started to work nine hours a day and occasionally on Saturdays. Fortunately, they were hourly employees that were paid overtime for their efforts. MC3I also had PRIDE (Professional Recognition for Individual Dedication to Excellence) awards that were awarded to approximately 10% of the MC3I staff at the yearly Christmas party. The two graphic artists that assisted me in the LTMS project were worthy of receiving these awards, but in the past, the PRIDE awards had only been given to the engineering staff in MC3I. Nevertheless, I decided to nominate the two graphic artists for a PRIDE award. The General Manager of MC3I commented on these nominations for a non-technical person, but I was able to justify their nominations. The MC3I General Manager decided to open the PRIDE awards to any person on his staff that deserved them. When the PRIDE awards for these two graphic artists were announced, along with the decision to open the PRIDE awards to any person on his staff that deserved them, the non-technical staff thanked me for opening the PRIDE awards for non-technical persons on the MC3I staff. The two graphic artists were exuberant about winning the PRIDE award and proudly displayed their PRIDE award certificates on the wall behind their graphic art tables.
The method to produce documentation in M&DSO was that the author would use pencil and paper to write the document, which was then submitted to the Wang computer Word Processing department, who would type up the document. Upon their completion of this typing, they would print out the document for the author to manually edit or correct their typing to produce the final document that met M&DSO standards (this was before the era of personal computers). I realized that this method was too cumbersome and time inefficient for the creation of the User Manual for the LTMS system. As there was an unused Wang computer Word Processing secretary station next to my cubical, I convinced MC3I management to allow me to write the User Manual on this unused Wang computer. I would write a chapter of the User Manual and then submit the diskette containing the chapter to the Wang computer Word Processing department for review to ensure it met M&DSO standards. This was the first time that an engineer had done this at M&DSO, and new classified security procedures had to be established for this process. The success of this process led M&DSO management to start using this process for other engineers that wrote extensive documentation as part of their efforts. Eventually, with the introduction of workstations at every engineer cubical, each having the capability of computer word processing, the utilization of workstations for documentation efforts became standard practice.
After we had finished creating the LTMS User Manual and the Tabletop Reference Guide and Training Presentation materials, we submitted them to the agency for review and approval. Within a week, the General Manager of MC3I received a letter from the Director of the agency stating that the LTMS User Manual was the finest user manual ever submitted to the agency and would be the future standard for which all other user manuals would be adjudged. After we submitted the Testing manual and submitted them to the agency for review and approval, they found it too detailed for the LTMS system testing, that it would take more than a few hours they thought the systems testing would take, but that it met the terms of the contract and was accepted. They changed their tune after the two days of systems testing, which was conducted by that agency analyst who was a part-time member of the agency's LTMS team. She remarked how easy and fun it was to follow the testing procedures, and it proved to her how useful the LTMS system would be in her job. A member of the small, specialized agency team was also present at the LTMS systems test, and when he compared her computational results to what they had computed for the selected sample intelligence information, they found the results to be within acceptable limits, and they approved of the utilization of the LTMS system in the efforts of the analysts. This system testing proved the technological feasibility of the LTMS system and that the calculations of the workstation computer were sufficiently accurate to be useful. After the LTMS system test was completed, the COTR thanked me for doing the system test in this manner, as there would be no need for him to prove the usability and accuracy of the LTMS system to the upper management of the agency, as the LTMS system testing was more than sufficient proof. When the Director of the agency was informed of the LTMS system testing results, he immediately directed the COTR to start the contracting process for the two contractors to produce one hundred units of the LTMS system, which made the two other contractors very happy.
Prior to the LTMS system testing, the LTMS development efforts by all proceeded apace for the next ten months. At the end of the development effort, I had to spend one week in Denver and two weeks in Dallas in my capacity as lead engineer, which was required for the unit testing and approval of the other two contractors’ development efforts. This posed no difficulty for MC3I’s testing and training efforts, as the LTMS System Testing plan was complete, the LTMS User Manual was complete, and the other training materials were being finished up under the guidance of Phil.
The Dallas trip also had an added benefit for me, as when I was in Dallas for two weeks, the Eagles were scheduled to play the Cowboys on Sunday between the two weeks I was in Dallas. The front desk of the hotel where I was staying managed to get an intermediate-priced ticket for me to attend the game at Texas Stadium, where my seat was located three-quarters of the way up on the forty-yard line of the Eagles sideline. When I arrived at the hotel the Friday afternoon before the game, I discovered the entire Eagles team was in the lobby checking in to the hotel. I got to meet and greet several of the Eagles Players that evening and three of them asked me if there was any nearby place to go for some fun. I informed them that the hotel was in the center of a large unpopulated plain, surrounded on all sides by highways and that without a car, there was no place for them to go. They were disappointed but resigned to Buddy Ryan’s diabolical plan to keep them in the hotel and out of trouble. The Sunday morning of the game, I met the late great Reggie White in the elevator, where we had a very short but pleasant conversation. As I picked up my ticket for the game from the front desk, they had a pleasant surprise for me in that they had packed a box lunch for my consumption during the game. I thoroughly enjoyed attending the game, made even more enjoyable by the Eagles defeating the Cowboys.
After the LTMS systems testing was complete, the engineer who developed the Tabletop Reference Guide and the Training Presentations and I conducted three sessions of four days a week to provide the agency's LTMS analysts cadre personnel with LTMS system training. All the cadre that took this training reported to their managers that they felt this was the best, most succinct, and most complete training ever provided by the agency, and the LTMS User Manual and Tabletop Reference Guide was the best and most useful user manual and reference guide they had ever seen.
This was the easiest and most relaxing three weeks I had spent in Washington D.C., as the training sessions were 9:30 AM to 3:30 PM Monday through Thursday, and all the trainees were very intelligent and affable, and excited and enthusiastic about the training. In addition, as the training sessions ended at 3:30 PM or shortly thereafter, my assistant and I were able to have an early dinner and then visit one of the museums in Washington D.C. that were open until 8:00 PM. As we both had a scientific and technological orientation, we had a mutual interest in the museums we visited. We also arranged to stay overnight on Thursdays by agreeing to drive to Washington D.C., very early on Mondays. As we were driving home on Friday morning and not arriving in the Philadelphia area until early Friday afternoon, it was not necessary for us to report to work, but instead, we went directly home for a long weekend with our families (and my dog).
After the LTMS system efforts were successful, the Director of the classified agency held a wrap party in his large luxurious conference room (as he often hosted the President and other high government officials in this conference room) for the agency and contractor personnel who were responsible for the success of the LTMS system project. At this wrap party, the Director noted MC3I's contributions to the success of the LTMS system and particularly praised me for my efforts. The Director also wrote a glowing letter of commendation to GE M&DSO senior management, commending my team and me for all our efforts. For my efforts, the MC3I General Manager awarded me with a General Managers Award for Outstanding Effort, which few people at GE M&DSO were ever awarded. This award was presented to me at a General Managers Award dinner at a fine local restaurant, which both my wife and I attended, as I was one of the few honored awardees. I also received a rather large bonus as part of this award. At this point, my career at GE was well set, and I continued to receive important jobs and positions of increasing responsibility and increasing salary.
Project 704
Project 704 was for the development of a computer system and database that would catalog the extensive Photos and Videos collection of the classified government agency that I had worked with on the LTMS system project. The Photo and Video department had a large text file on their workstation computer that cataloged the captions, the date, and geolocation name of their Photos and Videos collection, as well as the filing cabinet, drawer, and folder where the information was stored in the department. When they received a request to locate photos or videos, they opened this text file and did a find within the text file to locate photos and/or videos of interest. This was a cumbersome procedure that was fought with accuracy and thoroughness problems and which consumed much effort and time by the department staff to reduce these inaccuracies and make a more thorough search.
I was assigned to this project immediately after I finished the LTMS project, and I was given the responsibility of designing the database structure for the cataloging of the photos and videos and the procedures for backup and recovery and for the maintenance of the DBMS. I also developed the query and editing (add, delete, or change data in the DBMS) capability written in the fourth-generation programming language of the DMBS for the purpose of program development and testing. I was also responsible for the development of the query and editing capability for the various pull-down lists that would be utilized for the GUI of the computer system being developed. I was also responsible for the extraction of the testing data from the large computer text file that the department had maintained and the loading of this extracted data into the development database. I also created the testing procedures for the Project 704 computer system and assisted in the development of the User Manual.
During the course of this effort, it became necessary to spend two weeks at the agency’s headquarters to review their Photos and Videos collection and to interview the personnel that utilized these photos and videos to ensure that the computer system and the database design met all their requirements. In the first week of this two-week effort, my security clearance to enter the agency’s headquarters expired. When the guard at the front desk informed me of this expiration, I asked how long it would take to renew my clearance to enter the building. He responded that it normally took five to seven days to renew the clearance, and I was very tired from my LTMS efforts and needed a break. I thanked him and exclaimed, “see you next week”. The next thing I felt was a hand on my shoulder that was attached to the Director of the agency. He looked at me and said, “Sorry, Mark, you’re not going anywhere. I need you to finish what you’re doing.” He then turned to the guard and directed him, in his personal authority, to give me a one-week clearance to enter the building, and to accelerate the extension of my clearance for an additional three months. So, it was “Hi Ho Hi Ho, It's Off to Work We Go!!” for me.
I also spent a week at the agency’s headquarters installing and configuring the DBMS and the backup/recovery and maintenance procedures. I was also responsible for testing the population of the database with the extracted test data, with a program that was created by another MC3I software engineer to populate the database and remove duplicates from the database. Because of the impact on the department’s daily operations by my efforts, it was decided that my effort had to be conducted off hours, and I started work at 5:00 PM and generally worked until 2:00 AM, which required that a member of this department be present with me as for security reasons, as I was not allowed to be in this department alone. The following week I was also to work this late shift, along with the Project 704 software development team, to install the new computer software and populate the database with the full contents of the large computer file. After we had done this installation and population, the software development team leader and I were to provide two days of instruction on how to utilize Project 704 computer system.
At the end of the week of installing and configuring the DBMS, I needed a few extra hours to finish this task, and my escort and I decided to work until 5:00 AM Friday morning to finish my tasks. Unbeknownst to us, as we were working in a SCIF building with no windows and no media communications outside of the building, a freak snowstorm had hit Washington D.C. and blanked the metropolitan area with over two feet of snow by the time we left the building. The guard at the front door informed us that the Mayor of Washington had closed the city and restricted vehicle traffic to emergency and snow removal vehicles only. I wished my escort a safe trip home, but I had checked out of my hotel stay anticipating returning home for the weekend, and being snow-bound, I had nowhere to go. I telephoned the hotel that I had been staying at and asked if they had any room that they could give me. They informed me that the hotel was nearly empty, as most of the guests had departed early to avoid the snowstorm, and most of the reservations had been canceled due to the snowstorm, and they could host me in the same room that I previously stayed in. I informed them that I would be there as soon as I could navigate the roadways to reach the hotel. This trip to the hotel would normally take me fifteen minutes, but on this day, it took me nearly two hours to get to the hotel through all the snow. By the time I reached the hotel, it had snowed to over three feet, and the hotel was only staffed by the night shift that had to remain in the hotel.
It became necessary for me to remain in the hotel for the entire weekend while the city tried to remove the snow. The city was doing a horrendous job of removing the snow, and they did not finish removing the snow until Monday evening, and Washington D.C. remained closed until early Tuesday morning. I, therefore, was snowed into my hotel for four days with not much to do. The hotel was short-staffed for this entire time, and the hotel restaurant was closed, but the hotel allowed the dozen guests remaining to eat in the restaurant with simple meals that the remaining staff prepared for themselves and the guests. The hotel also allowed us to take magazines and books out of their hotel store free of charge, and they did not charge us for watching paid television programs in our rooms.
On very early Monday morning, I telephoned the manager of the Photos and Videos collection department to determine what he wanted the Project 704 team to do about their visit this week. He asked that we postpone the visit until next week, as he anticipated they would be busy catching up with the two workdays that they were snowed out of the agency’s headquarters. I agreed and telephoned the Project 704 team and informed them of this decision. As for myself, I was not able to get home until Tuesday afternoon, and when I called my manager and explained the situation, he told me to take the rest of the week off as compensation for my being snowed in the hotel room.
When we returned the next week, we discovered a significant problem with the database population program that was not discoverable in my populating the database with the small, extracted sample of the large computer file. The junior programmer who was assigned to develop this database population program decided to check for a duplicate in the database before he added a record to the database. As the database became larger during its population, this check for duplicates took longer to accomplish, and the population of the database became slower and slower to the point that it was taking too long to populate the database. Indeed, the husband of the senior computer programmer for Project 704, who was also an employee of GE M&DSO MC3I and a mathematician, upon being informed by his wife of this problem, calculated that it would take over a year to populate the database utilizing this method. Upon all of us examining this program and determining the problem, we rewrote the program to populate the database, then checked the database for and removed and reported the duplicates. We ran this revised program the next night, and it took over twelve hours to populate the database and check for duplicates.
After we completed these efforts and successfully completed the computer systems testing, the Lead Programmer and I spent the next two days instructing the agency’s department personnel in the usage of this computer system. We discovered that the usage of this computer system was slow, as their workstation computer was old and slower than a modern workstation computer. Upon this discovery, the Director of the agency authorized the immediate replacement of their workstation computer with the newest and fastest workstation computer that the agency possessed. This new computer workstation had a much faster processor and a larger and faster disk drive that was more suitable for the utilization of the Project 704 computer system. Upon this replacement, the computer system we developed was much more responsive and satisfactory for its purpose. The agency’s department manager was very satisfied and grateful for this computer system and the new computer workstation, as it reduced the effort to locate the Photos and Videos in their collection, and made their search for Photos and Videos more accurate and thorough.
Each systems engineering team in MC3I had a person or two that was considered an expert in the technology or processes of the team, and through my efforts at MC3I, I was considered a master of all these technologies or processes at MC3I, and I was to be henceforth assigned as a lead or chief engineer of a multi-disciplinary proposal or program efforts at MC3I.
AWHG Proposal
When Project 704 was successfully accomplished in a few months, I was assigned as the GE technical engineer to a NATO AWHQ proposal. The Alternate War Headquarters (AWHG) was a NATO Request for Proposal (RFP) for the development of a mobile battlefield trailer that would provide joint Command, Control, and Communications for the NATO forces of The United States, Great Britain, West Germany, France, and Italy, in the event of an active war in Europe. This AWGQ NATO proposal was fronted by the West German military, and our proposal effort was a consortium composed of a company from each country, except West Germany, which had two companies that were a computer software development company, the other being a military aircraft manufacturer. Each company had a representative on separate Marketing and Technical teams of the consortium. Fortunately, all the members of both teams spoke English, which was the official language of NATO. An independent American, who had spent several decades in Britain as a consultant on NATO contracts for the British military, was also hired to provide consulting services to the Marketing team and the technical team, as he had extensive managerial and technical expertise in the German military, and he wrote and spoke fluent German.
After spending three days reviewing the RFP at MC3I, I flew that weekend to Wilhelmshaven, West Germany, for almost a month of meetings with the other company’s technical team members to plan our efforts on this proposal, and to formulate a general design for the AWHQ system. When it was discovered, during my MC3I international travel security briefing, that I did not have a passport, the security department arranged for an expedited passport to be issued for me. I had my passport photo taken that afternoon, and the next morning I went to the State Department office in Center City Philadelphia, which was awaiting my arrival, and they pasted my photo into my passport that was prepared beforehand, and my passport was issued in less than a day. The international travel security briefing was not only for the purposes of protecting any classified information that I had in my head but a warning and directive to never carry any classified materials, which I was never allowed to do in any efforts that I undertook for GE M&DSO (including the NATO AWHQ proposal), as well as personal security precautions and GE M&DSO international travel policies. Such personal security precautions were to try and fly on only non-American airlines, always enter and exit an airport as quickly as possible and not arrive too early at an airport and proceed directly to the airport boarding gate to await your flight, avoid crowds of unknown persons, do not become too friendly with foreign nationals that you were not working with, never give out your personal address of phone numbers but utilize a dummy address and phone number that GE M&DSO had established, to over tip to avoid any possible unpleasant situations, and if you ever encountered any difficulties during the trip to try to buy your way out of any situation and leave the situation as quickly as possible, for which GE M&DSO would reimburse you. I did have occasions when I needed to apply these personal security precautions on the foreign trips that I took in my career at GE M&DSO. I also discovered that when you were flying internationally at the government’s expense, you had to purchase tickets in the coach class seating, but when you flew internationally at the GE’s expense, you could purchase business class seating. As the AWHQ proposal effort was a company expense proposal, I was able to fly business class on my AWHG Proposal efforts (all other international travel that I did for GE M&DSO MC3I was a government-related expense, and I flew coach class seating on these trips). I also learned that GE had an international telephone network that allowed GE personnel to make long-distance calls at a local call charge rate. GE had many local exchange telephone numbers around the world, and if you called this local exchange phone number, you could then dial any phone number in the world, and you would only pay the local exchange phone call rate. This proved quite useful on my future European business trips.
The German software development company had the lead on the AWHG proposal, which caused some consternation as much of the AWHQ proposal concerned equipment. The technical leader of the German software development company, who was appointed the Chief Engineer for the AWHQ Proposal, was very much a Prussian in this management style of authoritative directions, while the military aircraft manufacturer technical engineer was from Munich who had a laid-back style, and he had spent a few years studying and working in America. The other members of the technical team were also of a laid-back style, and it was very easy for us to get along with each other, except for the Prussian.
The meeting place was a hotel about ten miles outside of Wilhelmshaven, in the middle of nowhere, but it was constructed and owned by the German software development company. They did this in expectation of the near-term growth of Wilhelmshaven, as Wilhelmshaven was the only deep seaport for the German Navy, which was starting to modernize and expand its fleet.
The technical team spent almost a month examining the AWHQ proposal and breaking the proposal requirements down into categories of functionality, then into a conceptual design of the equipment, hardware, and software that would be necessary to develop a general design of the AWHQ. We agreed to meet a month later, during which time each technical person would formulate their concept of the general design of the AWHQ. At this future meeting, we would develop our general design for the AWHQ and delineate each company’s responsibilities for individual components of the general design.
While I was flying to West Germany with the MC3I International Marketing Manager, he informed me that he had not arranged for a rental car for me. He explained that he was visiting several companies in Germany, as well as the West German Federal Ministry of Defence, over the next several weeks. As his first visit was in Wilhelmshaven with the German software development company where my meeting was being held, he would drive me to this meeting. He had not arranged for a rental car for me and informed me that if I needed a car, I could be a passenger in another technical team member's car. Upon arriving in Hanover, we had a two-hour drive to Wilhelmshaven in a small Ford Fiesta, which he had rented for himself to drive around West Germany.
West Germany, at that time, had strict labor laws regulating work hours, and when the meeting started, I discovered that the meeting hours would be strictly 10:00 AM to 05:00 PM on Monday, 9:00 AM to 5:00 PM on Tuesday, Wednesday, and Thursday, and 9:00 AM to 2:00 PM on Friday. I also discovered that all the other technical team members were planning to return home on Friday afternoon and come back on Monday morning, which effectively left me without a car on the weekend in the middle of nowhere where the hotel was located. When I telephoned my manager on Tuesday afternoon to give him a status report as he requested, I mentioned this lack of a car to him, and he informed me it was GE M&DSO’s policy that all persons on a business trip over three days were entitled to rent a car. He instructed me to obtain a rental car as I was entitled to under this policy. Being in the middle of nowhere, with no car rental company except in the center of Wilhelmshaven, which was ten miles away, I discussed this situation with the front desk of the hotel. They kindly offer to have one of their staff drive me to the Wilhelmshaven Hertz Rental Car agency the next day during lunch hour.
The next day I went to the front desk as lunch began, where a non-English-speaking janitor had been instructed to drive me to the Hertz Rental Car agency in Wilhelmshaven and to wait for me to rent a car. When I arrived at the Hertz Rental Car agency in Wilhelmshaven, I discovered that it was a small storefront with no rental cars in sight. I further discovered that the rental agent spoke no English, and all the signs and literature in the store were in German. Through the utilization of pointing and motioning, I was able to communicate with this agent my intentions. I further discovered that there were no rental cars available that day but that the agent would deliver a rental car the next day to my hotel. Before I left the agency, he pointed to a sign that was obliviously a list of car models that were available for rental. I noticed that all the Cars were Mercedes and somewhat expensive to rent, so I chose a Mercedes car from the middle of the list. I then went back to my driver and motioned for him to drive me back to the hotel. When I arrived back at the hotel, I went to the front desk and explained what had happened and asked them to interrupt the meeting the next day when the rental car arrived. The next day, in the middle of the morning, they informed me that my car had arrived, and I and the other engineering team members, to whom I had told my rental car story too, went outside to look at my rental car to discover that it was a somewhat deluxe Mercedes 420 SEL four-door sedan. The team members were all impressed with the rental car, as it was the finest rental car of the technical team members, and they commented that such rental cars in their companies were reserved for upper management rentals. After the meeting broke up that day, I telephoned my manager to explain the rental car situation, as I knew that the cost of this rental was beyond GE M&DSO guidelines for rental cars. He laughed and told me to keep the car, as that would teach a lesson to the MC3I International Marketing Manager not to arrange rental cars for his engineers. For the rest of my stay on this trip, I was able to cruise around West Germany in my Mercedes 420 SEL rental car.
This proved advantageous to the other technical team members, as during the second week of the meeting, someone mentioned that he was tired of eating dinner at the hotel restaurant. We all decided to drive in my Mercedes 420 SEL rental car to Bremen for dinner, except for the west German team members and the independent consultant who had other plans. Bremen was the nearest large city to Wilhelmshaven (about a thirty-minute drive on the Autobahn), which we expected would have many restaurants which we could choose to have dinner after we strolled around the center city of Bremen. The four of us arrived in Bremen at about 5:30 PM to find that there was no on-street parking available, so I parked my Mercedes in a garage in the center of Bremen. We then strolled around the city center for about two hours and chose a restaurant for a leisurely two-hour dinner. When we left the restaurant, we discovered that Bremen was deserted, as there were no people on the streets and all the stores were closed and unlit. We later learned that Bremen city ordinances required all businesses, except restaurants, to close at 8:00 PM and not open until 8:00 AM on weekdays. We decided to hurry back to the garage to retrieve my Mercedes and drive back to the hotel. We were shocked to discover that the garage was closed and locked, with no attendant present. We were discussing what we should do when we noticed a young couple window-shopping across the street where the garage was located. We approached this young couple and discovered that the woman spoke broken English, and we explained our situation to her. She looked at our parking ticket and discovered a telephone number on the back side that we could call for assistance. We thanked her, and the Italian member of our team, who spoke no German like the rest of us, dialed this number on a paid phone booth outside of the garage. He discovered that the person on the other end of the line spoke no English, but he was able, with much difficulty, to explain our dilemma to this person, who was also the garage attendant where our Mercedes was parked. The attendant agreed to come to the garage and open the garage door for a fee of four German Marks. About a half hour later, he arrived and opened the garage door, but we discovered that due to a miscommunication, the fee was forty German Marks (quite expensive at that time). I gladly paid the fee, and the other team members wanted to contribute to this payment, but I assured them that GE would reimburse me for this expense. We then left Bremen and went back to our hotel.
During our meetings, the West German computer software development company that hosted the meeting decided that it would be nice for us to visit the west German Navy yard to tour a cruiser that had just been refitted, including the computer software that the company had developed for the cruiser. They rented a bus to transport us to this cruiser, and we gathered in an observation deck below the bridge of the cruiser to start our tour. There then ensued a rather loud and excited conversation between the German Captain of the cruiser and our West German company tour guide. I asked the independent consultant, who spoke fluent German, what they were discussing. He informed me that the German Captain thought that our visit was scheduled for the next week, and as they were currently loading munitions aboard the cruiser (a very dangerous operation for all ships that had munitions), he wanted all of us off the cruiser before we accidentally ignited the munitions and blew the cruiser up. We were hurriedly but carefully deboarded with anti-static electric socks that fit over our shoes, and we proceeded to a tour of a destroyer that was just beginning its refit and had no munitions on board the destroyer. I wanted to keep anti-static electric socks as a souvenir, but the West German Navy collected these socks for reuse after we deboarded the cruiser.
On the first weekend of this trip, I decided to visit the city of Bremen, the town of Bremerhaven, and the surrounding countryside to get a flavor of this part of Germany and observe the typical housing of the residents of this part of Germany. I made it a goal to only have my meals at local restaurants or taverns to get a taste of local food and beers. One local brewery brewed a Pilsner Beer that is still one of the best Pilsner that I have ever drunk. I discovered that all the German people that I met were very friendly and accommodating, and many of them spoke English. As this part of Germany was extremely flat and near Holland, I also saw several operating windmills.
The next weekend the United Kingdom engineer was not going home, as his wife decided to visit her sister in another part of England from his home. We decided to visit Hamburg on Saturday, which is the largest port city in Germany, which was a two-hour drive on the Autobahn from our hotel. He wanted to visit Hamburg as he had occasionally docked in Hamburg when he was an officer of the Royal Navy. Unfortunately for him, he was always assigned as the shore leave officer when he docked at Hamburg. The shore leave officer was responsible for policing the seamen of the ship while they were visiting Hamburg. As these seamen were often rowdy and drunk, they often became involved in activities that he had to break up or bail them out of jail, which left him no time to see the city of Hamburg. Upon arriving in Hamburg, we took a tourist open-air bus trip to see the sights of Hamburg, including the red-light district of Hamburg, when he regaled me with stories of his shore leave officer experiences. We then visited several sights that provoked our interest on the bus tour, and we decided that the next day we would return to Hamburg to visit a very large maritime museum that was in the Port of Hamburg, which he was very much interested in visiting. I assured him that I would not be bored by this visit to the museum, as I was very interested in all science and technology.
On early Sunday morning, we left for Hamburg so that we would arrive at the museum when it opened at 10:00 AM. During our drive to Hamburg on the Autobahn, which was very flat and very straight, we noticed that there was no traffic in either direction as far as we could see. We decided to rev up my Mercedes to one hundred and twenty miles per hour, but we only maintained that speed for two minutes. This was the fastest he and I had ever traveled in a car, and we agreed it was exhilarating but that we would never travel at that speed again, and we slowed down to eighty miles per hour for the rest of the trip. We spent six hours touring the museum, and with his extensive knowledge of maritime history, science, and technology, which he imparted to me, we both enjoyed every minute of our time spent at the museum. We then had dinner at a local Hamburg restaurant and proceeded back to our hotel at eighty miles per hour on the Autobahn.
The last weekend I was once again alone, and I decided to visit the historic and charming town of Heidelberg (which was quite some distance away). I started my trip early Friday afternoon and drove down the east bank of the Rhine River until I reached Koblenz shortly after darkness set. This Rhine River journey was very pleasant, even though it was during the winter when I took this journey. I stopped at a local winery and restaurant to partake in a late afternoon meal which was delicious, and the wine sampler that I imbibed was also very good. Continuing my Rhine River journey to Koblenz, I found a hotel on the west side of the Rhine River overlooking the well-lit Ehrenbreitstein Fortress on the east bank of the Rhine, where it is joined by the Moselle River.
The next day I proceeded to Heidelberg on the Autobahn and arrived in the early afternoon, found a hotel, and walked around the city of Heidelberg until about 7:00 PM, when I located a nice restaurant to partake in local cuisine and a local beer. Being tired from the trip, I went back to the hotel for a good night’s sleep, with every intention of visiting the famous Heidelberg Castle and other Heidelberg historical sights on Sunday. When I awoke on Sunday morning, had breakfast at the hotel, and checked out of the hotel, I drove to Heidelberg Castle and discovered it was closed on Sundays. I went to two other Heidelberg historic sites and discovered that they were also closed. I asked a nearby policeman (who spoke English) why they were closed, and he informed me that Heidelberg was a designated religious and historical town and that only churches, restaurants, and hotels were open on Sundays. Being disappointed, I left Heidelberg to go back to Wilhelmshaven on the Autobahn at a leisurely pace of seventy miles per hour. This Autobahn route led me through some scenic rolling hills of central Germany, and I passed by many charming small towns until I approached Hanover, where the countryside became flat, but the towns were still charming. This trip took all day, and I arrived at my hotel in the early evening, where I had dinner and then a good night’s sleep. The next day my West German engineer friend informed me that Heidelberg was also a university town that was famous (notorious) for its many public parties on Saturday night, but all parties had to end at midnight, as Sunday was designated a study day for the students. As I had gone to bed early Saturday night, I missed out on seeing one or more of these parties.
After I returned from this meeting in Wilhelmshaven, the GE M&DSO MC3I International Marketing Manager asked if I would be interested in becoming the permanent GE Chief Engineer for the AWHQ proposal. I expressed my concern that it appeared that our portion of this proposal would be limited to computer software development and that it would be more appropriate to appoint a Senior Software Engineer to be the GE Chief Engineer for the AWHQ proposal. I was also concerned about the extensive and sometimes long-duration travel to Europe that would be required to fulfill the duties and responsibilities of the GE Chief Engineer. As I had a young daughter that I did not wish to be separated from with the travel time and duration of these meetings that would be required, I was reluctant to accept this position. He agreed with me about appointing a Senior Software Engineer to be the GE Chief Engineer, and he understood my reluctance to be away from my daughter. He, therefore, found a Senior Software Engineer that was interested in and qualified for this position and had no family other than his wife, who would be allowed to travel with him at company expense for the long-duration trips. The only issue was that he would not be available for a month, and I agreed to continue my efforts on the AWHQ proposal until he was available.
Almost two weeks after I returned from this meeting, I was informed that the German software development company that had the lead on the AWHG proposal had called an emergency meeting, and it was necessary for me to attend this meeting. The purpose of this meeting was unknown, and I was reluctant to make this trip as I was feeling unwell with what I thought was a flu bug that was going around at this time. My manager could see no way I could not attend this meeting other than being sick, but he instructed me to go home and try to get better and take the trip to Wilhelmshaven on Monday morning, which they had already booked for me. By Monday morning, I was feeling better, and it was off to Wilhelmshaven that I went.
When the meeting began on Tuesday morning, we discovered the purpose of the meeting. Some of the company’s marketing representatives were complaining that their management wanted a more definitive answer to what and how much of the AWHQ proposal would be allocated to their company. They, therefore, were demanding that we create a general design and apportion the general design amongst the companies. Upon hearing this, I objected and explained my objection with the analogy of trying to slice up a pie before the ingredients were mixed and put into the pie pan and baked. Nevertheless, the Chief Engineer for the AWHQ Proposal (now known as The Prussian) insisted that we undertake this effort, to which I responded that I thought that we would be wasting our time attempting this. By the end of the afternoon, it was apparent to all but The Prussian that we were wasting our time. Several of the other engineers insisted that The Prussian inform the management team of the futility of continuing. The Prussian left our meeting to inform the management team of our opinion. Whereupon the entire management team entered our conference room and demanded we create a general design that could be divided up between the companies. This greatly upset me (and I was beginning to feel ill again), and I drew a Venn Diagram on my tablet of the categories of functionality and a guesstimate of which company would be responsible for the category and the percentage of effort for each category, then handed it to my marketing manager and told him that the management team should divvy up the Venn Diagram amongst themselves, but it would most likely not bear any resemblance to the final general design. The management team left the conference room with instructions that we complete the final design by the end of the week.
After the management team left the conference room, The Prussian directed that we create the general design as the management team required that we do this. Upon hearing his order, I whispered to the other German company technical leader with whom I had become very friendly, “Jawohl”, and he whispered back to me, “Mein Führer” (yes sir, my leader). As it was late in the afternoon, I suggested that the meeting be adjourned for the day to think about this issue. Upon leaving the meeting, I discovered that the management team had also adjourned for the day, and I sought out my management leader to have a private discussion with him about this issue. I discovered him in his room and on the telephone with the International Marketing Manager about this issue. He invited me in and turned on the speakerphone so that I could join in on the conversation. After I explained to the International Marketing Manager my reasoning, he agreed with me and directed that the Marketing Representative should oppose the demand to create a general design at the next day's management meeting. When I went to dinner that evening with the other engineers, except for The Prussian, the engineer from Great Britain and the West German military aircraft manufacturer revealed that they had similar telephone discussions with their management, who also thought it was a bad idea to force a general design by the end of the week. Near the beginning of the next day’s meeting, The Prussian was requested to step out and join the manager's meeting. When he returned in a few minutes, he informed us that it would not be necessary to create a general design by the end of the week but only firm up the Venn Diagram that I created with better estimates of the company responsibilities and the percentage of effort for each category. We, therefore, spent the next few days doing so, and by the end of the week, the engineers were satisfied that the responsibilities and estimates were reasonable.
Before leaving this meeting early Friday afternoon, I informed the engineering team that I was no longer going to be the representative from GE and that MC3I had found another engineer to take my place. They expressed regret that I was leaving (The Prussian looked relieved) and concern that I was being forced out, but I assured them it was my choice to leave and that my replacement was fully qualified for the engineering team’s effort. The return flight from this trip was interesting, as I discovered that Frankfurt airport was on lockdown as they had received a bomb threat. The entire airport was heavily patrolled by heavily armed West German Army forces, and remembering my international travel security briefing; I immediately went to the boarding gate to await my departure.
When I returned from this trip and documented our efforts of the previous week, I was informed that the Senior Software Engineer had become available, and I spent the next day with him discussing the AWHQ proposal and our efforts to date. He then assumed the duties and responsibilities of the GE M&DSO MC3I Chief Engineer for the AWHQ Proposal.
Several months later, I bumped into the GE M&DSO MC3I Chief Engineer for AWHQ in the marketing office and asked him how things were proceeding with the AWHQ proposal. He responded fine, especially since the lead company for the AWHQ proposal was reassigned to the West German military aircraft manufacturer, and their technical leader was named the new Chief Engineer for the AWHQ Proposal efforts. He also mentioned that they had completed the general design and that the Venn Diagram percentage estimates were close to the general design efforts, and that all the companies were pleased with their apportions of the AWHQ Proposal.
About a year and a half after the start of the AWHQ Proposal, I again bumped into the GE M&DSO MC3I Chief Engineer for AWHQ in the marketing office, and I again asked him how things were proceeding with the AWHQ proposal. He informed me that with the political and social unrest in the eastern European countries, and the possible crumbling of the Soviet Union, the AWHQ proposal was placed on hold by NATO until this situation was resolved. With the eventual collapse of the Soviet Union, NATO decided to cancel the AWHQ proposal.
Proposal Reviews
After I turned over the AWHQ proposal, I was asked to review two technical proposals that were in their final stages of development. They were interested in my comments on any issues or concerns that I may have about these proposals. I was able to provide helpful assistance with these proposals with the few issues and concerns that I uncovered. I was also asked to edit these documents, as the engineers who wrote these technical proposals were not adept in writing technical documents for the non-technical government persons who would be reviewing these documents, and I had become very good at doing this because of my effort in creating the LTMS User Manual. This review and editing took about four weeks, and afterward, I was offered the opportunity to become the Chief Engineer of the TADMS contract that MC3I had just signed.
TADMS
TADMS was a joint US Department of Defense (DOD) and the United Kingdom Ministry of Defense (MOD) contract to develop a mobile demonstration trailer that could exploit military intelligence in a battlefield situation. The DOD was to provide the data for the computer system and two computer systems to manipulate the data, while the MOD would provide the mobile trailer that housed the data and the computers. The MOD trailer would provide the communications systems, electrical power generation, heating, ventilation, and air conditioning for the trailer, as well as the personnel to man and perform the manipulations of the data. The DOD personnel assigned to TADMS was an Army Colonel responsible for the TADMS program, a Pentagon civilian employee COTR, and an Army Chief Warrant Officer (CWO) who would provide military and technical support to TADMS. The MOD DOD personnel assigned to TADMS was a Royal Air Force Wing Commander (RAFWC) COTR and a Royal Air Force Squadron Commander (RAFSC) who would provide military and technical support to TADMS and would be in command of the TADMS trailer after it was deployed.
GE M&DSO MC3I was the contractor to the DOD, while Ferranti was the contractor to the MOD, each of whom would design and develop their country's portion of the TADMS system. Ferranti or Ferranti International plc was a UK electrical engineering and equipment firm that operated for over a century from 1885 until it went bankrupt in 1993. The Ferranti division that MC3I was working with was located at Bracknell, a large town and civil parish in Berkshire, England, the westernmost area within the Greater London Urban Area and the administrative center of the borough of Bracknell Forest.
On my last visit to Ferranti, I engaged in a discussion with one of the executives of Ferranti to explain what GE M&DSO MC3I had done on the TADMS Program. During this discussion, he mentioned that we might soon become neighbors, as Ferranti was in discussions about purchasing International Signal and Control (ISC), a United States defense contractor based in Valley Forge, Pennsylvania. I warned him that James Guerin, founder of ISC, had a reputation for shady deals and that he should be very careful about this acquisition. I knew this but could not disclose any details to him for security reasons, as GE M&DSO was forbidden to have any relationship with ISC. I had come to know this because, on one of the proposals that I worked on, we were considering purchasing some equipment from an outside vendor, one of whom was ICS. A security officer of GE M&DSO MC3I approached me and informed me to disregard ISC, as GE M&DSO was forbidden to have any relationship with ISC. When a security officer tells you to do or not do something, you can assume it is for classified reasons, and you will do or not do what they instruct and not ask any questions as to why.
In 1987 Ferranti did purchase ISC, but unknown to Ferranti, ISC's business primarily consisted of illegal arms sales started at the behest of various U.S. clandestine organizations. On paper, the company looked to be extremely profitable on sales of high-priced "above board" items, but these profits were essentially non-existent. With the sale to Ferranti, all illegal sales ended immediately, leaving the company with no obvious cash flow. In December 1991, James Guerin, the owner, and CEO of ISC, pleaded guilty before the federal court in Philadelphia to fraud committed both in the US and UK. The financial and legal difficulties that resulted forced Ferranti into bankruptcy in December 1993.
The initial management planning for the TADMS team was that they would not need a Chief Engineer for financial reasons, as well as most of the contract being for software development. However, the Program Manager, John Eckert, who I had worked with previously as the part-time testing supervisor on the LTMS Program, soon realized that a Chief Engineer would be needed. I was asked to become the Chief Engineer of TADMS by John, who expressed some concerns that on TADMS, he would be my manager rather than the other way around, as it had been in the LTMS effort. I assured him that I had no problems with this arrangement, as I knew him to be a reasonable and fair person that I enjoyed working with. The lead software engineer for TADMS, Theresa, was also the same lead software engineer that I worked with on Project 704, which made my appointment as Chief Engineer more harmonious.
MC3I’s main task was to develop a computer system that would manage the data and workflow of the analyst who would utilize TADMS by integrating International Imaging Systems (IIS) subcontractors' computational equipment with this computer system, which MC3I’s software would provide the command and control of this computational equipment. The subcontractor was very much interested in modifying their computational equipment, as this computational equipment was a stand-alone device that did not have an interface to computer systems. If they modified this computational equipment to interface with a computer, they expected that their sales would increase. Therefore, they were eager to do this, as MC3I would be paying them to modify this computational equipment that they would have to otherwise fund themselves to achieve this interface capability. The modifications that TADMS needed for this computational equipment were extensive, expensive, and time-consuming for the subcontractor to accomplish.
The MC3I TADMS team was composed of the Program Manager, John Eckert; myself as the Chief Engineer; Teresa as the Lead Software Engineer; Dave and Tom as Software Engineers; Bill as the Operations and Testing Engineer; and Greg, a part-time Hardware Engineer who would provide any computer equipment assistance we required, as well as supporting Ferranti in the integration of the MC3I TADMS computer systems into the Ferranti trailer modifications.
For cost-saving and for efficiency purposes, the TADMS team did not have a separate Systems Testing and Operational person assigned to the TADMS effort. Instead, we combined these two jobs into one person, the Operational person, who would write the TADMS User Manual based on the TADMS operational flow, and then would create, with my assistance, the TADMS computer system testing procedure from this User Manual. The User Manual for the TADMS not only contained the instructions on how to utilize the TADMS computer system but also contained the operational procedure for the entire TADMS trailer and all the equipment that Ferranti was installing in the trailer. This required that the training person work closely with Ferranti but also with the RAFSC and CWO to learn their trailer equipment and the standard Army and RAF operational procedures. As he had previously served in the Army, doing things like TADMS was tasked to do, and he had previously written MILSPEC user manuals, he did not require much supervision on my part in the creation of the TADMS User Manual. It was only necessary for him to travel to Ferranti to conduct the TADMS systems testing and make final changes and improvements to the TADMS User Manual.
One of the first things I uncovered after accepting the position of Chief Engineer of TADMS was that there was no interface control document between the computer systems and the subcontractor’s computational equipment, which I believed was a big mistake. I immediately rectified this mistake by taking upon myself the responsibility for creating this interface document with the assistance of the lead software engineer of GE and the subcontractor’s lead engineer. This document proved to be invaluable when we encountered difficulties near the end of the TADMS program. I also assisted in the design of the database for the DBMS that would be utilized as the core of the TADMS computer systems and the design of the management reporting of the TADMS system activities.
As we began the creation of the interface control document, it was necessary for me to travel to IIS headquarters in Sunnyvale, CA, to meet and discuss the format and content of this document with the IIS Lead Engineer. Our meeting was scheduled for Monday morning at 9:00 AM, when he would first introduce me to the President of IIS, and then I would be given my first demonstration of their computational equipment (the MC3I TADMS team Program Manager and Lead Software Engineer had received this introduction and demonstration prior to my becoming the Chief Engineer).
As I had been to Sunnyvale, CA, for my CALMA efforts, and I had no desire to visit anywhere, I decided to take a late Sunday afternoon flight from Philadelphia to San Francisco, with a stop and plane switch at Denver, CO. Upon arriving at Philadelphia International Airport; I discover that my flight was canceled and rescheduled to a later evening flight. I did not arrive in Denver until almost 10:00 PM, and in bad weather, where I was able to make a connecting flight to San Francisco. Unfortunately, my luggage did not make this connecting flight, and the Denver Stapleton International Airport had closed at 11:00 PM, so my luggage would not arrive and be sent to my hotel until sometime Monday morning.
As I was dressed very causally for the flight, I did not have any change to appropriate clothing, fresh underwear, or any of my toiletries that I needed to meet with the President and Lead Engineer of IIS. Early Monday morning, I scrambled to locate an open store that sold underwear and toiletries that I needed. I found a store that was open and purchased underwear and toiletries (at the airline's expense), and proceeded to my meeting dressed in the very casual and day-old clothing that I had worn during my flight. Upon greeting the President, I apologized while I recounted my story, to which he assured me that he understood, as the same situation had occurred a few months earlier on a business trip he had made to meet with the President of another company that they were soliciting for new business. The casual dress was not a problem for the IIS engineers as they were dressed even more casually than I was.
A month after the TADMS contract was signed, a status review meeting was held in the City of London. The City of London is a city within the modern area named London that had grown far beyond the City of London boundary. The City of London is a ceremonial county and local government district that contains the historic center and constitutes, alongside many of the UK governmental offices and the primary central business district of London. The MOD's main headquarters was in the center of the City of London, within walking distance of most of the tourist attractions. As this was more of a management review, it was only attended by the MC3I Program Manager. At this meeting, they decided to schedule a technical review two months later to be held at the MOD Headquarters in the City of London, which John and I would attend.
Two months later, John was unable to attend this meeting for personal reasons, but he thought that my presence was all that was needed for this meeting. I flew to London and arrived early Saturday night, and checked into a small hotel at about 10:30 PM, just outside of historic St. James's Square in the City of London (which was in walking distance to the MOD headquarters). Not wanting to go to sleep as I had slept on the flight, I decided to see what was happening outside of the Hotel. When I stepped outside the Hotel, I discovered nothing but darkness, as all the buildings were dark, and even the streetlights were turned off. I did notice a glow of light far down the street, and I decided to walk toward this glow, never straying from the street as I did not want to get lost in the dark on my walk. After a twenty-minute walk, I suddenly found myself in the center of Piccadilly Circus at midnight. I spent the next hour standing on a corner watching the crowd of oddballs, wackadoodles, and the strangeness of the people that passed through Piccadilly Circus on a Saturday night. I then walked back to my hotel room for a good night’s sleep.
Sunday morning, I arose before 7:00 AM to have breakfast at the hotel and begin exploring the City of London. I discovered that the hotel restaurant did not open until 9:00 AM on Sundays, and after obtaining a tourist map of the City of London from the front desk of the hotel, I decided to explore Whitehall until the hotel restaurant opened. Whitehall is a road and area in the City of London containing many government buildings, and the street is known for its memorial statues and monuments. As Whitehall was very near to the hotel, I expected this to be a short walk on a Sunday morning. Whitehall was longer than I expected, and I spent almost three hours walking Whitehall before I returned to the hotel for breakfast.
I soon discovered that Whitehall was essentially closed on Sunday morning, as the retail businesses, restaurants, and tourist attractions were not open until noon on Sundays. Therefore, this stroll was done for observational purposes only, but I was also looking to buy more film for my camera, as I only had a half-used roll of film in my camera. I made it as far as Buckingham Palace on this stroll, which was deserted except for some King's Guards posted outside the palace when I turned back to have breakfast at my hotel.
On the way back to the hotel, I was walking on Horse Gardens Road, and I passed two armed guards posted at the end of a side street to Horse Gardens Road. I paused to look past the guards down this street to see what they were guarding. One of the guards informed me that the Prime Minister was not in residence, and it was then that I noticed that this was Downing Street, where the Prime Minister resided and had his executive office at historic Number 10 Downing Street in the City of London while he was engaged in government business. After walking a few hundred feet from Downing Street and the guards, I noticed a store on the other side of Horse Gardens Road that was open and had a film sign on its window. Rather than walking another few hundred feet to the crosswalk, I decided to jaywalk across Horse Gardens Road to buy film, as there was very little traffic on the road, and the traffic that there was had red lights equidistant from where I was jaywalking. I misjudged the height of the curb and the road conditions, and when I stepped down to jaywalk, I lost my footing and ended up splaying face down at the side of Horse Gardens Road. Although I did not hurt myself, I managed to tear a hole in the knee of my pants and grime up my jacket. At this point, I noticed the guards were looking at me with an expression of wonderment at what the crazy American was doing. It was also at this point that I noticed that both red lights had turned green, and the cars were approaching me. I quickly scrambled to the other side of Horse Gardens Road and took stock of what I had done to myself. After taking stock, I entered the store and purchased film, then returned to the hotel. Before my breakfast, I changed my clothes, then decided to take a short nap after breakfast until noon, as I was tired from my walk and when the tourist attractions would be open.
After my nap, I went to the tourist attractions such as Buckingham Palace, Trafalgar Square, Wellington Arch, Nelson's Column, and others in the City of London, including the Speakers' Corner. The Speakers' Corner, a public soapbox located at the northeastern edge of London’s Hyde Park near the Marble Arch, gained unofficial status as a “right to speak” area in 1872 and has since been considered a special free speech zone, where I listened to a couple of short speeches. While at Buckingham Palace, and as I was observing the events that were taking place when a properly attired Englishman approached me and started describing the events. I tried, unsuccessfully (remembering my foreign travel security briefing), to disengage with him, but he was persistent. A few minutes later, he asked if I would like for him to take a few photos of me with his camera, posing in front of Buckingham Palace, which he could postal mail to me for a modest fee. At this point, I knew that I was caught in a scam, which I would have to buy myself out of per GE M&DSO's foreign travel policy. I agreed, and he took several photos of me in front of Buckingham Palace. When I asked him how much his fee was, he responded twenty pounds, which would have been approximately fifty dollars at the current currency exchange rate. This twenty-pound fee was too exorbitant for my sensibilities, and I gently remarked so, and he agreed that ten pounds would be sufficient to cover his expenses. I paid him the ten pounds, then gave him the dummy address that GE M&DSO security had given me. I continued with my walking tour of the City of London until the late afternoon when I returned to the hotel exhausted by my extensive walking, had a good dinner at the hotel, and went to bed for a long night’s sleep. About two weeks after I returned from this trip, a security officer showed up at my cubicle and asked why they had received six photos of me posing in front of a palace. I explained to the security officer what had happened, and he laughed. He asked me if I had expensed the ten pounds, and I replied no, as I just wrote it off as a learning experience. He insisted that I expense it under the buyout of trouble category of my expense report, as security was compiling a list of the buyouts for foreign travel experiences for future reference and for the international travel security briefings. He also allowed me to keep the photos.
On Monday morning, our meeting promptly began at 9:00 AM (I learned that the English people were always prompt). About an hour after the meeting began, a junior RAF officer interrupted the meeting and whispered something into the RAFWC’s ear. He announced that something important had come up that needed his immediate attention (and we did not ask what it was out of security considerations) and that he would have to postpone the meeting until the next day and extend our stay for one day. This was not a problem, as all our flights home were scheduled to leave Friday afternoon, and it was no problem rescheduling our flights until Saturday morning. The Ferranti persons in attendance went back to Bracknell; the RAFSC had other things to do at the MOD, my COTR informed us that his wife wanted him to do some shopping for her in London, and the CWO wanted to visit some old friends in the MOD headquarters that he had worked with in the past. This left me on my own, and I decided to visit the British Museum, located a few blocks from the MOD Headquarters.
As I had a great interest in archeology in my youth, most especially Ancient Egyptian archeology which I often visited the University of Pennsylvania Museum of Archaeology and Anthropology with a fine Ancient Egyptian archeology hall, I was very much interested in visiting the British Museum, which is considered to have one of the finest Ancient Egyptian archeology collection in the world, as well as one of the best Ancient Greek collections in the world. To my surprise, after entering the museum, it appeared that I was the only visitor to the British Museum. Walking through the halls and exhibits, I saw no one else except an occasional guard. When I asked a guard about this, she informed me that Mondays in the winter were always slow for the British Museum, and even the guard staff was reduced on Mondays in the winter.
I did eventually run into a young boy of six or seven years old who was standing alone and appeared to be about to cry. I sized up the situation immediately and approached the young boy, and asked if his Mum was lost. He nodded yes, and I suggested that we both try to find his Mum. He again nodded yes, and we held hands as we began our search for his lost Mum. As we searched, I engaged him in conversation and talked to him about the Ancient Egyptian artifacts we were passing by, and this seemed to ease his fears. He asked me what my strange accent was, and I informed him that I was an American from Philadelphia, PA. I also told him my accent was considered strange to other Americans as well. Eventually, I noticed a guard down the hallway, and we approached her. I explained that the young boy's Mum was lost, and we were searching for her and asked if she could help us find his lost Mum. She used her walkie-talkie to contact the guard’s office, and she informed us that his Mum was at the guard’s office anxiously waiting for him to find her. I asked for directions to the guard’s office, but she responded that she would take the boy to the guard’s office. As we departed, he profusely thanked me for helping him find his Mum and said that he very much enjoyed our conversation.
A few hours later, I walked into a large hall that had a large upright stone in the center of the hall, surrounded by a velvet rope that cordoned it off. Upon approaching this stone, I discovered that it was the Rosetta Stone, a prized artifact of the British Museum that led to the deciphering of the Ancient Egyptian hieroglyphs. There was a sign on the velvet rope that warned the public not to touch the Rosetta Stone, as touching it could damage it. I knew from my knowledge of archeology that many ancient artifacts need to be very carefully handled, as even sturdy artifacts could be damaged by careless touching and that constant touching of even stone writing could wear away the writing. Being aware of this, and as there was no guard in sight, I decided to briefly and lightly touch the side of the Rosetta Stone where I could do no damage. Thus, for the first and only time in my life, I touched an ancient (and important) artifact. I stayed in the British Museum until it closed, then found a nice restaurant nearby for dinner. I then retired to the hotel bar, where the bartender let me sample the various English beers on tap at the bar (I paid for this sampling, and he received a very large tip for allowing me to sample the various beers).
The next day and the rest of the week, our meeting proceeded well and without any interruptions. At the end of Tuesday, my COTR, CWO, and I decided that the next night we would have a fine dinner together and attend a play that night. As The Phantom of the Opera play was sold out and there were no tickets available, we decided to attend The Secret of Sherlock Holmes – a play starring Jeremy Brett and Edward Hardwicke of the original TV series of the Sherlock Holmes stories of Sir Arthur Conan Doyle. The RAFWC was able to pull some strings to obtain tickets for us to this play, as it was also sold out, and we obtained complementary tickets and good seats to this play courtesy of the MOD. When a high government official requests three tickets to a play, he gets three tickets to the play, as every major theatre has a block of twelve seats reserved for special guests (except for The Phantom of the Opera, whose block was filled with other special guests).
On Saturday morning, as the taxi dropped me off at Heathrow Airport, there was a long line and a large crowd trying to enter the airport. Keeping in mind my international travel security briefing to not arrive too early at the airport, I was concerned that I might miss my flight, as it was scheduled to depart in less than an hour. I also kept in mind my international travel security briefing to always enter and exit an airport as quickly as possible, and I tried to locate a faster entrance to the airport. I noticed that some people had an easy access entrance to the airport, most of them dressed in flight crew outfits, and I waited for a small group of people not dressed in flight crew outfits that were about to use this entrance. I scurried behind this group of people and pretended to be one of their group, and I easily and quickly entered the airport and immediately went to my boarding gate, which was boarding the plane when I reached the gate.
The TADMS Design Review and Approval meeting, held at the end of the design phase, was a Tuesday through Thursday meeting at GE M&DSO MC3I. At this meeting, both Ferranti and MC3I presented to both government's management teams their final design and their development plans for their approval. This was a large meeting as the seven members of the MC3I Program team were present, along with three Ferranti Engineers (The Chief Engineer, the HVAC/Electricity/Trailer Engineer, and the Communications Engineer), along with six others from both government's management team (The MOD RAFWC and RAFSC, The DOD Colonel, COTR, CWO, and a DOD Security Officer). Each engineer (except the Two Software Engineers from MC3I) had to give a presentation of their design, while the MC3I Program Manager and the Ferranti Chief Engineer presented the development plans of their respective companies. A large secure SCIF conference room was provided by MC3I for these presentations. This was the first time the DOD Colonel made an appearance at any TADMS meeting, as he had other responsibilities for other programs in the DOD (which, of course, for security reasons, we knew nothing about), and the only other time he appeared was at the turnover ceremony in Bracknell UK upon the completion of the TADMS Program. These two times was the only time that I observed the DOD COTR behave himself, as usually he was aggressive and opinionated and tried to impose his will on everybody involved in the TADMS Program (including the Brits). John played the diplomatic person, while I played the tenacious person as we tried to keep him at bay from the other TADMS team members. The CWO assisted us in this act, as he understood the political games that the COTR liked to play.
The MC3I design review went well, with many questions and answers from all parties at the meeting, until the end of the MC3I presentation. The DOD Security Officer asked what the design was for the computer data to be erased in the event of imminent capture by hostile forces. We never considered this possibility, as we did not know this was a requirement for all intelligence facilities. The DOD Security Officer read the appropriate DOD security regulation, which was a simple paragraph that required any intelligence computer system to be safeguarded from hostile forces, and all computer data to be destroyed in the event of imminent capture by hostile forces. The safeguarding was easy as the trailer had safeguarding designed into it. The destruction of the computer data was another matter, as we did not know about this requirement and, therefore, never considered this requirement.
We then asked the DOD Security Officer for his recommendation to resolve this requirement, and he informed us of a project that was near completion that would attach a somewhat bulky device to the disk drive and, when activated, would magnetically wipe and scramble the disk drive contents in less than a minute. We asked him about the availability and cost of this device, and he responded that it should be available in six months, but the cost had not yet been determined, but they expected the initial cost to be in the low six figures per device. The bulkiness of the device could pose a challenge, but the cost was unacceptable as there were no funds available to TADMS to pay for two of these devices. We glumly sat looking at each other, trying to think what we could do. I then had a flash of inspiration and asked the DOD Security Officer if MC3I installed a grenade next to the disk drive, and drilled a pinhole in the chassis of the computer to activate the grenade, would that meet the DOD security regulation? The CWO chimed in that it should be a thermal grenade for dual destruction purposes, and the DOD Security Officer thought for a few moments and replied that this solution was acceptable. At that point, I chimed in that MC3I would design and develop this thermal grenade casing and install the casing in the two computers at no cost to the government. At this point, the CWO chimed in that the DOD would provide these two grenades (and a dummy grenade for design and testing purposes) at no cost to MC3I. We thought we had the problem solved until the Ferranti Chief Engineer pointed out that external computer data was present and stored in other forms in the TADMS trailer, and they had not planned for this DOD Security regulation. The RAFWC then chimed in that he would arrange to have thermal grenades supplied to Ferranti and that the MOD would pay the cost of modifying the trailer for the destruction of the external computer data cabinet in the trailer. The DOD Security Officer informed us that it would be necessary for him to review and approve these modifications before he could certify that we met this security regulation, which he did shortly after the development phase began. The meeting was then adjourned until the next morning when Ferranti began their presentation.
Ferranti began their presentation on Wednesday morning by announcing that MC3I had obtained two 19” monitors, at no additional cost for the two computer systems, instead of the originally planned 13” monitors. I informed him of this change a few weeks before the meeting, and he responded that he would have to modify the design of the computer stations in the trailer but that he expected that it would not be a problem. The reasoning for the change was that the 19” monitors were much more suitable for the tasks of TADMS. At the meeting, he informed us that there was no problem in modifying the trailer, but they had discovered an ancillary problem. As the new monitors would extend out an additional 8” into the trailer, this would reduce the space behind the person operating the computer to about 30”. As TADMS was a one-off demonstration unit that they expected to have high-ranking military officers and important politicians visit, this was a narrow space for them to observe TADMS operations. This also assumed that the computer operator was a small person, and they created an illustration of the ideal TADMS computer operator—less than 5’4” tall and no more than 120 lbs., and for them to be very thin. Any TADMS computer operator that exceeded this specification would further reduce the space behind them. We all chuckled, then the Colonel remarked, “I think that we are going to need a bigger trailer”, as Roy Scheider did in the movie “Jaws” about their need for a bigger boat. The Colonel then turned to the CWO and ordered him to visit another Colonel in the Pentagon who oversaw the manufacturing of over one thousand trailers for the Army, which were the bigger boat that TADMS needed. He asked the CWO if he thought there would be any problems obtaining a trailer from him. The CWO responded, “No sir”, as he knew and had served under this Colonel in one part of his Army career. True to his word, the CWO called me a week after the meeting and informed me that he had obtained the trailer and it would be shipped to Ferranti in two weeks.
At the end of Wednesday’s meeting, which went very well and quickly, we determined that the Thursday meeting would only take half a day to finish our Design Review. The Colonel and the DOD Security Officer decided that there was no need for them to attend Thursday’s meeting, and they departed from MC3I to return to Washington, D.C. We had also planned a dinner for Wednesday evening for all the attendees of the Design Review at a local Italian restaurant known for its quality meals. Everybody attended this dinner, and a good time and a good meal were had by all. After the MC3I Program Manager paid the bill of over $500, they left a gift certificate for $50 on the table next to John. I scarfed up this gift certificate and put it into my pocket to some friendly barbs from some of the MC3I personnel. Upon seeing this gift certificate, I immediately realized that I could put it to good use in the MC3I TADMS team efforts. My plan was that at the end of the TADMS Program, I would present this gift certificate to a TADMS team member who made an important contribution to the program. For morale reasons, I did not want to tell anyone of this plan, except for the Program Manage the next day, who approved of my plan and my reasons for the secrecy (I did not want any friendly competition nor verbal jostling within the team for this gift certificate).
We then started the TADMS development, which went smoothly except in the last two weeks. One problem that we did have during the development was that we had to create an algorithm of mathematical complexity. None of the TADMS team members had the mathematical knowledge to create this algorithm, and it would be necessary for me to find a mathematical person in GE M&DSO who could create this algorithm. Before I began my search, the Lead Software Engineer described this problem to her husband, who also worked at GE M&DSO with security clearances and had a mathematical degree, and he realized he could solve this problem. As this algorithm was not of a classified nature, he created this algorithm after several hours of effort over the weekend. When his wife returned to work on Monday morning, she informed us that her husband had solved the problem over the weekend. I thought he deserved to be paid for his effort but soon found out that this was not possible due to the nature of chargeback time accounting at GE M&DSO. I then decided to award the $50 gift certificate to him, which I did by inviting him to a meeting in our SCIF. Upon presenting this gift certificate to him in front of the entire TADMS team, some team members inquired if this was my plan for the gift certificate from the beginning, to which the Program Manager replied that I had informed him of the gift certificate plan the day after I had scarfed it up at the dinner.
During the TADMS development, it became necessary for the MC3I Hardware Engineer to visit Ferranti to inspect the trailer modifications and, more specifically, the computer system integration into the trailer and the custom computer cables that MC3I was responsible for delivering with the computer systems to assure that they properly fit into the trailer. It was also necessary for me to go with him to inspect the trailer to make any management decisions that may be necessary. Ferranti deliberately scheduled this meeting for Thursday, Friday, Monday, and Tuesday so that both of us would have a free weekend in England.
We decided that on Saturday, we would visit Stonehenge, Woodhenge, and the City of Bath, Somerset, in southwest England known for its Ancient Rome Architecture and Roman Baths on Saturday. We also decided that we would spend Sunday visiting the University of Oxford and the University of Cambridge and their surrounding environs. The University of Oxford’s Museum of Natural History holds the university zoological, entomological, and geological specimens, which we were both interested in seeing. The University of Cambridge was where many famous physicists, including Isaac Newton, studied and worked, and they had exhibits about their famous alumni.
Woodhenge was a recently discovered archelogy site that predated Stonehenge and was constructed in the same manner as Stonehenge, except that it used tree stumps instead of stones. It was also located near Stonehenge, and a detour to it would not take much time. We were driving along the road where Woodhenge was located but could not find it until I noticed a small plaque on the side of the road. We stopped to read the plaque, which noted that this was the site of Woodhenge. The site was a piece of farmland behind the hedge boarding the roadway, with no buildings or any archelogy activity present. We proceeded to climb the low hedge and look for the stumps. The stumps were easily discovered, and we both stood on various stumps to view the other stumps, being careful not to damage them. After fifteen minutes, we proceeded to Stonehenge. Stonehenge was an interesting visit, but we were disappointed that we could get no closer than one hundred feet from the stones, as a small wall and a slab of Plexiglas atop the wall stood ten feet high to prevent anyone from approaching the stones.
Bath was a fascinating city, and we took an extended tour of the Roman Baths and walked around the area surrounding the Baths. As we did not arrive in Bath until the early afternoon, and the extended tour took ninety minutes, there was not much time to spend in Bath before we returned to our hotel. We had an early dinner in Bath and then proceeded to drive back to our hotel.
The trip to the University of Oxford took longer than we expected, and we spent so much time in the University of Oxford Museum of Natural History that there was insufficient time to visit the University of Cambridge, which disappointed both of us, but the Oxford Museum of Natural History was so interesting that we were glad we spent as much time in the museum as we did.
While the Hardware Engineer and I were at Ferranti, I introduced him to some of the other Ferranti Engineers that worked across the hall from the Ferranti TADMS team. One of those engineers was a young, attractive, single Englishwoman, and he was a young, attractive, single American male, and it was obvious to all that they were attracted to each other. Unbeknownst to all of us, they started a trans-Atlantic relationship that blossomed into love and eventually an engagement and marriage. When I discovered this relationship a few months after it began, I asked him if he had discussed this relationship with a GE M&DSO MC3I Security Officer, as she was a foreign national, and we were not supposed to become entangled with a foreign national. He had not considered this, and I advised him to immediately report this relationship to a Security Officer. When he returned about an hour later, he informed me that the Security Officer had no concerns when he learned that she had a MOD security clearance. After they married, in London, she moved to King of Prussia, PA, and they hosted a marriage party for all the TADMS team members after the TADMS program was finished.
The RAFWC had an office in the MOD building located in Bonn, West Germany (the capital of West Germany at the time), and the RAFWC decided that, as he had a temporary assignment in Bonn, the next few meetings would be in Bonn.
The first meeting in Bonn was a technical review meeting attended by the MC3I Program Manager, the two Software Engineers, the hardware engineer, and the Ferranti Chief engineer, as well as the RAFWC and RAFSC, and the DOD COTR and CWO. I was unavailable to make this trip, as my mother-in-law had died right before this trip was to begin. The MC3I Lead Software Engineer also did not attend this meeting as she thought it would be nice for an all-guy trip and that she and her husband had been to Bonn previously. The RAFWC deliberately scheduled this meeting for Thursday, Friday, Monday, and Tuesday so that the guys would have a free weekend in Bonn and its environs. This meeting went well, and the guys decided to visit the magnificent historical Cologne Cathedral, which is the largest Gothic church in Northern Europe, and that has two spires that are the second-tallest spires in Northern Europe. In one of the spires, visitors can climb 533 stone steps of the spiral staircase to a viewing platform about 100 m (330 ft) above the ground, which provides a magnificent view of the city and countryside. This viewing platform is an open-air structure that has about twenty high steel steps to get up to the viewing platform. When the guys returned home, they raved about Cologne Cathedral and the view from the viewing platform.
The next meeting, two months later in Bonn, was only a development phase status review meeting. John decided that I be the only representative from MC3I, as he was scheduled to go on vacation. This meeting was also scheduled for Thursday, Friday, Monday, and Tuesday to give everybody a weekend in Bonn. The Ferranti people, along with the RAFWC and RAFSC people, had their own plans for the weekend as they had visited Bonn several times before. I decided that on Saturday, I would explore the city of Bonn and its magnificent mansions and gardens and the birth house of Beethoven. I also decided to visit Cologne, West Germany, on Sunday to see the Cologne Cathedral, which the other team members had raved about visiting on their previous trip.
I did climb the Cathedral and observational platform stairs, but as it was a cold and windy day, the climb of the observational platform stairs was difficult. I had to pull myself up and down the observational platform stairs by the handrails, as these open-air stairs were swaying from the wind in a frightening manner. When I returned from this trip and informed the other team members of my climb, they were astonished, as all of them admitted that if not for the presence of the other team members egging them on, they probably would not have done this climb by themselves to the observational platform. They commented that I was very brave to do this by myself, but I retorted that it was more my stubbornness in finishing whatever I set out to do that was more probable than my bravery.
The next review meeting, occurring near the end of the TADMS development phase, was held near Wiesbaden, West Germany, at a large American airbase where the RAF had a small contingent based in this American airbase. This would also be the final location for the TADMS trailer after it was commissioned. It was only necessary for me and the Ferranti Chief Engineer to attend this meeting, which was scheduled for Tuesday through Friday, as all the other personnel involved in the TADMS effort were very busy. John elected not to go to this meeting and remained behind at MC3I to supervise the TADMS development efforts.
As the meeting ended mid-Friday afternoon, the RAFSC decided to take the Ferranti Chief Engineer and me out to dinner at a good restaurant he knew in the nearby town. This charming modern town has a wide pedestrian thoroughfare at its center, with local shops on its borders and many tables and chairs in its center. We sat down and ordered some beers while we had personal discussions until we went to dinner. At about 5:30 PM, a wave of very attractive and provocatively dressed young ladies entered this thoroughfare. I asked the RAFSC why this was happening, and he informed me that these were the single young ladies of the town that hoped to hook up with an American or RAF serviceman that would soon be arriving on weekend leave. They hoped to find a husband among the serviceman and then move to America or England after they married. As I cautiously looked at these young ladies, the RAFSC said, “Don’t worry Mark, we’re not in uniform, so they will have no interest in us.” As the RAF servicemen arrived at about 6:00 PM, we decided that the thoroughfare had become too crowded, and we went to the restaurant to have dinner. The Ferranti Chief Engineer and I both departed Wiesbaden on Saturday morning to Frankfurt Airport for our trip home.
Near the end of the MC3I TADMS development efforts, it was time to create the computer cables that would properly fit into the TADMS trailer. On Monday afternoon, I sent our Hardware Engineer, Greg, to another MC3I Program that had a small group that had the capability to make these cables. As we had alerted the team leader of this group about a month beforehand that we would need his group to make these cables, he responded that it would be no problem to make these cables. Greg did not return before I left work for the day, but he did inform the Lead Software Engineer of what he had arranged with this group. The next morning when I arrived at work, I found the Lead Software Engineer and another software engineer working on the TADMS computers. They informed me that Greg had arranged for this group to come on Thursday morning and take over the computers for the entire day to make, install and test these cables. This entire day would have a significant negative impact on our software development efforts, and I responded to them, “Well, that’s not going to happen”. They looked at me incredulously, and I asked them why they were incredulous. The Lead Software Engineer responded that they had expected me to agree with this arrangement, as I very often deferred to Greg on other decisions that I made that involved Greg. I explained to them that I knew I was doing this with Greg, but as Greg was assigned to TADMS on a part-time basis and was an important contributor to the TADMS effort, I did not wish to perturb him and engender the possibility of his leaving the TADMS effort. They agreed that it was wise of me in the way that I supervise Greg, but they were still concerned about giving up the TADMS computers for a full day.
When Greg arrived at work and informed me of this arrangement, I again said, “Well, that’s not going to happen”, and explained to him that if this did happen, it would have a significant negative impact on the TADMS development efforts. I instructed him to return to this group and make a different arrangement that would not significantly impact the TADMS’ development. I also informed him that if he could not do this, I would find a local computer equipment vendor who could do this for us. I also asked if he wanted me to accompany him, and he responded that he did not think this was necessary. When he returned, he informed us that the group was willing to come over Thursday afternoon at 2:00 PM and work into the evening if necessary to finish this task. I asked the Lead Software Engineer if she and her teammates had any paperwork that they needed to catch up on, and when she said that they did, I agreed to this new arrangement as a good compromise for all the parties involved. When this group arrived Thursday afternoon and began their efforts, I decided to leave early and asked Greg if he needed me to stay. He responded he would only need me if I was needed to make a management decision, and I told him that I had every confidence in him to make any management decision that may be necessary for this task. The next morning the cables were installed and working properly, and Greg informed me that they had only worked until 7:00 PM to finish the task. I thanked Greg, and the other group’s team leader, for their schedule accommodation and efforts in doing so.
During the MC3I software development, which proceeded smoothly, we simulated the subcontractor’s computational equipment as they were in the process of modifying this computational equipment and its software to meet our specifications. When the subcontractor delivered the modified computational equipment and software three days prior to the MC3I systems testing, and we connected it to the computer system, the computer system would crash after a minute or two of commanding and controlling this subcontractor-modified computational equipment. We hurriedly tried to analyze and resolve this problem, but we were unsuccessful in doing so before the systems test. I asked the COTR to postpone the System Testing, as I knew we would fail the systems testing, but he refused (as was his prerogative) for reasons that I later learned were personal, which I discovered during the resolution of this problem.
During the systems testing, which was to be conducted by the Operational Engineer assigned to TADMS, I often intervened in his systems testing, as I did not want the Operational Engineer to take the brunt of the criticisms from the COTR. My interventions upset him, and he walked out of the building in frustration at my intervention after the systems test was declared a failure by the COTR. The next morning, he came to work early to privately discuss this situation. He vented his frustration, and I apologized for the manner of my intervention, but I explained to him that I did not want him to take the criticism of the COTR that could tarnish his reputation. He understood my reasoning but reminded me that he was a senior engineer who had done much good work at MC3I and that he could withstand any criticism of his efforts. I again apologized for my conduct during the systems testing, and we resolved our differences, and we both proceeded to try to resolve the problem.
After failing the Systems Testing, the TADMS team started working twelve-hour continuous days to resolve this problem. After seven days of failure, I gathered the team together on Saturday morning to discuss our options. As it was obvious to me that the team members were exhausted and not exhibiting their best thinking, I instructed them to go home, relax, and not think about the problem, and return to work Monday morning refreshed and ready to give it another go. I went home as well to relax, but I did not stop thinking about this problem.
At the beginning of our analysis of this problem, I asked the Lead Software Engineer and the Hardware Engineer if this could be a problem of improper data being transferred to or from the subcontractor’s computational equipment or a cabling problem. The Lead Software Engineer informed me that they had examined this possibility, but they could find no improper data being transferred, and she continued her efforts to resolve this problem. The Hardware Engineer also successfully retested the cables to ensure that they were working properly. As I began to think about this problem over the weekend, I started to think in terms of what I called my flow process analysis. In analyzing a software problem, I often thought of the flow and control of the data in the computer system, while in analyzing a hardware problem, I often thought of the flow and control of the electricity in the computer equipment. In thinking about the flow of the electricity through the computer equipment, I realized that there was one piece of equipment that we had not analyzed to resolve this problem—the interface control board in the computer that connected the subcontractor’s computational equipment to the computer. The Interface control board is normally a conceptually simple component of a computer that sends and receives data to or from the computer and a device attached to the computer. This Interface control board has a piece of operating system computer software called a device driver that manages this board. In our efforts to resolve the TADMS problem, we had never considered the interface control board or the device driver as a point of failure, as this board and driver were considered a simple and reliable component of a computer. I began to wonder if there was a problem with the interface control board or its device driver that was causing the TADMS software to fail.
On Monday morning, I arrived at my normal time of 7:30 AM to discover one of the two software engineers assigned to TADMS had arrived about twenty minutes before me and was working on the TADMS computer to try to resolve this problem. I asked him why he was so early, as I had suggested a 9:00 AM start time, and he responded he had woken up early and refreshed and just decided to come in as he had nothing else to do. I then discussed my insight with him, and he agreed that it was a possibility but unlikely cause of the problem. I asked him if he could modify the device driver to display all the data that went into or out of the Interface control board, then pause for us to review the data before the board transferred the data. He thought that this was possible and that it would only take him about thirty minutes to make this change to the device driver. I instructed him to proceed to make this change, and about thirty minutes later, he informed me that we could begin testing. As we started the testing, the data appeared to be normal when a stream of data from the subcontractor’s computational equipment appeared that was nonsensible. When we instructed the device driver to proceed, the computer system crashed immediately. We tried this a few more times, and every time the nonsensible data from the subcontractor’s computational equipment appeared, and we instructed the device driver to proceed, the computer system crashed immediately. Consequently, we discovered the cause of our problem, and we realized that during the previous week were looking in all the wrong places for the resolution of this problem. When the Lead Software Engineer arrived at work shortly thereafter, and we showed her what was happening, she agreed that this was the source of the problem. She then set about analyzing what this non-sensible data was, and she soon determined that this was not data but machine instructions that confused the TADMS computer software upon the receipt of these machine instructions, which forced it to crash. We had to wait until noon to discuss this with the subcontractor, as they were located in Silicon Valley, CA, and did not start work until 9:00 AM their time.
During our problem resolution efforts, the COTR showed up in our SCIF at exactly 10:00 AM for a status report of our efforts. He would leave our SCIF shortly thereafter to spend the rest of the day doing personal activities. This was the reason he would not postpone the Systems Testing, as if he had postponed the systems testing, he would have had to stay at his job in Washington D.C. By not postponing the System Testing, he would have a government-paid expense vacation at our site, as he would have to stay on-site while we resolved the problem. On the Monday morning that we discovered the problem, he arrived at 9:00 AM, at the same time as our Program Manager, and he directed him to the office of the Marketing Manager. The story of that meeting, as related to me by John, was that the COTR began to bitterly complain to the Marketing Manager that we were not at work on Saturday and Sunday and, therefore, we were derelict in our duties. He then complained that we were being negligent in our efforts to resolve the problem, as the problem was taking too long to resolve, and he even suggested that I be relieved as the Chief Engineer. After the TADMS team was sure of the cause of the problem, I looked for John to inform him of our discovery. One of the software engineers informed me that as he was entering the building, he noticed John and the COTR entering the Marking Manager's office. I entered the Marketing Manager’s office shortly after the meeting started and announced that we had found the source of the problem, and the resolution would require consultation with the subcontractor, as his computational equipment was the source of the problem. As the subcontractor was located in Silicon Valley, CA, this conversation could not occur until noon our time, when they arrived at work. After I left the meeting, the COTR was visibly embarrassed and spoke very little. The Marking Manager suggested that we all meet in his office after I had spoken to the subcontractor to decide our future course of action, and the COTR left his office and the building and did not return until the scheduled 4:00 PM meeting. When John and I met with the Marking Manager and were waiting for the COTR to arrive, the Marking Manager remarked that I had made the right call in letting the team members go home for the weekend and that he had every confidence in my skills and abilities as the Chief Engineer, and that he had never even considered replacing me.
Upon telephoning the subcontractor at noon and explaining what we had discovered, he asked for a little time to examine this problem. About two hours later, he telephoned me back and informed me that it was indeed happening within his computational equipment and that these machine instructions were the internal commands of the computational equipment that shared the same software pipeline as the data being sent to the TADMS computer system. He suggested that we modify the device driver to reject these commands, which I thought was not a technologically sound suggestion. I informed him that per the TADMS Interface Control Document, he was constricted from transmitting these machine instructions, and as the Interface Control Document was contractually binding on him, he had to correct this situation. He agreed that this was his responsibility and he would get back to me on what needed to be done by him to fix this problem. An hour later, he informed me that they had discovered a fairly easy fix to their software that would correct this problem, and they expected that they would have this fix done in two days, and we should receive the fix by Thursday morning. I informed John of this, which he reported to the Marketing Manager and the COTR at their 4:00 PM meeting. At this meeting, it was decided to redo the systems testing on Friday morning.
We passed the systems test with no problems and then began the process of shipping the TADMS computers and the subcontractor’s computational equipment to Ferranti, along with our personal computers that we utilized for the documentation efforts and the management of the TADMS program. As the TADMS system was a classified system, it needed to be shipped in a classified manner. This classified shipping required special packaging and protections to ensure the computers were not damaged in shipment, as well as protection of the classified data that was stored in the computer. It also required that the CWO be present with the containers for the entire shipment from MC3I to Ferranti, which required him to make a transatlantic flight on a bumpy and slow Army transport aircraft in the cargo department of the aircraft. As the TADMS team had no knowledge nor capability to do this classified shipping, we arranged for another MC3I program that had the knowledge and capability to do classified equipment shipping.
This shipment effort took four days to accomplish, and it also turned out to be a significant bureaucratic effort in filling out all the paperwork required for classified shipments. We asked the TADMS program secretary, Margie, to be responsible for this paperwork and to work with other MC3I program Security Officer to expedite and accomplish this shipment. This Security Officer had a reputation for being hard-nosed and uncompromising, as well as being curmudgeonly and difficult to work with. His reputation turned out to be well deserved, and he drove Margie crazy with his demands. At one point in this process, I found Margie crying in the hallway. She was exasperated by all the demands of the Security officer and distressed that her reputation for excellent work would be tarnished. I hugged her and assured her that there would be no ill consequences to her reputation or career, as this Security Officer was well known to be a bastard that nobody worked well with. I also reminded her that her skills and abilities would be expanded by this effort and that this would make her more valuable for other secretarial positions at GE M&DSO. She calmed down and thanked me for my comfort, then proceeded to get the shipping task done as properly and quickly as possible.
After the TADMS system arrived at Ferranti’s Bracknell location, most of the TADMS team was scheduled to be on-site at Ferranti for four weeks for the integration and testing of MC3I’s TADMS system and the Ferranti trailer. As the DOD COTR was still smarting from his embarrassment in the Marketing Manager's office, and he was a petulant person, he decided to take out his ire on me and directed that I should not take this trip as he believed that I would be unneeded for this effort. Despite the protestations of my Program Manager, I was left behind to close out any paperwork with Margie that was necessary to end the TADMS contract. The MOD RAFWC and RAFSC, and the Ferranti Chief Engineer, were very surprised by my absence, and they also began protestations to the DOD COTR. Finally, at the end of the week, the MOD RAFWC demanded my presence, and the DOD COTR reluctantly allowed me to come to Ferranti until the end of the integration and testing. This effort was accomplished without any problems, and a turnover ceremony was scheduled for the last day.
My presence proved invaluable near the end of this effort, as the COTR began interfering in the paperwork efforts of the MC3I TADMS team by being a pest. I suggested on the last afternoon of this three-day paperwork effort that the COTR and I visit the local tavern to get a flavor of the common man’s tavern experience. As the COTR was known for his drinking, he readily accepted this suggestion, and we walked to the nearby tavern. We spent the next four hours drinking heavily and swapping stories, and he seemed to be over his petulance to me. By the time the MC3I TADMS team retrieved me from this drinking fest, I was plastered. They thanked me for doing this, as they were able to complete their paperwork, and they suggested a celebratory dinner at a nice restaurant. We all piled into John’s car for this dinner, and after the dinner, I was still plastered, and they escorted me to my hotel room and put me to bed. During the night, I often woke up and stuck my head out of the room window for some fresh air and to regurgitate my dinner. The next morning at breakfast, several of the MC3I TADMS team members commented about awful noises during the night, and I explained that it was me making these noises and the reason for the noise. They laughed and remarked that I should receive a Distinguished Service Cross for my effort of keeping the COTR away from them while they completed their paperwork. I, fortunately, was sober by breakfast and did not have a hangover, and I was able to go with them to the TADMS trailer. I was, however, presented with a humorous Certificate of Appreciation for this effort, given to me by John on that last day of the MC3I TADMS effort, as he had prepared humorous Certificates of Appreciation for all the MC3I TADMS team members.
At the beginning of this final integration and systems testing trip, it was decided, for financial reasons and the fact that the hotel was located only a few blocks away from the TADMS trailer location, that the MC3I TADMS team would only rent one large car while they were in England, with John being the designated driver and chauffeur to the TADMS team. With my presence, it was necessary for me to rent another car for the duration of this effort. As I was present for three weeks, I had two weekends that the TADMS team and myself planned to visit some locations in southern England.
On the first weekend, the MC3I TADMS team decided that they were going to visit The City of London and view the tourist attractions. As I had already done this on a previous trip to London, and I had two personal places in England that I wished to visit, the team agreed that I should make these visits this weekend.
The first place I wished to visit was Stratford-upon-Avon, as my wife was an English Literature major in college and spent a study month in the summer after her junior year at Wroxton College in England. She often lamented that she did not get to see much of England, but she did make it to Stratford-upon-Avon to see a Shakespeare play. She also lamented that she did not have much personal money to spend in England; she purchased only a few souvenirs during her stay in England. I thought it would be nice for me to visit Stratford-upon-Avon and see the birthplace and boyhood environs of Shakespeare. I also decided to call my wife from a local phone booth on the street across from Shakespeare’s birth house. I telephoned her, using the GE worldwide telephone system, to inform her I was standing across from Shakespeare’s birth house. I also asked her if there were any souvenirs that she wished me to purchase in Stratford-upon-Avon. She mentioned a few items that she remembered from her visit, and I was able to find all the items she mentioned, which I purchased for her.
The next day I visited Canterbury Cathedral, as during our visit to her Godparent's home in Los Angeles while I was working on CALMA, she told me that she had always liked the painted ceramic tiles of the Canterbury Tales that her godparents had purchased on their vacation to England and Canterbury Cathedral. As these tiles were only available in the Canterbury Cathedral visitor's shop, she could never obtain them for herself. I thought I would purchase these tiles (although they were somewhat expensive) as a nice surprise for her when I returned home. I did so, and she was very surprised and grateful for this gift.
Canterbury Cathedral was very busy with tourists on the Sunday I visited, and I discovered the area around the Cathedral was blocked off to automobile traffic. It was required that you park in a public street parking spot or in one of the private garages around the long circumference of the Cathedral, then take a short shuttle bus trip to the Cathedral. While driving around the circumference to find a public parking spot, I somehow managed to enter and drive on a street within this circumference. I became hopelessly lost trying to find my way out, and I noticed a Bobby standing two blocks from where I was. I dove up to him and apologized for being somewhere where I was not supposed to be and asked him for the quickest way out. He wondered how I was ever able to drive in a blocked forbidden zone, and I replied that I didn’t know how I managed to get in, but I did know that I wished to exit as soon as possible. He provided me with simple directions to exit, and when I did so, a public street parking space opened, and I parked in this space and took the short shuttle bus ride to Canterbury Cathedral. Canterbury Cathedral was a fascinating visit, but it took me longer to drive there than I expected, and I could only stay for a few hours before I needed to drive back to my hotel.
The following weekend the MC3I TADMS team decided to visit the countryside of The Cotswolds area of west England, as it was considered an outstanding natural beautiful area of England, with many charming towns and villages. We all piled into John’s rental car, except for Greg, who was spending the weekends with his English girlfriend and the Operations Engineer as he had already seen The Cotswolds area when he was stationed in England during his military service and he wished to visit some English friends during this business trip. I lent him my rental car for the weekend, and we took a Motorway route to The Cotswolds in John’s rental car. This was a longer drive than we expected but was well worth the drive time as, indeed, we all agreed that this area was very beautiful. We dove around The Cotswolds for a few hours and had a midday meal in one of the small towns of The Cotswolds. Later in the afternoon, we began a leisurely drive on the non-Motorway roads back to our hotel to observe the scenery of this portion of England.
The next day we explored the south coast of England, starting with Plymouth, then onto Southampton, and ending with Brighton. John wished to visit Plymouth to see the HMS Victory (the flagship of Lord Nelson at the Battle of Trafalgar) to board this ship and tour the museum. We all wished to see the famous seaside resort of Brighton, while Southampton was between these two places. Unfortunately, when we arrived at the HMS Victory, there was a sign that informed us that the ship and museum were closed for the weekend. Disappointed, we visited some other tourist sites in Plymouth and drove on to Southampton. We did not spend much time in Southampton, as we wished to see and have dinner in Brighton. The beaches of Brighton were very lovely, but it was a resort town rather than a tourist attraction, with few places for a tourist to visit. We did have a nice seafood dinner in Brighton, and after dinner, we drove back to our hotel.
On our last day at Ferranti, the LTMS Program had a nice turnover ceremony and luncheon attended by all involved in the TADMS program, including the DOD Colonel and the high-level executive of Ferranti, who was responsible for the Ferranti effort. This executive knew of Ferranti’s efforts in TADMS but had little knowledge about the MC3I efforts in TADMS. As he had the proper security clearance to be informed, I was asked to give him a briefing on the MC3I efforts in TADMS but not to show him any classified data, as he had no need to know this data. It was at the end of this briefing after he mentioned the acquisition of ISC that I warned him to be careful about the purchase of ISC. With the turnover ceremony being complete, we all said our goodbyes and returned to America.
After returning from this trip, the COTR decided to issue an unclassified press release about the TADMS's success and asked John to prepare a draft of this press release. John did so while the TADMS team finished the paperwork to terminate the contract. Upon submitting this press release to the COTR, he was dissatisfied with the press release, as John had given equal weight to all the major parties involved in the TADMS effort, while the COTR wanted to emphasize the cooperation between the DOD and MOD and give little credit to MC3I, Ferranti, and International Imaging Systems for their efforts in TADMS. John responded that if that was what he wished to do, then MC3I could not participate in the press release. The final press release that the COTR released only gave a one-sentence mention of the efforts of MC3I, Ferranti, and International Imaging Systems, which was disappointing to all of us. On the final day of the TADMS contract, we held a party in our soon-to-be-closed SCIF, and John presented to each of us his humorous Certificates of Appreciation. We said our goodbyes, but we knew that as we all worked in MC3I, we would run into each other in our future efforts in MC3I.
* * * * *
Near the end of the TADMS Program, GE M&DSO decided to create a secretarial pool of all the secretaries in GE M&DSO that would be assigned as needed to the various managers in GE M&DSO. Previously, each division hired and reassigned secretaries as necessary. Margie, the TADMS secretary, was transferred to this secretarial pool and had hopes of becoming its manager as she had over ten years of experience in M&DSO as a secretary, and she was very competent and a self-starter, and she knew many of the managers and programs in GE M&DSO. Unfortunately, another secretary was assigned to this secretarial pool and appointed its manager. This other secretary was in her late thirties, recently divorced with an adolescent daughter, very sexually attractive, and was advancing her career by engaging in sexual relations with many married M&DSO managers. Margie was not, and would not, do this. This new secretarial pool manager recognized Margie as a threat to her position and started making life miserable for Margie in hopes that she would leave GE M&DSO. Margie put up with this for almost a year but finally decided her position was hopeless, and she resigned from GE M&DSO.
My duties and responsibilities as Chief Engineer during the development phase of TADMS did not require a full forty hours a week to accomplish. In the hours that I was not engaged in my TADMS efforts, I began to document the Systems Engineering process that I had learned in my career at MC3I. This document was about two-thirds completed by the end of the TADMS program, and I continued to work on it as time allowed. I was able to complete this document when I was awaiting the return of the MC3I International Marketing Manager from a three-week trip he made to Germany for our Tactical Intelligence Exploitation (TIE) Marketing effort.
Tactical Intelligence Exploitation (TIE) Marketing
After TADMS was successfully completed, I was assigned to be the engineering representative to the MC3I International Marketing Manager, who was about to begin a three-week tour of the Western European nations to search for business opportunities to partner with other companies (NATO preferred multi-company responses to their proposals). I helped him prepare an unclassified presentation of GE M&DSO MC3I technical capabilities, and he asked me to go with him on this trip and give this presentation. I was excited to do so, as I would be visiting a half dozen or so major metropolitan cities in Western Europe. Unfortunately, my father-in-law died right before this trip, and I was unable to go on this trip. The MC3I International Marketing Manager decided to make this trip alone and give this presentation, and he would schedule any follow-up trips for me to provide more insights on M&DSO MC3I technical capabilities to those companies that expressed an interest in partnering with GE M&DSO MC3I on NATO proposals. When he returned, he informed me that it was much too early for my services, as most of his interaction involved management and financial considerations that had to be resolved before my services were needed. I was, therefore, assigned to assist in the EOS/DIS Proposal. While awaiting his return from this trip, I completed my MC3I Systems Engineering processes documentation, which was very helpful in my EPI efforts.
FAA Request for Information
Whenever a federal government agency is thinking about issuing a Request for Proposal (RFP) for a new technological system for which they have scant knowledge or little experience in they will often issue a Request for Information from companies that they believe have the knowledge and experience to develop the technological system. The response to the RFI’s is voluntary and to be done at the company’s discretion with company monies. Most companies are interested in responding to these RFIs in hopes of giving them a competitive advantage when the RFP is issued. Most companies allocate only a few people for a few weeks to respond to these RFIs to keep the cost impact low.
Another GE Operation received an RFI from the Federal Aviation Administration for a technological capability to monitor aircraft in and around major airports to assist the air traffics controllers in their duties and responsibilities. The GE Aerospace Operation that was responsible for responding to this RFI did an initial review of the RFI and determined that they would need a complex computer system and a great deal of software development to accomplish this technological system. Having little knowledge nor experience in computer systems development, they requested that GE M&DSO provide a person who could provide this knowledge and experience in responding to the RFI. I was, therefore, assigned to assist them in responding to the RFI.
Upon being sent to Washington, D.C., to assist with this effort, I soon discovered how complex and impracticable such a system would be. At this stage of the airline industry, aircraft transponders only provided limited information about an aircraft, mostly just the identification of the aircraft. Radar was utilized to determine the position of the aircraft, and radar did not work for aircraft that were close to the ground. Thus, it was impossible to accurately determine the positions of aircraft in and around airports. Global Position Systems (GPS) technology in aircraft could solve this problem, but GPS technology was not fully operational at this time and was not incorporated in aircraft. Additionally, GPS had insufficient positional accuracy for this system to be effective, and positional accuracy was degraded by the United States government so that foreign belligerents could not utilize GPS in conducting military operations.
Upon examining the computer systems and software development needed to accomplish this goal, I determined that the current computer capabilities were insufficient for the processing requirements of such a system, and the software development would be exceedingly complex and fraught with errors. Therefore, I recommended that the FAA not pursue this RFP until the technological issues were resolved by future technological advances.
A few weeks after we submitted our RFI, the FAA announced that they agreed that this technological system was impractical at this time and that no RFP would be forthcoming. However, these technological advances did occur, and the FAA eventually developed such as system and is in the process of implementing this system at major American airports.
DEA Request for Information
Shortly thereafter, the Drug Enforcement Agency (DEA) issued an RFI with the goal of tracking all maritime and aircraft traffic on and over the Caribbean Sea in the hopes of discovering and interdicting drug traffic from South and Central America. I was assigned to this RFI team to assist them in responding to the complex computer system, which required a great deal of software development to accomplish this technological system. Upon examining the RFI, I realized that this technological system was even more impractical than the FAA RFI, as most maritime and aircraft traffic had no transponders and GPS capabilities, and it was expensive to install such systems in boats and airplanes. There were also no radar systems in the Caribbean that could cover the entire Caribbean Sea, and radar could not work for surface boats. In addition, we could not expect that drug smugglers would install such a system on their boats and aircraft, and it would be impossible to distinguish between legitimate and illegitimate maritime and aircraft traffic on or above the Caribbean Sea for those craft that did not have such transponders and GPS capabilities. I, therefore, became the naysayer on this RFI effort and recommended that we respond that such a system was technologically infeasible.
The DEA assigned three of their agents to our RFI team to assist us in answering any questions we may have had about DEA operations to make for a better response. The lead DEA agent, after I expressed my concerns and naysaying, pulled me aside to privately inform me of the real purpose of this system. CIA Director William J. Casey, who was the driving force behind this RFI, was obtaining intelligence about planned drug smuggling in South and Central America. However, he was constricted in sharing this information with the DEA as Congress had passed a law restricting the sharing of information between intelligence agencies and other non-intelligence agencies within the United States. Director Casey was attempting to do a run-around of this law by having the capability to report maritime and aircraft traffic involved in drug smuggling by tagging the source of this information from one or several fictitious companies that the CIA operated. When the DEA saw such tags, they would know that this was accurate information, and they could start an operation to interdict, arrest, and confiscate the drugs and the boats and aircraft involved in drug smuggling, thus skirting the law.
With this in mind, I went about thinking about how to accomplish this, but I was disquieted by the ethics of skirting the law. However, about two weeks after he had informed me of the true reason for this system, CIA Director Casey passed away, and both the acting CIA Director and the DEA Director decided to abandon this effort, as they had not wished to become involved in the political uproar if it was discovered what they were doing. Thus, I was relieved and happy to return to GE M&DSO to resume my career, where I was assigned to assist in the EOS/DIS Proposal efforts.
EOS/DIS
The Earth Orbiting Satellites / Data Information System (EOS/DIS) was a NASA RFP for the development of a common ground station for command, control, and communications capabilities (EOS) and a data repository and distribution capability (DIS) for all the current and future NASA Earth Orbiting Satellites. This was a very large contract, as it was projected as an initial contract of three years and three hundred million dollars for the design, development, and construction, with a follow-on contract of three years and three hundred million dollars for the data integration of current satellites as well as for improvements, enhancements, and upgrades. Every American aerospace company was very interested in winning this contract, and GE Aerospace dedicated six million dollars to the proposal efforts to win this contract (the largest proposal dollars ever allocated in GE Aerospace’s history).
GE Aerospace decided to combine two of its organizations to work on this proposal. The other GE Aerospace division had recently finished the development of a NASA ground station that NASA expressed much satisfaction with, and the MC3I division of M&DSO had much success in developing Data Information Systems. Due to classified information concerns of the possible leakage of classified information that could possibly occur in this joint proposal efforts, it was decided that M&DSO would be responsible for the EOS/DIS NASA proposal. About half a dozen of the people that worked on the NASA ground station moved themselves to an unclassified building at M&DSO to begin working on the proposal. This included the Chief Engineer and a Deputy Program Manager of the NASA ground station, and these two persons were appointed by senior GE Aerospace’s management to lead the EOS/DIS proposal efforts. Shortly after they began working on this proposal, I was asked to assist them with the Data Information System proposal effort.
I spent the next week reviewing the proposal, then joined them in the planning for the proposal efforts. It soon became apparent to me that they had no concept of Data Information Systems nor the complexity or effort that it would take to develop a Data Information System for the Earth Orbiting Satellites. They were concentrating their efforts on designing and developing the best ground station ever built for NASA. Despite my pleas that they expend more effort on the Data Information System, as my reading of the proposal led me to believe that NASA’s main interest was in the Data Information System, they ignored my pleas. This became a point of contention between them and me, and our working relationship deteriorated so quickly that by the end of three weeks of effort on my part, they were essentially ignoring me and excluding me from meetings.
I, therefore, decided to express my concerns directly to the M&DSO Marketing Manager, who previously was the MC3I General Manager that I had worked closely with since my employment in MC3I. As he trusted my judgment from our previous working relationship, he expressed concern about my concerns. However, he informed me that he was only titularly responsible for the EOS/DIS proposal, as the GE Aerospace management had made it clear that the EOS/DIS proposal team had free rein to do as they saw fit. I then suggested that I should be replaced, as I would no longer be an effective team member due to the deterioration of my working relationship with the other members of the EOS/DIS proposal team. He agreed to replace me, as he had another RFP, and he thought I was the best person to lead the proposal for this RFP. I was therefore assigned as the Proposal Manager for the CME-RADIUS Proposal.
While working on the EOS/DIS proposal in a one-story, very high-ceiling old GE factory building, where I spent my time awaiting clearance, I noticed one of the steel support columns near the EOS/DIS proposal team was shaking somewhat violently. I informed the EOS/DIS Proposal Chief Engineer of this and suggested that we evacuate the building until the building engineer inspected and corrected this shaking. He rejected my suggestion and did not evacuate the building, but he did inform the building engineer of this situation. I, on the other hand, left the building until the building engineer arrived a few hours later. When the building engineer examined this column, he immediately ordered the evacuation of the building until he discovered and fixed this problem. He discovered that the ceiling bolts of the column had cracked and were loose, which he promptly replaced and then allowed everyone back in the building.
About nine months after I stopped working on the EOS/DIS proposal, I was in the Marketing Departments Reproduction Room making copies of several reports. The Reproduction Room also contained the Marketing Departments FAX machine, and while I was making copies, the FAX machine started printing out a fax from the NASA EOS/DIS Proposal Office. This two-paragraph fax started with the normal greetings and salutations and thanks for submitting an EOS/DIS proposal. The next paragraph stated that they had reviewed our proposal, and their finding was that the ground station section of the proposal was estimable, but the Data Information System section of the proposal was deficient and showed a lack of understanding of the requirements nor the importance of the Data Information System for the EOS/DIS RFP. They, therefore, rejected our proposal, and this rejection was not appealable under the terms of the RFP.
I realized that this fax should not be left in the Reproduction Room, and I carried it down the hall to the Marketing Manager's office. Upon entering his office, I asked his secretary if he was available, and she informed me that he was having a meeting with the other marketing leaders in his office. I informed her that I needed to interrupt this meeting as I had a very important fax from the NASA EOS/DIS Proposal Office. With eyes wide open and shaking my head in a no fashion, she immediately allowed me to enter his office, and when I entered, he asked me what he could do for me. I went to his side and showed him the fax, and upon reading it, he turned pale. He then dismissed everyone from his office except for myself and commented to me that I apparently knew what I was talking about when I expressed my concerns about the initial EOS/DIS proposal team. He also directed me not to inform anyone about this fax until an announcement was made, and I responded, “What FAX?”
After the announcement about the EOS/DIS proposal rejection was made, GE Aerospace fired the Proposal Manager, shipped the ground station people on the proposal to their former division with inferior positions, and the MC3I Marketing Manager found other employment outside of GE within two months. His EOS/DIS experience of not having authority but responsibility is the perfect example of a maxim I had to never accept responsibility without having the authority to do what I believed to be correct, for the consequences of doing so are usually failure and being blamed for the failure. His leaving GE had unfortunate consequences for my future career in M&DSO, as I shall explain later in this document.
RADIUS- RCDE Proposal & Program Management
The Defense Advanced Research Projects Agency (DARPA) of the DOD issued a directed proposal to the Stanford Research Institute (SRI) for the Research and Development of Image Understanding Systems (RADIUS) and a RADIUS Common Development Environment (RCDE). The RCDE was for the design and development of a software environment that could be utilized for the development and evaluation of image understanding algorithms. The application focus of RCDE is on image exploitation, where the exploitation tasks are supported by 2D and 3D models of the geographic site being analyzed. An initial prototype for RCDE was SRI International‘s Cartographic Modeling Environment (CME), and MC3I was subcontracted to SRI, who had the lead on the RADIUS- RCDE Proposal. This team was composed of Lynn H. Quam and Thomas M. Strat of SRI, Joseph L. Mundy of GE R&D, William Bremner, and Mark Horwedel of MC3I. MC3I was involved as we had the security clearances to utilize classified data in the development and utilization of the RCDE. Dr. Mundy eventually obtained the proper security clearances so that he could join the classified efforts of MC3I in the RCDE.
As this proposal was for the design and development of a computer system rather than an investigative effort, the contract was to be an engineering contract rather than a research and development contract. An engineering contract has specific requirements, with due dates and deliverables throughout the contract, for a tangible engineered product to be delivered at the end of the contract (rather than wordy reports). As this was an engineering contract, I was appointed the Proposal Manager for the MC3I RADIUS- RCDE Proposal & Program efforts, reporting to the MC3I Research and Development Manager, who reported to the MC3I Marketing Manager. The MC3I Research and Development Manager was very appreciative of my appointment, as I understood engineering contracts and their legal, financial, engineering, and management requirements, even though I did not have a college degree as all his other staff had. The other members of the RADIUS-RCDE team did not understand engineering contracts, as all their previous experience was with research and development contracts. Other leading scientists on image understanding systems in the United States wished to join us in this effort, and they were allowed to do so at their own expense and only in an advisory role.
The RCDE computer system was a thorny computer problem, as RADIUS scientists utilized the LISP computer language or the C/C++ computer language to develop their algorithms. The computer environments for LISP and C/C++ had little in common, and while a Unix computer could have both a LISP and a C/C++ computing environment under their operating system, there was no way to interactively share algorithms or data between the LISP and C/C++ computer environments. Dr. Mundy of the RADIUS- RCDE Proposal & Program team thought of a way to accomplish this sharing, and the RADIUS- RCDE contract was for the design and development of this sharing capability between these two environments. This sharing was very important to DARPA, as it could accelerate the research efforts of image understanding scientists and the interoperability and testability of their algorithms.
Funds for the RCDE contract were very limited, with most of the funding supplied by another unclassified government agency that had only previously funded research and development contracts. Therefore, the RCDE contract had to be severely constrained to match the funding available for the RCDE contract. An engineering contract always had a FERB component to process RFCs, as I previously explained in my FERB job efforts at MC3I. If we included FERB in the RADIUS- RCDE Proposal & Program engineering contract, we would overextend the funding for the RCDE Program. I explained this to DARPA Management and the other agencies' management for the RCDE contract, and they agreed not to include FERB in the RCDE engineering contract. This lack of FERB in an engineering contract also needed approval from MC3I management, as they had never done this before in an engineering contract, but they agreed not to include FERB in the RCDE contract. This lack of FERB ultimately proved my undoing in the RADIUS- RCDE Program.
During the contract development and negotiation efforts between DARPA, SRI, and MC3I, it became obvious to DARP that SRI was not capable of leading an engineering contract, and they decided to put MC3I in the leadership role of the RCDE contract, which seemed to relieve the SRI RCDE leader, Dr. Quam, as he was a renowned scientist that only wanted to do scientific work and wanted no parts of any management efforts. DARPA also insisted in a clause of the contract that MC3I could not replace me without their approval, as they had faith that I could effectively lead the efforts of the RCDE team and did not want to lose my services.
The RADIUS- RCDE contract development efforts required that I travel a few times to SRI International headquarters, located in Menlo Park, California, for meetings with them and sometimes DARPA management. These meetings were generally two- or three-day meetings in the middle of the week, and as I was familiar with this area from my CALMA efforts, I made no excursions during these trips. I simply flew to SRI on the day before the meeting and flew back on the evening after the last day of the meeting. The RADIUS- RCDE contract negotiations were all held at MC3I, which SRI was not allowed to attend as we often discussed confidential company information during these negotiations. However, the SRI's subcontract was reviewed during the negotiations for DARPA approval of the subcontract to SRI.
In order to obtain upper DARPA management approval for the RCDE contract, we had to give a briefing on the contract to the upper DARPA management. This was a formal briefing with all the RCDE team present, and the DARPA RCDE management suggested that we be more formal in appearance rather than the casualness we normally maintained, as this could impact the approval of the contract by upper DARPA management. As Dr. Quam had a wild scientist’s appearance, I suggested that he dress more conservatively and wear a tie to this briefing. When he showed up for this briefing, he had indeed dressed more conservatively, but he topped off this somewhat conservative dress with the biggest and most garish tie that he could find. We inwardly laughed at his tie and his independent streak and never again made any suggestions regarding his appearance. The upper DARPA management approved the contract, and the RCDE team efforts began immediately.
Being the Program Manager of the RCDE team was often frustrating for me, as I came to adopt a belief that “If you gather the leading dozen scientists in a room to get an opinion, you will end up with sixteen different opinions.” It was also very difficult to get them to focus on the practicability of the RCDE computer system, as they wanted to focus on the conceptual aspects of the RCDE computer system. We held monthly meetings in Washington D.C. of the RCDE team with the DARP and the other Agency managers of RCDE, which the science advisors that could attend. These meetings usually achieved very little and were mostly gabfests.
At the fourth or fifth such meeting, in which very little was resolved, I was frustrated by the indecisiveness and the gabfest. When the DARPA and the other Agency manager of the RCDE program announced at the end of the all-day meeting that they wanted to accelerate some of the deliverables and their due dates, I lost my self-control. Unbeknownst to me, I was suffering from severe Sleep Apnea and was sleep deprived (which I did not discover until a few months later) and not fully in control of myself. I briskly informed them that this was not possible as the contract had no ability to process RFCs. They then asked how they could issue an RFC for this change, and I told them that they would first have to come up with an additional one hundred thousand dollars for the contract before I could even consider reviewing an RFC. This stunned and upset them, as they had obviously forgotten our FERB discussion, and they were accustomed to getting whatever they requested, as was possible in a research and development contract.
It was also during this time that the MC3I Research and Development Manager found another position in GE M&DSO, and the Marketing Manager that appointed me to the RADIUS- RCDE Proposal & Program left GE as a result of the EOS/DIS debacle. The new MC3I Research and Development Manager did not want anybody on his staff that was not a college graduate, and the new Marketing Manager was someone unknown to me and did not appreciate the special skills and abilities that I brought to the RADIUS- RCDE Program. Shortly after the new MC3I Research and Development Manager was appointed, he tried to have me replaced, on a part-time basis, with the salesman who was responsible for finding research and development contracts for MC3I. As this involved a contract change to the costs, and an agreement from DARPA to waive the contractual requirement that I could not be replaced without their approval, nothing came of this effort. Also, when working on RADIUS-RCDE, it was decided that I would no longer be assigned to the Marketing Department, as CME-RADIUS was considered an engineering program. I was placed under the supervision of Steve Schramm, the assistant manager of the MC3I Systems Engineering Department. I had known Steve for some years, and we both liked and respected each other. Steve was fully aware of my skills and capabilities, and he refused to replace me and allowed me to operate freely on the RADIUS- RCDE Proposal/Program.
A week after I lost my self-control, I was informed by Steve Schramm that I was to be replaced as the RADIUS- RCDE Program Manager at the request of DARPA, and with the concurrence of the new MC3I Research and Development Manager and the new Marketing Manager. He thought that this was the best for me, as I now no longer had any support from the MC3I management of the RADIUS- RCDE Program and of the government agencies. I agreed with Steve, and I began working on EPI. Steve also arranged to shift the RCDE Proposal management back to the Marketing Manager, as when he heard from me what was happening in the RCDE efforts, he did want any parts of this contract to involve any Systems Engineering personnel or himself.
EPI
The Engineering Process Improvement (EPI) was an effort by GE M&DSO MC3I to formalize the engineering processes by documenting the who, what, when, where, why, and how of the engineering processes of Data Base, Hardware, Networking, Operational Processes and Training, Software Engineering, and the Testing components of a Proposal and Program. Each individual engineering process would have a separate volume documenting the processes to be utilized when undertaking any effort for a process, with an additional introductory volume that would summarize all the processes. This effort had been ongoing for many months when I was assigned to assist this effort. During my efforts as the TADMS Chief Engineer, as time allowed, I created my own documentation of the engineering process that I had learned from my experiences at MC3I. Upon showing this document to Steve Schramm, who was leading the efforts of the EPI team, he remarked that my document was a succinct summary of the EPI efforts that would make a good start for the introductory volume. I was therefore tasked with drafting the introductory volume. This required that I review the other draft volumes to ensure that all their major points were included in the introductory volume. This review and drafting took me approximately two months to complete, and at the end of these efforts, there were no available assignments to which I could be tasked. This was not unusual at M&DSO, as occasionally, when an engineer completed their efforts, it took a few days to find a new proper assignment for them. This was known as Awaiting Assignment (AWA), and good management often planned for someone to be AWA until the proper assignment was available.
The Hell Hole
While I was working as the CME-RADIUS Program Manager, and during my efforts on EPI, GE M&DSO MC3I was completing its main contract, and the GE M&DSO management decided to disband MC3I. Many of the employees were assigned to other divisions and quite a few of them we laid off, as government spending on GE M&DSO efforts had decreased as a result of the peace dividends from the collapse of the Soviet Union. I was one of the employees who was transferred, and I learned that the laid-off employees were preparing a class action age discrimination lawsuit, as all the laid-off employees were over forty years of age and they were some of the highest salaried employees in MC3I. I do not know what happened in the lawsuit, but I do know what happened to me because of this transfer, and it was not good.
The Systems Engineering Manager that I was transferred to had a very different management style from the MC3I management style. MC3I believed, as I do, that if you give someone responsibility, they had to have the authority to do what they thought was correct, as long as they did violate GE M&DSO and Federal contract regulations. As such, I had much flexibility and discretion when I was in positions of responsibility in MC3I. My new Systems Engineering Manager believed in a top-down authoritative management style, in which decisions were passed up and down the management structure, with him making the final decision, and little discretion nor any flexibility for anyone on the staff that was not a manager. He also expected his staff to genuflect on his knowledge, intelligence, wisdom, and management style, which he had very little of. He had risen to his current position by office politics machinations and backstabbing, and his flattering of upper management, and he retained his position by ensuring no one underneath him could pose any threat to his position. This was not a management style that I felt comfortable with and one that could properly utilize my skills and abilities.
In Federal contracts for development efforts by the contractor, there were three types of contracts—a Firm Fixed Fee Contract, a Cost-Plus Fix Fee Contract. and a Cost-Plus Award Fee contract. In a Firm Fixed Fee Contract, the government would pay a negotiated price for all efforts and fees of the contract. In a Cost-Plus Fix Fee Contract, the government would pay the costs associated with the contract, and the contractor would be paid a negotiated fixed fee based on the costs incurred for their efforts, either at the end of the contract or at scheduled intervals in the contract. In a Cost-Plus Award Fee contract, the government would pay the costs associated with the contract and, at scheduled intervals, would grade the contractor’s performance on a scale of 0 to 100, which would be the award fee percentage of the negotiated fee for their efforts.
Both MC3Is main contract and my new Systems Engineering Manager's contracts were Cost-Plus Award Fee contracts. However, MC3I had consistently been graded in the nineties, while my new Systems Engineering Managers contract grading was usually below (and sometimes much below) the seventies. GE M&DSO was hoping that by transferring many of the MC3I staff to this contract, their skills and abilities would elevate the grading of this contract. Unfortunately, my new Systems Engineering Manager and his staff were often compared unfavorably to the MC3I staff by the government, and being a resentful person, he decided to assign the MC3I staff (including myself) to non-important positions in his organization (and his grades did not improve).
He also believed that all of the engineers on his staff should, at a minimum, be college Bachelor's Degreed graduates, and his managers should have at least a Master’s Degree. When I and two others who did not have college degrees were transferred to his staff, he was determined to make them resign by making their life miserable, as he could not terminate their employment except for cause.
In addition, I had an interaction with him a year earlier where he came out second best. It had always been my policy, when I started a new proposal, to review with the Costing Department Manager the expected need for manpower and equipment to meet the requirements of the proposal. I did this to ensure that I would provide them with all the paperwork they would require to generate the Cost Volume for the Proposal. The Costing Department was responsible for creating the Cost Volume to be negotiated for a proposal or changes to a current contract. This was done to ensure that the Federal Acquisition Regulations were followed, that the costs were thorough and accurate and that the equipment to be procured was obtained at the lowest cost available. When I discussed this with the Costing Department Manager, we agreed upon a date that I would deliver this paperwork to her so that she could generate the Costing Volume in sufficient time for me to review it and submit the proposal by its due date. We had successfully done this several times in the past, and she had no difficulties preparing my Cost Volumes.
On the last proposal I prepared (the RADIUS- RCDE Proposal), we agreed that I would deliver the cost paperwork on a Monday morning, and she would have the Cost Volume prepared by Thursday morning. When I arrived Monday morning with the paperwork, she was in a heated argument with another man that I did not know, who turned out to be my future Systems Engineering Manager. He was demanding that she prepare a costing for a contract change with the paperwork that he had just handed her by Wednesday afternoon. She had reviewed the paperwork, then informed him that the paperwork was incomplete to prepare a costing based on what she saw, and it would not be possible to produce a costing for this change in less than a week. He was being very combative with her, and she stood firm as she knew her business and knew that there could be professional and legal consequences if she did not do her job properly. He continued to harass and berate her (which made me angry, but there was nothing I could do for her), and after ten minutes, she turned away from him and asked me if that was the paperwork that we had agreed upon. When I replied in the affirmative, she took the paperwork from me and, without looking at it, told me that my costing would be ready Thursday morning. At that point, he started taking his wrath out on me, telling me I was a nobody as he didn’t know me, that my contract could not be as important as his contract, and then began chastising the Costing Manager for giving me priority without even looking at my paperwork. The Costing Manager and I said nothing but shook our heads to each other, and I left the Costing Department. When I returned to the Costing Department on Thursday morning to retrieve my Cost Volume, she attempted to apologize to me, but I cut her off, telling her that she had nothing to apologize for and that she should get an apology from the rude man who was attempting to bully her. She responded that that would never happen, as he had a reputation that did not allow him to admit mistakes and for being abrasive to those that did not work for him. I thanked her and left with my Cost Volume, which had no problems.
After I was transferred to my new Systems Engineering Manager and was introduced to him in his office, he glared at me with a scowl and said, “You’re that guy in costing”, and then turned his chair away from me. I left his office knowing I had a big problem. I discussed this problem with Bob, an MC3I Manager that had also been transferred to this Systems Engineering Manager and who also did not have a college degree. Bob informed me that he had a short discussion with this Systems Engineering Manager upon his transfer and determined his prejudice against non-college degree engineers, which resulted in a lack of assignments he was experiencing. He also informed me that he had decided that there was no future for him in GE M&DSO, as no other division was hiring due to decreased spending as a result of the peace dividends from the collapse of the Soviet Union. He, therefore, was considering his employment options outside of GE and suggested that I also make such considerations. As Bob was older and his children were grown up, and his wife worked at GE M&DSO in a secure and well-paying job, his outside options for employment were greater than mine. As I had a wife who was currently unemployed and a young daughter enrolled in a private educational school, I decided to hang on to my GE M&DSO employment.
My first problem was that as I was awaiting an assignment, he decided to give me no assignments for the next six months. I was given an open-air desk, as a cubicle would afford me some privacy, and for six months came into work and sat at my desk, starting at the other non-college MC3I transferred person as his desk was across from my desk, and reading technical magazines and technical textbooks, which almost drove me out of my mind. My new manager provided no help, as she was a puppet of the Systems Engineering Manager and not very competent as well. It was not until Human Resources discovered that we had not done any work on a government contract, for which they could bill to a government contract while awaiting assignment was paid by GE M&DSO funds, that they insisted that the Systems Engineering Manager assign myself and the other person to a task in his government contract.
My Systems Engineering Manager then assigned me to a series of small, insignificant, and very short-term assignments that were ill-suited to my skills and abilities but were more suited to a very junior engineer on his staff. He did give me one assignment of small importance, as no one else was available to do this assignment. This assignment was to write a two-page description of a piece of equipment they were going to use, as the COTR wanted to better understand this piece of equipment. I was given one week to complete this assignment (which was no problem as I could do it in two days), but I milked this assignment to fill my week. I awoke Friday morning to discover that my wife had taken very ill during the night, and she asked me to stay home to take her to the doctor. I called my manager to explain my absence that morning and that we had a doctor’s appointment at 3:30 PM. She insisted that I come to work and complete the assignment before I took my wife to the doctor or face the consequence of being late on an assignment. I knew the COTR did not need this paper immediately and that this was an attempt to give me a black mark that could be used in the future to terminate my employment for cause. My wife heard the conversation and told me to go to work but return by 3:00 PM to drive her to the doctor's office. I did so, completed the paper and, turned it in on time, then went home to take my wife to the doctor.
I did get assigned to one other important task, which I recognized as an attempt by the Systems Engineering Manager to have me terminated for cause. The head of the Government Agency for the contract had to decide on what network topology (how the workstations connected to the Mainframe computer and communicate with each other and the Mainframe computer), and he didn’t understand the different topologies and their costs and benefits, as well as deficiencies, to make an informed decision. He asked my Systems Engineering Manager to prepare a no more than ten-page white paper that explained these topologies in a manner that he could understand and make an informed decision. My Systems Engineering Manager realized that this was an important white paper, and as my experience profile did not show any experience in networking, he assigned me to write this white paper. He did this in the hopes that I would write an inferior paper and that the Agency head would complain that the white paper was deficient, which he could then utilize the complaint as an excuse to terminate my employment for cause. Little did he know that while my experience profile did not show any network engineering, I had been involved in networking in my leadership of other MC3I proposals and programs efforts and that I had the networking knowledge to write this white paper. I also had the ability to write on technical subjects for non-technical people, which I had gained in the creation of the LTMS User Manual, and I utilized this skill and ability for other efforts that I undertook for MC3I.
I began this task by gathering unclassified information on the different network topologies, and I discovered that there was one network topology with which I was unfamiliar. I also discovered there was a network engineer in our Systems Engineering group who was knowledgeable and experienced in this topology. I went to her cubicle the next morning to discuss this network topology with her, and she informed me that she had written an unclassified technical white paper on this network topology for another program at GE M&DSO. I asked her if she could provide me a copy of this technical white paper, and she replied that this was possible, but would require an hour’s worth of her time to go to the building where the white paper was stored and locate it, then copy it and return the copy to me. I told her that this would not be a problem, as I had a time charge number for the activities of writing the white paper, and she could utilize this time charge number to obtain a copy of her white paper. She promised that she would do so that afternoon. Later that morning, my manager called me into her office to chastise me for not utilizing the proper bureaucratic process to assign work to another engineer.
The network engineer who agreed to provide me with a copy of her unclassified technical white paper informed her manager after our meeting that she was going to leave the building that afternoon for an hour to retrieve this white paper for me. He told her that this effort was not approved by management and she would have to await management approval until she could retrieve her white paper. Her manager then went to my manager to start this bureaucratic process. This bureaucratic process required that I ask my manager for the services of an engineer, and if she approved, she would get approval from the Systems Engineering Manager. The Systems Engineering Manager would then discuss this request for services with the engineer’s manager, and if the engineer’s manager agreed with this request, they would then task the engineer to perform this effort. While this bureaucratic process was necessary for large efforts to ensure the request was within contractual bounds and done with the proper allocation of human resources as well as proper time charge accounting, this was ridiculously time-consuming for minor tasks. At MC3I, I would have the authority to make minor task requests of engineers, and for intermediate requests for services, I would discuss the task with their manager for approval and to ensure that the request fit within contractual bounds before they tasked them. It was only for large requests for services that could have contractual and financial implications that MC3I utilized this bureaucratic process.
My manager denied my request for the retrieval of her white paper and informed me that I was the only person to work on this white paper for the head of the Government Agency. I came to believe that they only wanted one person (me) to blame when they thought that the Agency head would complain about this white paper. However, the next morning the network engineer handed me a copy of her white paper to me. She had gone to the other building before work to obtain a copy of this white paper for me without using the time charge number. She explained that she thought that this denial was ridiculous, and she provided me with this white paper on the condition that I serendipitously utilize her white paper, which I agreed to do so. A few weeks later, she resigned from GE M&DSO, which she explained to me was because she was tired of all the bureaucracy and politics of the Systems Engineering Manager.
I then wrote this white paper and had the Network Engineering Manager review my white paper to ensure that there were no flaws in the white paper, to which he had only a few minor comments about the white paper. I incorporated his comments in the white paper and handed it to my manager, who instructed me to give it to the Systems Engineering Manager. I later learned that the Systems Engineering Manager did not read my white paper but sent it directly to the Agency head. About two weeks later, he received a letter from the Agency head, and he opened it in front of the Network Engineering Manager (who told me this story) while they were in a one-on-one meeting in his office. The Systems Engineering Manager began to chuckle as he was opening the letter, and after he began to read the letter, his chuckles turned to consternation and then anger. This was a letter of commendation from the Agency head about the white paper, and he commented that it was one of the best white papers that he had ever received on a technical subject and that he felt very comfortable in making an informed decision on the network topology after reading this white paper. The Systems Engineering Manager sputtered to the Network Engineering Manager that he needed to review my white paper and make any correction to it he thought was necessary so that he could send a letter of apology and a corrected white paper to the Agency head. The Network Engineering Manager informed him that he had reviewed the white paper before I had turned it over to him, and he thought it was a very good white paper that needed no corrections. The Systems Engineering Manager then slammed the letter onto his desk in pique and began to mutter to himself angrily. After I wrote this white paper, I was again assigned to another series of small, insignificant, and very short-term assignments.
At the beginning of December, I was given a month-long assignment to write the Operational Procedure required to synchronize the internal clocks of the three Mainframe computers to be utilized by the government once the contract was completed. These three computers were geographically separate from each other across the world, and this was a difficult task in the pre-Internet age. This synchronization was even more difficult as the precision of the time had to be seven decimal places. Today, this would not impose any difficulty, but in that computer era, there was no easy solution for synchronization of that precision over long distances.
I went to the Chief Engineer to discuss the design of the clock synchronization, and he informed me that they had not yet designed this clock synchronization, as it was not considered a high priority, but they planned to do so in about two months. When I asked him how I could write an Operational Procedure for something that was not yet designed, he replied that I should just write anything, and they would modify it after they completed the design for the clock synchronization. I recognized this as another trap by the Systems Engineering Manager to find grounds for my dismissal, as he could claim incompetence on my part for writing an improper Operational Procedure that did not reflect the design of the clock synchronization. Rather than compose a fairy tale, I decided to research this problem to discover how this could be accomplished. After spending two weeks reviewing what literature I could find, I discovered that this was an unresolved issue in the computer field but that some efforts were being undertaken to solve this issue. I began to formulate some ideas of how we could design the clock synchronization, and I went back to the Chief Engineer to discuss what I had uncovered and my possible solutions to a design for the clock synchronization. After listening to what I had uncovered and my potential solutions, the Chief Engineer admitted he had no idea of the difficulties of the clock synchronization design. I offered my services to design a solution for the clock synchronization, and he paused, then looked around his cubicle to see if any people were present around his cubicle. Upon discovering that nobody was nearby, he told me that he would love for me to design a solution to this synchronization problem as he was aware of my excellent reputation for quality work, but that he had been informed by my new Systems Engineering Manager that I was not to be assigned to any important work on the contract, and he would have to find someone else for the design of the clock synchronization.
Stunned by his revelation, I went back to my cubicle to think about his revelation, and I soon realized that my career at GE M&DSO was finished. I stared at the wall clock ticking off the seconds, and after twenty minutes, at exactly 2:00 PM, I decided to leave the premises and go home. Upon my arrival home, my wife asked why I was home so early, and I explained what had happened and that I would have to resign immediately. She was understanding of my desire to resign, as she knew that my situation was having a deleterious effect on my mental health, but she reminded me that if I stayed until the new year, I was eligible for three weeks’ vacation, and we could use the pay for these three weeks after I resigned. I agreed with her and did not resign immediately, but returned to work the next day and did nothing but move my personal, non-classified possessions from my cubicle to my house the next two weeks, in small quantity by small quantity, so that no one would be suspicious of my actions.
On January 2nd, 1992, I went to my manager's office and resigned, informing her that I was taking the next three weeks off as vacation and that I would return the day after my vacation to receive my classified debriefing and sign a necessary termination paperwork that was needed. As I turned to leave her office, she asked me where the Operation Procedure documentation I was preparing was located, and I replied, “I didn’t do it.” then walked out of her office and the building. The next morning my manager called to inform me that I was not approved to take a vacation until I submitted the Operational Procedures documentation and scheduled a security debriefing. Knowing GE M&DSO vacation policy, I informed her that I did not care if I had her approval or disapproval to take a vacation, and I would not change my plans. As for the security debriefing, I told her to arrange this debriefing for the last day I was to be a GE employee, and then I ended the conversation with her by hanging up the telephone. She called back later in the day to inform me that my vacation had been approved and that the security debriefing could not be scheduled until after the day I specified in my resignation letter. I agreed to show up that day for my security debriefing and to sign the GE M&DSO employment termination paperwork.
When I showed up for my classified debriefing, which was given to me personally by a Security Office that I had worked with in the past and liked, he asked me if I had resigned or had been laid off or terminated. I informed him that I had resigned, then asked him what difference it made to my classified debriefing. He informed me that there were two different unclassified debriefings, one for the laid-off or terminated employees that were more of a threat and a warning nature, the other for employees that resigned which was more of a guidance nature, which instructed them of the precautions and legal ramifications for the revocation of security clearances. I received the resignation classified debriefing, then went to the Human Resources Department to sign my GE employment termination paperwork. I then went home unemployed, and my wife suggested that I take some additional time off to recover my mental health.
On the day I tendered my resignation, I went back to the Marketing Department to say my goodbyes to the people in marketing that I had worked with the last few years at GE M&DSO. One of my friends in the Marketing Department inquired as to the reason for my resignation, and when I informed him of the events of the last year, he suggested that I apply for unemployment compensation on the basis that it was a forced resignation. He did not know if I would be successful in obtaining unemployment compensation but that it would not hurt to apply. The day after I signed my GE employment termination paperwork, I went to my local unemployment office to apply for unemployment benefits. At the end of the week, I was informed by the unemployment office that I was eligible to receive unemployment compensation, which I collected every Friday when I reported to the unemployment office. After nine weeks of collecting unemployment compensation, I was informed that GE M&DSO was challenging my reasoning for collecting unemployment compensation.
An arbitration meeting was scheduled, which both I and my ex-manager at GE M&DSO attended to present our cases. My ex-manager made claims of incompetency on my part that led to my resignation, despite my submitting to the arbiter my unclassified performance reviews, which except for the last performance review, which was prepared by her, were graded a 4 out of 5 with many praiseworthy comments. She responded that her division had higher standards which I did not meet, despite MC3I receiving 90%+ award fees while her division had received 40% to 60% award fees, of which I informed the arbiter. My ex-manager denied these award fees (which could be considered perjury as this was a sworn legal deposition), but as I had no documentation of these award fees, he informed me that he could not consider these award fees in his decision and her perjury was therefore mute. A few days later, the arbiter decided that my resignation did not fall under the criteria of forced resignation and that my unemployment compensation would cease. A letter was sent to me informing me of this decision and asking me, but not requiring me, to return the previous unemployment compensation that I had received. Although disappointed by this decision, I ignored the request for the return of the previous unemployment compensation and went on with my life.
* * * * *
Other stories occurred during my employment at GE M&DSO, and while some of them did not relate to me directly, they are humorous enough to be related herein.
Performance Reviews
Every year, on or about the date of your security clearance, your GE M&DSO manager was required to give you a written performance review. This written performance review assigned you a grade (1 for lowest, 5 for highest) for your efforts during the previous year and unclassified comments about your efforts of the previous year and the areas for improvement in the next year. As each manager usually had about ten people reporting to them, and they were very busy, this performance review effort took some effort and time from them to write up a performance review for everyone that worked for them.
The first performance review I discussed in the Promotion section of this document, while all my other performance reviews were standard performance reviews, except for their preparation. As most of my efforts at MC3I were outside of the main contract of MC3I, my managers had little knowledge of my assignments and work efforts. I, therefore, took to writing my own performance review, which I submitted to them for their review and comments. They were thankful for this and edited my performance review as appropriate. Needless to say, I always received a very good performance review with a grade of 4 and positive comments with minimal areas of improvement.
At one of these performance reviews, my somewhat newish manager commented that it was unique that a staff member of his created their own performance review, but that I was a unique staff member. When I asked him what he meant about my being a unique staff member, he replied that I was the first staff member that he had ever managed and that he did not really know what they were doing, as I was not involved in the MC3I main contract efforts. He also commented that I was the only staff member that he had ever managed, and he was not concerned with my efforts, as he had not heard anything but good reports on my efforts. I was also the only staff member that did not often consult him about technical issues but only conferred with him when I needed assistance with procedural or bureaucratic difficulties. He commended me on my uniqueness and said he wished he had more staff members like me, as this would make his job less difficult.
Except for my first Performance Review, in which I received a grade of 5, my other Performance Reviews were graded a 4, except my last performance review under my new management after my transfer from MC3I, for which they graded me a 2. They also made unkind and untrue comments and warnings for areas of improvement, which I had never previously received in a Performance Review. I challenged this performance review, as was my right under GE M&DSO Human Resource policy. After a review of my performance at a meeting that was attended by Steve Schramm, who was my advocate, and me, as well as my new manager and the Systems Engineering Manager, along with a few of his managers that I worked with, my performance review was upgraded to a 3, and the untrue comments were excised from the performance review. This was the best I could hope for in my challenge, but this meeting exposed the enmity of my new manager and my new Systems Engineering Manager had for me. At this point, I became even more concerned about my future at GE M&DSO.
Conferences
Each year the management of MC3I would send about a dozen engineers to different weeklong conferences about issues and concerns about future technology that MC3I may need to incorporate into their contracts. Every engineer was allowed to submit a written request to attend a conference and their reasoning why it was important for them and MC3I to attend this conference. Upon learning about this opportunity to attend a conference, I began subtly inquiring of all the managers in MC3I that I had become friendly with because of my FERB efforts about what they thought were the future technologies that could impact MC3I. I then found a conference about what many of the managers were concerned about and submitted my application to attend the conference. Lo and behold, for the next three years, I was one of the engineers selected to attend a conference.
The three conferences I attended were about digital image manipulation, the future of the expansion of the ARPANET into a Public Internet, and the management of software development under the DOD 2167a MILSPEC, which MC3I was starting to see in the proposals they were receiving. My attendance at these conferences was helpful in my career at MC3I and very useful to MC3I, as they did incorporate many of these future technologies into their contracts. In the fourth year, when conference attendance applications were submitted, my manager communicated to me that I should not submit an application, as I had attended a conference the previous three years, and MC3I management wanted other engineers to have the opportunity to attend a conference. I never again submitted a conference attendance application, as I had become less of an engineer and more focused on specific issues regarding proposals and program management.
Awards and Personal Satisfaction
During my time at GE Aerospace, I received many PRIDE awards (Professional Recognition for Individual Dedication to Excellence), a General Managers award (and a bonus) for an outstanding effort, and many Personal Commendations from the customers of the programs that I worked on. All of which were a testimony to the excellence of my efforts.
Several years after I had left GE Aerospace, I was contacted by a co-worker of mine on the LTMS and TADMS efforts. He related that he had discovered through government sources that they believed that the LTMS and TADMS systems had a very positive impact on the Desert Shield and Desert Storm military actions in Iraq. They believed that the success of our efforts in these programs led to thousands of armed service personnel’s lives being saved in combat and many tens of thousands of armed service personnel avoiding injury in combat. This reduction in the number of armed service personnel casualties has provided much personal satisfaction and meaning to my life.
Lockheed-Martin Employment Recruitment
Lockheed-Martin had just won a very large, classified government contract, which GE had lost, and they needed to quickly staff up for this contract with people that already had security clearances. They, therefore, decided to try to hire away GE M&DSO personnel with security clearances, as they thought they would be available as GE M&DSO had lost this contract. They rented a large dining room at a large hotel in King of Prussia, PA, and arranged for at least two hundred meals to be served to prospective GE M&DSO employees that they hoped to lure to this dinner.
Before lunchtime on the day of the dinner, they placed a flyer on each car window in the GE M&DSO building parking lots inviting GE M&DSO personnel to attend this dinner. All that was necessary for entrance to this dinner was for the GE M&DSO person to show their unclassified color-coded security badge to receive a free dinner. That afternoon all GE M&DSO personnel received a security alert reminding us that it was illegal to show your security badge outside of a GE M&DSO building. It also did not help that Lockheed-Martin had chosen a hotel that was known to be the location of hostile foreign intelligence services espionage efforts against GE M&DSO, and security reminded us that this hotel was a no-go location for all GE M&DSO personnel.
That evening only three GE M&DSO personnel attended the dinner, all of them security officers, to make sure no GE M&DSO personnel attended this dinner. Lockheed-Martin was shocked to discover this lack of attendance until the GE M&DSO security officers informed them of the security breach in attending this dinner. Consequently, Lockheed-Martin was out of the cost of the room rental and the meals that were not served for this dinner. Lockheed-Martin was also warned by the U.S. Government security service not to try this form of employment recruitment in the future with any other classified government contractor.
GE CEO M&DSO Briefing
When Jack Welch was appointed CEO of GE, he decided to make a tour of all GE businesses to learn what they did and their future business plans. When he arrived at GE M&DSO for this briefing, they informed him of nothing of significance. When he remarked on their lack of candor, they responded that they were not permitted to discuss anything of significance due to classified security reasons. He then instructed GE M&DSO to obtain the proper security clearances for him to be briefed properly. They assured him that this could be done but that he would have to file the proper paperwork to receive the security clearances. When they showed him the paperwork required to obtain the security clearance, he was astounded by how much detail of his past life was required to obtain the security clearance.
The information required to obtain a security clearance was, at a minimum, the addresses and dates of your residences throughout your life, your educational institution's names and dates, your past employers name, location, dates, title and job description of employment, and the location, dates, and residence of any foreign travel that you had undertaken in your life. As Jack Welch had only been employed at GE in his life, he had to provide all the different locations and positions of his career at GE. Mr. Welch had also taken many foreign trips for business or pleasure purposes throughout his life. He remarked that it might not be possible to recall or obtain this information, and the GE M&DSO security department advised him to provide as much information as possible, but if any information was left out and discovered by the DOD security investigators, it could be sufficient grounds to deny him a security clearance. He agreed to try to uncover all this information, and fortunately, his employment history and business travel were in his GE personnel file, along with the residential address where he lived while at his different positions at GE. It still took him (and a personal assistant) a month to gather this information, which was submitted and processed by the DOD security investigators within another month.
One day, while playing a game of Bridge at lunch with some fellow co-workers, we heard the sound of a low-flying helicopter above the building. One of the Bridge players remarked that this was Jack Welch flying in to receive his security briefing, as he knew this because he was a personal friend of the GE security officer (they had served in the military together) that was responsible for Mr. Welch’s security clearance processing. When I left work early in the evening, I saw the helicopter taking off from a GE parking lot to transport Mr. Welch to Philadelphia International Airport. The next day at our Bridge game, our knowledgeable Bridge player informed us what had occurred with Mr. Welch the previous day. Mr. Welch was driven to the security departments SCIF to receive his two-hour security briefing and clearances, then driven to the GE M&DSO managers SCIF to get his briefing on what was currently being done at GE M&DSO and what was expected to happen in the near future at GE M&DSO. He was amazed to learn what was occurring at GE M&DSO, and he expressed satisfaction that he understood the operations of GE M&DSO. When he got up to leave this briefing, the security officer informed him that he could not leave just yet. As he no longer had a need to know the classified information, and he was not working at GE M&DSO, he would have to have his security clearances revoked and for him to be debriefed. They then drove him back to the security department's SCIF for his one-half-hour revocation and debriefing. He was then driven to his helicopter, from whence he departed GE M&DSO.
GE Aerospace President Dismissal
After Jack Welch had his briefing on the GE M&DSO classified contracts, he had a complete picture of GE Aerospace’s operations. In the previous year of GE Aerospace’s operations, they had returned a profit of 42 million dollars to GE Corporate coffers. He decided that the next year's profits should be 45 million dollars and instructed the President of GE Aerospace to achieve this goal by making GE Aerospace’s operations more efficient, as they had little control over their contract profits due to most of their contracts being Cost-Plus Award Fee contracts.
As GE was taking a beating in the stock market for their sluggish growth and criticisms of their operating efficiencies, Jack Welch was promoted to GE CEO, as he had a well-deserved reputation for turning around poor-performing GE operations. One of the (true) stories about his abilities was that he was given the responsibility to turn around a poor-performing GE operation that could possibly go bankrupt. After touring their factory, he turned to the factory manager and instructed him to reduce his inventory of parts by half in the next nine months, and then half again a year later, and continue to reduce their parts inventory until they reached 10% of their current parts inventory. He left the factory with a warning that if they did not do this, then heads would roll. This forced the Factory manager to introduce a Parts on Demand Inventory Management System, which turned around their GE operation and they became profitable. Jack Welch did nothing else about this GE operation except show up at the deadlines to inspect their inventory.
At the end of the next year, the GE Aerospace President informed Jack Welch that he had returned 44 million dollars to the GE Corporate coffers. Jack Welch informed him that he did not achieve the profit goal that he had set for him and immediately fired him. This was a wake-up call to GE Aerospace, and more specifically, GE M&DSO, as they had not met their goal by a wide margin, and they had to operate more efficiently, or their executives could face the chopping block.
Unemployed (Jan 1992 - Feb 1992)
After leaving GE Aerospace, my wife and I agreed that I needed some downtime to restore my mental health. I, therefore, decided to take the next two months off and spend time with my wife and daughter and not think about employment.
Pet Sitting (Mar 1992 - May 1994)
Background
A co-worker and friend of mine, Bob, left GE Aerospace because he did not have a computer degree and he decided to exit the computer profession. He decided to set up a Pet Sitting business in the Main Line Philadelphia suburb, where he lived, as a Franchisee of the Critter Care Franchisor. When he discovered that I had left GE Aerospace and was taking a break, he telephoned me to see if I wanted to work for him as a Pet Sitter. He explained the job and that it was very therapeutic for him being a Pet Sitter. Being a pet lover, I agreed to try it out, as I also needed the therapy.
Critter Care
Critter Care was established to provide pet-sitting services to busy professionals and businesspersons who often worked long hours or were on business trips or vacations. We would show up at their home’s mornings, afternoons, and evenings to feed and provide fifteen minutes of attention as was needed by our customers. It was normal for the pet sitter to have half a dozen or more visits to different customers in the mornings, afternoons, and evenings. I was responsible for most of the morning visits, while Bob was responsible for most of the evening visits, and we both shared responsibility for the afternoon visits, as the afternoon visits were a large percentage of our visits. We also worked weekends as required. Usually, there were no problems, but several incidents occurred that are worth reciting in this book.
One of the Critter Care customers was a well-respected, well-known, and high-priced lawyer in Philadelphia who owned a prized Irish Wolfhound dog. He hired us to visit his dog in the afternoon while he and his wife were working, which Bob did. That summer, he and his wife decided to take a three-week vacation to Europe, and they hired Critter Care to take care of his dog while they were away on vacation. I took care of the dog in the morning, and Bob took care of the dog in the afternoon and evening. The first morning that I took care of the dog, Bob and I met at the home of the customer so that he could explain the security system of the house and the care that the Irish Wolfhound required. Irish Wolfhounds are notoriously skittish when meeting new people, and they do not react well to strangers by hiding and quivering. After the dog and I were introduced, and I took care of him, we became good friends, and he was always welcoming of me when I came to take care of him in the morning.
One day, in the middle of the customer's vacation, Bob went to this Irish Wolfhound house to take care of him. The dog was lying in a corner and quivering, which was very unusual for him as he excitedly greeted Bob when he came to take care of him. Bob immediately knew something was wrong, and he used the wall phone next to the side door, which we always used to enter the house, to call the police and report that he thought that a stranger was in the house. The police directed him to immediately proceed to the street and wait for a patrol car to arrive. When the patrol car arrived within a few minutes, they directed him to remain on the street. Bob informed them that there was a prized and much-loved Irish Wolfhound in the house that he wished to extricate before they took any action. The two police officers agreed to let him follow them into the house to remove the dog before they did a house search. Bob, without incident, removed the dog to the street and waited for the police officers to do a house search.
A few minutes later, the police officers laughingly exited the house and informed Bob of what they had found. The police officers discovered the son-in-law in one of the bedrooms in bed with his girlfriend, engaging in passionate lovemaking with the girlfriend. The police officers directed the two of them to get dressed and leave the house and never return. After they did so, Bob took extra time to soothe the dog, then took care of him. Bob also knew that he had to telephone the owner of the dog to inform him of what had happened. The customer had left the dates and telephone numbers of the hotels they were staying at, with instructions to call them at any time if any problems were encountered in taking care of their dog. He did so, and the customer profusely thanked him for his actions and for taking good care of this dog (he also tipped him a large amount when he returned from his vacation). The customer also informed him that they were suspicious of the possible infidelity of their son-in-law, and the police report of this incident would go a long way in the divorce that their daughter was going to file as proof of her husband’s infidelity.
One of the Critter Care customers was a Maine Coon Cat breeder. The cat kennels were in the basement of her home, which Bob visited every afternoon to care for the four female breeder cats that she owned. One week she decided to go on vacation, and she had Critter Care come in the morning, afternoon, and evening to take care of the cats. I was responsible for the morning and afternoon visits, and Bob did the evening visits. One of the breeder cats was pregnant but was not due for delivery until the week after the owner came back from vacation. Unfortunately, during the middle of the week, the pregnant cat gave birth to a litter of six kittens which Bob discovered on his evening visit. Bob telephoned the owner at the vacation retreat she was staying at and informed her of this birthing. She provided additional instructions to Bob on the care of the newborn kittens. He decided that he would be responsible for all the visits to properly take care of the kittens per her instructions. One day after the birthing, one of the kittens died, and it seemed to Bob that the mother was not properly caring for the kittens. He again called the owner to inform her of this situation, and she responded with additional instructions for the care of the kittens. She also informed Bob that as this was the mother cats first litter and often the first birthing, the mother cat did not know how to properly take care of the kittens. The next day Bob discovered that two more of the kittens had died, and the following day the other three kittens had died; thus, the entire litter was lost, and Bob telephoned the owner to inform her of the deaths. Upon the owner returning from vacation, she had the last kitten that died examined by her vet, who discovered that the kitten had died from a bacterial infection, and it was most likely that the other kittens had died from this bacterial infection. This was not uncommon for cat breeders to have this problem, which required the cat breeder to fumigate and sterilize the kennel to ensure that this bacterial infection would not spread to the other cats and any kittens that were birthed. She informed Bob of this and assured him that he bore no responsibility for the deaths, and she fumigated and sterilized her kennel to prevent future problems.
One of the Critter Care customers had Bob visit his dog every weekday afternoon. This dog was kept chained in the basement during the day so that he could not reach the shelving around the perimeter of the basement. Bob did not care for the way this dog was being housed during the day but made no mention of it to the owner. One day Bob visited this dog and discovered that the dog had become entangled in the chain and choked himself to death. Upon telephoning and informing the owner of what he discovered, the owner was not upset by the dog’s death. Indeed, Bob was more upset by the dog’s death than the owner, as he very much liked the dog and felt sorry for the way the dog was housed during the day. Bob resolved that he would begin to inform his customers of any potentially dangerous situation he encountered when he undertook a new customer or observed any situation in which he felt that the pet was being mistreated.
One of the Critter Care customers hired us to take care of his dog while he was on vacation. On the introductory visit, which Bob always did before taking care of any pet, he recorded all the information about the proper care for the pet that the owner desired. He also recorded any special household instructions that we would need to know to properly take care of the pet. One of the things that Bob meticulously recorded was the instructions for any security system that was installed at the residences of the pet. Upon my initial visit, while entering the house to take care of his dog, an alarm sounded. I looked at the recorded instructions, and there was nothing mentioned about the security system. I called Bob to ask if he had any instructions for the security system, and he informed me that, as far as he knew, there was no security system installed at the house. He had the telephone number of where the owner was staying during his vacation, and he would telephone the owner to find out about the security system. In the meantime, the security alarm was blaring, the dog was frightened, and a few minutes later, the local police showed up with guns drawn to determine what was happening. The police were highly suspicious of my presence in the house, and I informed them why I was in the house. I again telephoned Bob to see if he was able to contact the owner to get the security system information. He had succeeded in getting the security system information and gave me the code to shut off the alarm. After I did so, the police officers dropped their suspicions and warned me about getting this security system information before I entered any residence. When I next met with Bob, he informed me that there was no security system installed at the time of his initial visit, but the owner decided to install a security system before he went on vacation and did not think to telephone Bob to provide the instructions to unarm and rearm the security system before and after our visits.
In the early autumn, on a cold and rainy day, I was driving down a steep hilly, curvy road to return to the Critter Care office (Bob’s apartment). My car began to slip on the road, and I lost control of the car and slammed into a big roadside tree. My car was significantly damaged by this collision, and Bob had to rescue me and help arrange for my car to be towed to a repair shop. It cost me five hundred dollars of the deductible on my auto insurance to repair my car, as well as the daily fee of twenty-five dollars to rent a car while my car was being repaired, for a total out-of-pocket expense of six hundred dollars. I decided that as the Main Line had many steep hilly, curvy roads, I did not want to continue Pet Sitting on the Main Line during the bad weather of autumn and winter. I also decided, as it was a forty-five-minute commute from my house to and from the Main Line, that it was time to start my own Pet Sitting business around where I lived, where there were not many steep hilly, curvy roads. I discussed this with Bob, and he agreed to help me setup up a Pet Sitting business around where I lived.
Duchess Pet Services
I had originally considered establishing a Critter Care franchisee in my suburban region. After discussing this with the franchisor and learning about the fees and services they provided (mostly instructions on proper pet-sitting procedures), I realized that I already knew much of what they would provide me, and the fees they charged were inordinate for the services they provided. I, therefore, decided to set up my own Pet Sitting company—Duchess Pet Service (named after my recently departed dog). Bob thought that this was for the best, as he, too, thought the annual fees that they charged him were inordinate for the services they provided. Bob also volunteered to help me in the establishment of the business by providing advice on any questions I may have. For the next year and a half, I ran a successful Pet Sitting business without any incidents but a few humorous stories.
One of my first customers was a successful businesswoman who owned seven dogs which she housed in a large barn on her property. She explained that she had rescued one of the dogs who was roaming a highway that she was traveling on. After bringing the dog home and visiting a vet, she discovered that the female dog was pregnant. After the dog gave birth to six puppies, and she helped the mother nurture them, she did not have the heart to give them up. She decided to convert the unused barn into a living space for all the dogs. All the dogs were very friendly, but they were not housebroken nor trained. She wanted me to visit the barn daily to feed the dogs, clean up their messes, and give each dog a short walk around her property. I agreed to do so, but after the first week of taking care of these dogs, I discovered that it took an hour per day to take care of them and much physical effort to clean up their messes in the barn. I realized this was unsustainable at my current rate and time allotted per visit. I discussed this problem with the owner, and she agreed to double my rate per visit to take care of her dogs, and I did so for the entire time I was a Pet Sitter.
Another customer owned two big rottweilers that required special care when I visited them. He hired me to take care of the rottweilers three times a day while he and his family were on a two-week vacation. These rottweilers were also very protective of the family, and on my introductory visit, the owner instructed me to knock on the door, wait a few moments while he leashed and tied up the dogs, then he would escort me to each dog individually to introduce us in a manner that the dogs understood that I was friendly, after which he would release the two rottweilers onto the high slot less wooden fenced in the back yard where I would spend ten minutes playing with them to forge a bond with them. He also informed me that the rottweilers would have free access to the fenced-in backyard via a dog door while he and his family were on vacation, as they both were housebroken and knew to use the dog door when they needed to relieve themselves. He also requested that I clean up their backyard messes, with a scooper tool which he provided, on the two Saturdays that I took care of them. The introductory visit when off without a hitch, and there were no problems with their bonding with me. The owner also instructed me to only enter through the front door and announce myself before entering the house. He explained that if I did anything other than what he instructed, the rottweilers would ferociously bark and growl at me.
I discovered the truth of the entrance instructions when on one of my visits, I noticed a neighbor's blown trash can against his fence. I went over to retrieve the trash can, and the two rottweilers started to ferociously bark and growl at me despite my talking to them through the fence. I went back to my car for five minutes hoping the rottweilers would calm down, which they did, and I entered the house as instructed, where the rottweilers greeted me warmly. On my visits with the rottweilers, after I fed them, I would sit on the back deck and watch them play for about ten minutes. One of the rottweilers noticed me sitting on the deck and ran over to me, and plopped himself on my lap like he was a lap dog. The other rottweiler noticed this and ran over to me, nudging the other rottweiler off my lap, whereupon he plopped himself on my lap like he was a lap dog. They took turns doing this until I left the premises. This lapdog routine became a regular routine whenever I visited them.
Another customer had a large Great Dane that she hired me to take care of three times a day while she and her family were on a week’s vacation. During my introductory visit, as I sat down to write the instructions on the kitchen table, the Great Dane placed his front legs on my shoulders and looked down intently at what I was writing. I would occasionally tell him that I was getting it all written down, and he would lick my cheek once and continue to look down intently at what I was writing. Whenever I visited him, he was very happy and excited to see me, and my visits with him were a pleasure.
When I informed Bob that I was shutting down the Pet Sitting business to start a computer consulting business, he confessed that he had the same doubts as I was having as to the long-term viability of being a Pet Sitter for the rest of his life. He was in the process of turning over the Critter Care franchise to his son, who also was a Pet Sitter for his Critter Care business, to restart his computer career. We decided it would be a good idea if we went into the computer consulting business together, where he would primarily be responsible for Sales and Marketing, and I would be responsible for the technical services to the customer, but we would help each other out as the need arose. Unfortunately, shortly after we agreed to this, he became involved in a bitter divorce with his soon-to-be second ex-wife. After the divorce was finalized, he decided to move to Texas, where a long-time friend of his lived, to get away from both of his ex-wives, where he restarted his computer career. Thus ended the partnership, and I was left alone to fend for myself in my new business.
* * * * *
After my experiences at PSFS, INA/CIGNA, GE Aerospace, and Pet Sitting, I believed that I had become a fully mature adult. While I had more to learn, my character was established (but not set in stone), and I became satisfied with my character.
Independent Computer Consulting (Jun 1994 – Dec 2019)
Background
As an independent computer consultant, I was not only involved in the technical aspect of my client’s computers, but I also provided guidance and assistance in the implementation and training of computers in the operation of their business. As computers in the operation of small businesses were fairly recent, this assistance was vital for the health and continued operation of their business. I forged and maintained a personal relationship with the owners and employees of these clients, and I still maintained contact but engaged in no work with some of my clients after I retired. Knowing that I made a difference for these clients has provided more meaning to my life.
I began by providing services for Apple Macintosh computers, which I was familiar with, but I soon realized that there were many more opportunities for providing services for Microsoft Windows computers. I, therefore, purchased a Windows computer and became knowledgeable about the Microsoft Windows operating system. As the Internet was just exploding upon the scene, I also decided to learn how to create web pages for my clients.
I developed cardinal rules before I became a computer consultant for a business, as these cardinal rules were critical for the health and safety of their computers. These cardinal rules were:
- Thou shall have Backups and recoveries for all the computers; in the event of any problems with a computer, the backup could be utilized to recover a computer or any of the data stored on the computer.
- Thou shall have an Uninterruptible Power Supply (UPS) for all computers to protect the computer from electrical power surges, brownouts, and blackouts that are common to electrical power supplies.
- Thou shall have Security software installed on all computers, and this security software shall be kept up to date, along with any operating systems updates from Microsoft or Apple.
These cardinal rules were often violated by my new clients, and often the first thing I did for my clients was to correct this situation.
I also emphasized to my prospective clients that I was not only a computer technician but an excellent Business Process Automation person that could assist them in integrating their computers into their business operations. As part of my integration efforts, I could provide training to their personnel in the usage of their computers and the software installed on their computers. After explaining the reasons for my cardinal rules, and my services as a Business Process Automation person and Computer Software Trainer, they often expressed gratification that I could do all of this for their company as their computers and company personnel were lacking in these capabilities. I also provided instructions for the correct ergonomic seating in front of a computer to lessen the aches and pains of improper seating. As a result of my efforts, my clients often became close friends, and our relationship was not only professional but personal.
I also provided my clients with computer problem advice in the event their computers were behaving strangely. This advice was:
- Save any work in progress and quit all software applications that were active.
- Shut down the computer for one minute.
- Power on the computer and wait ten minutes before doing anything other than a logon.
- Determine if the problem reoccurred, and if it does not reoccur, then ignore the problem. If the problem reoccurs, then call me for advice.
This is good advice as the first step in solving computer problems, as most often, the computer problem will not recur after doing these steps. I informed them that if they did not do this, then I would insist that they do this before I provided any services. After a few times when they did not do this, they learned that I was true to my word and that this had to be done before I provided my services.
I also install about a half dozen utility programs on their computers that I would utilize to maintain their computers and diagnose computer problems. I would also alert my clients to the current e-mail scams and common malicious malware that were circulating on the Internet, which were significant and widespread enough that they should be concerned so that they could avoid these scams and malware. I also instructed them never to click on a hyperlink in an e-mail unless they were certain of the origin of the -email. Even then, they should be careful and validate the hyperlink address by hovering their mouse pointer over the hyperlink and waiting for a second for a pop-up to display the web address of the hyperlink. If they did not recognize the web address, then the e-mail was probably a scam or malware. Many of my clients informed me that by using these precautions, they were able to avoid scams and malware that they initially thought were valid e-mails. They also informed me that this procedure calmed their initial fears invoked by a suspicious e-mail.
When cell phone usage in business became more commonplace, I expanded my business to also support cell phones in the business operations of my clients. E-mail, Voicemail, Text Messaging, Contact, and Calendaring, as well as photos, needed to be integrated into the business operations, as well as connecting the cell phones to their computer network for integrating these items in their business operations and for cell phone backup and recovery purposes.
Most of my clients I retained for many years, and sometimes decades, during which I would replace their aging computers and computer equipment with new computers and computer equipment, as well as expand their computers and computer equipment as needed. I also incorporated new software and technologies into their business operations, especially in integrating the Internet into their business operations.
When networking my clients’ computers, there were two means to accomplish this networking: Peer-To-Peer or Client-Server networking. Peer-To-Peer networking was rather simple, as each computer was independent of the other computers on the network but shared common data. This was usually done by having a shared folder on one of their computers or there having a dedicated file-sharing computer that was not utilized for anything other than file sharing. A Client-Server network was more complicated, as one computer was a server computer that was the file-sharing computer and managed and controlled the other client computers. There are many advantages and disadvantages for each type of network, the largest being cost and complexity. For small computer networks, the cost and complexity of Peer-To-Peer networking were low, while larger computer networks needed a Client-Server network whose cost and complexity were high. Peer-To-Peer networking could easily be implemented and required little administration, while Client-Server networking was complex to implement and required regular administration by a highly knowledgeable and skilled Computer Network Administrator. Most Client-Server networks had an in-house Computer Network Administrator(s) to manage their network, or they subcontracted to a computer consulting firm to provide Computer Network Administration on an as-needed basis. I did not have much Client-Server knowledge or any experience in Network Administration, nor did I wish to be a Network Administration, as I was primarily interested in integrating the computer into the business operations of a company (which Network Administrators almost never did).
Whenever my services were required for a Client-Server network, I immediately contacted the Network Administrator and worked with them to ensure that my efforts would integrate into their Client-Server network with minimal impacts. I did, however, implement many Peer-To-Peer networks for my business clients that needed networking capabilities. One of my clients, AIA-ISSI, eventually outgrew the Peer-To-Peer network that I had implemented for them, and they asked me to implement a simple Client-Server network with a newer simplified Small Business Server technology being offered by Microsoft. I did this for them, and this was my only experience in implementing and managing a Client-Server network.
In the first few years of my computer consulting business, I also created websites for my clients. These websites were what I referred to as brochure websites. I would take their marketing and sales printed brochures and create web pages of these brochures. These were simple and functional websites that presented a polished appearance for their business. However, as website design became more elaborate and interactive, often requiring a team of website designers, I stopped doing this as it was beyond my skills and capabilities to create such websites, not to mention that they took a considerable amount of time to create, which I could ill-afford given my computer support responsibilities for my clients.
The services I provided were at an affordable rate for these businesses, and I only raised my rate at the end of six years of my computer consulting business. I was about to raise my rate again when the economic downturn of 2007 hit the American economy. I decided to postpone this rate increase until the economy became better, which did not occur until eight years later. By the time the economy recovered, I had lost several of my larger clients, and I was contemplating possible retirement in a few years, and I did not increase my rate for concern for my own and my client’s economic well-being. While I did not earn a lot of money in my computer consulting business, I was able to pay my home and business bills with the money I made, with a little left over for personal use.
During the first year of my computer consulting business, I was not very busy, and I became involved in three activities for The Lower Moreland Township School District, The Huntingdon Valley Library, and Pennsbury Manor on a volunteer basis. A volunteer effort that eventually paid dividends for my business.
The Lower Moreland Township School District
I had become involved with the Lower Moreland Township School District and their Superintendent in a dispute over closing the elementary school due to declining enrollment. During my involvement, the Assistant Superintendent informed me that they had just installed a computer lab in all three schools, with the Elementary and Middle schools being Macintosh computer labs, while the High school lab was Windows computers. However, most of their teachers had no knowledge or experience of how to utilize these computers. I informed him that I had training material for the instruction of Macintosh and Windows computers, along with the instruction on Microsoft Word and Excel software. We soon agreed that they would hire me to provide this training to selected teachers on a paid basis. After completing this training, they suggested that these courses should be given as an Adult Evening School course, which I agreed to. They also asked if I would lead a Computer Club that they were forming at the high school that was to be held from 2:30 PM to 4:00 PM twice a week. I volunteered to do this until my business picked up, and I was able to do this for a year until my business appointments would no longer allow any time for the computer club.
The Huntingdon Valley Library
During the dispute with the Lower Moreland Township School District, I met a woman that was having some problems with her home computer, which I agreed to correct. After I fixed her problems, she mentioned that she had several other friends with computer problems that needed help with their home computers. She put me in contact with them, and I was able to assist them. I then decided that I would expand my computer consulting to help people with their personal home computers, but only on the basis of non-interference with my business clients. I also had the pleasure of meeting and greeting their dogs and cats when I visited their homes, and all but one dog was very friendly, and the unfriendly dog was very protective of my client and had to be locked up when I visited their home.
She also mentioned that she was on the board of the Friends of the Huntingdon Valley Library volunteer association and that they had just posted a web page about the Huntingdon Valley Library. They were dissatisfied with this webpage, as it was created by a high school student of one of the board members who had no interest in improving the website, and they wished to improve their website. I volunteered to improve their website, as it would be a good experience for me and a showcase for prospective clients of my website creation capabilities. After the completion of this website, during which I became friends with the Library Director and all the librarians, the Library Director mentioned to me that the library was about to purchase four computers and a wireless Internet connection for their patron's usage while at the library, which would eventually expand to ten computers. She also mentioned that they were having difficulties with the six computers that the library staff utilized. She, therefore, wanted to procure my services for all the computers at the library, and I became their computer consultant for the next half dozen years. As the utilization of computers and the Internet became more widespread in all the libraries of Montgomery County, PA, the libraries formed a consortium of all the libraries to provide computer and internet support, as well as a centralized catalog of the library’s collections, and they contracted a medium-sized computer consulting firm to provide these services to all the libraries in Montgomery County.
Pennsbury Manor
During the first summer of my computer consulting business, my young daughter became interested in historical herbalism, and she was excited to discover that Pennsbury Manor, the colonial estate of William Penn, founder, and proprietor of the Colony of Pennsylvania, maintained a historic garden of herbal medicinal plants. We visited Pennsbury Manor during the week and encountered the head gardener, with whom my daughter had a two-hour discussion about historic herbal medicines. Normally, my daughter was too young to become a volunteer at Pennsbury Manor, but the head gardener, who was impressed by my daughter’s knowledge, arranged with the Site Director for my daughter to assist her two mornings a week (under her direct tutelage). On one of my chauffeur's duties, I engaged in a conversation with the President of the volunteer association, and when she discovered that I created websites, she asked if I would be interested in volunteering to create a website for Pennsbury Manor. As Pennsbury Manor had many visitor brochures, which I had looked over, I replied that I would do so based on these brochures. For the next few months, I worked on this website as my time allowed, and when I completed this effort and previewed it to the volunteer association and the Site Director and his assistants were very pleased with this website. The Site Director proudly displayed this website to other Pennsylvania historical sites, and when he displayed this website to the Pennsylvania Historical and Museum Commission at their annual meeting, they decided to start the development of websites for all the historical sites in Pennsylvania. This website remained active until four years later when it was replaced by the website developed under the auspices of the Pennsylvania Historical and Museum Commission. This website was also a showcase of my website creation capabilities for prospective clients.
Sabre Systems
About a year and a half after I started my computer consulting business, I was contacted by Sabre Systems about subcontracting to them for a new line of business that they had just started. Sabre Systems was a medium-sized computer services business that had several U.S. Navy government contracts with the Naval Support Activity in Northeast Philadelphia, PA, and in support for the United States Navy’s JTIDS and TACAMO Program for what is now known as NAWCAD.
Sabre Systems Corporate headquarters is based in Warminster, PA, and they wanted to branch out into commercial computer services around this location. They had decided to do this by offering computer network administration services and becoming a Value-Added Reseller (VAR) for the Goldmine (GM) Contact Relationship Management (CRM) Microsoft Windows computer application. CRM computer applications allow a company to computerize all contacts (both customers and vendors) by storing information in a DBMS about the contact and any information about the calendar activities, telephone conversations, documents, faxes, and e-mail correspondence that they had with the contact. GM CRM was very customizable in the information it stored and very adaptable to the business operations of a company. Sabre Systems had the technical expertise to install and configure GM CRM on a networked computer system, but they required assistance in customizing the GM CRM to the business operations of their GM CRM customers. This computer application customization for the business operations of a company was an expertise that I had, and even though I did not have any GM knowledge or experience, they wished for me to provide my expertise to their clients.
After accepting their offer to subcontract to Sabre Systems on a part-time basis, the Sabre Systems Network Administrator taught me what he knew about the installation and configuration of GM on a network computer system. He also gave me a brief introduction to GM, and I spent the next few weeks at Sabre Systems (on a part-time basis) learning GM and its customization capability by reviewing the GM User Manual and the GM Administrators Manual while experimenting on a test GM system on one of their Microsoft Windows computers.
As GM was developed a decade before the Internet, it had a somewhat unique computer software technology built into it—GoldSync. GoldSync allowed for multiple Goldmine installations to be created at different geolocations, and GoldSync could be used to synchronize the GM databases between the locations by means of a telephone line via computer modems at each GM installation. With the rise of the Internet, GoldSync became obsolete, as Internet communications technology made multiple GM databases unnecessary. Sabre Systems had one client who utilized this capability, as they had their main GM located in Montgomery County, PA, and two other locations somewhere in the Midwest and the Pacific Coast. As I would be supporting them, it was necessary for me to learn GoldSync.
After I finished learning GM, I took the GM Certified Technicians test to become a credentialed GM value-added reseller technician. A test that I passed with ease and almost with a perfect score. As part of my agreement with Sabre Systems, I would be allowed to incorporate GM support into my computer consulting business for my clients that were too small for Sabre Systems' interest and could not afford Sabre Systems services, as they charged three times my computer consulting business rate for their services. The only caveat was that I had to purchase GM through them, as they would get commissions and credit for the sale of GM from the GM vendor. This was a caveat that I put to good use, as I had several small business clients that had a need for CRM in their business operations.
For the next three years, I provided GM support for Sabre Systems GM clients, which increasingly took more of my time as their GM business grew. At the end of this time, Sabre Systems re-evaluated its commercial computer services business and decided to exit the commercial business, as its return on investment was low, and its Naval contracts had rapidly grown. The Network Administrator, Max, decided to take a severance package from Sabre Systems and leave the company while I was released from my subcontract. When Sabre Systems ended its commercial business, they allowed me to retain the contact information of their GM clients to solicit their business for GM support through my computer consulting business. Several of these clients contacted me directly when they learned of Sabre Systems' exit from the commercial business sector, and I immediately started supporting their GM needs.
In thinking about the other Sabre Systems GM clients, I realized that I could not provide proper support for them, as I would have to expand my business by becoming a GM VAR and hiring employees to provide the proper and sufficient support for them. Becoming a GM VAR required a significant fee and yearly sales quotas for GM, which I could ill afford, and which would require much of my time in the sale of GM. Instead, I looked for another GM VAR that I could team up with where they would provide the sales, and I would provide the support for GM. I found a GM VAR that wished to team up with me, as he was much more sales oriented and not much of a GM technician (he only knew the basics of GM customization and very little of GM problem resolution). I shared the Sabre Systems GM client's contact information with him so that he could solicit their GM business, from which he did garner some new GM clients. After a year of working with him, I realized that I was providing little technical support for his GM clients and only providing technical support when GM problems arose at his client’s operations. I telephoned a few of his clients that he had obtained from Sabre Systems and discovered that he was doing the minor customizations himself and that these clients were dissatisfied with his performance. Some of them had even found another GM VAR for their business. When I confronted him about this, he could not deny it, as he stated that he needed the income for himself. I terminated our relationship on the spot and went about growing my own computer consulting business with only GM support incorporated into my business. This was possible as the Goldmine vendor changed its sales policy to allow direct GM sales to companies with no customizations by the GM vendor, which fit well into my business model.
While working at Sabre Systems, their GM client who utilized GoldSync reported a problem that their GoldSync did not seem to be syncing properly. I was tasked to investigate and correct this problem which turned out to be a significant GoldSync problem. In analyzing the GoldSync data stream, I noticed some anomalies that I could not explain. Doing a deeper analysis, I was able to pinpoint the source of these anomalies, which was located in the functioning of the GoldSync process. When I telephoned GM VAR technical support to discuss these anomalies, the technician on the other end of the telephone line admitted she did not understand the technical details of what I had uncovered, and she transferred my call to the GoldSync development team to explain this problem. After I explained to the GoldSync development team what I had uncovered, they said they would immediately look into this problem and get back to me ASAP. The next morning, I received a telephone call from the GoldSync development team informing me that I had uncovered a problem with GoldSync that had gone unnoticed for quite some time. They were in the process of preparing a patch to correct this problem, and they requested that I apply this patch as soon as it was complete and retry the GoldSync to determine if the patch corrected the problem. I agreed to do so, and the next day I had the patch, which I promptly installed and tested, which revealed that the problem was fixed. When I called the GoldSync development team to inform them of my successful effort, they were very grateful that I had uncovered this problem, and they mentioned that this was the first time that a GM VAR GoldSync technician had been able to diagnose a GoldSync problem.
Another time, while I was at Sabre Systems headquarters, the President of Sabre Systems walked into the commercial business support office early one morning and informed us that his laptop would not start up and asked if one of us could help him with this problem. As I had the available time to do this, I went to his office to examine his laptop. Upon opening and closing the lid of the laptop, I noticed that it was very cold. He sheepishly admitted that he had forgotten to take the laptop out of his car the previous evening, and as it was a very cold winter night, his laptop became very cold. I explained to him that this was a problem with any computer that became very cold or very warm, as these temperature extremes interfered with the operation of the computer. I informed him that we would have to wait for at least an hour for the laptop to warm up but that he may have damaged the computer, especially the disk drive, by trying to power the computer up outside of the operating temperature boundaries. I also informed him that if the disk drive was damaged, we could restore it from the backup to a new disk drive that I could install. He again sheepishly admitted that he had not allowed the automated backup to run the last two weeks, as it was interfering with the work he needed to do on the laptop. I informed him that this could be a serious problem as if the disk drive was damaged, I could only restore it to the state of the last backup, and he would lose all of the data on his laptop that he had created or modified since the last backup. The next day Sabre Systems issued a new corporate policy that all laptops had to have a successful backup when they returned to the office with their laptop. An hour later, I went back to his office and felt the laptop, which was cool but not cold, and we powered up the laptop. Much to his relief, it powered up, and after a quick check of the health of the laptop, I determined that it was functioning properly and that no data had been lost.
One particularly noteworthy story was Physicians Endoscopy L.L.C., which contracted with Sabre Systems to install, configure, and customize Goldmine for its business operations. Physicians Endoscopy purchased expensive medical imaging equipment and then leased the equipment to health service providers. On paper, this was a very profitable and growing business that many people invested in. However, unbeknownst to its investors, Physicians Endoscopy had created a dummy corporation to which they transferred their losses to hide the fact that they were unprofitable. When this was discovered, the Federal government prosecuted and convicted several of their executives, and they spent many years in prison for this fraud, and Physicians Endoscopy went out of business. The person I worked with most closely at Physicians Endoscopy left the company before they went under and became the General Manager of a small legitimate healthcare services company, where he hired my business to install, configure, and customize Goldmine CRM for his new company.
Another particularly noteworthy story was Numoda, a company that developed customized software for business clients to run on Blackberry Personal Digital Assistants (PDAs) cell phones. Numoda contracted Sabre Systems to install, configure, and customize Goldmine CRM for their business, which I did. They then refused to pay for my services, as they claimed the work was unsatisfactory despite their signing off on a work order that stated all work was complete and satisfactory. Sabre Systems filed a lawsuit against Numoda to recover their costs, and I had to testify in small claims court in this lawsuit. Sabre Systems also discovered that Numoda used this same tactic to not pay for the services of other subcontractors. After testimony was complete, during which the Judge often ruled against Numoda’s legal motions and evidence submission, he ordered Numoda to pay Sabre Systems the full amount that they were due. As Numoda was teetering on bankruptcy, they did not have the monies to pay Sabre Systems, and instead, they decided to transfer some of their office furniture to Sabre Systems in lieu of payment.
Sutton Advertising
After I had completed the first training for the Lower Moreland Township School District, one of the teachers came up to me and introduced herself. She informed me that her brother, Russ Sutton, owned a small advertising agency that had just had three Macintosh computers installed at his company and that he was having some difficulties. She suggested I telephone him to determine if I could be of any assistance and that she had informed him to expect my call.
Sutton Advertising Agency was a full-service agency located nearby, whose primary clientele were real estate agencies for which he created their newspaper advertisements. Upon meeting Russ and his staff of two graphic artists, it was quickly determined that I could be of assistance to his business. All of us also liked each other, and we immediately formed a friendship bond.
After discussing the business management needs of Russ’s Macintosh computer, I sat down with the graphic artists to discuss the needs of their Macintosh computers. They explained that they had attended a three-day training course on how to utilize Adobe Photoshop to create the advertisements, but they had very little other Macintosh instruction. In discussing this with them, I asked how often they turned off or restarted their computers, and they replied that they never turned off or restarted their computers, as nobody had ever shown them how to do this, and they were even unaware of the power on/off button on their computers. I immediately knew that I would have to provide my Macintosh training to all, including Russ, as he also did not know how to turn off or restart his Macintosh computer. This training was provided on the afternoons of the following week, and they were amazed about how much their Macintosh computers could do for them that they had not known could be done.
I also created a simple website for his business, in conjunction with Russ, so that he could understand website development. He decided to refer my website development services to anyone he knew that needed a website. Although I did develop a few simple websites, his referrals did not amount to much new business for me.
I also immediately fixed the three cardinal rules that they were violating. For the next fifteen years, I provided my computer consulting services to Sutton Advertising until they went out of business. The advertising industry was going through a revolutionary change from print to webpage advertising, which needed a different skill set that Sutton Advertising could not provide. With the decline of print advertising and newspaper circulation, the revenues of Sutton Advertising also declined. While Sutton Advertising made an attempt to create webpage advertising, Russ soon determined that his agency did not have the skills and abilities to create webpages and that most of his large clients started to subcontract their webpage advertising to independent website developers.
While providing the training to Sutton Advertising, I also met their part-time bookkeeper, Marion Demcisak, who mentioned that she had another part-time client that needed computer assistance. She arranged for me to meet with the President of Huston Clay Products to discuss my services and how I could be of assistance in computerizing his business operations.
Huston Clay Products
Huston Clay Products was a leader in the marketing, distribution, and servicing of architectural masonry products in eastern Pennsylvania, southern New Jersey, and Delaware. They also oversaw the construction of major masonry projects for which they were the supplier of masonry products. Their office was an old house in Willow Grove, PA which had been converted to an office building by Huston Clay Products. Their office had six computers and four persons: President Tom Huston, a salesman and construction engineer Mike, the business operations manager Doris, and a self-anointed Chief Financial Officer Fred. They had the computers installed in a peer-to-peer network by another computer consultant a year before I arrived for an interview. As they were dissatisfied with their current computer consultant, Marion Demcisak suggested that they interview me as a replacement computer consultant.
After a forty-minute interview, Tom decided to contract my services, and he gave me a brief tour of the office to meet and greet the company personnel and examine his computers. When we arrived at the fully functional kitchen, which was never used as a kitchen, he pointed out the file server computer, which was on a shelf located across the room from the sink and stove. Looking above this computer, I noticed that it was almost directly below a fire sprinkler nozzle for an automated fire suppressor system that was installed throughout the building. I immediately pointed this out to Tom and remarked that this was not a good situation, as any fire alarm or false fire alarm would activate the fire sprinkler system, which would douse and destroy the file server computer. He agreed to move the sprinkler nozzle above the stove and install a cone around the nozzle that would direct the water downward and hopefully away from the file server computer. I also discovered that all the computers violated my three cardinal rules, and Tom agreed that I should fix these problems ASAP.
I learned that Tom and Mike were rarely in the office, but Doris and Fred were there during business hours and that I would primarily be working with Doris and Fred. I also learned that all the personnel were practicing Christians that attended the same church. They never proselytized nor spoke of their religious beliefs, and they were both very friendly, cheerful, and intelligent people. Tom also had a home-office computer, located some distance from the office, which I would also be responsible for maintaining. All Huston Clay Products personnel were fairly proficient in utilizing their computers, but I was able to provide them with assistance in improving their computer skills and integrating the computers into their business operations.
After I became a GM CRM Certified Technician, I purchased, installed, and configured GM for Huston Clay Products, then provided instructions to all the personnel on its usage. I also scheduled a Friday and Saturday monthly visit to maintain all the computers and often had visits to analyze and correct any problems that they encountered.
Working with Doris and Fred was a pleasure. They were both Classical Music enthusiasts and Movie and Television buffs, and we would listen to classical music and pose Movie and Television trivia questions throughout the time we spent together. Our favorite trivia was to quote a line from a movie or television show, and the others would have to come up with the name of the movie or television show and who spoke the line. We were all very good at this trivia contest, and nobody was superior to any other person.
I am not much of a practical joker, and Doris and Fred were not practical jokers, but I twice did play a practical joke on Fred, which all agreed was hilarious after the practical joke was over.
While perusing the web while at home, I came across a video clip from the movie ‘When Harry Met Sally’. This video clip was the famous deli lunch table scene where Meg Ryan fakes an orgasm with Billy Crystal. I was able to extract the audio of the fake orgasm, and I brought this audio to Huston Clay Products on my next visit, where I was fixing a problem on Doris’s computer. Before Fred arrived for work, I placed this audio in his computer startup folder, where it would automatically play whenever he powered on or restarted his computer. Shortly after Fred arrived at work and began playing classical music, I asked him to turn up the volume of the classical music so that I could hear the music. He turned the volume up some, but I requested that he make it louder, which he did. A few minutes later, I asked Fred to finish what he was doing and restart his computer, as I explained that I needed to examine his computer after a fresh restart to compare it to Doris’s computer. He did so and informed me that he had restarted his computer, at which time I walked to his desk, where Doris was standing behind and talking to Fred, to watch his reaction when the orgasm audio started playing. When the orgasm audio started to automatically play, Fred looked like a frozen deer in headlights; Doris was shocked but immediately got the practical joke. Fred started to sputter and tried to explain away the orgasm audio, to which I exclaimed that he needed to stop visiting porn sites during working hours because they could infect his computer. After a few moments, he recognized the audio, looked at me, and said, “Meg Ryan in When Harry Met Sally”, and we all began to laugh. Fred then said that this was a good practical joke but that I should immediately delete this audio from his computer, which I did.
On another occasion, I needed to telephone Fred to discuss a minor issue that I was in the process of resolving. Fred always answered the phone by saying, “Huston Clay Products, Fred speaking.” In a flash, I realized that I could play another practical joke on Fred based on his telephone greeting. I decided to pose as a prospective major customer who mistook his telephone greeting as “Mr. Fred Speaking”, with speaking being his last name. I then began the telephone conversation (in a fake Englishman accent) by informing Mr. Speaking that I had a major masonry construction that I wished to talk to him about. When Fred tried to correct my misunderstanding about his last name, I chastised him for misleading me with his telephone greeting and asked how I could trust Huston Clay Products with my masonry construction when the first thing he did was mislead me about his last name. As Fred started to apologize, he paused, then said to me, “Mark, what do you want?”. I started laughing, and he started laughing, and he then admitted to me that I had fooled him at the beginning of the conversation until my Englishman accent faltered. However, I did notice afterward that he started answering his telephone with the greeting, “Huston Clay Products, Fred Muller speaking”.
About twelve years after I started providing my services to Huston Clay Products, I received a telephone call from Fred to inform me that Huston Clay Products had been sold. Tom had been suffering from back pain from a serious car accident that he had been involved in before I met him, and he had decided that as the back pains had worsened, he could no longer do his work, and he needed to retire for medical reasons. He had contacted a competitor of his about the sale of his company, and she was eager to purchase his business. As she had a computer consultant for her own company, she decided not to retain my services. She would not even allow me on the premises of an (unfounded) concern that I may cause some problems. Thus, I lost a major client and some good friends that I never saw again.
My First Lawyer Client
Marion Demcisak’s husband, John, was a successful civil lawyer with his own legal business, which was staffed by only John and his legal secretary. As each had their own computer, John decided to hire me to take a look at their computers to evaluate their computer system. Upon review, I discovered that they had no UPS, their Microsoft Windows and Security software had not been updated since they purchased their computers, and while they did have backups, they were done manually to 3.5-inch floppy diskettes. I also discovered that they shared documents by copying them to a 3.5-inch floppy diskette and handing the diskette to the other person.
The manual backups to 3.5-inch floppy diskettes were fraught with problems, as I could be certain that the backups would be incomplete and out of date, and the restores would be laborious and time-consuming. The sharing of documents via a 3.5-inch floppy diskette was done because the two computers were not networked to each other, although both computers had a shared internet connection.
Upon explaining these problems to John, he directed me to correct these problems ASAP. I installed a UPS on both computers, updated their security software and turned on automatic updates for the security software, and updated Microsoft Windows on their computers. I also created a peer-to-peer network with a shared folder on the legal secretary’s computer that John could access, and I purchased a Zip drive with a removable Zip disk that had sufficient storage space for backing up all their current and future documents onto one zip disk. I automated the backup procedure with backup software that I scheduled to run every Friday afternoon at 4:30 PM, whereupon John would take the removable Zip disk home for offsite backup purposes. I then provided John and his secretary with instructions on the backup and the security software update procedures and how to share documents via the shared network folder. They faithfully followed these instructions and were thankful that these procedures made their work efforts easier. I also visited their office once a month for about four hours to check the health of their computers and to ensure that there were no problems with their computers, backups, and security software, and to apply any Microsoft Windows updates.
This backup procedure proved crucial, as about two years after I instituted this backup, I received a telephone call from John on a Monday morning, in which he informed me that his two computers had been stolen during the weekend. I inquired if he had backed up the computers on Friday afternoon and if he had the backup Zip disk in his possession. He informed me that they had indeed backed up on Friday afternoon but that he had left the backup Zip disk in the Zip Drive and that the thieves had only taken the computers and had left the Zip drive and the printers. He also informed me that the police had taken the Zip Drive to dust it for fingerprints, and my heart sank. I informed him that the dusting could damage the Zip drive and Zip disk and possibly make them unusable. He informed me that he had spoken to the police officers about this dusting, and they assured him that they were aware of this problem and would take precautions to not damage the Zip disk.
I then proceeded to John’s office to discuss what we needed to do to replace the stolen computers. I discovered that the thieves had simply cut the cords attached to the computers and spirited away the desktop computers leaving all else behind. Thus, all we needed to do was purchase two new computers, and replacement cords, then install and configure these computers and his application software, and when the Zip disk was returned by the police, restore his documents. Simple in concept but time-consuming to accomplish. I spent all day Monday and Tuesday doing this, and when the police returned the Zip disk on Tuesday afternoon, I restored the documents on Wednesday morning. By noon on Wednesday, he had fully functional computers with no loss of his documents.
John and Marion also had home office computers that I also maintained. Marion did much client bookkeeping on her home office computer, while John did little work on his home office computer but utilized his computer for his hobbies of photography and woodworking. I set up these home computers with my three cardinal rules, then assisted Marion in establishing her business procedures for transferring her clients’ accounting data to and from her home office computer. When John retired, he decided to purchase a Macintosh computer, as a Mac was more suitable for his hobbies. I set up and configured his Macintosh computer, then transferred his personal Windows documents to the Mac, as well as restored his office legal documents to the Mac so that he would have a historical record of his legal correspondence.
John and Marion were both somewhat unique individuals and a somewhat unique married couple who adored each other, and I thoroughly enjoyed working with them. We had many personal discussions and swapped stories while we worked together. Our relationship lasted for two decades until both John and Marion retired and moved to Indiana to be near their daughter and son-in-law and their children.
My Divorce Lawyer Client
While teaching an adult evening school class on Microsoft Windows computers, one of the enrollees was an older man who sat across from the other enrollees. Within twenty minutes of instruction during the first class, I heard a “Whoops” being exclaimed by him. Upon going over to examine the whoops, I discovered that he had gotten ahead of the instruction and changed his desktop background to a nonsense scribble that had obviously been created by one of the students at the school district. I changed the desktop back to what it should be, and I requested that he not get ahead of the instruction. After the class was over, he came up to me and introduced himself, and told me that his college nickname was “Whoops”. He had the habit of getting ahead of the professors, which on one occasion led him to drop and shatter a tray of glass test tubes in his chemistry lab, to which he exclaimed, “Whoops”, and the other students started referring to him as “Whoops”.
After the course was completed, he again came up to me and informed me that he was a lawyer and would like to hire my services for his law firm, which offered clients extensive legal expertise in domestic relations for over 40 years throughout Bucks County, Montgomery County, and Philadelphia County. He specializes in divorce with emphasis on complicated custody-related and relocation issues, as well as same-sex and racially diverse matters. I, therefore, began to refer to him as my divorce lawyer.
His law firm was staffed by only himself and his legal secretary, and he had the same initial problems as My First Lawyer Client, which I corrected, and I provided him with the same services as I did for my first lawyer client. I also created a website for his business that he was very pleased with and which garnered him a few clients. We quickly became very good friends that have lasted until today. He also had a home office computer that I was responsible for maintaining, and I provided individualized computer instruction to his wife on this home office computer. When he retired and permanently moved to his shore home, I purchased and set up a new computer in his shore home and transferred all his personal and professional documents (so that he would have a historical record of his legal correspondence) to this new computer. I still maintain personal contact with Rich, occasionally providing him with free advice and free remote assistance with any problems he may encounter with his personal computer, and I visit him once a year at his shore house.
When I first started working for Rich, I noticed a plaque on his desk that read, “A Good Lawyer Knows the Law, a Great Lawyer Knows the Judge”. I asked him what he meant by this, and he explained the meaning of this statement. He elucidated that a Judge had some discretion in the interpretation and application of the law in their rulings, and if you knew the judge’s proclivities, you could tailor your legal argument to these proclivities and thus were more likely to receive a favorable ruling from the judge. As he knew all the judge’s proclivities that he argued in front of, he often had favorable legal rulings for his clients.
One day I showed up at his office, and he was walking with a cane with his knee in a brace, his wrist was in a cast, and his forehead all bruised. I asked him what had happened to him, and he explained he had the biggest “Whoops” in his life. A few weekends back, he decided to clean out the gutters at his house, and after he climbed to latter to the gutter, the ladder slipped off the gutter, and he tumbled six feet to the ground injuring his knee and wrist, banging his forehead as he hit the ground, as he let out the loudest “Whoops” of his life as he fell to the ground. As he was scheduled to appear before a judge on Monday morning, he did so but asked for a delay of one week to recover sufficiently to argue his case. The judge granted him the delay, with the admonishment that older men of their economic status did not do much physical work but hired younger men to do the physical work for them. From that point onwards, Rich hired younger men to do his physical work, a lesson that I applied when I became an older man.
While perusing Rich’s legal secretary computer documents folder structure for improvements to the structure, I noticed a folder named DAL Inc. I asked Rich what his association with DAL was as I was doing some Goldmine work for DAL. He informed me that he was the lawyer for DAL, as he and the President of DAL Inc. had been personal friends for over twenty years when he had met him on a cruise that they and their wives had taken. I commented that I was also doing some work for DAL, and we remarked that it was a small world in which we both worked for the same company.
DAL Inc.
DAL Inc. was a credit collection company that would purchase debt at a discount from businesses, then attempt to collect this debt from the debtors. They had about twenty employees, each with their own client computers that were connected to a server computer. This Client-Server network, and all the computers, were managed by another computer services company that specialized in providing support for Client-Server networks. DAL Inc. had contracted with Sabre Systems to install, configure, and customize Goldmine on their network, which I spent about three weeks accomplishing. They also occasionally required Goldmine update support and modest enhancements to Goldmine. When Sabre Systems exited the Goldmine business, they contracted with me to provide this update support and modest enhancements to Goldmine.
At one point, they started to incur some problems with Goldmine, and they contacted me to analyze and resolve these problems. During the process of analyzing these problems, Goldmine crashed and became unusable by all. After several hours of analyzing the crash, I was able to determine that the Goldmine database had become corrupted, and I would need to restore the backup from the point before the problems and the crash. Upon contacting the Network Administrator, he started the process of restoring the Goldmine database and informed me that it would have to be done overnight but should be completed by the next morning. The next morning, when I arrived early at DAL, the Network Administrator informed me that there was a problem restoring the Goldmine database. Apparently, while the daily tape backup of the Server computer reported that the backups were successful, there was a mechanical problem with the tape backup drive that made reading the backup tapes impossible. Thus, proving the old computer adage that if you cannot do a restore, then you have no backup.
The Network Administrator needed to purchase a new backup tape drive and then determine when the last readable backup tape had been created. When he determined this, he could then restore the Goldmine database to the time of the last readable backup tape. After installing the new tape backup drive, he discovered that this problem was several months old, and the last readable tape would be considerably out-of-date, and we needed to determine how we could recover the current Goldmine database with the up-to-date information. Fortunately, the DBMS for Goldmine maintained a transaction log of all the database activity, which we could utilize to update the restored database. The Network Administrator set about to discover when the last readable backup tape had occurred, while I set about to create the procedure to apply the transaction logs from that point onward. I informed all my clients, for which I had scheduled appointments for the next week, that I would be unavailable until this problem was corrected, and after the problem was corrected, I would telephone them to reschedule our appointment.
In the middle of that night, my wife and I received a telephone call from our daughter’s college nurse, informing us that our daughter had come into contact with some peanut dust at a bowling alley, which she was highly allergic to, and as she had forgotten her EpiPen, she had gone into anaphylactic shock and was admitted to the local hospital where she was in stable condition. My wife and I immediately left to be by her side, but as the college was several hundred miles away, I left a message on DAL’s phone system that I would not be able to return to DAL for the next several days until my daughter had recovered and that I would contact them when I returned. I initially thought that I would return in two or three days, but upon our return with our daughter five days later, I telephoned DAL to determine the status of the recovery efforts. They informed me that the Goldmine database had been restored, that they had hired another Goldmine consulting firm to apply the transaction logs, and their Goldmine database was up to date. They also informed me that the other Goldmine consulting firm had several Goldmine Certified Technicians on staff, and they thought it best to hire them as their future Goldmine consultant, as they would always have the services of a Goldmine Technician when problems occurred.
I adopted the attitude of “Que Sera, Sera (Whatever Will Be, Will Be)” and wished them well in their future efforts. I later learned from Rich Moore that they had never heard my telephone message and that they assumed that I had just abandoned my efforts to help resolve the problem. As I had forgotten my cell phone in a rush to visit my daughter in the hospital, and I hadn’t contacted them until I returned, the lack of Goldmine support was impacting their business, and they needed immediate assistance to resolve the problem. I vowed never to forget my cell phone and to remain in contact with my clients no matter what the circumstances.
Harold Goldberg & Associates
While teaching another adult evening school class on Microsoft Windows computers, two of the enrollees were an older man and his wife. After the course was completed, he introduced himself and his wife, Harold and Shirley Goldberg, and he informed me that he was a self-employed accountant for about twenty small businesses in the area. While Harold did the accounting for these small businesses, these businesses employed bookkeepers for the daily accounting, while Harold monthly audited the books to ensure their correctness and to provide financial and tax advice to the owners. He further informed me that he did the business and personal taxes for his clients, and he needed some assistance in preparing the taxes for his clients. He had a young man that provided computer assistance in entering the tax information into the computer software application that he utilized to prepare taxes, but this young man had recently moved about twenty miles away and could no longer assist him with the tax preparation. He asked me if I would be interested in providing him with assistance in preparing taxes, to which I agreed to do so. Thus began an over twenty-year relationship with Harold that went far beyond just tax preparation.
I not only entered the tax information into the computer application, but Harold also imparted much of his knowledge about taxes to me, and as I became more knowledgeable about taxes, I became more of an assistant in preparing the taxes rather than just a data entry clerk. I occasionally joked that as his business name was Harold Goldberg and Associates and that as he worked alone, then I must be the associate in his business name. We laughed whenever I made this remark. The tax knowledge that he imparted to me I was able to put to good use in my own business and personal taxes, as well as when I configured my client’s accounting software. I became friendly with many of Harold’s clients because of their visits to Harold’s home office to discuss their taxes, and I was also hired by a few of them to maintain their computers. I also discovered that if you knew a business or a person’s tax information, you knew a lot about the person or business.
Harold was also very much a family man, and we often swapped stories about his wife, his son, his daughter, their spouses, and their children, as well as my own family stories. Harold was also a religious Jewish man that was very knowledgeable about the Jewish religion, its traditions, and the history of the Jewish people. He often imparted this knowledge to me, and as a result, I became much more familiar with the Jewish religion and culture, as well as its people throughout the world.
Harold was old enough to be my father, but this age difference played no part in our relationship. As Harold entered his late seventies and early eighties, he reduced his clientele to a half dozen people. One tax season, he informed me that he would be retiring after the tax season. We finished the tax work a week early when Harold told me that he was not feeling very well and that he was going to an endocrinologist the next day to determine if he had any medical problems. The day after his appointment, I called him to find out how he was doing. His wife answered the telephone and informed me that Harold had a rare thyroid disease that was virulent and terminal and that he was admitted to the hospital, where it was expected that he would only have a few more days to live. He had sufficient time left to gather his children and grandchildren, who lived in other parts of America, to say his goodbyes. A few days later, I called Shirley to find out how Harold was doing, and she informed me that he had passed away that morning. In the Jewish tradition, he was buried three days later, ironically on April 14th, and I attended his services and interment. At the end of the interment, Shirley invited me to her house for the beginning of the shiva, but I had to politely decline as, ironically, being busy with my other clients, I had not done my own taxes, and I needed to immediately complete them. I did, however, prepare a personal eulogy for Harold which I printed and gave to her. After Shiva was complete, they held a luncheon in Harold's memory, which I attended, along with family, friends, and clients of Harold (many of whom I knew from working with Harold). A year later, I was invited to the Jewish Unveiling and Visiting the Grave ceremony, which I attended. At the end of the unveiling, Shirley invited me over to her house to read my eulogy to Harold. I again had to politely decline, as one of my clients was having a serious computer problem that needed my immediate attention. Harold’s son read my eulogy, and Shirley later informed me that all present thought that it was very touching and appropriate for Harold.
During the many years that I assisted Harold in tax preparation, I encountered many stories about his clients, a few of which are worthy of relating.
One Hanukkah, Harold‘s daughter and son-in-law (who was a renowned Radiologist), along with their children, decided to spend part of the holiday at Harold‘s home. When I went to Harold’s house in January, I noticed that the utility programs that I had installed, along with several other programs, were no longer present on his computer. When I asked Harold about this, he informed me that his son-in-law was using his computer and recommended that these utilities and other programs be uninstalled as he thought they were not needed and were cluttering up his computer. I explained to Harold the purpose of these utility programs and that they were not cluttering up his computer and consumed no resources (other than a small amount of disk space) except when I utilized them to maintain or diagnose his computer. As I was reinstalling the utility programs, I commented to Harold that the next time his son-in-law wanted to change anything on his computer that he should remember that “He’s a great Radiologist”.
One of Harold’s clients was a manufacturer and installer of large outdoor signage, with almost all his sales and installations with the K-Mart corporation. When K-Mart started to have financial difficulties, they stopped ordering signs from him. Despite his efforts to obtain new clients (as it was the start of the 2007 recession and almost all businesses were not spending more than was necessary), he was unable to gain any significant clientele, and he went out of business. Thus, proving the old adage, “Never put all your eggs in one basket.”
Another of Harold’s clients owned a small trucking business that employed the owner’s brother as a truck driver. Harold did all the accounting for this business, as well as the business taxes and the personal taxes of the owner and his brother. One year the brother came down with an eye condition that did not allow him to keep his eyes open without his holding them open. The brother was reassigned to clerical duties, where he held one eye open with his left hand while he used his right hand to do the clerical work. After Harold and I prepared the brother’s taxes, in which we truthfully declared him legally blind, we both noticed that because of rolling over his taxes from the previous year, his occupation was listed as a Truck Driver. Thus, we were about to declare to the IRS that the brother was a legally blind truck driver. After much merriment about this faux pas, he became a legally blind clerk.
One of Harold’s clients was a manufacturer of ties and other apparel accessories that he sold to gift shops at hotels across the country. This was a very successful business in which the owner employed his two sons to help manage the business. Harold did all the accounting for this business, as well as the business taxes and the personal taxes of the owner and his sons. One day, in the middle of the 2007 tax season, one of the sons visited Harold’s home office to discuss his personal taxes. Harold and I had the habit of keeping the television at low volume on a business channel. As we were discussing his taxes with him, he seemed to be turning pale and sickly looking. After he left, I mentioned this to Harold, and he agreed and informed me that he would be seeing him a few days later at the business location when he would check up on him. The next week I arrived at Harold’s house to do other tax preparation when Harold informed me of the reasons for the son’s appearance. The son had purchased about $500,000 dollars of stock on credit secured by his house. As the stock market sank while we were discussing the son’s taxes, he realized that his stockbroker was going to call in the loan, and he would have to pay off the loan, probably by selling his house. Harold also informed me that when the father learned about this situation, he lent his son the money to pay off the loan but garnished forty percent of his salary over ten years to repay the loan. This reinforced the maxim that you should never borrow money for investment unless you can pay off the potential losses, and any and all investments are prone to losses.
Another of Harold’s clients had turned his business over to his son as he was establishing a new business. Harold informed me that he would provide accounting and tax services to the son, but he would have no part in the new business as he thought that the new business was unethical and perhaps illegal. About a year after the new business was formed, the owner was arrested and prosecuted for fraud and sentenced to three to five years imprisonment after he was convicted. He was released on parole after eighteen months, with the proviso that he could not own nor operate a business for the next ten years. The father then became an employee of the son until he retired.
On another occasion, I discussed a problem that I was having with a newer client of mine. She was a mature Jewish woman who was having difficulties using her personal computer, and she wanted me to assist her with her computer usage and problems. Our relationship had started out very cordially but had degenerated in the last several months. She became very needy, demanded my immediate attention whenever she encountered a problem, and did not pay me in full. She was also a constant complainer about her life, even though she had a good and healthy middle-class life. Harold informed me that there was a Yiddish word for such people—kvetch and that these people were considered to be unredeemable and should be avoided at all costs. He recommended that I immediately cease all contact with her, write off her debt, and go on with my life. Advice which I followed and was grateful to Harold for giving me.
I often think of Harold and Shirley, and for as long as I live, I will fondly remember Harold and Shirley and the personal relationship that we forged, and I hope for the best for his family.
The Omega Man
One of Harold’s clients was a self-employed businessperson, Art Senno, who operated a chemical waste treatment and disposal service, Alpha-Omega, for dry cleaners in the Philadelphia metropolitan area. I became very friendly with him in helping to prepare his taxes, and he contracted with me to supply my services for his home-office computer. During our many discussions, while I was working with him, he offered me a Root Beer, to which I explained to him that I only drank one brand of Root Beer, Stewart's, which I found to be so excellent that I disliked other Root Beer brands. I also informed him that it was difficult to obtain Stewart's Root Beer in this area, as they were a southern company that did not have many outlets in the Philadelphia area. The next time I showed up at his home to assist him, he had a pleasant surprise for me—a six-pack of Stewart's Root Beer. He explained that he had gone into a grocery store near one of his New Jersey clients and discovered that they sold Stewart's Root Beer. From then onwards, whenever I went to Art’s home, he had a six-pack of Stewart's Root Beer waiting for my arrival. I should also note that Stewart's Root Beer and other Stewart's beverages have since become generally available in the Philadelphia area, and I would highly recommend that all give it a try.
After I retired, one of Art’s two daughters telephoned me to inform me that Art had died (his wife had died several years previously) and that she needed my help accessing Art’s computer business information. She and her husband had moved into Art’s home upon the death of his wife, while the other sister had a house a few blocks away from Art’s house. I had helped the one sister that lived a few blocks away with her home computer problems, and I telephoned her to offer my condolences and mentioned that the other sister was requesting my help with Art’s computer. As this sister was considered the good daughter, while the other sister living in Art’s house was considered the problem daughter, the two sisters never got along with each other. She informed me that the estate was in dispute between her and her sister, and she did not want me to provide any computer assistance to her sister.
I immediately telephoned my retired divorce lawyer for advice, as he was an expert in family estates and their legal disputes. He advised me to do nothing without a court order and being paid by the estate under litigation, as otherwise, I could expose myself to legal action by either of the sisters. I, therefore, called back both sisters and informed them that I had been advised by legal counsel to do nothing without a court order. I never heard back from either of them, and no court order was ever served upon me.
HK Pickles
Harold’s sister-in-law's husband, Hank, was a manufacturer and wholesaler of kosher Dill Pickles to delis and restaurants in the Philadelphia area. He contracted my services to take care of his home-office computer, which he utilized to manage his business. He had the same initial cardinal rule problems, which I corrected. As the internet was booming at the time, he decided that he wanted to sell his pickles online. I explained that not only would he have to create a website that would take orders but that he would have to have a back-office procedure on his computer to process payments and provide shipping and handling of orders. I further explained that he would have to market this website for people to know of its existence.
He decided to proceed with doing this, and I created a website for him, as well as the back-office procedures, but the marketing of the website would be his responsibility. After successfully developing the website and testing the back-office procedures by having Harold, Hank, and I order and receive pickles through the website, I turned the website over to him to begin the marketing. He promptly did nothing to market the website, and he only sold a few dozen pickle jars over the next few months. He later informed me that he had contacted a sales and marketing company to promote the website, but as they would have charged him $25,000 dollars for the initial marketing, he declined to expend this money. As a result, he discontinued website sales and concentrated on his wholesale distribution.
This lack of website success did not fracture our relationship, as he realized it was his inactions that led to the failure of online sales, and I maintained his home-office computer until he retired and turned over the company to his son.
H. Katz Capital Group
- Katz Capital Group is a $100,000,000 acquisition/venture capital firm formed by entrepreneur Harold Katz to acquire businesses and provide funding to a wide range of companies. His firm consisted of a Financial Advisor/Lawyer, Brian Siegel, an Office Administrator/Personal Assistant, Helen, and a Clerical assistant that varied throughout the years that I supported H. Katz Capital Group, all of whom had computers to perform their tasks. They had the same initial problems as My First Lawyer Client, which I corrected, and I provided them with the same services as I did for my first lawyer-client. I also created a website for his business that they were very pleased with and which garnered them a few acquisitions and financial funding clients. The Financial Advisor/Lawyer also had a home-office computer for which I provided my services, and Helen had a personal computer in her condominium, which I supported as a personal client. Harold’s wife also had a home computer which she utilized for her charitable efforts and for which I provided my services.
On one occasion, Harold’s wife was working with the wife of the Comcast President on a large charitable event that they were coordinating with each other through their Comcast internet connection. A few days before the event, I received a telephone call from Harold’s wife that her internet connection was not working, and she was frantic to restore this connection to complete the final details of this charitable event. I immediately went to her home to determine what was wrong and fix the problem. I soon discovered that the internet connection was not working between her house and the Comcast Streetside connection box. I called Comcast technical support to report this problem, which they confirmed, then asked them to immediately dispatch a repair crew to fix the problem. They informed me that as this was a personal residence, they could not immediately dispatch a repair crew, and I would have to wait a few days for them to dispatch a repair crew. I asked the technician if he knew who Harold Katz was, and he responded in the negative. I informed him that Harold Katz was the former owner of the Philadelphia 76’s NBA basketball team and that he was a very rich and influential person in the Philadelphia business and social community. He was unresponsive to this, and I then informed him that Harold’s wife and the wife of Comcast's President were working on a joint large charitable event, and they needed this Internet connection restored immediately to complete the details of this charitable event. I also informed him that I was looking at Harold’s wife's personal contacts, which contained the personal telephone number of the Comcast President's wife (a true statement). If he could not dispatch a repair crew, then I was going to contact the Comcast President's wife to have her arrange for a repair crew to be immediately dispatched. After he discussed this situation with his manager, a repair crew was immediately dispatched and arrived at Harold’s house within an hour. I waited for the repair crew to arrive and assisted them in making sure that the Internet connection was working properly. The problem was quickly diagnosed and repaired, much to Harold’s wife’s relief.
- Katz Capital Group had become a major investor in LA Weight Loss Centers, which was interested in creating a website, and Brian directed them to me for my website creation services. Shortly after I created a website for them, it was decided that the L A Weight Loss Centers computer services department would be responsible for the computer service of H. Katz Capital Group, as they would Internet connecting each’s other computer systems. Although I did occasionally help Brian and Helen with their home computers, this did not last but for a few years, and I eventually lost contact with both Brian and Helen.
LA Weight Loss Centers
LA Weight Loss Centers was a premier weight loss/management franchise operation that was rapidly expanding its franchises to service the needs of its customers. Upon meeting with the head of Marketing, I discovered that the website was for prospective franchisees to learn more about the opportunity for a franchise with LA Weight Loss Centers. They were about to finish with the creation of their printed marketing brochures, and they wanted to post these brochures on an attractive website. As this was right up my alley, I informed them that I could do this with about five days of effort if they provided me with the electronic version of their brochures. They readily agreed to do this, and they would call me back when the brochures were completed and they needed the website to be developed.
The next week, on a Wednesday morning, they informed me that the brochures were completed, and I could pick up the printed and electronic versions of these brochures to begin developing the website. When I arrived later that morning to do so, The Marking Manager informed me that they had purchased full-page advertisements featuring the website address that was to be run on Sunday in many major newspapers in the Boston to Washington D.C. metropolitan area. This left me four days to complete the website, and I spent the next four days, twelve to fourteen hours a day, developing this website. Late Saturday afternoon, I met with the Marking Manager for approval of the website, and after a few minor corrections, the website was posted very early Sunday morning.
Due to the extensive keyboarding and mousing in the development of this website, I developed aches and pains in my right hand, elbow, and shoulder, which despite physical therapy, have occasionally plagued me for the rest of my career.
Blue Bell Hearing Aid Center, Inc.
A client of mine informed me that a neighbor of his was having difficulties with her two office computers and her home-office computer, and he had given her my name, and she was expecting a telephone call from me. Alicia Kurtzman had just obtained her Hearing Aid Specialist license, and she had just purchased Blue Bell Hearing Aid Center, Inc. from a good friend who was moving to Florida. We agreed to meet at her house one morning, where I would examine her home-office computer, and then I would follow her to her office to examine her Office Administrators and her computer. Alicia was in her late thirties when I first met her, and she was a very attractive and sexy woman who enjoyed displaying her attractiveness and sexiness, which she put to good use in caring for her older male clients.
We had an unusual start to our relationship that should be recounted, and it bears upon the future course of our relationship.
I went to her house to meet her and examine her home-office computer and entered through the open side door to the laundry room, which was next to the kitchen. Upon entering the kitchen, Alicia was sitting behind the kitchen counter, in her bathrobe, and a towel wrapped around her hair, and we greeted each other and explained that she had not yet finished getting ready for work, but she would do so while I was examining her computer. She explained the problems she was having with her computer, with the most pressing problem being that her printer was not working. She led me upstairs to show me the room where her computer was located, and I began my examination while she finished getting ready for work in her bedroom.
Upon the examination of her computer, it became necessary for me to crawl under her computer desk to check the cable connection, where I discovered the truth of a modification that I had made to Sir Walter Scott's line in a poem of his, "Oh, what a tangled web we weave...when first we practice to computer cable." I also discovered that she had more cables than equipment, and because of the cable entanglement, I could not trace the printer cable. As I was crawling backward to extradite myself from under the computer desk, I reached around for support from the computer chair that I knew was behind me. Unbeknownst to me, Alicia had entered the computer room, fully dressed, and was sitting in the chair. As I turned around on my knees, I found myself looking up Alicia’s dress and began to apologize, to which she responded that this was no problem as I was where she wanted all men to be—"On their knees in front of her.” We both laughed, then I explained what I had discovered about her home office computer and recommended that I re-cable her computer to discover the printer problem. She agreed but suggested that I do this after I examined her business computers, and she gave me a spare key to her house so I could return later that day to work on her home office computer.
We then proceeded to go to her office, and I followed her in my car. After arriving at her office through a most circuitous route that took forty minutes to navigate, I asked her why she dove to her office via this route. She responded that it was the only route she knew how to get to her office. I chuckled, then informed her that there was a more direct route that could save her ten to fifteen minutes of her commute time. I gave her directions for this route, and she began to utilize this route for her commute.
Upon entering her office, I met her Office Administrator, and Alicia suggested I look at her computer first, as she had much to discuss with her Office Administrator. I went into her office to begin my computer examination and again had to crawl under her desk to examine the cabling, which was also a tangled mess. Once again, as I was crawling backward to extradite myself from under her desk, I found myself on my knees looking up her dress, as I had not heard her enter her office. Before I could apologize, she remarked that I was obviously easily trainable and that I should continue to be on my knees in front of her. We laughed, and I commented that henceforth her every wish would be my command.
For the rest of our relationship, we engaged in outrageous harmless flirtation and meaningless sexual innuendo, including in front of her husband number one and husband number two (but never in front of her daughter). We both enjoyed this repartee, especially as we both knew it would never come to fruition.
On one occasion, Alicia informed me that her brother required computer assistance and that I should telephone him. She also mentioned that I might like him more than her, and I responded, with my hands moving up in down in opposite directions and my head looking back and forth between my hands, “Let’s see, good-looking, sexy gal versus guy.” To which she retorted, “I know, I know. What could I possibly have been thinking?”
Alicia was a very intelligent, independent, self-reliant, and strong-willed woman, which ultimately led to a divorce from her first husband, as he wanted a more traditional wife (which he obtained in the marriage to his second wife). Alicia also remarried, and her second husband enjoyed her personality and independence. Both ex’s and their current spouses became good friends, and often celebrated family events and dinners together. Both times Alicia married a Jewish man, and in her first marriage, she converted to the Jewish religion, despite her Italian Catholic upbringing. Her mother and father, whom I got to know from my visits to her house, often joked that she was an Italian Princess transformed into a Jewish Princess.
Alicia’s mother (and sometimes father) would come to her house to take care of her daughter when she came home from school and until Alicia came home from work. I became very friendly with her parents, as I met them on the occasions that I went to Alicia’s home to take care of her home-office computer. On one occasion, when I went to Alicia’s home, I discovered her mother in a very frightened state. Alicia’s mother was deathly afraid of bees, and a bee had somehow entered the house. She was running away from the bee, and I calmed her down by volunteering the track down and kill the bee. I spent the next several minutes swatting at the bee until the bee landed on the high-ceiling foyer entrance to the house. I grabbed the ladder from their garage and climbed it, then killed the bee. From that point onward, her parents referred to me as the “bee swatter”.
Alicia noticed my hearing problems immediately (which was hard not to notice) and insisted that she do a hearing evaluation on me. I agreed as I knew Alicia to be an honest and truthful person, and she would not recommend anything more than I needed in a hearing aid. After the hearing evaluation was completed, she informed me that I was very deaf and that without hearing aids, I could not understand anything other than one-on-one conversations in quiet rooms, and without hearing aids, I would probably be deaf to all conversations in a few years. I also needed high-end hearing aids to allow me to hear properly. I, therefore, agreed to purchase hearing aids from her and have been doing so ever since, and I have become progressively deafer ever since. She attributed my deafness to the many years I had worked in Mainframe computer rooms, as the noise that the computers, printers, and air conditioning units had been found to cause progressive deafness, even after a person no longer worked in a computer room.
During my initial examination of Alicia’s home and business computers, I noticed that the computers violated my cardinal rules, and I recommended that she have me institute my cardinal rules on all three computers, which she agreed to. I informed her that it would be best to institute these cardinal rules before I began an in-depth analysis and any fixes that would be required. I informed her that this cable de-entanglement, the institution of the cardinal rules, and in-depth analysis and any fixes would take approximately three to four hours per computer to accomplish, during which time she would not have the usage of the computer I was working on. She agreed to this, and she suggested I do this for her home-office computer when I returned to her house later that day. She also suggested that as she would not be in her office the next afternoon, I do this the next morning on her Office Administrator’s computer and the next afternoon on her business computer. I agreed to this schedule and proceeded to undertake this effort.
I also suggested that I examine how she and her Office Administrator utilized her computers in their business so that I could make suggestions for improvements in how they utilized their computers. She agreed, and after I completed my initial efforts, I sat down with her and her Office Administrator to discover how they utilized their computers, and I made several suggestions that improved the efficiency of how they utilized their computers. Throughout the more than two decades that I assisted Alicia, she had several Office Administrators, all of whom I worked with and instructed on the usage of the Office Administrator’s computer.
Several years later, as hearing evaluation equipment became smaller, less expensive, and able to connect to computers, Alicia obtained a laptop computer that would connect to the hearing evaluation equipment and perform hearing tests outside her office. She began to provide a hearing evaluation at retirement and nursing homes and community centers and spent a good deal of her time outside the office. I also became responsible for maintaining this laptop, which I often did at her home, where I met her parents.
A few years after I began providing my services to Alicia, she decided that she wanted a website to promote her business, which she contracted me to develop. As she had much-printed literature about hearing health and hearing aids, the development of her website would be more of style rather than content, and Alicia wanted a very stylish website. I took all her printed literature and photographed her and her assistant, as well as the office and hearing aid equipment, and began to develop the most stylish website I had ever created. I spent many weeks developing this website, and Alicia was so pleased with this website that I thought our sexual innuendo would come to fruition (just kidding!). Alicia was so proud of this website that she displayed it to the national marketing manager for her main hearing aid supplier, who was also very impressed, and he began exploring the possibility of creating websites for his other hearing aid providers, which they did several years later.
With the rise of Facebook, Alicia decided she wanted a Facebook account to promote her business. As I had no experience with Facebook, Alicia decided to pay me to learn Facebook, which I did by creating my own Facebook page, which I never utilized after I created it. I then sat down with Alicia to interactively create her business Facebook page and taught her how to use Facebook, which she does even today.
Alicia was a joy to work with, and we became personal friends at the beginning of our relationship, and I have missed our interactions since my retirement.
Richard N. Best Associates
Richard N. Best Associates was a Value-Added Reseller (VAR) for multiple manufacturers of parking and access revenue control systems, who plans and implements a comprehensive approach to systems integration that meets the unique needs of an organization. Best Associates was a client of Sabre Systems, which they had contracted with Sabre Systems to provide network administration, computer administration, and Goldmine CRM for Sales and Marketing purposes. I would be responsible for the Goldmine installation, configuration, and customization and assist Max in computer administration, while Max had full responsibility for network administration.
Best Associates was founded by Richard Best, who was semi-retired at the time we started working at Best Associates, while his son, Jeffrey Best, was the General Manager of the company, and his son’s best friend, Terry Dun, was responsible for sales and marketing and construction project management. Best Associates had an administrative support staff of four people and six technicians that did the field installation and maintenance for the equipment that Best Associates supplied.
Best Associates had two server computers—a Domain Controller with MS SQL DBMS and File server capabilities, and a Microsoft Exchange Server for e-mail purposes. Best Associates also had eight client desktop computers for office usage and six client laptops for the technician’s usage in the field. Shortly after I finished my Goldmine effort for Best Associates, Sabre Systems withdrew from the commercial business sector, Max was laid-off, and my services were no longer needed by Sabre Systems. Jeff immediately contacted both Max and me to see if we would directly support Best Associate's computer service needs. We both accepted this offer, and Max and I agreed that he would be responsible for server computers and network administration while I would be responsible for the client's desktop and laptop computers. This began a relationship of over two decades between Best Associates, Max, and myself that ended with my retirement. Max eventually moved to New York State to accept a job with Verizon as a business customer network technical support person, but he still provided network administration to Best Associates via remote access support. Whenever on-site support was required, he would travel to Best Associates for the weekend, or I would provide him with the eyes and hands at Best Associates while he directed me on the telephone. Eventually, Max left Verizon and split his time between upstate Pennsylvania and central Florida, where he continued the remote access network administration support for Best Associates, and I provided the eyes and hands as necessary. While Max was very good at network administration, he was not very good at documenting his tasks, while I was very good at documenting my tasks, and I often documented the server and network configuration with Max’s approval.
At the beginning of this relationship, I joined a conversation between Jeff, Max, and two support staff sisters (Chris and Lisa), where they were discussing Jeff’s past weekend events with the sister’s mother. I looked askance at Jeff and asked what his involvement with the mother was. It was then I learned that Jeff was the brother of the two sisters and that one of the technicians was also a brother. I also learned that the technician’s supervisor was Terry’s brother-in-law. Best Associates was truly a family business, and all of them owned a piece of Best Associates.
Jeff was very conscientious in applying updates and upgrades for all the computer software installed on the computers, and it was necessary for me to apply these updates and upgrades on all the client computers on a regular basis. This required that I work two weekends every three months, one weekend for the desktop computers and another weekend for the laptop computers, with each Saturday and Sunday taking ten to twelve hours of effort per day. This was not only because of the number of computers at Best Associates but also because of the number of computer applications they utilized at Best Associates. The applications were primarily Microsoft Word and Excel, Sage Accounting for the company finances, Evron ESP and Dispatch Board for technicians reporting, Goldmine CRM and DetailsPlus for Goldmine, Stonefield Query reporting for Goldmine, QuoteWerks for proposal preparation, UPS WorldShip for shipping, miscellaneous Adobe Software, the Security & Backup software for all the client desktop and laptops computers, and various utilities that I utilized in my maintenance and problem diagnosis. In addition, the technician’s laptop computers had various parking and access control software from multiple manufacturers that they utilized for maintenance and problem diagnosis in the field. I also created a Best Associates User Guide for Goldmine and QuoteWerks.
Jeff was also very conscientious in replacing aging computers, and none of his client computers were more than four years old. Whenever a replacement client computer arrived, I was responsible for the installation and configuration of the computer on the network, as well as installing and configuring the various computer applications on the new computer. Whenever Max did an upgrade or update to the server computers, I was also on-site at Best Associates in the event that problems were encountered. Whenever Best Associates replace a server computer (which they do every five years), Max and I worked the weekend on this replacement and were on-site on Monday in the event that any problems were encountered.
Whenever a new computer for Best Associates customers arrived, either Max or I would be responsible for installing and configuring the software needed for this computer. The technicians would then transport and install this computer at the customer site. Whenever there were problems with a customer’s computer, the technicians would try to solve these problems on-site, sometimes with telephone support from either Max or myself. If the computer problem was unsolvable on-site, the technician would transport this computer to Best Associates’ office, where I would work on this computer to solve the problem. Occasionally, I went on-site to help the technicians, but this was a rare occurrence.
Consequently, Best Associates accounted for about twenty to twenty-five percent of my yearly labor efforts and revenue. Throughout the years, minor problems and issues were resolved by Max and myself, and Jeff often asked me to make enhancements to Goldmine and the other software he utilized to extend their capabilities or integrate their data into each other. I was able to accomplish his request without much difficulty but sometimes with some extensive hours to accomplish. There were only three major issues at Best Associates that I need to recount:
The Symantec Security software and Veritas Backup software that Best Associates utilized were from major vendors that were used worldwide by tens of thousands of customers in mid to large-size businesses. Despite this, the installation of the client computer software for these products was cumbersome and convoluted, and I often had difficulty installing them on the client computers. Normally I would expect that this type of software would take approximately ten minutes to install, and they would automatically configure themselves to work with the server computer. Instead, these products required manual installation and extensive configuration to work properly, often fraught with errors. These installations required that I manually configure the client computer on the Server computer, which controlled the client software, where the slightest misstep or typo would require that you restart the configuration process. As these were the last two software products that I installed on the computer, I knew that I had two or three frustrating hours to complete the installation of these two software products. After I retired, and the new, very experienced computer consultant started doing this, he often telephoned me for advice during this process. He would also always complain that this was a ridiculous process for major software vendors to implement in a Client-Server network. This was a problem with many legacy Client-Server network software, as often something that was necessary at the beginning of networked computers had to be done manually, but as network technology evolved could be done automatically, but the software vendor did not commit the resources, and the financing necessary to upgrade the client installation software to take advantage of the network automation capabilities.
In one situation, this Symantec Security software and Veritas Backup software spectacularly failed Best Associates. I had scheduled cataract and lens replacement surgery for successive Tuesdays and alerted my larger clients that I would not be available, except for telephone support, for those two weeks. On the second Wednesday morning, I received a telephone call from Jeff informing me that on Monday afternoon, his computers had been attacked by Ransomware. Ransomware is malicious software that makes a computer unusable unless a payment is made to the attacker. All his computers had been infected, as well as his backup drives. Jeff was not about to pay the ransom, and Max had been alerted and had been on site since early Tuesday morning trying to restore the server computers from Friday night’s off-site backup. He was encountering some problems with the restore, and he was not expecting to complete the restore until the end of the week. Meanwhile, the client computers had to be rebuilt from scratch, as we had no off-site backup for the client computers. Jeff asked if there was any way that I could help him out in rebuilding the client computers. I responded that I could come in the next day and start the rebuilds, but my eye surgeon warned me that I should not put any physical strain on my eyes for a week after the surgery. I could come in and start, but I would undertake no physical activity, and if my eyes started to become tired, I would have to retreat to my car for twenty to thirty minutes to relieve the strain on my eyes. Jeff responded that if I needed to do anything physical, he would do it for me, and he had no problem with me retreating to my car and would even pay me for the retreat.
Thus began the most arduous two-and-a-half weeks of my career. The first seven days, I worked ten hours per day for seven days straight, and the second week I worked twelve hours a day for ten days straight. As Max was restoring the server computers, which he was having difficulty doing so, I wiped the hard drives of the client computers and installed Microsoft Windows and Microsoft Office on all the client computers. I then installed on the technician’s laptop computers the various parking and access control software from the multiple manufacturer’s website downloads of their software. This took me seven days to accomplish; meanwhile, Max was still trying to restore the server computers, but he had discovered that he could not do a full disk restore, and he would have to rebuild the server computers by reinstalling Microsoft Windows Server and all the application software on the servers. After he finished this rebuild process, he could then do a restore from the backup of all the data on the servers.
After one week of rebuilding and reinstalling the servers, the computer system was functional but had no data restored on the server computers. Max and I then “joined” the client computers to the server Domain Controller, and Max set out to restore the data on the servers while I was able to install the client software of the server applications on all the client computers. After we had successfully completed these tasks, both Max and I had to tweak the server and client computers for them to be fully functional for Best Associates usage. After two and a half weeks of efforts by Max and myself, during which Best Associates had no use of their computers, Best Associates was able to use their computers, and they spent the next week updating their data. Max went home to New York while I went home for a long weekend to recover from my arduous efforts.
At the end of the next week, after we had finished this effort, I visited Best Associates to discuss with Jeff and Terry, and in a conference call with Max, the events of the past few weeks and determine how we could alleviate this situation in the future. I explained to Jeff and Terry that the ransomware was a zero-day exploit that was not detectable by the Symantec Security software, as they had not yet discovered this malware and created a signature to protect against this malware. Security software was of two types—Signature Detection and Heuristic Detection. Signature Detection required that the malware be known to create a signature defense against the malware, while Heuristic Detection guarded against suspicious activities and did not allow them to occur without permission. Also, Heuristic Detection was not vulnerable to zero-day exploits, as it constantly guarded against suspicious activities, and it did not need to know of the existence of a particular malware. Normally, it is a bad idea to have two security software running at the same time, as they will conflict with each other and tie up the computer resources in detecting signatures. However, a properly designed Heuristic Detection security software could co-exist with Signature Detection security software and not tie up the computer resources in any significant manner. I had also done this for AIA-ISSI and my own computers without detecting any problems. I, therefore, recommended that Best Associates install a Heuristic Detection security software, Malwarebytes, that had a reputation of being the best Heuristic Detection security software and was known to not conflict with Signature Detection security software. Max was initially reluctant to do this, as he had little knowledge of Heuristic Detection security software, while Terry was insistent that we do this. Jeff directed Max to learn about Malwarebytes and get back to him with a recommendation. The next week Max responded that Malwarebytes seemed to be a good solution, but he was still concerned about running two security software simultaneously. Jeff decided to utilize Malwarebytes and requested that I install and configure Malwarebytes on the server and client computers under Max’s watchful eye. We did so, and there were no difficulties running both the Symantec and Malwarebytes security software simultaneously.
We next discussed the backup situation, and Max admitted he was frustrated by what had occurred trying to make a full disk recovery and the time needed to recover the data from the off-site backup drive. By this time in my career, I had become somewhat of a backup and restore expert, and I explained the difference between image and file/folder backups and the methodology of full, differential, and incremental backups. I recommended that we abandon the usage of Veritas Backup software and obtain image backup software that had full, differential, and incremental backup capabilities. Max was unfamiliar with image backups but asked if I knew of any backup/restore software that could be utilized by Best Associates. I gave him the name of three such backup/restore software applications, and Jeff directed him to research these and other image backup/restore software applications that would be appropriate for Best Associates usage. A few weeks later, Max recommended one backup/restore software application that he thought would be the best solution for Best Associates. Jeff directed Max to purchase and install this software on the servers while I installed the client software on the client computers. Jeff also directed that Max develop a backup scheme, which I would have to approve, that utilized both the image and file/folder backup/restore capabilities of the software. We accomplished this task fairly easily, and Best Associates has been utilizing this approach henceforth.
On another occasion, Best Associates was replacing the Microsoft Exchange server computer, and we discussed an E-mail service switchover to Microsoft’s e-mail services. It was decided to do both the new e-mail server computer and the e-mail service switchover at the same time. Max purchased this new e-mail server computer and configured and tested it at his home in New York. He then shipped this new e-mail server computer to Best Associates, then came down one weekend to install the e-mail server computer while I changed the client computers to work with this new e-mail server computer. Apparently, Max had not done sufficient testing, as we immediately began to run into problems utilizing this new e-mail server computer and the new e-mail service. It took a week to resolve all the problems, during which Best Associates could not utilize Microsoft Outlook on their client computers to process their e-mail (which was their main source of communication between the customers and vendors). They were able to utilize the web browser-based capability of the new e-mail service provider to remain in contact with their customers and vendors, but this capability could not be integrated with their other application software. After Max resolved these problems, all was back to normal at Best Associates, but Jeff directed me to become involved with Max in the testing of new server computers and major upgrades to their server applications before they were installed. This testing occurred several years later when it was decided to replace and re-configure the other server computer for efficiency and load-balancing purposes, and we had very few problems in doing so. I even lent him my laptop computer, which I was not utilizing, so that he could test a client computer connection to the new server for testing purposes, to verify that there were no problems with this re-configuration.
After my retirement, I had a telephone call from Jeff, in which he asked me for a big favor. He had just hired his son-in-law as a salesman, and he wanted me to train him in the usage of Goldmine, as the Goldmine usage and Goldmine data integrity would be a primary responsibility of his son-in-law. Jeff knew that the original Best Associates Goldmine User Guide that I originally created was somewhat sparse, and he asked me to upgrade this user guide and train his son-in-law with this updated user guide. I agreed to do so, as I knew that this would not be a difficult task for me to accomplish. After I did so, Jeff commented that he had read this updated user guide and that he had also learned some things about Goldmine that he did not know or had forgotten.
While my efforts for Best Associates were sometimes arduous, they were always pleasant, as I enjoyed working with all the people at Best Associates, and I became an extended family member of Best Associates.
Chartwell Advisory Group
Chartwell Advisory Group was a Sabre Systems client for Goldmine CRM, in which I automated their business processes centered around Goldmine. Chartwell Advisory Group contracted with companies to examine their State and Local taxes to determine if they were overpaying on these taxes. This required them to examine their client’s financial statements and the State and Local tax laws to determine if they were overpaying on their taxes. Chartwell Advisory Group was paid a fee for their services and a multi-year commission on the amount of the savings from the overpayments.
Chartwell Advisory Group was owned by two wealthy people who were not involved in the operations of Chartwell Advisory Group. Stephen Deviney was the President and General Manager of Chartwell Advisory Group, and he was the person to whom I reported. Steve was a very nice and intelligent person who I enjoyed working with. When Sabre Systems withdrew from the commercial marketplace, Steve contacted me directly to contract my services for Goldmine support.
This support continued for about ten years when the owners of Chartwell Advisory Group decided to shut down the business due to the impact of the 2007 recession. They did not completely shut down the business, as they were involved in a lawsuit with one of their clients. They retained Steve’s services but laid off the dozen or so other employees of Chartwell Advisory Group.
The lawsuit they were engaged in was against a Las Vegas casino that contracted their services. Chartwell Advisory Group had discovered several redundancies and tax law loopholes that saved the casino sixty million dollars a year in tax payments. Chartwell Advisory Group was supposed to receive a commission of several million dollars a year for the next few years, and the owner of the casino did not want to pay this commission. This lawsuit was decided in favor of Chartwell Advisory Group, but the casino operator appealed this decision to the Nevada Supreme Court, where the casino again lost its appeal. A side issue of this lawsuit was that the State and local lawmakers closed many of the tax loopholes that Chartwell Advisory Group had discovered; the casino owner was claiming that the future commissions should be based on the new tax laws and not what Chartwell Advisory Group had initially saved them. The court rejected this argument, as they ruled that Chartwell Advisory Group could not be held accountable for future tax laws but only the tax laws at the time they completed their contract.
The casino delayed paying Chartwell Advisory Group as they were in the process of selling their casino operator to other owners. The new owners then claimed that they were not responsible for this debt, as they had only purchased the assets and not the liabilities from the previous owner and that the previous owner would have to pay this debt. Chartwell Advisory Group instituted another lawsuit against the new ownership, claiming that when they purchased the casino, they assumed all liabilities of the old ownership and that if they did not purchase the liabilities, then the sales agreement was void as Chartwell Advisory Group had a financial and legal interest in the sale and had not given approval of the sale to the new ownership. Again, Chartwell Advisory Group won this lawsuit, which was appealed by the new ownership to the Nevada Supreme Court, where the casino lost its appeal and had to pay Chartwell Advisory Group the monies that they were due. Steve had telephoned me to inform me of the results of these lawsuits and that Chartwell Advisory Group was in the process of collecting the monies that were due to them from their successful lawsuits.
During these two lawsuits, Chartwell Advisory Group called upon my services to produce Goldmine reports of all the activities that Chartwell Advisory Group engaged in with the casino. I had set up Goldmine to record all telephone calls, appointments, meetings, and work efforts for all the people who worked for Chartwell Advisory Group, which they faithfully recorded in Goldmine. Thus, these reports were important evidence in the lawsuit, and the owners of Chartwell Advisory Group were very thankful for all my Goldmine efforts throughout the years, as they considered these reports to be essential evidence in their lawsuits.
Catalyst Partners
Catalyst Partners was a Sabre Systems client for Goldmine CRM, in which I automated his business processes centered around Goldmine. Catalyst Partners was a marketing consulting company that helped small regional businesses to expand their market nationwide. Jim Kosa, the President of Catalyst Partners, ran a one-man show from his small farmhouse home office in the Bucks County countryside. After the Goldmine development was completed, he expanded his business by hiring two partners, whom I had to train in the usage of Goldmine. When Sabre Systems withdrew from the commercial marketplace, Jim contacted me directly to contract my services, not only for Goldmine but for his business computer system and his wife’s personal computer.
A year after I started my services for Jim, his two partners and he became involved in a dispute, and they ended their relationship. A few years later, Jim was diagnosed with a heart ailment that required him to retire early to maintain his heart health. Fortunately, Jim planned for the possibility of early retirement and purchased insurance that would pay him an annuity in the event he had to retire early for medical reasons. I continued to support Jim and his wife’s computers after his retirement.
Jim was an avid hunter and fisherman, and he had two hunting dogs (a mother and son) that he had trained. These dogs were very loving, and they happily greeted me whenever I went to Jim’s house. One cold, blistering winter morning, I had to go to Jim’s home to solve some minor problems and maintain the two computers. Jim and his wife would not be present for the day, and they left the key to the house hidden near the front door. When I arrived at his house, one of the dogs ran up to my car, which surprised me as Jim instructed me not to let the dogs outside due to the cold weather. Somehow the dog, unbeknownst to Jim, had gotten out of the house before Jim and his wife left the house. As soon as I unlocked the door, the dog ran over to the radiator and plunked himself down in front of it for the next hour. When I informed Jim of this situation, he guessed that the dog had been outside for over two hours, and if I had not been there to let the dog inside, he might have died from exposure to the weather.
Jim and his wife eventually moved to Seattle to be close to their son and daughter-in-law and their children, but I had two decades of friendship with Jim and his wife to fondly remember.
AIA-ISSI
Association Insurance Agency (AIA) is a small, specialized insurance agency that had, just a few months before they contacted me, had Microsoft Windows computers installed in their company for the purpose of supporting a line of business insurance that they sold. The computer consulting firm that purchased and installed the computers had a specialized line of business insurance computer software hosted on a Unix computer that they also installed at AIA, which was networked to the AIA Microsoft Windows computers. This computer consulting firm also installed Microsoft Office on the Microsoft Windows computers so that the three people using these computers, the President of AIA, Mary Smith, the Office Manager Deb, and the Insurance Agent Tressa, could write letters in Microsoft Word to their clients and insurance companies whose policies they sold. They also had the ability with Microsoft Outlook to engage in e-mail correspondence with their clients and insurance companies. As this was the first time that anyone at AIA, in both their professional and personal lives, had used a computer, they were not knowledgeable about computers. The computer consulting firm had provided some basic instructions on how to utilize Microsoft Windows, Microsoft Word, and Microsoft Outlook, but they had not really trained the AIA personnel in the usage of these software products.
AIA’s Accountant had installed QuickBooks Accounting on Deb’s computer and taught her how to use QuickBooks, for which she would be responsible for entering transactions. Their Accountant also recommended that they purchase and install Contact Relationship Management (CRM) software to keep track of their client's and insurance companies’ correspondence. As he had heard good things about the Goldmine CRM, he suggested that they find a Goldmine CRM consultant. After an Internet search, they discovered my services for the Goldmine CRM software, and they contacted me about providing my Goldmine CRM services for AIA. After I interviewed and was hired by AIA for my Goldmine CRM services, I began to learn about their business operations, as Goldmine CRM could be customized to adapt to their business operations.
While learning about their business operations, I had some issues and concerns that needed to be resolved by Mary to continue my efforts. I, therefore, went into Mary’s office to discuss these issues and concerns. I found Mary standing behind her chair, looking down at her computer consultant seated in her chair, as he was explaining what she had to do to manage and update the security software that they had installed on the AIA Microsoft Windows computers. Every so often, he would turn to Mary and ask if she understood what she had to do, and Mary would nod her head yes and mumble an assent that she understood. He also informed her that this would have to be done on all the Microsoft Windows computers on a weekly basis. As I observed this interaction, I could clearly see in her facial expressions that she was really nodding no, and her body language was communicating that she had no idea what he was saying.
After the computer consultant left her office and the building, Mary sat down visibly frustrated and bewildered, and I remarked that she should not have to do any of this as it was the responsibility of the computer consultant to provide this service. She responded that she had never had a computer consultant and asked me what services a computer consultant should provide to a small business such as AIA. I spent about fifteen minutes explaining the services that a computer consultant should provide in non-technical language that she understood. After I finished, she asked me if I provided these computer consulting services, and I responded that these services were a major part of my company. At that point, she said to me, “In that case, he’s fired, and you're hired!” and that I was to immediately start providing these computer consultant services to AIA.
At another time, during my learning about their business operations, it was necessary to learn how they utilized Microsoft Word and Microsoft Outlook, as these products could be integrated with Goldmine, and I had to create Word templates they could utilize for their correspondence. I sat down next to Tressa as she was typing a letter in Microsoft Word and watched what she was doing. It soon became obvious that she did not know how to properly utilize Microsoft Word, as she never did a cut, copy, and paste operation, nor a drag-and-drop operation, which would have made her typing of the letter much easier. When she finished typing the letter, she printed out two copies of the letter, and I asked why she printed two copies. She responded that one copy was for their files, and one copy was to be postal mailed to the client or the insurance company. She then quit Microsoft Word without saving the document by clicking no on the dialog box that asked he if she wanted to save the document. I asked her why she didn’t save the document, and she responded, “What’s a Save.” At this point, I was sure that she had no idea how to properly use Microsoft Word. I then asked her what she would do if she needed to change the letter, and she informed me that she retyped the letter. After I explained and demonstrated to her what a save was and how to utilize the save, save as, and open in Microsoft Word to manage the letter she created, I also mentioned to her that she could e-mail a saved document to the customer. I explained that when she composed an e-mail, she could attach a saved document to the e-mail. At this point, she informed me that she only knew how to read e-mails.
As Mary and Deb were only a few feet away from Tressa’s desk, she shouted over to them, “Hey guys, did you know that we could save letters and e-mail them to the customer?” They both shook their heads in amazement, and I demonstrated this capability to Mary and Deb. I then suggested that I provide training to them in the proper utilization of Microsoft Word and Microsoft Outlook, as this would be needed for Goldmine usage, and Mary agreed and requested that I do this as soon as possible. As I already had training materials for Microsoft Word and Excel, it took me a few days to create Microsoft Outlook training materials, and the next week I provided them with this training. Within a few weeks after the training, they were comfortable with saving documents and e-mailing them.
As it was necessary for Goldmine and its DBMS to be hosted on a separate computer from Mary’s, Deb’s, and Tressa’s computers, it became necessary for me to purchase and install this computer. In addition, now that they were saving their Microsoft Word documents, these documents needed to be in a central repository accessible to all their Microsoft Windows computers, and this new computer would act as this central repository.
When I started working at AIA, they were a very paper-oriented business. Indeed, the attic above their office was full of filing cabinets to store all their correspondence with their clients and insurance companies. Each Windows computer had a printer attached so they could conveniently print their correspondence. As they transitioned to utilizing Microsoft Word documents and Microsoft Outlook e-mails and linking them to a Goldmine contact, they started utilizing the printers less and less. A few years after the transition to Goldmine was complete, each Windows computer had a document scanner attached. Whenever a paper document was received by AIA-ISSI, they would scan and save the paper document, and link it to a Goldmine contact, then place the printed document in the shredder bin to be destroyed. They had become a paperless business in which all business operations were conducted electronically.
On one weekend, when I was maintaining the AIA-ISSI computers, I noticed that Deb’s computer UPS was reporting an unusually high number of electrical events that were inconsistent with the other computers' UPS reports. I ran a self-test on the UPS to determine if it had any problems, and upon discovering that it had no problems, I powered off Deb’s computer and unplugged all the devices connected to the UPS as well as the plug of the UPS to the wall outlet. After re-plugging the UPS into the wall outlet and the devices into the UPS, I continued with my maintenance efforts for all the computers. At the end of my maintenance efforts, I rechecked Deb’s UPS and discovered that there were several more electrical events since I had unplugged and re-plugged.
When I returned to AIA-ISSI on Monday morning to inform Mary of my maintenance activities, I again rechecked Deb’s UPS and discovered that there were several more electrical events since I last checked. Upon informing Mary of this problem, I suggested that she contact an electrician to check and determine if there was an electrical line problem that was causing these electrical events. As her neighbor was an electrician, she contacted him, and he scheduled a visit for the next morning to check on this potential problem. Mary telephoned me the next day and informed me that the electrician had discovered that the circuit breaker in the circuit board was shorting and sparking and that they were lucky that it had not started a fire which may have consumed their office space as well as the other office spaces surrounding Mary’s office. When the electrician discovered this short and sparking, he immediately shut off all electricity to Mary’s office, and the computers UPSs supplied the electricity to the computers while they powered off all the computers, thus avoiding any computer problems from the loss of power to a computer.
About fifteen years after I started working for AIA, Mary informed me that she had bought another insurance agency from a former mentor of hers, who was retiring. This insurance agency, Insurance Specialty Service Inc. (ISSI), was at one time larger than AIA, but they had been downsizing the agency because of the changes to the insurance business when insurance companies started to utilize franchises rather than independent insurance agencies. It also did not help that the 2007 recession was in progress, which impacted many independent insurance agencies, but not AIA, as their specialty lines of insurance were necessary for the client’s business to operate. At its height, ISSI had a server computer and ten client computers, which were utilized by eight insurance agents. By the time Mary purchased ISSI, there was only one insurance agent that worked on the same line of insurance that Mary was interested in obtaining. Mary eventually decided to rename AIA-ISSI to just ISSI, and I had to update Goldmine and its document templates to reflect this change.
Mary and I met with this insurance agent, Kathy Liney, to discuss how to incorporate ISSI’s clients into the AIA business operations. For the next several months, Kathy and I worked closely to accomplish this incorporation. Kathy was very computer knowledgeable and skilled, which made the incorporation easier, which we did with minimal difficulties. As a result of Kathy’s computer skills and abilities, she was able to assist the other ISSI personnel with minor computer problems, and I was able to provide telephone instructions to her in resolving other non-minor problems, thus alleviating the need for me for onsite support when any problems arose. Kathy eventually left ISSI after four years to become a financial insurance advisor for a Boston, MA, wealthy persons financial advisory company.
About a year after we incorporated ISS into AIA, the Goldmine CRM started reporting time-out requests for data from the Microsoft SQL database (MSSQL) that stored the Goldmine data. A time-out occurs when MSSQL does not process a request for data within a fixed interval of time. These time-outs never occurred before the AIA-ISSI merger and were only happening infrequently but increasingly after the AIA-ISSI merger. I decided to go to ISSI on a Saturday to determine why this was happening and to fix this problem. The MSSQL DBMS was hosted on the Windows 7 computer that was utilized for all shared information at ISSI. Windows 7 had a number of utility programs that allowed me to see the activity that was occurring on the computer, and I utilized these utility programs to diagnose this problem. I was able to replicate this problem and then started my diagnosis. As I turned these utility programs on and off, the problem began to occur less frequently and sometimes vanished.
After about an hour of this occurring for no apparent reason, I sat back to think about why this was happening. It was then that I had a flash of inspiration, based on my physics knowledge, as I recalled the Heisenberg uncertainty principle problem of sub-atomic physics. The uncertainty principle, also called the Heisenberg uncertainty principle or indeterminacy principle, articulated in 1927 by the German physicist Werner Heisenberg, was that the position and the velocity of an object cannot both be measured exactly at the same time, as measuring one interfered with the other. I realized by utilizing these utility programs that I was interfering with the normal process of the Windows 7 computer, which alleviated the MSSQL problem and made diagnosing this problem impossible.
I, therefore, had to resort to theory rather than practice to resolve this problem. I began by researching several Microsoft technical articles about how MSSQL processed transactions, then researching several Microsoft technical articles about how Windows 7 allocated computer resources to the running processes. After an hour of this research, I concluded the MSSQL Goldmine database had become sufficiently large enough that it outpaced the ability of Windows 7 to allocate resources to MSSQL. I also discovered that Windows 7 had insufficient tools to reallocate resources to MSSQL but that Windows Server had the proper tools to do this reallocation and, indeed, was designed to automatically reallocate computer resources on demand. I telephoned Goldmine technical support to confirm my findings, and not only did the support technician know Goldmine, but he was also an MSSQL support technician for Goldmine. After discussing this problem and my findings, the support technician explained that this was a known problem of MSSQL on a Windows 7 computer, and the only solution was to upgrade to a Windows Server computer to host MSSQL. I then stopped my efforts to resolve this problem and went home to think about how to upgrade to a Windows Server and the issues and concerns of changing ISSI’s network from a peer-to-peer network to a Client-Server network, which was necessary whenever a Server computer was installed on a computer network.
By Monday morning, I had a plan, and the costs associated with the plan, to upgrade to a Windows Server computer and convert their network to a Client-Server network. After discussing this with Mary and Kathy, she agreed that it was necessary to do this. I also expressed my concern that I was not a Network Administrator but familiar with Network Administration and that I would be venturing into uncharted territory for myself. Both Mary and Kathy expressed confidence in my ability to do this upgrade, and I started my efforts on this upgrade. I decided to purchase a bare-bones computer for my own usage and install an unused Windows Small Business Server license that another of my clients (Best Associates) had available to learn and test out this conversion.
From this learning experience, I determined that the conversion would be a four-day effort. After discussing this with Mary, she agreed that they would cease using their computers on a Friday afternoon at 2:00 PM when I would begin my conversion efforts. I did not expect this effort to be complete until late Monday morning, and she agreed not to use her computers on Monday morning. I also decided to remain at ISSI all Monday afternoon to resolve any issues or problems that may arise from this conversion. All went well with this conversion, and their computers were available by noon on Monday. There were also very few issues and no problems after their computers became available for their use. I then became the Network Administrator for ISSI, the first and only Network Administration that I did as a computer consultant.
Mary turned out to be one of my most wise and intelligent clients, and after over two decades of being hired by Mary, I decided to retire. I discussed this with Mary, for which she understood my reasons but was saddened that I would no longer be able to assist her and ISSI. She requested that I help her find my successor, and after I researched various computer consulting firms, we interviewed five different companies. Only one company impressed us during these interviews. He was a self-employed computer consultant with one junior assistant who would not be needed for ISSI computer consulting. I remarked to Mary that he reminded me of myself, and Mary commented that she was thinking the same thing. She, therefore, hired him to be my successor.
During over two decades of working at ISSI, I noticed that nobody worked for Mary but that everybody worked with Mary. This was because her management style was one of an extended family relationship, with Mary being the matriarch of the extended family. This led to a very cordial and friendly relationship with and between all the people working at ISSI, including myself, and was also a testament to Mary’s character. I was often included in outside activities such as luncheons or special dinners. When my beloved dogs died at the beginning and the end of my relationship with Mary, whom I had taken to the AIA-ISSI office on a few occasions to meet the gals, she sent me flowers and a condolence card on the death of my dogs. Mary also gave me a retirement dinner which everybody at ISSI, and my wife, attended. I will always fondly remember my experiences working with Mary and the ISSI personnel, and Mary and I also maintained a personal friendship after I retired.
Elder Service and Betterlife
Elder Service, Inc. was a professional service company that assisted Seniors and their Relatives through the maze of Social Services and Health Care processes, as well as providing home healthcare assistants to home-bound seniors. Mary Van Everbroeck was the founder and manager of this company that she started shortly after her retirement as a U.S. Army Major, where she was a personal and family counselor to U.S. Army servicepersons and their families. She contacted me as she started to encounter problems with her computer. I was able to quickly diagnose and correct these problems, and afterward, she mentioned that she was overwhelmed with work managing her business, and she often found herself working ten hours a day, seven days a week, leaving her with no personal life. I engaged her in a conversation to determine if there was any way I could assist her in reducing her workload. I discovered that her business operations were very inefficient and paperbound. After I explained what I could do for her business, I suggested that she hire me to computer automate her business operations. She readily agreed to this, and I began my efforts to computerize her business operations.
She had the same initial cardinal rule problems, which I corrected, and I installed, configured, and customized Goldmine CRM and QuickBooks accounting for her business. I then developed and documented the operational procedures for Goldmine CRM and QuickBooks then instructed her over several days on how to utilize these computer applications to conduct her business. After a few months of utilizing these computer applications, she informed me that she was now only working eight hours a day, six days a week, leaving her with one day to enjoy her personal life.
She also had me develop an Elder Service website that she utilized to market her services, and she informed me that she was garnering many clients from this website.
Her husband, Leo, who had left the Catholic priesthood to marry Mary, had started his own business, Betterlife. Betterlife was a public speaking seminar workshop service to lecture and counsel his Five-Step Life Empowerment Model, A Practical, High Power, Optimum Results Oriented Model developed over several decades combining academic research in the Systemic Paradigm together with consulting and working with a multitude of professionals and organizations. Leo hired me to develop a Betterlife website that he utilized to market his services, and he informed me that this website garnered him a few clients and speaking engagements.
Eventually, Mary decided to sell her business to a competitor, and as she looked around for another career, she decided to establish Pet Guardian Education and Animal Advocacy Services, Inc., A 501c Public Charity Organization dedicated to pet rescue, adoption, and pet care counseling. She had me develop a website for this organization and set up modest business operations for this organization on her computer.
After a few years of doing this, she realized that it was not going very well as there was limited demand for these services, and she closed down this organization and opened a marriage counseling service, which I played no part in.
Auto Exchange
Sam Feinstein of Feinstein Racing, 1973 SCCA National Championship Runoffs Class A Production Shelby Cobra 427, a.k.a. “The Green Dragon”, had long since retired from racing when I met him. He owned a small used car lot when another client introduced him to me. He had just bought a computer for his used car lot, and he was having difficulties utilizing the computer to operate his business. I provided him with all my services, including computer training and the development and regular updates for the next fifteen years of a website featuring all the cars that he had for sale on his lot.
Sam and I became very friendly, and as his used car lot was only a mile from my house, I often passed by the lot and stopped for some friendly conversation. When my Subaru car died after ten years and 120,000 miles, I purchased a ten-year-old Lexus with 60,000 miles from Sam. This Lexus had been sitting on his lot for nine months, as he found it difficult to sell to his normal clientele. He offered it to me at his cost, which I readily accepted. When the Lexus died, after five years and an additional 60,000 miles, I purchased a Toyota Avalon from Sam, which I drove for seven years, and 70,000 miles before I purchased a new Mazda, as Sam had retired. I also purchased a used car from Sam for my daughter’s use during her senior year at high school and her college years. Sam eventually retired and closed the used car lot, and I lost touch with him shortly thereafter.
BioTech
BioTech was a self-employed home-based business that provided independent technology reports about the biotechnology industry development efforts. I was contacted by Bob, the owner-operator of this business, to provide computer support for his business. This was a modest effort after I corrected his initial cardinal rule problems. About two years later, Bob called me to report that his computer was not working. I soon discovered that he had a hard disk crash that would require a replacement disk and a restore from the backup of all his documents. He sheepishly admitted to me that he had canceled the automatic backups as they were interfering with his work schedule.
After I replaced his disk drive and installed Microsoft Windows and his application programs, I restored his documents from his last backup and discovered that his latest backup was over six months old. When I informed Bob about this, he was glum, but as he had paper copies of all the reports he had created, he would be able to retype the missing documents (which took him over a month to accomplish). Bob never missed a backup after this, but a few years later, BioTech went out of business.
Bob’s wife, Liebe, also operated a self-employed home-based business for which I provided my services. Liebe was a physician who examined medical claims made to an insurance company to determine their medical appropriateness and if they were within the boundaries of their insurance policy. I also corrected her initial cardinal rule problems, then provided both Bob and Liebe with whatever computer support they needed until their son became an adult and started assisting them.
A2G Sales, Non-Stop, and CuTech
A2G Sales was a company that sold and distributed pet supplies from manufacturers to retail pet stores in the Philadelphia metropolitan area. This company was a self-employed business owned by Gary, the second husband of Alicia of Blue Bell Hearing. Gary was not very literate about using computers, and I assisted him in setting up and using his home-office computer to run his business. While he eventually became self-sufficient in utilizing his computer, I often had to visit his home (which was only a half mile away from my home) to help him with his computer issues. When he obtained a cell phone, he took to it like a duck to water, and I only had to provide him with minimal assistance with his cell phone.
A few years after I started helping Gary, he informed me that he had a manufacturer that he wanted to integrate into his business. CuTech, Inc. was a domestic and international supplier of specialty chemicals to the printed circuit industry. The President and chief engineer of CuTech had developed a new product that he wished Gary to sell. He formed a new subsidiary of CuTech, Non-Stop Inc., that manufactured top-of-the-line, quality stain and odor control products and backed them up with a commitment to customer satisfaction. He had hired Gary to sell this product to pet stores, and Gary wanted a website to promote this product. After creating this website, the President of CuTech decided that I should create a website for CuTech. In the middle of this website development effort, the President of CuTech unexpectedly died, and his wife sold the business. The new owner of CuTech had no interest in the Non-Stop product and ceased production. He also absorbed CuTech into his current business and discontinued the CuTech brand, which ended my development of the website for CuTech, but the new owner paid me for my efforts to date.
I provided my services to A2G Sales for two decades until my retirement, with an occasional call for advice thereafter.
MEDS-I-TAKE, DBA-Bvi Ltd, and Guardian Angel Products Inc.
Chuck Pescatore was a client of Sutton Advertising that had prepared a print advertising campaign for a new business Chuck was starting—MEDS-I-TAKE. Russ Sutton recommended my services to Chuck to computerize this new business and develop a website for this business. MEDS-I-TAKE was for the purpose of producing a bright yellow credit-card size plastic card that listed all the medications a person was taking, which could be used when filling out forms for a doctor, hospital, or medical emergency services.
In discussing my services with Chuck, I learned that he wanted an automated process that would allow the customer to fill out a web form with the medication information, pay for the card with a charge card or PayPal, automatically import this information into his computer, and produce the card and a postal mailing label. He had already purchased a computer for MEDS-I-TAKE that had a printer, a plastic card printer, and a postal mailing label printer attached. I informed Chuck that it would be possible to accomplish this by utilizing Goldmine CRM as the core of this automated system and that I had the knowledge and experience to accomplish this. The only knowledge I lacked was how to utilize PayPal for payment purposes, but I knew how to utilize credit card payments from my experience with HK Pickles. He commented that I would gain this PayPal knowledge and experience, as he intended to hire me to undertake this effort as I suggested.
I spent the next month (on a part-time basis) developing the website and automated computer system, along with instructions on how to utilize this system. Chuck was very pleased with this website and automated computer system and started his marketing campaign to promote MEDS-I-TAKE. Unfortunately, the demand for this product was small, and he sold less than one thousand cards in the first year and even fewer cards in the second year, and he decided to close this business down after two years.
Chuck also had two other businesses, DBA-Bvi Ltd, and Guardian Angel Products Inc., for which he contracted with me to provide my services. Each business had its own computer system, and I would be responsible for maintaining the three computers which Chuck utilized. All three computers had the same initial cardinal rule problems, which I corrected. I also assisted Chuck in automating the business processes for these companies.
The one company, Guardian Angel Products Inc., manufactured in China a small, low-cost, one-usage electrical process for testing the electrical power of defibrillators before they used the defibrillator on a person. Chuck also sold small surgical medical equipment (such as scalpels, forceps, and tweezers) manufactured in America and Germany to local hospitals in China. Chuck traveled to China twice a year to oversee these businesses, and he would often tell me about his experiences in China, which I referred to as my China Experience.
As Chuck approached his mid-seventies, his health started to fail, and he passed away at seventy-seven years old, just three days after I last saw him. I helped his wife, Sue, and his daughter understand how he utilized his computers so that they could sell these businesses. It was fortunate that I had most of his passwords, and I knew where he kept a list of his passwords; otherwise, they would have been unable to access his computer information. Something that all businesses and people should keep in mind in the event they become medically impaired or pass away.
I often stopped by Chuck’s office, which was only a mile away from my house, to just have a friendly conversation with him, as we both regarded each other as friends. I miss these conversations and our friendship, and I will always think of Chuck with admiration and respect.
Qualified Sales, Inc.
Qualified Sales was a self-employed businessperson who set up his own company to support the marketing, sales, and distribution logistics for a national bakery. He had two computers in his home office, as well as two other computers for his wife's and children’s use. He contracted my services to support all the computers in his home, but most especially for the support of his home office computers. He had the same initial cardinal rule problems, which I corrected, as well as my installing, configuring, and customizing Goldmine CRM for his business. I also developed a website for his business. I even spent a long weekend at his mountain vacation home in central Pennsylvania to set up and maintain the computer in this house for his business usage while he and his family were staying at this house.
I provided my services for over a decade when our relationship ended abruptly. I watched his children grow up, and when the eldest son graduated college, he asked me to modify the website to extoll the contributions of his son to his business. As I knew that his son had no contributions to his business, and mindful of Harold Goldberg’s example of not becoming involved in any unethical conduct of a client, I refused to do so. He informed me that if I did not do so, then he had someone else he knew who would do so, as well as provide him with his computer support needs. So ended our relationship.
Telegard, Inc.
Telegard, Inc. is a full-service consulting firm providing Telecommunications expertise to clients in supplemental staffing, project management, cost control, and permanent staffing. They helped their clients organize, identify, analyze, and optimize their telecommunications areas, including systems, equipment, services, and contracts. While Telegard had several technicians, John Harahan was the owner and manager of Telegard as a one-man show, and he needed assistance with his laptop computer that he utilized to manage the business. He had the same initial cardinal rule problems, which I corrected, as well as my installing, configuring, and customizing Goldmine CRM for his business. While John’s computer support needs were modest, as he was very adept at utilizing his laptop, I, therefore, have no professional stories to relate. We quickly developed a personal relationship, and he often called me to just chat and see how I was doing. This personal relationship with John also extended to our having several breakfast meetings at Starbucks coffee shops, as well as a few lunches together over the many years that I supported his laptop.
Ty Steinberg
One day I received a telephone call from Ty Steinberg, who introduced himself as a friend of a client of mine. He explained that he had some computer problems and required some computer assistance. I agreed to meet him the next day at his apartment complex, which was a senior citizen complex. I was greeted by an eighty-eight-year-old spy and intelligent man that utilized his computer for business and personal purposes. Ty explained that he was the former major owner and President of Buten Paints and that when he sold this business, he retained ownership of many of the paint stores, which he and his partners refurbished and leased out to other businesses. His problems were modest, but he did require assistance in utilizing QuickBooks accounting for his business, Quicken accounting for his personal finances, and Microsoft Excel spreadsheets, which he prepared for his business partners every month.
I was able to quickly resolve his current computer problems, and I recommended that I fix his cardinal rule problems, which he was not abiding by. He agreed that I should do this, and he mentioned that his wife, Marjorie, also had a personal computer in the room next door that did not abide by these cardinal rules. She was also having some minor problems that I was easily able to resolve. For the next five years, I was able to assist Ty with his computer problems and the utilization of QuickBooks, Quicken, and Excel. Many times, he had minor difficulties that I was able to resolve by remotely accessing his computer, but many times I had to visit his apartment to resolve the problems or provide extensive assistance with QuickBooks, Quicken, and Excel.
During many of my visits, Ty, Marjorie, and I had lunch together at his kitchen table, and we developed a personal relationship almost immediately. I was always happy to visit Ty and Marjorie, as I knew that it would be a pleasant and warm visit. In the middle of our relationship, I encouraged Ty to turn over his business to one of his sons and enjoy the time he had left in his life with Marjorie. Near the end of our relationship, Marjorie started to suffer from dementia, and I was able to commiserate with Ty as my mother had just passed away after more than ten years of suffering from dementia. About a year before I retired, I received a telephone call from one of Ty’s sons informing me that Ty had slipped and fallen and was injured and unable to run his business, and he needed my help to take over the business. I was able to remotely help him, as I knew practically everything about Ty’s computerization of the business, including his passwords and where he stored his passwords list.
A few months after I retired, I received a telephone call from this same son informing me that Ty had passed away. His son mentioned to me that Ty often would comment that he would brook no negative comments about me and that I should always be trusted as he knew me to be a truthful, honest, and ethical person. I was invited to the funeral, but on the morning of the funeral, I injured my knee and could not attend. However, the funeral was being videocast, and I watched every minute of the funeral. Afterward, I wrote some comments about Ty, which I e-mailed to his son, who shared it with his mother and brother, and all found it quite touching. I often think about Ty and Marjorie and the wonderful but brief four-year relationship that we had.
My Last Lawyer Client
After My First Lawyer Client retired, I had a personal legal issue that required legal counsel, and I telephoned John to get his advice and a recommendation for a lawyer who could help me with this legal problem. Adrian Meyer was the civil lawyer that he recommended, who had his own legal business, which was staffed by only Adrian and his legal secretary. After Adrian helped me with my legal problems, he hired me to support his and his legal secretary's computers. As usual, he had the same initial cardinal rule problems, which I corrected. I also helped Adrian with his wife’s home computer, and I provided my services to Adrian for many years until I retired.
Mutual Real Estate Corp
My last client came to me via a plea from another client that even though he knew that I was a few months away from retirement, he had a good friend that was experiencing computer problems with his business computers, and could I please advise his friend about his problems? I telephoned Mutual Real Estate Corp. to discuss their problems, and I agreed to a visit to examine their computers and discuss their problems, but I may elect not to solve their problems.
Mutual Real Estate Corporation (“Mutual”) is a commercial real estate brokerage and appraisal company which specializes in commercial and industrial real estate sales and leasing and evaluation services within Southeastern Pennsylvania and New Jersey. Mutual also devotes approximately one-third of its annual activities to multi-tenant investment properties comprising Commercial office, retail, and apartment communities.
I discovered that Mutual Real Estate Corp. was a two-person business headed by the owner-operator, Lou, and his secretary. Each had their own computers, which were over six years old and utilizing Microsoft Windows 7, and the computer software installed on these computers was out-of-date. The computers were also not networked to each other and not sharing company data. In addition, both computers violated my cardinal rules.
In discussing these problems with Lou, I advised him not to fix his problems, as they may not even be fixable, and it would take some considerable time to diagnose and fix the problems. Instead, I recommended that he should purchase two new computers and reconfigure his computer environment. This reconfiguration would be to purchase upgrades to all his computer software, network the computers via a firewall/router, utilize a Network Attached Storage (NAS) hard disk drive to store and share all company data, backup his computers and the NAS drive on a weekly basis to a USB connected External Disk Drive, and have a UPS to protect all the computers and equipment on his computer system. After this was done, it would be possible to transfer the data from his old computers to the NAS Drive.
Lou asked me how much this would cost and how long it would take to accomplish this effort. I estimated that it would cost about $6,000 and sixteen to twenty hours of labor. He asked me if I would do this for him, and I responded that this would not be difficult for me to accomplish but that I could not support his computer system after the new year as I was retiring. He responded that he was aware of my impending retirement, but he wanted me to undertake this effort, as the client who had recommended me highly praised the quality of my work and that I was an honest and trustworthy person.
I agreed to do this for him, and three days after the new computers arrived, he had a new computer system that he was very pleased with. Over the next several weeks, I visited his office to make minor tweaks to his computer system and to instruct him and his secretary on how to utilize their new computer system. After I finished this effort, he had a friend who was the manager of a computer department for a small business examine his new computer system. His friend commented that I had done an exemplary job for him, and he could not think of any improvements to what I had done for Lou.
Miscellaneous Stories
Several other stories that occurred throughout my computer consulting career are worth relating without mentioning the client:
The Retail Furniture Store
A client of mine had a friend that owned a small retail household furniture store, and he was thinking of computerizing his business operations. I paid a visit to his friend at his store to discuss his needs. His needs were modest but extensive, as he wished to convert his paper-oriented transactions to electronic documents, keep a record of his customers and suppliers, do basic bookkeeping for his business, as well as maintaining an inventory of his stock. I knew that computerizing his business operations would not be difficult for me to accomplish, and I informed him that I would prepare a proposal for the costs involved in undertaking this effort.
I prepared a proposal listing all the material and labor costs to computerize his business, which I dropped off a few days later at his store to discuss this proposal. He was flabbergasted at this cost ($6000) as he knew a computer and printer only cost about $2000, but he was unaware of the other equipment costs, as well as the software costs, nor how much labor would be required to install the equipment and software, as well as provide him training on the software. He informed me that he would have to think about my proposal and that he would get back to me when he made his decision. A week later, he telephoned me to inform me that he was not going to computerize his business as he could not afford the cost. I thanked him for his interest in my services, and if he changed his mind, to please contact me.
About nine months later, my client, who referred me to him, informed me that he had contacted another computer consultant who quoted him a cost of $5000, and he had this other computer consultant computerize his business. He also informed me that he was highly dissatisfied with this other computer consultant as he had overrun his budget by $2000 and did not provide proper instruction on how to utilize the software to operate his business. He regretted ever getting involved with this computer consultant, and he wished that he had instead utilized my services, as he was now sure that I knew what I was doing while the other computer consultant was just leading him on to get more money out of him. I had no regrets, as it has always been my policy to inform my clients what they needed to know and not what they wanted to hear. I always slept well at night, as I was always honest and truthful with my clients, and I never had any regrets about my dealings with my clients.
The Adobe Acrobat Sham
Shortly after I began my computer consulting business, I was contacted by a small start-up insurance company that wanted me to create Adobe Acrobat application forms that they could distribute to prospective customers. These Adobe Acrobat forms would have fields that the user could type information into, drop down, or click buttons for the selection of what was to be covered, amounts to be insured, then calculations for the premiums for the insurance coverage. Although I had no Adobe Acrobat experience, I did know JavaScript, which Adobe Acrobat used to accomplish these tasks. They hired me to do this, and I set about learning how to do this in Adobe Acrobat, which was not difficult. I then asked for the specifications for the user-supplied information and the calculations that would be required, and I discovered that they had no specifications or calculations nor plan of how to do this; they just wanted me to start this effort and make any corrections that I found necessary to accomplish this task. In reviewing these forms with the persons who would process these forms over the next several days, I learned that these specifications and calculations were complex and fraught with the possibility of errors.
Upon discussing my findings with the general manager of the company, I informed her that the effort to document these specifications and calculations would take several weeks, if not months, to properly document, and some of the calculations may not be possible in Adobe Acrobat. She was not interested in hearing this, and she instructed me to just begin the effort of creating the Adobe Acrobat forms. After thinking this over, I decided that this was a hopeless task, doomed to failure and possible financial and legal repercussions if not done correctly. I, therefore, declined to do this and informed the general manager of my decision and the reasons for my decision, and left the building to never return. I invoiced her for my efforts, but they never paid me for my efforts, and I just wrote off the monies due to me for my efforts.
The Dark Desk
While visiting a client of the other Goldmine VAR that I was briefly associated with, I was working on the President’s secretary's computer when the President stepped out of her office and declared that her computer mouse was not working again, and her frustration that this was the fourth mouse that had failed her in the last month. This company had a computer and network support department that seemed unable to correct this problem. I asked her if she would like me to look at this problem, and she responded affirmatively. Upon entering her office for the first time, I discovered that it was a beautiful office adorned with ebony wood and black granite tables and desktops. She commented that she had just a few months ago had the office refurnished, and ever since they replaced her computer, the mouse would act sporadically.
I sat down at her beautiful ebony black marble desktop and picked up her mouse, then turned it over to examine it. I immediately knew what her problem was. She had an optical mouse, which along with her black marble desktop, was the reason for the problem. An optical mouse is now the most common type of computer mouse, first introduced in 1999, that utilizes LEDs (light-emitting diodes) or a laser to track or detect movement. As her previous computer had a mechanical mouse (a computer mouse containing a metal or rubber ball on its underside), a mechanical mouse would not be a problem. With the introduction of an optical mouse with her new computer, this was a big problem. The black marble desktop was absorbing and diffusing the light from the optical mouse, thus causing it to act sporadically. I explained this to her and demonstrated this effect by using a paper pad as a mouse pad. I suggested that she stop at an office supply store and purchase an optical mouse pad to her liking, and her mousing problems would disappear. After she came back from lunch with an optical mouse pad, she no longer experienced any mousing problems. She commented on the idiocy of her computer department in not knowing this, but I informed her that as optical mice were so new that many computer support personnel were not aware of the problems with optical mice. I also began to recommend that all my clients use an optical mouse pad when they acquire an optical mouse.
Fix It – Don’t Replace It
While visiting my divorce lawyer’s office, he informed me that his neighbor next door was complaining of computer problems, and he suggested that I stop by his office and introduce myself and my services. When I finished with my divorce lawyer, I did so. He was a self-employed person who provided Computer Aided Designs (CAD) diagrams for his clients. His computer was responding slowly and sometimes freezing while he created his CAD diagrams. Upon examining his computer, I discovered that he was having intermittent disk drive problems that were causing his problems. When he asked what could be done to fix this problem, I responded that the disk drive would have to be replaced and rebuilt, along with restoring his data from a backup. He admitted that he had no backups, and I also discovered that he was violating my cardinal rules. As his computer is over five years old, I recommend that instead of replacing the hard disk drive, he purchase a new computer, which I would set up with my cardinal rules, then back up his old computer data and restore it on his new computer. He asked how much effort, time, and cost it would take for each solution. I ballparked the disk replacement at about six hours and five hundred dollars, with an additional three hundred dollars to implement my cardinal rules, while the computer replacement (and my cardinal rules implementation) would take about sixteen hours and at the cost of about three thousand dollars.
He elected not to replace his computer and directed me to do the disk replacement. I cautioned him that his computer could fail at any time and he would probably need a computer replacement within a year. He informed me that he would do this when his computer finally failed. The next day I arrived at his office with a new disk drive and spent the next six hours backing up his computer data, installing the new disk drive and Microsoft Windows and his computer applications, then restoring his data onto the new disk drive. He was satisfied with my work and paid me on the spot, informing me that he would contact me if he encountered any problems.
Three days later he telephoned me to inform me that his computer would not turn on. Upon arriving at his office, I opened the computer case to diagnose the problem. It was immediately apparent that his computer had experienced an electrical surge, and the motherboard, and possibly other components, was damaged beyond repair. I showed him the problems and informed him that he would have to purchase a new computer. He asked if we could purchase a new computer without a disk drive and use the disk drive that I had just replaced in the new computer. I informed him that there was no guarantee that the new disk drive had not been damaged in the electrical surge, and purchasing a computer without a disk drive was possible but difficult and often more expensive than a fully functional computer.
I, therefore, purchased a new computer for him at a bare minimum configuration and cost, then installed his computer applications, followed by a restoration of his data that I previously backed up. I also insisted that he follow my cardinal rules with this new computer, which, if he had done it previously, would have prevented the electrical surge. After I finished this computer replacement, he was again satisfied with my work and paid me on the spot, informing me that he would contact me if he encountered any problems. I never heard from him again, which in many ways I was thankful for, as I believed him to be penny-wise and pound-foolish, which never bodes well when dealing with computer technology. I have never had a client complain that they spent too much on computer technology, but I have had a few clients that complained that they spent too little on their computer technology. They discovered that the cost of upgrading their computer technology was much greater than the cost of originally purchasing upgraded computer technology, and it was better to be pound-wise and penny foolish when purchasing computer technology.
The Cleaning Lady
A business client telephoned me one Monday morning to inform me that his computer would not turn on, which was stranger still, as he had forgotten to turn it off when he left work Friday afternoon. When I arrived at his office, I examined the UPS that I had installed for him and discovered the UPS was not plugged into the wall outlet but was instead plugged into itself. He informed me that he had left work early Friday afternoon as the cleaning lady was doing a thorough cleaning of his office and making quite a racket with the rug shampoo machine. I deduced that she had unplugged the UPS to shampoo the rug underneath it and then re-plugged the UPS into itself when she was done. As his computer was still on, it was running on the UPS battery that drained the battery over the weekend. I plugged the UPS into the wall outlet, and the computer was able to power on. After testing the UPS and determining that the computer had not been damaged by the loss of power, I exited his office just fifteen minutes after I arrived.
The Porn Incident
I had a family client, who I was very friendly with, that had a laptop computer for the husband’s practice usage (he was a physician who literally saved my life one time) and another computer for his wife and two boys' usage. While working on the wife’s computer, which was experiencing minor problems, I discovered a hidden folder on the computer, and when I examined its contents, I discovered his teenage son’s porn stash. I laughed and said nothing about this to him, but a few days later he telephoned me to ask if I had discovered the hidden folder which he had just discovered. I admitted that I had but said nothing because I did not want to embarrass anyone. He started to apologize to me, but I cut him off, saying that this was often common to teenage boys in the Internet age. I did point out the upside to him, as he now knew for certain that his teenage son was not gay. We both laughed, and our friendly relationship lasted past my and his retirement.
The Builder
One of Harold Goldberg’s accounting and tax clients was a self-employed home remodeler and improvement contractor, and if you couldn’t place a tool in his hand, he couldn’t understand it. He was a very nice person, but computer illiterate. I went to his home office to help him with his computer problems, which turned out to be easier than I had dreaded. His newlywed wife was computer literate, as she had a full-time clerical job at a plumbing supply company in which she utilized a computer to do her work. She informed me that she was going to take over the computer work for her husband’s business, as he was hopeless at computer work but very good at home remodeling and improvement. She was very adept at doing his computer work and required little of my services after my initial visit and instructions. Fortunately, his ego did not preclude him from allowing his wife to do the computer business operations. It was refreshing to have a client with this lack of ego about their computer literacy, as one of the problems I encountered in my computer consulting was the ego of my clients regarding their computer knowledge, which I was able to overcome with non-technical explanations, diplomacy, and a little flattery.
The Phillies Games
One of my clients was a successful salesman who had two-season box seat tickets to the Phillies, which he often gave to his customers. After I started helping Bill with his home-office computer and his wife Joy with her personal laptop, with their computer problems, he always made sure that every season I would get two of these tickets. As my wife was not a baseball fan, my best friend and I enjoyed a Phillies game every year.
* * * * *
While I had other business and personal clients throughout the years, the above stories are those that helped shape my computer consulting career, and I thought it would be interesting to relate.
Retirement (Jan 2020)
As I reached my sixty-seventh birthday, I realized that the physical efforts and mental stress of performing my job were becoming very difficult. At my annual checkup with my doctor in July 2019, I mentioned this to him. He, whereupon consulted an online database of job titles and descriptions that contained the percentage of people by age group who were working in these jobs. We decided that my proper job title was Computer Administrator. The database revealed that only 0.05% of the people employed in Computer Administration were in my age group. He informed me that when these percentages were in the single digits, he advised his patients to start considering retirement, and when they were less than 1%, he asked them why they were not retired. He commented to me that the only valid reason for not retiring was financial, and he asked me if I needed the money. When I replied in the negative, he asked me why I hadn’t retired. Having no good reason for not retiring and given the physical efforts and mental stress I was feeling, I soon thereafter decided to retire.
I began to inform my larger clients of my plans to retire, and we began a search to find another computer consultant that could properly meet their needs. After we interviewed a half dozen potential computer consultants, we focused on one Computer Consultant. Both my clients and I remarked how much he reminded us of myself in my younger days. I, therefore, started the process of turning over my business to this computer consultant. I had calculated the sale price value of my business, but it was so ridiculously low that I did not sell him my company, and I was more concerned about finding the right computer consultant to meet my client's needs. I have remained in contact with some of my former clients, and they have all expressed that they were very satisfied with this computer consultant. By the end of the year, I had finally retired and was glad that I had done so.
Epilog
One of the overarching lessons that I learned is that when you are faced with a serious problem, an adverse situation, or an emotional confrontation, the best thing you can do is become dispassionate and analytical and remain silent until you have gathered as many of the facts as possible. Only then should you speak up, but only speak up in a rational and reasonable manner. It took me several decades to fully learn this lesson, and I can objectively say that most of the problems in my professional life were a result of not applying this lesson, and most of the successes of my professional life occurred when I applied this lesson. I still occasionally make this mistake, and when I do make a mistake, I instantly regret it and then apologize to the people involved when I regain my composure. I have also learned the importance of an apology when you realize that you have behaved inappropriately. You should never be afraid to apologize when you are wrong, as an apology will often elevate you in the eyes of those to those you offer an apology. You will also often gain more friends, and fewer enemies, after an apology.
Many people would ask if I had any regrets or if I wished I could have done anything different or changed anything that I said or did. To this, I would say I have written my regrets in this book. As to doing anything different or changing anything, I would remind all that the events of our life shaped us and led us down the path of our life. To change or to make anything different would have created a different life path. The question is then whether this different life path would have been any better or worse than the life path we have taken. To this question, there can be no answer. The real question is if the life path we took was a worthwhile path.
My professional life path has led me to do many different and sometimes unique things in my career. Many things that I have done have had a positive impact on me, my professional associates, and the businesses for which I was employed or was a consultant. I know that I have taken much gratification in the accomplishments of my career. The good that I did, I believe, has far outweighed the harm that I may have occasionally inflicted. Consequently, I can say that I am satisfied with my professional life path and that it was a worthwhile path.
Winston Churchill once said, “The pessimist sees difficulty in every opportunity. The optimist sees the opportunity in every difficulty.” to which I would add, “A realist sees both the difficulty and the opportunity of all challenges and deals dispassionately with whatever happens.” My professional life has led me to be a realist, and I eventually learned to deal dispassionately with all the challenges I faced in my career. I also believe that my life path has increased my intelligence, knowledge, and wisdom. The intelligence, knowledge, and wisdom that I have utilized to write the Chirps and Articles of my website, and the knowledge and wisdom that I try to impart to others in the hopes that it will positively influence their life paths. It is for this reason that I have written these stories from my examined professional life.
Throughout my professional computer career, I have had many good and bad things happen to me. Sometimes these things have happened because of my own actions, sometimes because of the actions of others, and many times they just happened. This led me to compose the following ditty:
"Shit happens. Sometimes you shit on
yourself, sometimes others shit on you,
and other times shit just happens.
It doesn't matter how shit happens, it only matters how you deal
with the shit.
You can either clean yourself up and smell the roses,
Or you can wallow in the shit and everything stinks.
And remember, It's just as important to learn from the shit,
as it is to clean yourself up from the shit!"
- Mark Dawson
I have therefore spent my professional life examining the shit that happened to me and learning from this shit. This examination needs to be done in an honest and brutal fashion that examines your own faults and good points, as well as the faults and good points of others. This examination has made me become a better computer professional, helped mold my character, and made me a better person.
These autobiographical stories from my computer career are the result of my examining my computer career in an honest and brutal fashion. I would encourage all to examine their own life experiences in an honest and brutal fashion to become a better person in their career and personal life.
